Who is the information of the user who sells the coin? What have the leaked information been taken?
While enjoying the convenience of the Internet, it also makes privacy data a step closer to streaking.
Recently, many people in the currency circle have been caught in the trouble of "information disclosure."
In the past month, many investors in the currency circle have received a type of telephone call: the other party claims to be a customer service of the fire currency (or coin security, OKex, Golden Finance, Bitland, currency world, etc.), claiming that the platform is doing activities. There are professional analysts with a single in the group, plus a WeChat to pull you into the group.
- Babbitt exclusive | dForce is invested by the mysterious bank, intends to launch an index-type stable currency pair Libra?
- The essence, risks and new opportunities of exchanges from the perspective of monetary finance
- From $4,000 to $13,800, analysts say the behind-the-scenes push for bitcoin is Tether.
Most of these phones start with 146, 165, and 170. The other party not only knows that you are a user of the currency circle, but some even expose your name directly! When you really enter the group, it is not for you to buy spicy chicken coins, it is to sell you stocks, in short, you are tricking you into spending money.
In fact, the exchanges such as the fire currency and the currency security have issued statements, all of which are fake customer service. Therefore, the information that contains your phone number, name, or even ID card is a high probability. It is still a mystery as to how the information is leaked and sold.
Currency leaks have become the norm
Yesterday afternoon, a user named Guardian M released a series of high-definition photos of handheld ID cards in the telegraph group. These pictures were taken for the KYC certification. The time is February 2018, and the user information is all over. In China, the United States, Japan, South Korea and other places, there are 480 unsigned photos that everyone can see in the telegraph group.
Some domestic users even found their own information in the leaked photos. For a time, the currency was pushed to the forefront, and the news that “KYC data was leaked” was spread to all major communities and social media, making the entire currency circle. People are upset.
In fact, this batch of information was "disappeared" as early as the beginning of this year. In the latest statement, the currency said that it was threatened recently and was asked to exchange 300 bitcoin chips for the 10,000 KYC information he claimed to have, but the currency did not agree.
Obviously, this user named "Guardian M" chose to retaliate because he did not receive the blackmail. After the storm, the user logged out of the account and disbanded the telegraph group with more than 10,000 people watching.
After completing this "prank", the criminals have escaped, but after this shock, the coin has to squeeze the KYC certification data that has been done before. No one knows whether his information is in the black market. Rogue.
Time is a little earlier. Last May, a large number of users who have registered an exchange have received a number of mobile phone text messages "HLC Halal Chain and XX Signing Cooperation". At the end of the SMS, they also revealed that "it will rise recently." To lure the user to buy the coin.
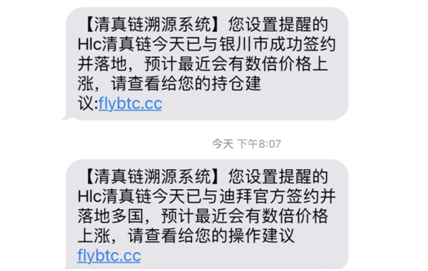
Regardless of whether the news is sent by the project or not, it is undeniable that the mobile phone information of the users of the currency circle has been leaked and has been "precisely marketed".
Combined with the recent privacy breach, let us see the fact that some of the ID numbers that have been used to do KYC, those that have registered for the exchange have been leaked, and some are at high risk of disclosure. Among them, they have already been clearly priced, and they are secretly traded by various criminals.
How are these information leaked?
In the Internet age, privacy leaks are no longer new.
In general, there are four ways to be leaked: hacking, thieves in the enterprise, users registering inappropriate websites, and users' mobile phone software cause information leakage.
1 , hacker stealing
Many large companies have been hacked. Facebook has been leaked 30 million user information by hackers. Consumer data of Uniqlo shopping site has also been stolen by hackers. Domestic A station and Mobike user data have also been stolen by hackers. Information is sold in high-profile telegraph groups and dark networks.
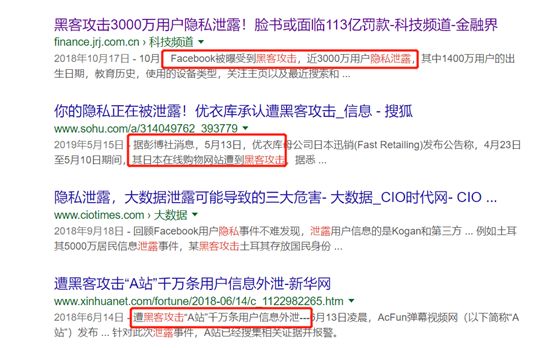
The currency circle is a "cash machine" that hackers love to visit. They not only steal information, but also take away thousands of assets. They often scare the currency market down. In recent years, countless large and small exchanges have been hacked, and the degree of privacy risk of users is self-evident.
2 , registration of informal website
Whether it is online or shopping, there are requirements for “filling in personal information” and “registering an account”, and some small companies or small websites are often easy to play “bad ideas” after receiving personal information, and sell these materials to P2P at a high price. For financial management, insurance, and selling, because there are too many places for users to leave information, they will never know which one is leaking.
The same is true for the money circle. Users will inevitably register some unknown project websites because of some “airdrop temptations”, or some pheasant exchanges. These are the illegal costs and moral senses of companies that are outside the law. Very low, it is easier to make some embarrassing things to sell information.
3 , corporate thieves
In the event of information disclosure, many people will point their finger at the main body of the enterprise for the first time. They believe that unscrupulous enterprises actively disclose user information, but in fact, some companies that really want to do things, the purpose is to make money, and "sell information." This can directly block this road. The more the big business, the less the big company will do.
But even if the company is self-respecting, it can't stop the thief, and many privacy leaks in the world are harmed by " self ".

4 , mobile phone software leaked
At the beginning of this year, a hacker said in the dark network that he got the information of the 100,000-dollar user and put some photos of the user's hand-held ID in the post, some of which are KYC, Kraken, and Bitfinex users. data.
When the user suspects that the material has been leaked by these exchanges, the currency tells the media:
"The internal information of the currency security is all electronic watermark, and the pictures on the Internet do not have a specific electronic watermark. Therefore , it is believed that these materials are not the internal information of the source. "
Kraken’s boss also said that the exchange did not disclose information, he pointed out:
" Photos are likely to be leaked on users' mobile phones. For example, iCloud / GSuite software accounts that can sync phone photos are phishing."
In fact, some mobile phone software often gets a lot of permission to read photos, mobile phone numbers, and text messages without the user's knowledge. The photos of "Hunger Games" heroine Jennifer stored in iCloud have been leaked.
And each person's mobile phone software carries a large number of users' taxi information, shopping information, location information, and the incidents of leaking privacy of these apps over the years are not uncommon.
How to save streaking privacy?
More troubling than data breaches, you can't know what your personal information is used in addition to being resold by second-hand and third-hand . Those who buy user identity information, in addition to selling to the sales call will use it?
1 , is used to register various accounts
There are black products on the Internet in bulk sales accounts, a real name registered micro signal can sell 60 yuan, a real name Alipay account 20 yuan can also be bought.
The most used personal information is to take "薅 wool" . Registering P2P financial apps with real identity information can get 50 yuan return. Many Internet companies also have such registered "counter-subsidy" activities.
2 , is used to apply for online loans
When the online lending platform is prevalent, some online lending companies are not strict in risk control, and they often illegally lend money. Criminals can apply for online loans by taking your information for certification. And if you have your four sets of "ID card, bank card, bank card password, and calling card" , you can directly take away tens of thousands of loans.
In addition to these, personally identifiable information may also be used for money laundering, legal entities registered as shell companies, accurate online scams, etc. In short, the more detailed the information, the more places that can be used.
On the Bitcoin forum, a user posted a question: "Are you worried about KYC certification?", the post attracted hundreds of people to reply, most people answered: "I am worried that the information was leaked, but I can not change anything. , you must fill in when you register for the exchange."

In the face of the law, the general exchange will require KYC certification in order to avoid the suspicion of money laundering. "Uploading information" may be unavoidable for most people in the currency circle.
So how should the currency circle reduce the risk of privacy being leaked? Here is a practical idea for everyone:
Don't sign up for some pheasant exchanges and some websites of unknown origin. These websites can't do your job and become the only valuable thing;
More than one mobile phone card, separate Alipay, bank card, digital currency account;
Avoid "a string of passwords to go to the world", different fund accounts try to use several different passwords;
Don't easily click on the link in the mailbox to avoid being phishing;
Specially set up a bank card for the import and export of speculative funds;
Try not to save your personal ID card and hand-held ID card information on your mobile phone or computer.
Author: Ma Shaka
Source: Block wave
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Being shot, being controlled, and being exiled globally, is the founder of the exchange the most dangerous occupation in the currency circle?
- Analysis | Supporting POW security is not power, but belief
- Bitcoin fell to $8,000 in August? This mysterious giant whale is willing to bet 10 BTC
- QKL123 market analysis | Bitcoin 12,000 US dollars were resisted, market uncertainty increased (0807)
- The first time there has been a buy signal since June, Bloomberg believes that Bitcoin will see a new high.
- Industry Research Report | Take USDT as an example to see stable currency: Although the positions are too concentrated, the role of “stability” is indispensable.
- 50% of the assets are bitcoin, is it crazy?





