PoS, DPoS, PBFT… Innovation consensus, PoW is outdated?
Is PoW obsolete in today's blockchain world, which is full of innovation consensus (PoS, DPoS, PBFT)? What is the future of PoW? Do you still want to do some consensus optimization and innovation work based on PoW?
We believe that PoW is still the core or foundation of other current consensus and has an irreplaceable position. Why do you say that? We try to see the connection between these consensuses.
Distributed consensus
Looking back at the history, Satoshi Nakamoto's PoW is not a continuation of the academic circle's research on distributed consensus. He did not know at first whether his own set of programs corresponds to an academic theme, but later, everyone thought that Nakamoto Satoshi The PoW is a solution that roughly gives a distributed consensus on the Byzantine environment. We have an academic perspective on PoW that can link PoW research issues with academic research on distributed consensus.
Speaking of distributed consensus, we have to say "FLP impossible" theorem: There is no deterministic consensus algorithm that can solve the consistency problem in a system that is reliable in the network but allows node failure (even if there is only one). . The paper "Impossibility of Distributed Consensus with One Faulty Process" , which proposed and proved the theorem, was published in 1985 by three scientists, Fischer, Lynch and Patterson. The revelation of this theorem is that the distributed consensus that we are now working on must be compromised in some respects.
- What does the wealth of the cryptocurrency field mean?
- Bloomberg: Bitcoin bull market pushes Asian encryption-related listed companies to rise
- Ernst & Young Blockchain Supervisor: Ethereum will be the largest blockchain, and 99% of cryptocurrencies face compliance issues
In fact, there are indeed two directions for compromise, one is to compromise on asynchronous, and the other is to compromise on certainty.
The so-called compromise of asynchronous is to set the timeout mechanism, thinking that the message will not be infinitely delayed. The DLS algorithm ( "Consensus in the presence of partial synchronization" ) and the PBFT algorithm ( Practical Byzantine Fault Tolerance ) are both solutions in this direction. Furthermore, the DLS paper reveals two goals of asynchronous consensus in the Byzantine environment: security (consistency) and activity (availability), both of which make synchronization assumptions for activity rather than security. Sexuality makes the synchronization hypothesis that if the real environment does not satisfy the synchronization hypothesis, it will only cause usability problems and will not cause consistency problems. That's why we often say that PBFT is a consensus algorithm that prioritizes usability over availability.
The so-called compromise of certainty is the new world introduced by Nakamoto, and certainty is probabilistic. In this direction, through the proof of workload, block rewards, peer-to-peer networks jointly construct a probabilistically secure consensus scheme. It seems that on the map, the Nakamoto consensus is only one of the compromises of the asynchronous Byzantine consensus problem defined by consensus researchers, but the introduction of probability certainty not only solves the traditional asynchronous Byzantine problem, but also solves a bigger problem. : Allows any number of nodes to participate in the system in an open manner, and no participant has to know the complete set of participants. This is very remarkable, and this is the environment that the public chain system really faces. In practice, the Nakamoto consensus on compromising certainty has achieved great success.
The innovative public-chain consensus mechanism is nothing more than the two compromise directions. Some of them are introduced below.
Compromise analysis of different consensus
PoS
Pos is essentially a PoW and compromises certainty. Staking can be regarded as a barrier to entry. By increasing the threshold, the size of the participant set is reduced. The smaller participant set size has two advantages: 1. The total workload of the entire system will be reduced, and the energy consumption will be reduced; Asynchronous communication networks are smaller in scale and are less likely to be delayed due to partitioning, and smaller inter-blocking intervals can be set. This is why PoS says its TPS is higher and more energy efficient.
DPoS+PBFT
DPoS+PBFT is of course PBFT in nature, which is a compromise for asynchronous. The purpose of DPoS is to select a set of participants who can apply the PBFT algorithm among the open public chain participants. This set satisfies three conditions: 1. The scale is small enough, otherwise the traffic is huge; 2. The total number of sets is determined. It is an asynchronous consensus problem that PBFT can solve; 3. The number of malicious participants (Byzantine nodes) is less than 1/3. The Staking mechanism plays two roles in it: 1. Screening users as thresholds; 2. As an incentive mechanism to reduce the proportion of malicious nodes.
Tetris
Tetris is a knowledge-based consensus algorithm pioneered by YeeCo. It is essentially BFT and compromises asynchronous. Tetris itself is a solution to the standard Byzantine problem, with a focus on its high performance and proven security. Its BFT participant set is selected through a pluggable upper layer protocol, PoW, DPoS, VRF, etc.
Algorand
Algorand is essentially a BFT that compromises asynchronous. Algorand chooses a set of participants that can apply the BFT algorithm in a very special and ingenious way, using VRF (verifiable random function), similar to each participant owning a lottery device, you can know yourself without communicating with other participants. Whether it is selected or not seems to be very energy efficient, but there are a few issues to solve: 1. Need to set a threshold for the participants, because the cost of creating a private key that can participate in the network is very low, in fact Algorand according to the participants The balance is given a weight; 2. The lottery needs to set the winning rate, and the total number of participants needs to be known. This is a consensus problem in itself. Algorand tries to reach the online balance and the total system balance by rewarding the nodes online. The number of participants can be reversed. This is in fact a Byzantine fault-tolerant system that requires an online and honest balance of >2/3.
DAG
DAG (Directed Acyclic Graph), whether it is an IOTA with a transaction as the vertices of the graph or Conflux with the vertices of the graph as a graph, still works on the PoW, compromising the certainty. If the previous consensus is to avoid forks, then DAG is to control the fork to a certain level, thereby improving the system's TPS. The essence of DAG is proof of workload, but the principle of the longest chain has been changed to the most difficult principle of structure.
PoW is the kernel or foundation
We will summarize the model of consensus, as shown below: 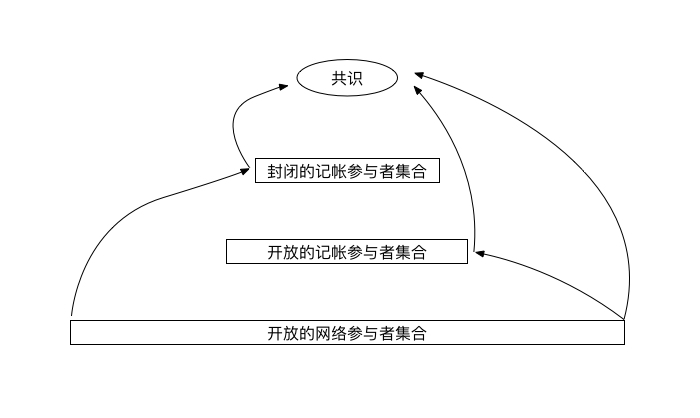
The difference in the consensus mechanism is actually the difference in the path from "open network participant set" to "consensus". For example, directly from "open network participant set" to "consensus", that is PoW; first to "open billing participant set" to "consensus", that is, PoS; first to "closed billing participant The collection "re-to" consensus, that is X+BFT, X wants to see what the "closed billing participant set" takes, which can be either DPoS or VRF.
It can be seen that so many consensus algorithms do not invent too many new things. As long as a consensus is formed from an "open participant set" (node free entry and exit), this mode can only be adopted: the node is motivated in a probability Based on the deterministic consensus results, the consensus results will continue to be established, which is the consensus of Nakamoto.
The significance of PoW's consensus on current innovation lies in two points:
- If the consensus involves forming a consensus from an "open participant set" (node free entry and exit), then it is essentially the Nakamoto consensus, which is the "core that is still the kernel or foundation of other current consensus". ";
- If the consensus involves turning the "open participant set" into a "closed participant set", then the Staking mechanism is still needed. Where does the value consensus of Staking come from? Still passed from the PoW chain. This is the "foundation" in the previous "PoW is still the core or foundation of other current consensus";
The essential advantages of PoW
PoW supporters have given many of the qualitative advantages of PoW, such as nature, credibility, and purity. Regarding energy consumption, some people think that this is the shortcoming of PoW, and some people think that the cost price is the cornerstone of security.
Let's talk about the essential advantages of PoW in my eyes:
Consensus openness
PoW is designed for an open set of participants. This openness (the instability of the set of participants) is always challenging the achievement of consensus, whether it is the earliest cold start, or the occurrence of the mine pool, the emergence of ASIC mine Machine, currency price fluctuations, difficulty ups and downs.
PoW has adopted an extremely simple mechanism to solve open problems . PoW does not need to patch any of the scenarios, any stage, do any governance, always rely on its core mechanism to drive the entire system to run, and has withstood the test of time. In our concept, some systems grasp the essence, ingenious and simple, and adapt very strongly, and some systems are full of compensation mechanisms, constantly changing with the changes of the environment, PoW is the outstanding representative of the former.
PoW is the Permissionless system for bottoming . At any time, the computing power can enter the market and compete with the existing computing power at the same starting line. Staking input and computing power look very similar, but in the game environment, the difference in parameters of the starting point will result in a completely different pattern. If the blockchain system is a system that is easy to fall into the "Matthew effect", PoW's external entity computing power is an important parameter to resist this effect. On the one hand, the hysteresis adjustment mechanism increases the system's entry into the steady state. On the other hand, the external entity computing power has better independence than Staking. The positive feedback of the consensus advantage of PoW to the business advantage is one-way, and the positive feedback of the consensus advantage of Staking in the business advantage is two-way.
The ultimate in consensus security
Consensus is often talked about security issues such as 51% attacks, more than 1/3 Byzantine nodes, all under consensus rules, and the blockchain system is ultimately a system running on a physical network, compared to Under the consensus rule, the attack at the physical network level is the reduction of the dimensionality of the blockchain system.
The pervasive PoW believes that the weight of a node should not be determined by the virtual resource (Staking), but should be determined by the physical resource (power calculation).
The former is easy to fall into the continuous investment of virtual resources, but the growth of network node size does not have enough driving force, that is, the economic scale of the system and its resistance to threats from the network are not matched, and there is no endogenous The mechanism promotes matching.
The latter's resource input corresponds to the input of the network discourse right. The initial calculation power input is to invest more nodes. Later, the professional mining machine and the mining pool appeared, and the calculation power and the node do not match exactly. The situation, but since the investing power is invested, people will definitely take measures to get the corresponding network voice, and the economic scale of the system and its resistance to threats from the network are matched. Node weights The more virtual resources are considered, the greater the difference between the voice rights of the nodes in the system and the voice rights in the physical network, regardless of the PoW of the virtual resources, the voice of the nodes in the system and the physical network. The right to speak is the same. The security of PoW is reflected here, and the root of the cost cost to support security lies in the physical network environment.
"Consensus openness" and "consensus security" are familiar. They are "blockchain impossible triangles" (that is, they cannot achieve both Scalability, Decentralization, and Security). Security), the three can only get the two corners of the second).
The essential advantage of PoW is that it provides a highly decentralized, highly secure consensus mechanism. And scalability, it is the direction of the PoW consensus needs to develop and innovate.
Author: YeeCo, Babbitt authorized reprint information
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Is the Morgan coin finally coming? JPMorgan Chase announced that it will start trial operation as early as this year
- Iranian Ministry of Energy official: involved in bitcoin mining or power outage
- False websites open Libra pre-sales, fraudsters receive IQ tax
- Blockchain is an unstoppable trend, and optimists are more likely to see the future
- A solution to the problem of eclipse attack in Ethereum
- The world influence of Libra and China's countermeasures
- Research report | Bitcoin bull market really came? In fact, FOMO emotions are far from being ignited.






