Under the blockchain blessing, your copyright is yours
The era of digital economy is an era of science and technology, and it is an era of copyright exposure.
In April of this year, the dispute over copyright rights caused by the black hole and the national flag of China was revealed by the public, which caused public concern about the “copy of copyright”.
According to Ai Media Consulting, 78.8% of the respondents believe that Visual China’s rights protection method is extortion, and more than three-quarters of the respondents have resolved copyright disputes for more than three months, and 69% of the respondents It is considered that the handling of "copyrights against porcelain" disputes has become a burden on enterprises.
The phenomenon of “copying of copyright against porcelain” has become more and more serious, and it has caused serious interference to the social order. The behavior of infringing enterprises lacking social responsibility should be resisted.
- Private placement is smooth, opening is deserted, why is LEO not as expected?
- Ron Paul: Bitcoin or dollar substitute
- In response to the surge in capacity, how does Coinbase guarantee reliability?
Copyright protection is of interest to all originators. At present, domestic copyright protection programs cannot effectively solve copyright disputes.
How to use advanced technology to effectively solve copyright problems has become a social problem that needs to be solved now.
On May 11th, I was deeply convinced that Science and Technology CEO Yang Zijiang, Tsinghua University Assistant Professor Jiang Yu, and Secretary General of the Copyright Blockchain Alliance Hao Han, in the “Traveling Tourup2019” event organized by FISCO BCOS open source community, “blockchain copyright landing, Use technology to eliminate disputes as the theme, and share with the corresponding practice cases. Zinc Link is the first media in the industrial blockchain. This activity is tracked and reported. The following is the sharing content, which has been deleted:
Blockchain code quality and security

Society relies on the development of software technology, but as software goes deep into all aspects of our lives, the quality and security of software has reached an inflection point.
IT practitioners agree that software security is important, but Aunt Square Dance may not be interested in it. And now software security has reached the 2C stage, which is crucial for everyone.
In terms of financial software applications, there are currently two main pain points:
First, testing with a lot of manpower is tedious and time consuming.
Second, smart contracts are widely used in the financial sector, and because of the large number of asset transactions, it has become the target of public criticism. Hackers will choose places where the benefits are maximized, such as smart contracts within the digital pass.
Convinced that Kechuang's blockchain-based automatic detection system can reduce test costs. You can automatically analyze smart contracts and discover vulnerabilities. Try not to have false positives and find real errors.
When we were doing the test, we found that there were some smart contracts. The address looked no problem, but the address did not exist. So for specific application areas, do specific analysis and find out where the security vulnerabilities are.
If you just do general software, the efficiency is very low, you can only find some common errors. For example, zero error, zero error may be wrong for any software, but the problem is, for the application of copyright, its business logic error is exactly where, this is no way to find, so need to find some optimization Algorithm.
Transform smart contracts into a flow chart to increase efficiency. When you find a lot of vulnerabilities, which ones are to be repaired immediately, use a formula to sort them. Sorting first looks at the path, because one path may have multiple security holes in it. On the other hand, we tend to be short. Path, because the shorter the path error, the better the fix. So we first report that the vulnerability is serious and the shortest path is for the user to fix it.
For smart contracts, the effect of using symbols is still very good. The amount of code is relatively small, the errors we report are basically true errors, and the false positive rate is very low, but we try to use symbols to do relatively large programs, the effect is not particularly good.
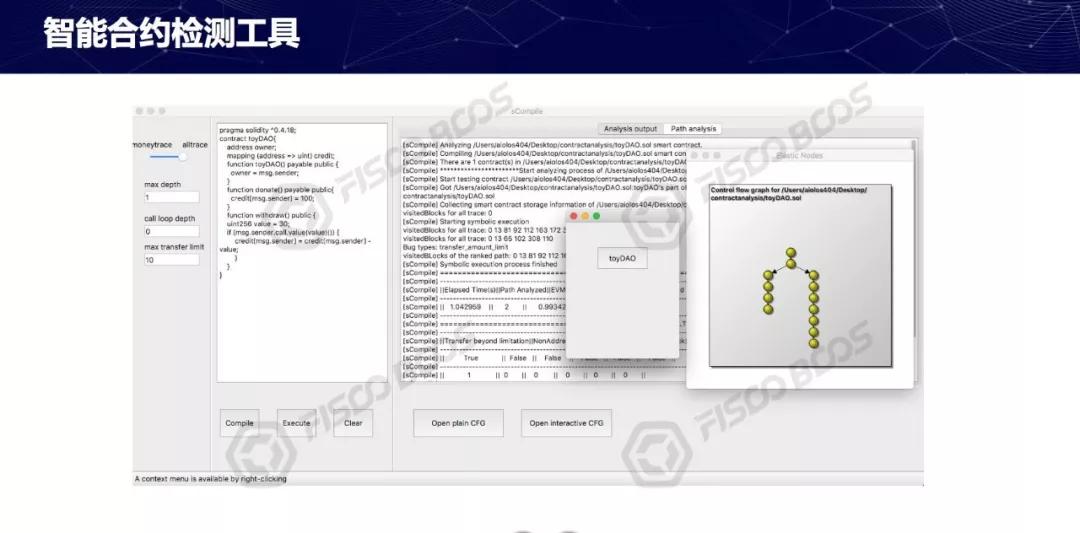
So for large programs you need to use dynamic detection, dynamic detection is not simply run, use a lot of optimization to find as many errors as possible. This aspect is not a simple solution. There is no way to ensure the correctness of the whole program. In essence, it is an auxiliary means. The code itself should be standardized in the process of doing it. The technology should be excellent. Try to reduce the code from all aspects of design and development. mistake.
Today's industrial-grade code, on average, has seven errors per thousand lines. Software errors are difficult to eliminate, so that some people say that software is the most complex man-made body created in human history, so the quality of software is guaranteed. And security is a long-term process.
Virtual machine security

At present, the blockchain is widely used. Both the game field and the financial field have a lot of related applications, and they occupy a very important position in our daily life. It is precisely because of the popularity of this application that the security of the transaction has also attracted a lot of attention.
To solve the security problem of the transaction, the first is to develop related security evaluation tools for smart contract security detection. The second is that in addition to smart contracts, we should also see some of these underlying infrastructure platforms, such as virtual machines.
If there are defects and vulnerabilities in the underlying virtual machine, it will bring more security problems. Therefore, we must not only ensure security and reliability at the level of smart contracts, but also try to ensure security at the bottom of the virtual machine or facility.
But nowadays few people do the testing and verification of such virtual machines to ensure its security. The big reason is that the virtual machine has a very large amount of code and special input, and the traditional solution has a high false positive rate.
We propose the hardening and testing of virtual machines. Through the EVM hardening method, we can avoid the contract vulnerabilities that can not be found in the smart contract test, and test the EVM vulnerability by testing the EVM itself through differential testing.
Virtual machine hardening is real-time protection through real-time monitoring of contract execution, and immediately blocks execution when risk is encountered. EVM testing is a comparison of the differences in execution results.
To give a simple example, suppose that there is a Baidu self-driving car in a certain scene, there is a Huawei auto-driving car, give it the same picture of the left turn, if Huawei's car turns left, and Baidu's car right Turning, then we know that these two are definitely inconsistent.
At this time, I introduced Google's self-driving car. Google's left-hand drive, it can be found that both Google and Huawei are turning left, but Baidu is turning right. There may be a mistake in Baidu.
Using differential testing to detect bugs is currently the most effective technical solution. First of all, you need to do some instrumentation at the EVM level to get some information that I care about. Then analyze the variation and generation of these information-oriented contracts, observe whether there are some attributes that violate, and stop if they violate.
Copyright trading system based on blockchain technology

At present, the threshold of creators is decreasing and everyone can create. These creations are valuable and can be realized, but the phenomenon of plagiarism is very serious. There are three ways to maximize the value of the creator's work: the first is to create and confirm the right, the second is to use the authorization, and the third is to discover the rights.
At present, there are three major pain points in the digital copyright industry:
First, it is difficult to confirm power. The traditional copyright registration period is long, and the registration price is too high, which is not applicable to a large number of micro-works.
Second, authorization is difficult. If the confirmation link is not done well, there will be problems with the authorization. The ownership is unclear, the settlement is opaque, and the transaction is not guaranteed.
Third, it is difficult to defend rights. The evidence is difficult to fix, the infringing body is difficult to find, the process is cumbersome, and the cost of safeguarding rights is too high, which is not worth the candle.
So how to use blockchain technology to solve it?
First, there is a node plan in the blockchain. If there are no nodes on the chain, it makes no sense. After having a node, negotiate specific matters to achieve consensus. Nodes include parties to copyright protection services, third parties to judicial services, and other trusted third parties.
Next is the deposit of the copyright blockchain. The confirmation of the right is to prove that this thing is yours, and authorizing a contract for filing is a contract deposit. After confirming the right, the information is registered and is also a deposit. For example, Jingdong's traceable blockchain, from large and small warehouses, to contractors and wholesalers. The last thing to deal with is the deposit.
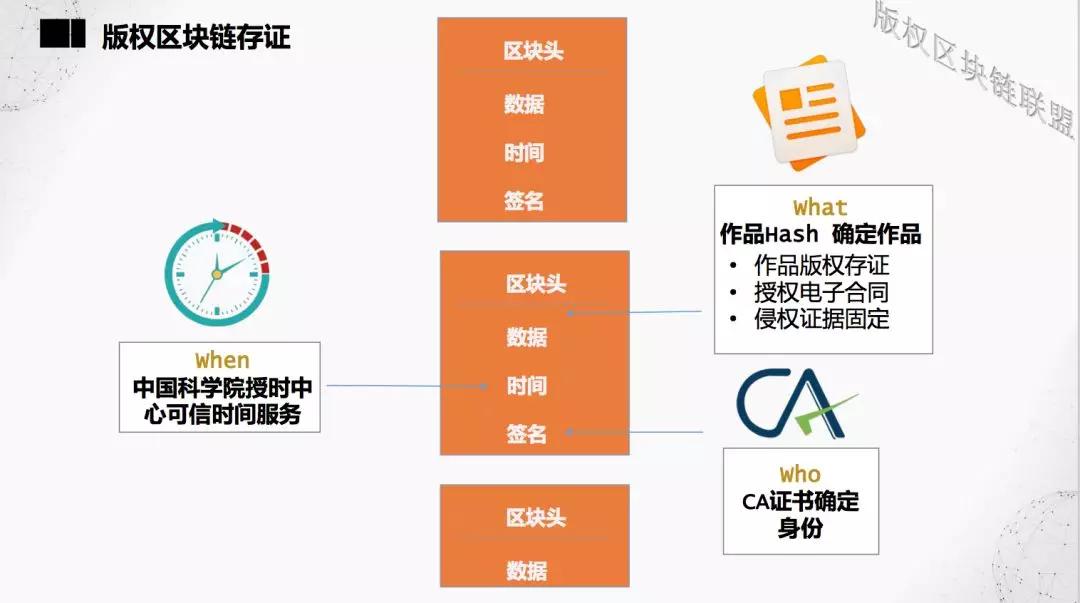
And to do the deposit is inseparable from three major elements: people, things, time.
Regarding people, the services provided by manufacturers of digital identity authentication must be real-name. If it is anonymous, it will not work according to the new regulatory requirements.
Regarding the issue of depositing certificates, the difficulty is not at the blockchain. How to ensure the consistency of data under the chain is the most important issue. But digital works are fine. Digital works have a hash value, and as long as the work changes, the hash value will change.
Regarding the time of deposit, the time on the blockchain is not allowed. There is a time lag within the block network, and using trusted time can enhance credit.
After the solution is proposed, how to apply it to the specific scene?
The application of the copyright blockchain includes three aspects: first, the deposit of the right to prove that the thing is yours; second, the transaction authorization, prove that I am authorized to give you, and issue a certificate of authorization. Third, infringement and evidence collection, the authorization credentials are stored on the blockchain through screen recording and screen capture.
The actual application scenario is this:
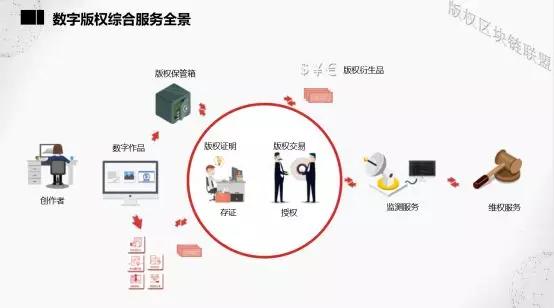
Once the creator's work is generated, the copyright safe deposit box will protect the creator's digital content copyright, and it will communicate with the copyright blockchain in real time, which means that any version of the creator's work can be placed in the copyright safe deposit box. Retain and write on the blockchain to achieve copyright proof.
Based on this proof, the corresponding copyright transaction can be launched. The copyright blockchain is built and maintained by everyone. The National Copyright Administration can stamp the work and it can be verified by the court.
In the application of rights protection forensics, one side is the copyright blockchain and the other is the balance chain. First, while the data is on the chain, the corresponding data should be packed, and then a hash value is calculated and stored on the balance chain, and the balance chain returns the corresponding number. In litigation, the client extracts the original evidence from the blockchain from our platform, the platform provides an index file, and finally submits the original evidence and index file to the litigation platform of the Beijing Internet Court.
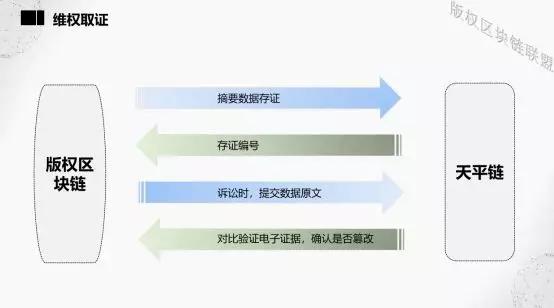
Real-time chaining, realizing creation and confirmation, using authorization, authorizing evidence, and retaining the right to pursue at any time, so that the creator can create with peace of mind.
Therefore, everyone is a creator, and everyone is a copyright owner.
Text: Yu Xiqing
Editor: Wang Qiao
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Ace vs. Ace: Against double-flower attacks, who is better with DCR and Bitcoin?
- Jingdong has applied for nearly 200 blockchain patents, and the number of BAT blockchain patents ranks among the top 20 in the world.
- 66 times the income! Block.one is not afraid of huge amounts of money to buy back shares, is the SEC going to shoot?
- 10% layoffs, financing target fell to 150 million US dollars, the market is adjusting the framework after the market recovers
- Institutional users are more likely to buy Bitcoin funds than Bitcoin?
- Does the Martin Act not apply to USDT? Bitfinex asks the judge to dismiss the lawsuit filed by the Attorney General of New York
- The 9th anniversary of the Bitcoin Pizza Festival, the story that the encrypted community has to say





