The phone suddenly has no signal, but it is a precursor to the theft of 100,000 US dollars of encrypted assets.
Guide: One day, the $100,000 worth of crypto assets in the Coinbase account is gone! Bitco's engineering director Sean Coonce thought that just because the phone was accidentally dropped, the SIM failure lost the mobile service. It was not expected that this was a signal of hacking money.
Last Wednesday, I lost a cryptocurrency worth $100,000. The money disappeared from my Coinbase account in a single day due to a "SIM card transfer attack."
It has been several days since this happened, and I am very depressed. I don’t know how to eat, I can’t sleep at night, I feel that I am immersed in anxiety, regret and embarrassment.
This is the most expensive lesson in my life. I want to share the lessons I have learned from this incident with as many people as possible, and hope to enhance your understanding of this type of SIM card attack and strengthen your online identity. Security.
- "Safety Blockchain White Paper" was launched, and blockchain application was implemented in 14 scenarios.
- Industry blockchain one week news | China's blockchain enterprises have reached 672, the industry scale exceeds 1 billion yuan
- Xiao Lei: I thought of Huawei and Bitcoin from the American occupation of all human scientific and technological achievements.
01 attack details
You may ask a question first, what exactly is a " SIM card transfer attack "? In order to understand the reason for the attack, you need to look at the typical online authentication. For most people, the picture below should look familiar:
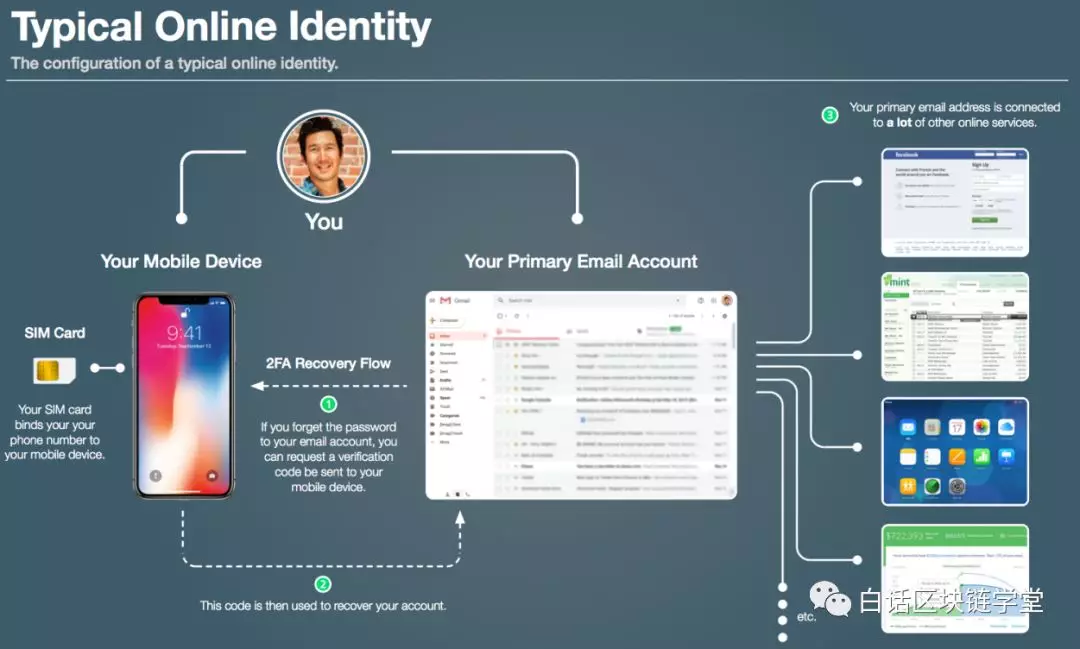
• The SIM card in our mobile phone binds the mobile phone number to the mobile phone; • When we forget the login password of the email account, we can ask the email to send a verification code to your mobile phone. This verification code will be used to recover you. Email account; • Our email address is bundled with many online services.
1. Authorized SIM transfer
Allowing users to transfer SIM cards to another device is a service provided by mobile operators. This service allows users to transfer their phone number to a new device. In most cases, this happens when we have a new phone or if we want to change a mobile operator, which is a perfectly legal requirement.
2, SIM card transfer attack
However, a "SIM transfer attack" is a malicious transfer performed by an unauthorized attacker . The attacker transferred your SIM card to the phone they controlled. The attacker then initiates a password reset process on your email account. The verification code will be sent from your email provider to your phone number, and the attacker will intercept the phone number because they now control your SIM card.
The following diagram provides a step-by-step overview of the attack process:
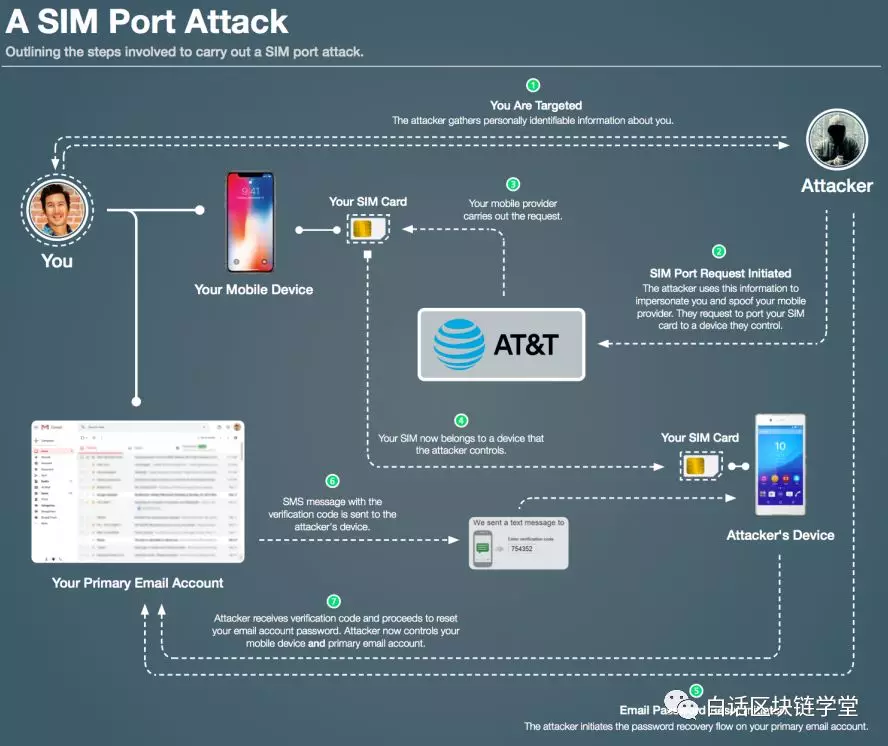
• First, the attacker will collect your personal information and lock you into the target of the attack; • Start the SIM transfer request, use the collected personal information to prove to the mobile service provider that you initiated the application, and ask the mobile service provider to Transfer your SIM card to a device controlled by them; • Your SIM is now transferred to a device controlled by the attacker; • Reset the mailbox password and wait for the mailbox to send the verification code to their phone; The mailbox sends the verification code to the attacker's mobile phone via SMS; • The attacker gets the verification code and starts resetting your email password, now they have control of your mobile phone and email.
Once the attacker controls your email account, they will begin to gradually control any online services (such as bank accounts, social media accounts, etc.) that you manage through the email that are beneficial to them. If they do it too much, they can even lock your account and you can't do anything about it.
Here, let's take a moment to sort out a lot of personal sensitive information that you bind through a Google account:
• Your address, date of birth and other personally identifiable information; • Have access to photos of you or your partner; • Access your schedule and recent travel itinerary; • Access your private email, documents and historical search Record; • Get your contact list, their private information and the relationships between you; • Get all the other online services you use as your source of authentication.
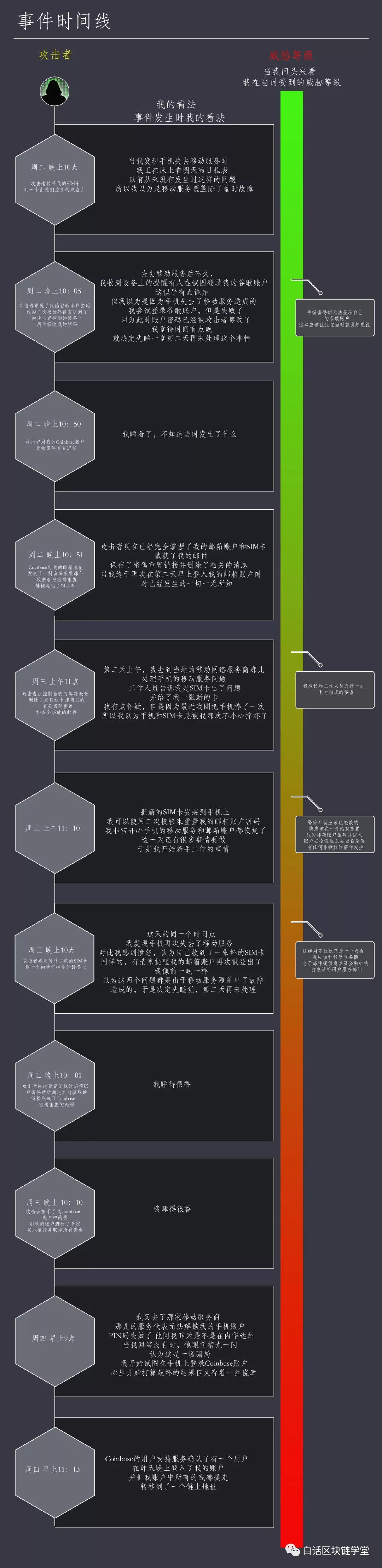
02 Timeline of this attack
Through the above, I believe that you have a certain understanding of how the attacker can carry out such SIM card transfer attacks and the consequences of the attack.
Below, I will tell you in detail about the attack process: how the attack was initiated, my experience during the attack, and what you can do to protect yourself in case of similar situations.
The timeline of the attack can be divided into four parts:
1. What I have experienced: In my opinion, these things that I have experienced or if you encounter similar things are clear indicators that you may be attacked.
2. What the attacker was doing at the time: the strategy used by the hacker to sneak into my Coinbase account.
3. The level of threat I feel: the level of threat I feel when these events occur.
4. The level of threat I should have: I want to come afterwards. When these things happen, I want to have the level of threat I have.
03 Lessons and recommendations
This is the most expensive lesson in my life. I have forever lost this net worth that is significant to me in a single day.
Here are some suggestions for how to strengthen my protective measures:
1. Use your hardware wallet to protect your password: Whenever you are not trading, save your password in a hardware wallet/offline wallet/ multi-signature wallet instead of leaving the funds idle on the trading platform.
I treat Coinbase as a bank account and there is no reparable measure in the event of an attack. Although I know more about the risk of putting money on the trading platform than most people, I never thought that this would happen to me. I am very sorry now that I have not taken stronger security measures against my cryptocurrency.
2. Secondary verification based on SMS service is not safe enough : Whether you want to protect online assets or online identity, please use some hardware equipment to enhance protection. In this way, in order to carry out the attack, the attacker must obtain the equipment for storing the password in real life.
Google Authenticator and Authy can turn your mobile device into such hardware to improve security, but I suggest you go one step further: choose a Yubikey (a small USB that you can actually control without being spoofed by an attacker) device).
3. Reduce your online presence: Suppress the urge to share personally identifiable information online (eg, your date of birth, address, pictures with geographic location information, etc.). In the event of an attack, all such publicly available data information may be used as a tool to launch an attack.
4. Google's voice secondary verification : In some cases, online services do not support hardware-based secondary verification (they rely on secondary authentication of weaker SMS services). At this time, you'd better create a Google Voice phone number (it can't be transferred via SIM card) and use Google Voice Phone as your secondary verification tool.
4. Create another email address : don't bind everything to the same email address. Create another email address for some very important online identities (such as bank accounts, social media accounts, cryptocurrency trading platforms, etc.). This email address must be kept secret. Do not use it for any other content. Use hardware-based secondary authentication to enhance the security of this email address.
5. Offline Password Manager : Use the password manager to enter a password, preferably a manager that can use an offline password, such as the Password Store (a software for managing passwords).
04 Summary
I talked about the beginning and end of this incident. The purpose is to let everyone know how easy it is to be attacked. I hope that everyone can adopt the suggestions I made above to strengthen your online identity security.
I could have done some very simple and easy protection measures to protect myself. I can't help but think "if I…", the development of the matter will be completely different. However, when I think about it, two other ideas are coming to me: laziness and survivor bias .
I have never experienced an attack before, so I didn't take my online security seriously. Although I understand my risk situation, I am always lazy to protect my assets with a more rigorous attitude. Therefore, I urge you to learn from my mistakes.
Author: SeanCoonce wearing boss
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Market Analysis: Has Bitcoin formed the top of the round?
- Is Bitcoin safe without block rewards? It’s noisy on Twitter.
- Development Challenge Competition | Quick and Easy Certificate – Decentralized Platform to Protect Intellectual Property
- Weizhong Bank Li He: 8 key issues that need to face the blockchain operation
- Bitcoin's "roller coaster" plot is hard to stop the trend, and the seven major indicators indicate that the bull market has officially returned.
- The value of money is out of nothing and there is no middle and no life.
- The price of the currency should be determined by the market, and Algorand will hold a Dutch auction.