Introduction to Blockchain 丨 How to prevent SIM card fraud attacks?
Author: Cobo Vault security trainee
In September 2019, network security company Adaptive Mobile discovered a serious vulnerability in the SIM card, Simjacker. Recently, the company released a list of countries vulnerable to Simjacker attacks, including 29 countries on five continents.
On August 15, 2018, US investor Michael Terpin filed a lawsuit worth AT $ 24 million with AT & T. Because he believes that the telecommunications company provided hackers with access to his mobile phone number, which led to a major cryptocurrency theft. Michael Terpin is a Puerto Rican-based entrepreneur and CEO of TransformGroup inc. He is also the co-founder of BitAngels (an angel team for Bitcoin investors) and the digital currency fund BitAngels DApps Fund. Terpin claims he suffered two hacks in 7 months, which directly resulted in him losing $ 24 million worth of cryptocurrency-in a 69-page indictment he filed with California law firm Greenberg Glusker Two hacking cases that occurred on June 11, 2017 and January 7, 2018 were mentioned, and the document showed that AT & T failed to protect his digital identity in both hacking attacks.
What is a SIM card scam?
- "Chain Shanghai South" plan announced! Hainan Free Trade Zone (Hong Kong) Blockchain Pilot Zone Releases "Six Chains"
- The biggest "coin difficulty" after 9 • 4 is happening, or it will pave the way for the central bank's digital currency
- European Central Bank: Central bank digital currency will be issued without efficient pan-European payment solution
Most of the SIM card fraud is to copy or re-process the victim's SIM card by bypassing the security measures of the telecommunications operator, so as to control the stolen SIM card. In the current Internet security environment, the mobile phone number of the stolen person can be controlled, and the majority of the stolen person's account permissions can be obtained through the SMS verification code verification mechanism. This also includes the vast majority of the stolen financial account Or a cryptocurrency cloud account. For most attack methods, the attacker only proves to the operator that it is the user who reissues the SIM card through simple social engineering, such as collecting the identity information of the stolen person and stealing the letter. In the early days, in order to make the replenishment process more convenient, most operators did not adopt real person authentication or two-factor authentication.
How do SIM card fraud attacks steal your "money"?
We mentioned earlier how scammers can obtain cloned SIM cards. Scam assets are often one of the main targets of attackers. In today's payment environment and account security environment, 2FA verification is often achieved through SMS verification codes, which also depends on the more complete real-name system in China. After gaining control of another person's SIM card, the attacker can further obtain personal privacy information through a similar icloud or email. May I ask if your personal ID card or driver's license photo is stored in your phone? These photos or information may be silently submitted to your cloud storage account by a certain cloud software. After the attacker has completely collected this information, he can use it to extract your personal account assets; or simply use your identity information to obtain loans from multiple online loan agencies.
What's more frightening is that because most users save trouble or don't know basic security transaction knowledge, attackers don't need identity information at all. You only need a mobile phone number, SMS verification code and password to complete a series of steps such as transactions, withdrawals, and issuance.
If your phone suddenly has no signal in the environment and it lasts for a long time, you must be alert.
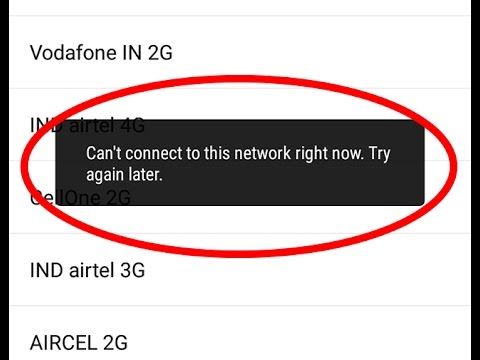
The picture above is a picture taken by a person while traveling in Brazil. The mobile phone suddenly lost the signal for about half an hour.
After multiple restarts to no avail, he contacted the local mobile operator before learning that the SIM card was reported as "lost or stolen" and asked the author to activate on another SIM card.
Earlier analog GSM standard SIM cards allowed the same mobile phone number to be connected to the Internet at the same time, so this technology was also used to catch primary three and spy applications in the early days. After subsequent upgrades of operators and networking standards, most mobile phone networks only allow the same SIM card to be connected and used at the same time. Therefore, multiple devices will not receive the same short message in China.
How to prevent SIM card fraud attacks?
1. Never use weak passwords
After the attacker obtains your SIM card, it is only one step to enter the password before the withdrawal. So if you use a weak password or a password related to personal information, the defense line will be broken in the end.
2. Try to choose a software APP that can realize device identification
In the current payment and transaction environment, part of the security protection has applied the IMEI identification technology. Every time a user logs in and trades, the system verifies that the current IMEI is a previously logged in device.
3. Important accounts use 2FA verification like Google Validator
Don't use SMS verification codes as your transaction 2FA verification!
Don't use SMS verification codes as your transaction 2FA verification!
Don't use SMS verification codes as your transaction 2FA verification!
4. Consider using a cold wallet as the last line of defense for "coins."
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Long Baitao Recommendation | First Deputy Governor of the Bank of France: Financial Inclusion in the Digital Age-How to Change the Status Quo?
- Policy “ripens” blockchain application, China's number of landed projects increased by 110% in November
- Research Report | The Status Quo of the Application of Blockchain in the Logistics Industry and the Three Challenges Facing the Landing
- Viewpoint | Rather than technological breakthroughs, asset chaining requires more institutional building
- IMF Liu Yan: Legal definition of digital currency is the basis of regulation
- 4D long text explains the latest development of Ethereum
- The Revolutionary Potential of the Bitcoin Lightning Network from the Internet





