Is a hardware wallet that uses Bluetooth to transfer data safe?
In August 2019, CVE (Common Vulnerabilities & Exposures, Common Vulnerabilities and Disclosures) updated a Bluetooth vulnerability KNOB (Key-Negotiation-of-Bluetooth) code-named CVE-2019-9506, with a CVSS score of 9.3. The vulnerability was discovered by researcher Daniele Antonioli of Singapore SUTD, Dr. Nils Ole Tippenhauer of CISPA, Germany, and Professor Kasper Rasmussen of University of Oxford, UK. The vulnerability spans the Bluetooth BR / EDR Bluetooth Core Specification versions 1.0 to 5.1, affecting more than 100,000 devices Bluetooth devices, including smartphones, laptops, IoT devices, and industrial equipment.
Many hardware wallets at home and abroad also use Bluetooth technology to complete the hot and cold side information transmission. So, does KNOB pose a threat to these hardware wallets?
- European Central Bank board member: Globally stablecoin untested, may trigger risks in multiple policy areas
- Opinion: Can blockchain really save the debt economy?
- High-quality asset shortage, four-step analysis of whether digital assets are independent of traditional market conditions

The KNOB vulnerability appeared during the entropy negotiation of traditional Bluetooth (BR / EDR) devices.
After research, it is found that the process of entropy negotiation uses the LMP protocol (Link Manager Protocol), which is neither encrypted nor verified, so it can be used for attack support and operation by OTA.
The specific process is as follows:
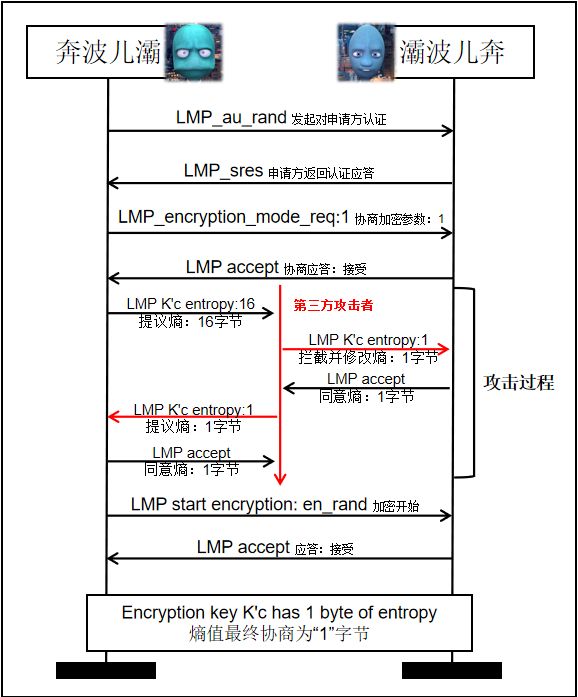
Let's summarize the necessary conditions for KNOB attacks:

After understanding the principle of KNOB, I personally believe that the Bluetooth hardware wallet is still relatively safe, because it is really difficult to meet the attack conditions .
However, like all wireless technologies, Bluetooth communication is vulnerable to a variety of threats. Because Bluetooth technology uses a variety of chipset, operating system, and physical device configurations, this involves a large number of different secure programming interfaces and default settings. These complications increase the likelihood and impact of Bluetooth attacks. Attacker k can use this vulnerability to monitor and manipulate data transmitted between two devices, which can lead to the leakage and tracking of personally identifiable and sensitive information.
Here are some suggestions for you:
1. Before purchasing a Bluetooth hardware wallet, confirm the Bluetooth type and version of the device, and avoid versions with a history of vulnerabilities;
2. Try not to use the Bluetooth hardware wallet in public places and crowded scenes;
3. When the device is not in use, please keep the Bluetooth function off;
4. You can consider a hardware wallet with two-dimensional code for data transmission, which is more secure and transparent.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Read the next wave of DeFi in one article: Security and Privacy
- Coinbase five-year veteran: how the excellent blockchain product "Koi" was made
- In-depth analysis: about the new Filecoin mining solution, you need to know these
- Ant S9 reached shutdown price. Earned 90 yuan a day, now it is 6 yuan.
- Despite the plummeting price, most Bitcoin investors lost less than $ 200
- What kind of organization is the "super ledger" scrambled by the tech giants?
- MIT Technology Review: Can Photonic Chips "Save" Bitcoin?






