Under the chain expansion plan, the calculation of the chain is still in the process of expansion of the journey – the thirteenth block of the blockchain technology

General Education Institute × FENBUSHI DIGITAL
Text: Song Shuangjie, CFA; Tian Zhiyuan; Wang Zelong; Jin Jiahao
Special Adviser: Shen Bo; Rin
- Inventory: 28 “blockchain scams” we experienced in 2019
- Blockchain Security Science: How Counterfeit Attacks Steal Your Digital Assets
- Heavy: Bakkt will launch its first physical delivery bitcoin futures contract on September 23
Guide
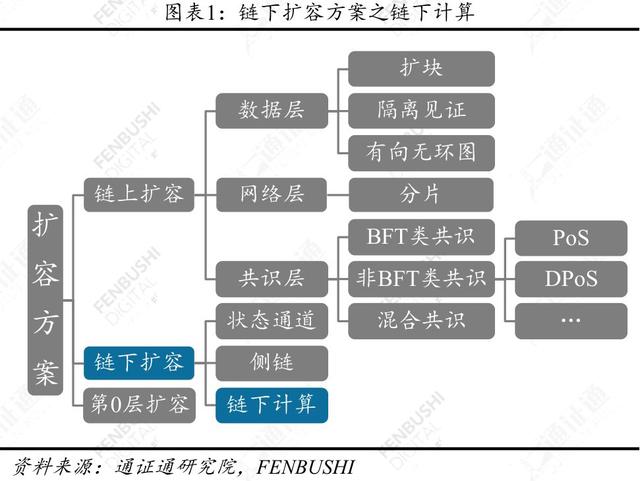
Offchain Computation is one of the solutions for capacity expansion under the blockchain chain. Various chain computing schemes have been proposed and are gradually being implemented.
Summary
The current blockchain generally faces shortcomings in the data processing capacity of the chain, which restricts the possibility of further application of the blockchain. With this as the background, the calculation of the chain is proposed as one of the expansion schemes. The basic idea is to move all kinds of transactions that were originally placed on the chain to the chain, while only the verification part is retained in the chain. Improve data processing capabilities on the chain.
The calculations under the chain mainly include four methods: verifiable chain calculation, “enclave type” chain calculation, chain safety multi-party calculation, and incentive-driven chain calculation. They have their own advantages and disadvantages. Some programs are relatively new, with little or no project deployment, such as zk-STARKs, Bulletproofs, etc. Some programs have passed the inspection and recognition of large projects, such as zk-SNARKs.
Verifiable under-chain calculations involve two types of roles: the verifier and the prover , the former being on the chain and the latter being under the chain.
The calculation of the "enclave" type chain is based on TEE (Trusted Execution Environment, used to ensure confidentiality and complete code execution). In this calculation mode, the under-chain calculations are performed exclusively in a trusted "enclave".
Secure multi-party calculation can achieve the final result by combining the calculation results of each part of the data without knowing the complete data content.
Incentive-driven chain calculations assume that all parties involved in the calculation are rational economic agents . This mode mainly involves two types of roles: the solver who processes the computational task, the computational task that recalculates the solver's processing tasks, and verifies whether it is erroneous. But in some scenarios, more roles will be introduced.
At present, a variety of chain computing solutions have made progress or are landing, and the calculation of the chain as one of the blockchain expansion plans will be further developed and applied in the future.
Risk warning: technology progress is less than expected, channel security under the chain
table of Contents
1 chain calculation, chain verification
2 four main modes of calculation under the chain
2.1 Verifiable chain calculation
2.2 Calculation of “enclave” type chain
2.3 Chain-based secure multiparty computing
2.4 Excitation-driven chain calculation
3 is still on the way, gradually landing
text
The calculation under the chain is one of the solutions for capacity expansion under the blockchain.
1. Chain calculation, chain verification
The occurrence of a new transaction causes the "state" on the chain to change, and the blockchain can be thought of as a machine that handles a "state transition" function. The sub-chain calculation is a model that transfers the process of calculating the "state transition" function from the chain to the chain, and then the corresponding result is verified by the chain.
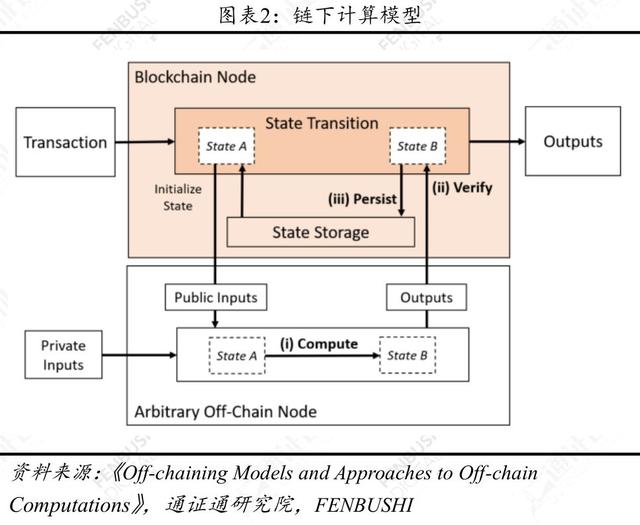
First, any sub-chain node retrieves the relevant state from the blockchain as input. Unlike the processing mode in which the data is completely publicly available on the chain, the relevant information in the calculation process under the chain can be either public or private.
Based on the input values, the nodes under the chain compute the results of the "state transition" function and then send them to the chain. The public input does not need to hide the calculation process, while the private input calculation process needs to remain private. The function value is checked on the chain, and if the function value is correct, it is recorded in the state on the chain.
Why do you need to introduce chain verification? Because the "state transition" function is calculated under the chain and the results are submitted, there may be fraud or fraud, and the verifier on the incoming chain can have a corrected plan B.
2. The four main modes of calculation under the chain

2.1 Verifiable chain calculation
To implement a verifiable under-chain computational model, there are three algorithms that can be used as paths:
(1) Concept
This model involves two types of roles: the verifier and the prover (Prover), the former is in the chain and the latter is in the chain. The operation of this mode is similar to the basic definition of the calculation under the chain, and will not be described here.
(2) Main characteristics
Non-interactive. The prover is able to convince the verifier in a piece of information (ie, a chain-to-chain transmission process). A highly interactive solution will generate multiple blockchain transactions, increasing the burden on the blockchain network and increasing verification costs.
Low cost of verification. In special cases, if the confidentiality information is checked, the relatively high verification cost is acceptable; otherwise, under normal circumstances, the cost of the chain calculation + chain verification should be lower than the pure chain calculation cost.
(3) Implementation status
To implement a verifiable under-chain computational model, there are three algorithms that can be used as paths:
1) zk-SNARKs
zk-SNARKs is a variant of the zero-knowledge proof algorithm, whose names are: Zero knowledge, Succinct, Non-interactive, and Arguments of Knowledge, Proofs (Proofs) Proof) A composite abbreviation for these terms.
Compared to zero-knowledge proof of this "ontology", zk-SNARKs makes little or no interaction between the prover and the verifier, and its verification cost is relatively low, and the computational security is relatively high.
Currently, zk-SNARKs relies on initial authentication settings between the prover and the verifier – this means that a set of public parameters is needed to build zk-SNARKs to create private transactions. These parameters are incorporated into the agreement and are one of the necessary factors to prove the validity of the transaction. The underlying problem is that the parameters are usually set by a small group of people and there may be trust issues. In addition, in theory, if the prover has sufficient computing power, he can submit false evidence and affect the entire system. This is why quantum computers are considered a threat to this algorithm.
Well-known projects that currently deploy the zk-SNARKs algorithm include Zcash, Loopring, and so on.
Ethereum is also expected to deploy zk-SNARKs. In January 2019, the Ethereum Foundation and start-up Matter jointly released a sidechain expansion solution using zk-SNARKs on the Ethereum test network.
2) Bulletproofs
The algorithm was jointly proposed by Jonathan Bootle of University College London and Benedikt Bunz of Stanford University in late 2017. It is a non-interactive zero-knowledge proof verifiable computing solution. Compared to zk-SNARKs, its verification cost is higher. But no need for a trusted initial setup.
Monero is the first to deploy Bulletproofs in the main encryption pass. According to Monero's official website, in the summer of 2018, the community released an audit report on the deployment of Bulletproofs for Monero, and Bulletproofs was first deployed on Monero Stagenet. By October 2018, Monero's main network completed the deployment of Bulletproofs.
According to Sarang Noether, a researcher at Monero Research Lab, since the deployment of Bulletproofs, the average volume of transactions on Monero has dropped by 80% and transaction costs have dropped significantly.
3) zk-STARKs
The algorithm was created by Professor Eli-Ben-Sasson of the Israel Institute of Technology. It is a replacement for zk-SNARKs and is considered a more efficient algorithm, but it is not yet known whether it will be more cost-effective in the future due to its difficult deployment status.
Similar to Bulletproofs, zk-STARKs does not need to initialize trusted settings because it uses collision-resistant hash functions for more streamlined symmetric encryption, and the algorithm eliminates the number theory assumptions that exist in zk-SNARKs. — The latter is costly to implement and vulnerable to attack by quantum computers.
But compared to zk-SNARKs, its shortcoming is that the proof may be more complicated, which limits its potential performance.
2.2 Calculation of “enclave” type chain
(1) Concept
This calculation mode is based on TEE. In this calculation mode, the under-chain calculations are performed exclusively in a trusted "enclave", and each message of the "enclave" can be authenticated and certified by a trusted external entity. When the calculation is initiated, the public input values are obtained from the blockchain, while the private input values are selectively added by the underlying nodes. The integrity of the output is verified by proof of the chain verification of the "enclave". Once the verification is successful, the new status is recorded in the blockchain.
(2) Implementation status
At present, projects such as Enigma and Ekiden have tried the program.
In the Enigma project, calculations can be performed either on the chain or in a separate enclave under the “enclave”. Enigma's specific scripting language allows developers to mark target items as private, forcing them to be evaluated in an offline mode.
Contrary to Enigma, Ekiden does not support chain computing, and blockchains are only used for persistent state storage. The code and private input values are provided by the under-chain client that only communicates with the "enclave". Once the calculation is complete, the "enclave" feeds the results directly back to the client, while the status is recorded in the blockchain.
2.3 Chain-based secure multiparty computing
(1) Concept
Secure multi-party computing can achieve the final result (equal to the result of calculation using complete data) by combining the calculation results of each part of the data without knowing the complete data content.
The same is true for the implementation of secure multi-party computing under the chain. The difference is that the concept of chain and chain is introduced:
First, the privacy data is divided into multiple shares and distributed in the form of private input values among the nodes under the chain. The current state value of the blockchain can be used as a common input value. The sub-chain nodes then calculate the sub-chain state transition values for their respective parts.
The underlying nodes publish their respective results and combine them and then place them on the chain.
One characteristic that needs to be met by a secure multi-party computing protocol under the chain is public auditing. For example, an auditor who does not participate in the above process can verify the correctness of the calculation results. Thus, the correctness of the calculation results can be verified by the chain auditor during the verification phase, or by the chain auditor by evaluating the audit trail of the auditor on the chain (the flow record of the system activity).
(2) Implementation status
The implementation of secure multiparty computing can generally be divided into three categories:
1) A construction method based on the Ya confusion circuit;
2) Construction methods based on secret sharing;
3) Construction method based on homomorphic encryption.
At present, many projects have tried to use secure multi-party computing protocols, such as Defi and Enigma .
2.4 Excitation-driven chain calculation
(1) Concept
This model assumes that all parties involved in the calculation are rational economic agents (ie, the participants maximize their own interests at minimal cost). This mode mainly involves two types of roles: Solver, which handles the computational task, Solver, which recalculates the computational tasks that the solver has processed, and verifies that it is incorrect. But in some scenarios, more roles will be introduced.
(2) Implementation status
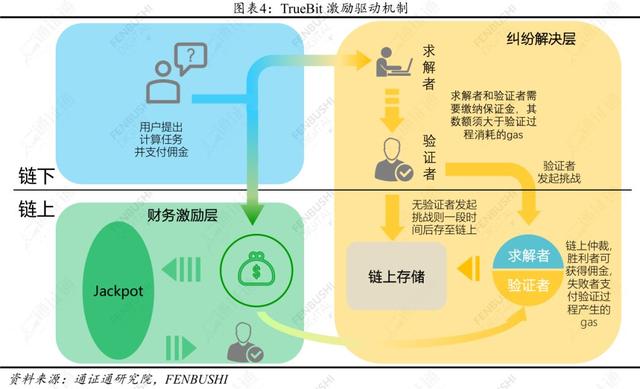
The most well-known solution in the calculation of incentive-driven chain is TrueBit . The basic principle is:
The user proposes a calculation demand and pays a commission. If the solver under a certain chain believes that the commission price is in line with expectations, then the calculation is performed and the result is published. In addition, the solver also needs to provide a margin.
Relative to the third party of the user and the solver – the verifier (also under the chain), you can re-run the above calculation and check if it is wrong ; if you find that the solver gives the wrong result, you can initiate a challenge and submit it to Arbitration on the chain. Similarly, the verifier needs to provide a margin.
Through the smart contract on the chain, the solver and the verifier jointly perform a verification game, and the code placed on the chain by the user is used to verify the authenticity of the answer between the solver and the verifier, the correct party obtains the commission, and the other party The gas cost incurred during the entire verification process is payable.
TrueBit also designed a Jackpot mechanism to maintain the certifier's ecosystem. The system randomly selects some transactions and asks the solver to submit both the correct answer and the Force error (the wrong answer), either of which will be verified by the chain request. When the forced error is verified and challenged by the verifier, the solver No need to be punished. The commission for all transactions will be drawn a small portion and pooled into a prize pool for payment to the successful verifier in the jackpot mechanism.
3. Still on the way, gradually landing
In the three implementations calculated under the verifiable chain, the computational cost of zk-SNARKs is relatively high due to the existence of the initial trusted settings, but after the initialization of the trusted settings is completed, the complexity of the proof and the complexity of the verification are very high. Low; zk-STARKs and Bulletproofs algorithms do not need to initialize trusted settings, the computational cost is relatively low, but the difficulty and verification complexity is higher, which is the constraint of its application.
From a security perspective, the incentive-driven chain calculation relies on the assumption that there is at least one honest participant in the system, and the malicious verifier can challenge each calculation step by submitting the wrong answer, allowing all tasks to pass through the chain. The "challenge" link affects the overall speed and safety of the system.
A disadvantage of the calculation under the "enclave" type chain is that it relies on TEE. For example, Intel's SGX (Software Guard Extensions), a technology that allows the Inter processor to create a "small black box" as a TEE, has lost its effectiveness before hacking.
At present, a variety of chain computing solutions have achieved results or are landing, such as Monero's successful deployment of Bulletproofs after the transaction volume is significantly reduced; Ethereum using zk-SNARKs in the test network, TPS is expected to reach 500; the first dedicated to deploying zk-STARKs The project StarkWare is also under test.
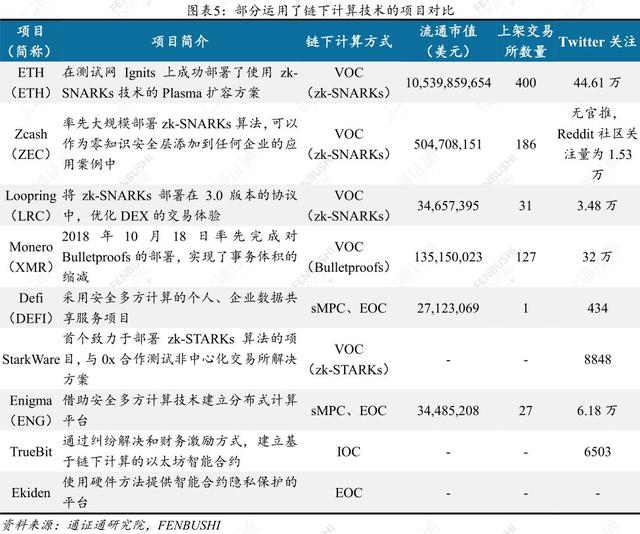
Note: The market value of the circulation and the number of followers of Twitter are as of July 20, 2019.
The calculation under the chain is entering the vision of major projects, and further development and application will be obtained in the future. With a variety of excellent features, the success of the chain calculation has attracted attention. For example, Zcash and Menero have deployed zk-SNARKs and Bulletproofs respectively. The Ethereum core developers agree with zk-SNARKS's performance in terms of capacity expansion. The technology under the chain computing expansion plan will be pushed to the entire Ethereum.
Note:
For some reasons, some of the nouns in this article are not very accurate, such as: pass, digital pass, digital currency, currency, token, Crowdsale, etc. If you have any questions, you can call us to discuss.


We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Think about it: return to basic logic in a market that lies
- What is the loss of his position? 1000 BTC, OK started the contract trading battle chain node AMA
- Blockchain Talent Survey in 2019: Corresponding to cryptocurrency-related job search fell by 67% Recruitment Top Ten Employers Only One Blockchain Enterprise
- Failure to cancel the case, CSW is not trusted by the judge
- Ethereum 2.0 Economic Incentive Analysis: How much can the pledge annualized income be?
- Bitcoin is controlled by the "big family"? Analysts say that the distribution of Bitcoin ownership is “very balanced” and that this problem exists in competitive currencies.
- Cryptographic lending industry report: market volume of 4.7 billion US dollars, return rate less than 2%