Research | Domestic encryption algorithm combat government affairs alliance chain Can they replace mainstream public chain algorithms?
Recently, the research on the autonomous and controllable system of blockchain has become a hotspot for many institutions. Consensus Wang Maolu published a paper in "Information Security and Communication Secrecy" to study the state secret substitution of blockchain.
The construction of the government affairs chain based on the business secret system mainly includes the following aspects: ① the identity authentication mechanism based on the business secret system; ② key security measures based on the business secret system; ③ information security guidelines based on the business secret system; ④ business secret based System data verification method; ⑤ Privacy protection level based on the confidentiality system; ⑥ Data storage specifications based on the confidentiality system; ⑦ Hardware support system based on the confidentiality system.
The focus of the government affairs chain serving a wide range of domestic government affairs areas is to ensure support for the business secret series of algorithms at the security level. At present, the hash algorithm is widely used in the proof of work of the blockchain. Each innovative blockchain project has its own different implementation, which is a relatively core and basic technology in the blockchain. The main asymmetric encryption algorithm in the mainstream public chain mainly adopts the RSA algorithm, and the following mainly demonstrates the confidentiality alternative of these two algorithms.
In order to ensure the security of commercial passwords, the Commercial Password Management Office of the State Password Administration has formulated a series of password standards, including SM1 (SCB2), SM2, SM3, SM4, SM7, SM9, Zuchong's Password Algorithm (ZUC), and so on. Among them, SM1, SM4, SM7, and Zu Chong's password (ZUC) are symmetric algorithms; SM2, SM9 are asymmetric algorithms; SM3 is a hash algorithm. At present, these algorithms have been widely used in various fields, and it is expected that one day, blockchain applications using commercial algorithms will appear. The SM1 and SM7 algorithms are not public. When calling this algorithm, it needs to be called through the interface of the encryption chip.
- Viewpoint | Promoting the modernization of national governance system and governance capabilities
- In 2019, the U.S. Congress frequently moves. What impact will the two crypto-related bills it proposes have?
- Trend prediction: upcoming events in 2020
Digest algorithm using SM3 in the business secret system as the government chain
Blockchain can be used to register and issue digital assets, points, etc., and transfer, pay and trade in a point-to-point manner. Due to the high network latency in a point-to-point network, the order of transactions observed by each node cannot be exactly the same. Therefore, the blockchain system needs to design a mechanism to agree on the sequence of transactions that occur in a similar time. This algorithm that reaches a consensus on the sequence of transactions within a time window is called a "consensus mechanism".
Existing consensus mechanisms include Pow, Pos, and DPos, among which Pow is the most secure public chain consensus algorithm. The existing Bitcoin uses the Pow consensus algorithm chip. In the Bitcoin system, miners must perform and complete the proof of work process in order to mine new Blocks (data blocks). The miner calculates the SHA256 value (a type of HASH value) of the header information of each data block. If it is smaller than the SHA256 value of the previous data block, the P2P network will accept the new data block. At present, Bitcoin has attracted most of the world's computing power. Other blockchain applications that use the Pow consensus mechanism are difficult to obtain the same computing power to ensure security.
Based on the investigation of various domestic and international consensus mechanisms and consensus algorithm chips, the SM3 consensus algorithm is studied. The algorithm flow is shown in Figure 1. The SM3 password digest algorithm is a Chinese commercial password hash algorithm standard published by the National Password Administration's Commercial Password Management Office in 2010. The SM3 algorithm is an improved algorithm based on SHA256. It uses the MerkleDamgard structure. The message packet length is 512 bits and the digest value length. It is 256 bits. This algorithm generates a 256-bit hash value for a message with an input length less than 2 to the power of 64 to the power of 64, using XOR, modulo, modulo addition, shift, AND, OR, NOT operation. , Consisting of padding, iterative processes, message expansion and compression functions. The compression function of the SM3 cryptographic hash algorithm has a similar structure to the compression function of SHA256, but the structure of the compression function of the SM3 algorithm and the design of the message expansion process are more complicated. Each round of the compression function uses 2 message words. Message expansion Each round of the process uses 5 message words, etc. Based on the SM3 consensus algorithm chip to ensure higher security, at the same time, because the SM3 algorithm is similar to the SHA256 algorithm structure, it can use a unified processing model with the HASH256 chip, but it is designed separately for each computing unit to effectively save resources . The SM3 cryptographic hash (hash, hash) algorithm is suitable for digital signature and verification in commercial cryptographic applications, the generation and verification of message authentication codes, and the generation of random numbers, which can meet the security requirements of various cryptographic applications.
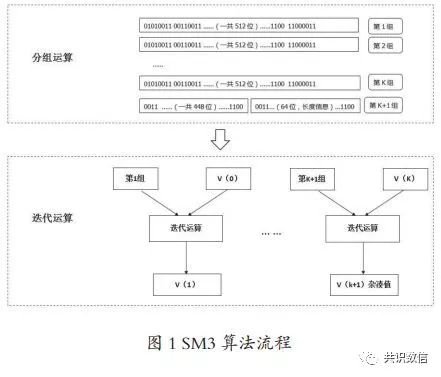
The government chain uses the SM3 hash algorithm for digest calculation. Because SM3 is an improved implementation of SHA-256, although the compression function of SM3 algorithm and SHA-256 compression function have similar structure, the design of SM3 algorithm More complex and relatively secure.
Digital signature algorithm using SM2 in the business secret system as the government chain
The traditional blockchain uses multi-signature technology. This is to better protect the rights of both parties to the transaction. The address of a multi-signature transaction can have multiple associated private keys. The most common is a 2/3 combination, the so-called 2/3 It means that the address of a multi-signature transaction can have three associated private keys, and the trader needs two of them to complete a transfer. The biggest benefit that the multi-signature technology can bring is to ensure the security of the transaction. Multiple parties to the transaction can see the secure storage of the funds. Only when both parties agree, the funds can be transferred and the rights of the parties to the transaction are guaranteed. However, the existing multi-signature transactions are not necessarily secure. Currently, multi-signature wallets appear as client web applications. If an attacker controls the server of the trading platform, they will be able to deliver the wrong web application to users. The signature scheme does not provide the security guarantee that multi-signature should have. The scheme provider plays the role of client and server in the protocol.
Based on the investigation of domestic and foreign blockchain technology and blockchain transaction methods, the research determined a multi-signature transaction method based on SM2 in the business secret system. The SM2 algorithm was released on December 17, 2010 by the State Cryptographic Administration, and is called an elliptic curve algorithm. The algorithm encryption and decryption process is shown in Figure 2. The security of the SM2 algorithm is based on the mathematical problem "discrete logarithm problem". When using the SM2 algorithm for digital signatures, the required key length is shorter than the previous RSA. The multi-signature transaction method based on the SM2 algorithm not only makes it easier for users and trading platforms to memorize and store keys, accelerates the verification rate, and ensures that transactions are not affected by one party, that is, the rights of buyers and sellers are guaranteed, and the platform cannot misappropriate transaction funds. , And the outside can not compromise the economic security of the public chain by attacking the server.
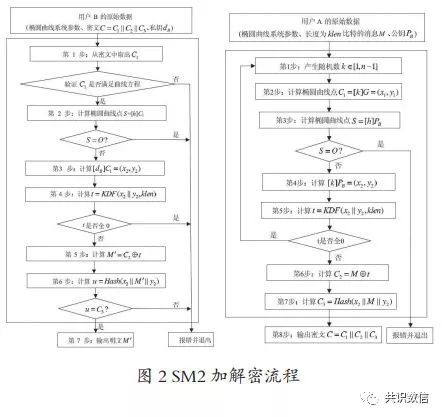
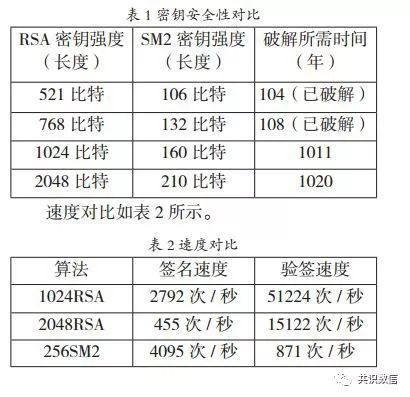
The government chain uses the SM2 elliptic curve algorithm to generate the public and private key pairs of the blockchain and verify the signature, making its own computational complexity completely exponential, and compared with the RSA used in the traditional blockchain, the same Under the security performance, the required number of public keys is less, and the speed of key generation and encryption and decryption is more than 100 times faster than that of the RSA algorithm. The SM2 algorithm is superior to the RSA algorithm in many respects (RSA developed early and is widely used, and SM2 is also a natural leader). Table 1 shows the security comparison with RSA.
The elliptic curve asymmetric encryption algorithm used for the public-private key pair on the chain is SM2, and the hash hash algorithm used in the distributed ledger bookkeeping of the blockchain is SM3. Through the encryption method of China's independent intellectual property rights, the effective guarantee of data security on the chain has been achieved. Therefore, the government chain can be used as a built-in security guarantee mechanism of the data exchange system and an important function of a third-party security authentication platform. While providing encryption guarantee for data information exchange and transmission, it also provides authentication, authorization, anti-tampering and traceability to the data itself. Contour security guarantee. Secret system-based government affairs chain integration and sharing exchange applications provide tag on-chain. Through the storage and preservation of data tags, the total data exchange, current running status, transmission line status, data exchange process status, and exchange of each node can be maintained. Service status, etc. can be effectively monitored and traced, and specific data exchange packets can be queried and counted according to items such as in / out, destination / source, and amount of data within a specified time; data status (such as waiting for exchange) , Being exchanged, exchange completed, receipt received, processing interrupted, etc.), tracking the status of a certain specified data.
Conclusion
The government chain can play the technical characteristics of blockchain in industries such as food anti-counterfeiting traceability, financial fund auditing, insurance traceability, lottery certification and other industries. It can be used as a technical framework to solve the market demand between government and industry. In addition to cryptography itself, the construction of the government affairs chain based on the business secret system can also provide applications with rich permission policies, security key management systems, and user privacy protection solutions, thereby ensuring the security of data on the chain as a whole. When the government affairs at all levels develops the application of the government affairs chain in the area of blockchain security, government affairs big data sharing exchanges will gradually be on the chain and personal identity information will be on the chain. Therefore, credible government affairs chain standards for government affairs are particularly urgent. One needs the government and industry regulators to jointly study and promote the direction.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Ten important advances in cryptocurrency in 2019
- Blockchain practitioners: 2019 is too difficult for me
- SheKnows Year-end Ultimate Debate | Can Big Companies Get Into the Start?
- In Nordic Blockchain Week, I felt the power of the winter
- The market segment suitable for blockchain should have these seven attributes
- Lighthouse: Lessons Learned from Testnet Collapse
- Will there be "explosive applications" for blockchain in the future?





