Research | Data Compliance, Reptile Technology Interprets Legal Issues
The rapid development of big data, cloud computing, artificial intelligence and other fields has made the call for strengthening personal information protection constantly rising. At a deeper level, the protection of personal information involves not only the protection of individual basic rights, but also the industrial development, national strategy, national security and many other issues.
For enterprises, the situation of data compliance work is urgent and has a long way to go. With increasingly stringent regulations and possible criminal sanctions, data compliance efforts are urgently needed.
For the blockchain industry, what kind of legal problems will the public trust that has been caught in the data storm? What inspiration can we give us?
Recently, a video of the seized office of Gongxinbao (Hangzhou Chuangxin Data Technology Co., Ltd.) was circulated on the Internet, and many media in the industry verified it. The matter was confirmed to be true.
- Swiss FINMA issued a guide to the stable currency, proposing Libra to obtain the necessary conditions for payment of the license
- Close the back door of the transaction, Zcash is the biggest defect or is solved due to this program
- What kind of consensus algorithm do we need?
According to public information, the public credit chain GXChain is a basic chain for the global data economy, designed to create a value network of trusted data. Gongxinbao will use the blockchain technology to play a decentralized platform to connect data buyers and sellers. When the buyer needs data, it will broadcast to the whole network through blockchain technology, and the data source will query its own offline database. If there is relevant data, the smart contract transaction is carried out, and if not, no subsequent operations are performed.
Some insiders told the media that the reason for the investigation of the public trust was not related to the blockchain business. Some analysts believe that the big probability is because of "data", not because of "blockchain and currency." Including the previous data for online loans, crawling data, data, and purchasing black data. The well-known risk control data provider, Capricorn Technology and Xinyan Technology, was taken away by the police and included konjac, shield, and new face. , Tianji, Juxin Li, etc. have stopped the crawler service actively or passively.
In a 2018 product price service list exposed by the media, Gongxinbao introduced its reptile data types including Social Security, Xuexin.com, Jingdong, Telecom, China Mobile, China Unicom, Zhilian Recruitment, Sesame Credit, WeChat, Alipay. Even people's credit data, etc. (The above content comes from the Planet Daily, Golden Finance and other media)
According to public information, Hangzhou Chuangxin Data Technology Co., Ltd.'s business scope includes data processing technology, blockchain technology, etc. In addition to Huang Minqiang, its shareholders include Li Xiaolai and Zhenge Fund.
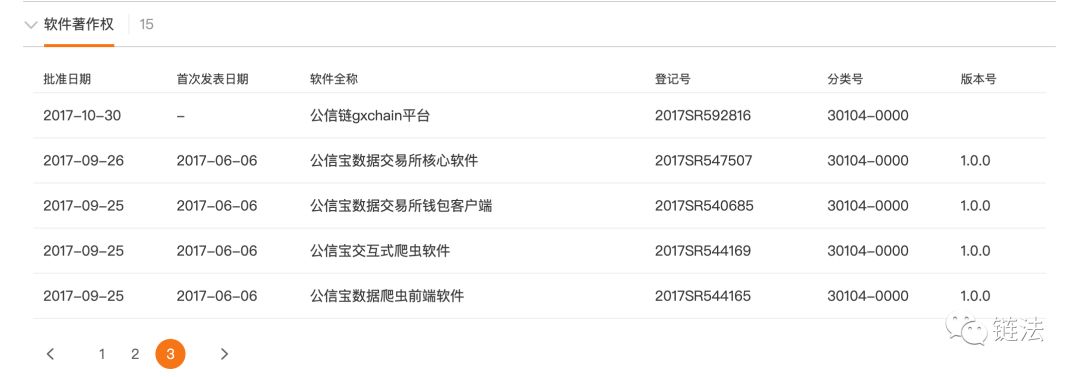
At a glance at its software copyrights, crawler software is on the list.
Vaguely remember, in 2018, the best article written in the industry called the blockchain, it was mentioned that big data is easy to do evil, and the emergence of blockchain technology may help the Internet to falsify the truth and return to its original. The meaning of decentralized equality. The public letter with the slogan "Be the master of your own data", because of the data problems encountered Waterloo, people are embarrassed.
If the incident is not related to the blockchain as speculated, but it is planted on the "data", it cannot be said that it is "caused by the wind."
The rapid development of big data, cloud computing, artificial intelligence and other fields has made the call for strengthening personal information protection rise again. At a deeper level, the protection of personal information involves not only the protection of individual basic rights, but also the industrial development, national strategy, national security and many other issues.
It should be emphasized that the reptile itself is not legally prohibited, but there is a certain legal risk in using reptile technology to obtain data. Malicious reptiles face various legal issues, including copyright infringement, infringement of trade secrets, infringement of personal privacy and personal information, constituting unfair competition, and serious intrusion into computer systems, which also constitute a criminal offence.
In fact, the research and protection of personal information has long been a hot topic of justice and has been included in the national legislative plan.
What is the legal definition of “personal information”?
On August 22, 2019, the draft of the Civil Code's personality right was reviewed for the third time at the Twelfth Session of the Standing Committee of the 13th National People's Congress. The draft of the second draft has specific provisions on the definition of personal information: the scope of personal information includes the name of the natural person, date of birth, ID number, personal biometric information, address, telephone number, etc. The draft three-review draft incorporates the natural person's "e-mail address" and "whereabouts" into the scope of personal information on the basis of the definition of personal information in the second-instance draft.
In addition, in order to strengthen the protection of personal information, the draft three review drafts modify the “use” of personal information to “process” personal information, and add provisions: the processing of personal information includes the use, processing, transmission, provision, disclosure, etc. of personal information. . In order to cover as much as possible the various aspects of personal information protection.
In academia, there is a basic consensus on the definition of personal information: personal information refers to all information that can identify a specific individual, individually or in combination, including name, gender, age, weight, file, medical record, income, family. Address, telephone number, car engine number, computer serial number, even walking routes, spending habits, Internet browsing records, etc. The most basic feature of personal information is that it is recognizable, whether it is direct or indirect, single information or combined information, as long as it can determine the information of a particular individual, that is, it belongs to personal information.
If understood semantically, personal information is all information related to natural persons.
If the public letter treasure is suspected by the outside world, what kind of legal responsibility will it face?
In violation of the relevant provisions on the protection of personal information, its legal liability may include civil, administrative and criminal liability.
civil liability
The illegal disclosure of personal information may constitute personal rights violations such as personal privacy or reputation rights, and shall bear corresponding civil liabilities (mainly including compensation for losses, apology, elimination of influence and restoration of reputation, etc.). The legal basis is "People's Republic of China". The Tort Liability Law and the Provisions of the Supreme People's Court on Several Issues Concerning the Application of Law in the Trial of Civil Disputes over the Use of Information Networks for Personal Rights and Interests.
Administrative responsibility
If the relevant personal information protection regulations are violated, the relevant government authorities (such as the Ministry of Industry and Information Technology) may order corrections within a time limit, warnings, fines, confiscation of illegal income, revocation of licenses or cancellation of records, closure of websites, prohibition of responsible personnel from engaging in network services, etc. Administrative punishments can also be recorded in social credit files and published.
criminal responsibility
Article 7 of the "Amendment of the Criminal Law of the People's Republic of China (VII)": Add one after Article 253 of the Criminal Law as one of the 253rd: "State organs or finance, telecommunications, transportation The staff of the units such as education, medical care, etc., in violation of state regulations, sell or illegally provide personal information obtained by the unit in the course of performing their duties or providing services. If the circumstances are serious, they shall be sentenced to fixed-term imprisonment of not more than three years or criminal detention. , or a single penalty.
"Stealing or illegally obtaining the above information in other ways. If the circumstances are serious, it shall be punished in accordance with the provisions of the preceding paragraph.
"If the unit commits the first two crimes, it shall impose a fine on the unit, and the person in charge directly responsible for it and other directly responsible personnel shall be punished in accordance with the provisions of each paragraph."
It can be seen that Amendment VII has a limited scope for the sale or illegal provision of personal information, and the penalty is relatively light, which cannot effectively curb illegal activities and illegal disclosure of personal information.
Article 17 of the Criminal Law Amendment (IX) of the People's Republic of China promulgated on November 1, 2015 stipulates that one of Article 253 of the Criminal Law shall be amended to read: “Prohibition of the relevant provisions of the State and sale to others Or provide citizens with personal information. If the circumstances are serious, they shall be sentenced to fixed-term imprisonment of not more than three years or criminal detention, and shall be punished with a single penalty. If the circumstances are particularly serious, they shall be sentenced to fixed-term imprisonment of not less than three years and not more than seven years, and fined.
"In case of violation of relevant state regulations, the personal information of citizens obtained in the course of performing their duties or providing services shall be sold or provided to others, and shall be severely punished in accordance with the provisions of the preceding paragraph.
"If you steal or otherwise illegally obtain personal information of a citizen, you shall be punished in accordance with the provisions of the first paragraph.
"If a unit commits the first three crimes, it shall impose a fine on the unit, and the person in charge directly responsible for it and other directly responsible personnel shall be punished in accordance with the provisions of each paragraph."
In addition, in the notice of the Ministry of Public Security and the Ministry of Public Security on punishing criminal activities against citizens’ personal information according to law:
At present, some criminals have gradually used the Internet to resell citizens' personal information in pursuit of illegal interests, and have gradually formed a huge "underground industry" and black interest chain. The personal information of citizens who buy or sell includes household registration, banking, and telecommunications account information, and covers all aspects of the citizen's personal life. Some state organs and financial, telecommunications, transportation, education, medical and property companies, real estate agencies, insurance, express delivery and other enterprises and institutions will sell or illegally provide personal information obtained during the performance of duties or service. Give it to others.
Intermediaries who obtain information build data platforms on the Internet and sell information for huge profits. According to this information, illegal investigation companies engage in illegal criminal activities such as illegal debt collection, fraud and extortion. Such crimes not only endanger the information security of citizens, but also easily lead to a variety of crimes, which become the root cause of information crimes such as telecom fraud, cyber fraud and nuisance-type “soft violence”, and even crimes such as kidnapping, extortion, and violent debt collection. The combination of activities affects the sense of security of the people and threatens social harmony and stability.
Legislative status of personal information protection
Generally speaking, there is no unified personal information protection law in China, and the provisions on personal information protection are scattered in laws, regulations, rules and judicial interpretations.
But in recent days, legal regulations related to personal information and data compliance have entered the legislative fast lane.
For example, "Children's Personal Information Network Protection Regulations", "Information Security Technology Mobile Internet Application (App) Collecting Personal Information Basic Specification (Draft)", "Data Security Management Measures", "Personal Information Exit Safety Assessment Method", "Personal Information Security Specification", "Data Safety Management Measures, "Apps for illegal use of personal information collection methods (draft for comments)".
In addition, on April 10, 2019, the Network Security and Protection Bureau of the Ministry of Public Security, the Beijing Network Industry Association, and the Third Institute of the Ministry of Public Security jointly issued the "Guidelines for the Protection of Internet Personal Information Security."
Case-driven rule of law
On a case-by-case basis, Xu Yuyu, who was sensationalized throughout the country and was selected as one of the “Top Ten Cases of Promoting the Rule of Law in 2017”, was born into a telecom fraud case that gave birth to the provisions on the protection of personal information in the General Principles of Civil Law. Some people referred to it as “Xu Yuyu”. Article: Article 111 of the General Principles of the Civil Law stipulates that "the personal information of natural persons is protected by law. Any organization or individual who needs to obtain personal information of others shall obtain and ensure the security of the information according to law, and shall not illegally collect and use it. Processing and transmitting personal information of others, and not illegally buying, selling, or publicizing other people's personal information."
How do companies do their personal information protection compliance?
It should be emphasized that for enterprises, the data compliance work situation is urgent and has a long way to go. With increasingly stringent regulations and possible criminal sanctions, especially for data companies, data compliance efforts must be both depth and breadth.
In the vertical direction, it is necessary to make the data source legal and the data use legal. If the data is out of the country, it is also necessary to leave the country legal. In the horizontal direction, it is necessary to ensure the security of data and the corresponding risk prevention and control work.
The development of compliance work must be institutionalized, regularized, and systematic. Enterprises should establish and improve the compliance system and compliance system related to network security and data protection, including the establishment of compliance procedures and the corresponding manpower.
For companies in many blockchain industries, such as agreeing and collecting the scope of users' personal information and the corresponding privacy policy drafting, for example, to understand what data is required by the policy to be stored only in China? This requires companies to review user data and form a corresponding review mechanism. For example, when a wallet enterprise involves payment services, it is necessary to avoid storing user information in an overseas server.
In addition, in view of the current tightening of the regulatory trend of personal information protection in China, new laws and regulations are constantly being introduced. Enterprises involved in data need to closely follow the progress of laws and legislative developments, and ensure that measures for handling personal information comply with relevant laws. Requirements. For the enterprise data compliance, the chain lawyer team will also introduce the chapters in the following articles in detail, and interested readers should keep their attention.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Liang Xinjun: In the next fifteen years, blockchain restructures social production relations
- Encrypted synthetic assets DIY era is coming, UMA brings DeFi new explosion point?
- It’s better to chase the wind than to create the wind – to pay tribute to the participants in the Ant Blockchain Innovation Competition
- Babbitt Column | Cai Kailong: Is Bitcoin a safe haven asset?
- Babbitt column | "Privacy-transparency" binary paradox is broken, blockchain positioning faces crossroads
- EOS daily support appears, but it also needs to pay attention to the market dynamics
- HKEx's merger and acquisition of the Stock Exchange clearly entered the digital asset trading, impacting the existing pattern






