Why did hardware wallet Ledger launch the Ledger Recover service, which has sparked criticism from the Web3 community?
Why did hardware wallet Ledger launch its controversial Ledger Recover service?Author | Sethforprivacy, Content Manager of Bitcoin Tool Development Company Foundation
Translation | PANews

On May 16, Ledger released the Nano X cold wallet 2.2.1 firmware update, which introduces a key mnemonic recovery feature called “Ledger Recover” as an ID-based key recovery service. The feature will back up the user’s private key recovery phrase and requires a subscription ($9.99 per month) to activate. Currently, a passport/ID card issued by the EU, UK, Canada or the US is required to subscribe to this service, but in the coming months, more countries will be covered and support for more documents will be added.
- 3 Counterintuitive Experiences in Cryptocurrency Investment
- EigenLayer, which raised $64.5 million in financing: A new narrative in the collateralized track
- US SEC Chairman’s pessimistic tone: Cryptocurrency businesses often non-compliant, filled with opacity and risk
However, this feature has raised concerns among many Web3 users about privacy and security, especially when it comes to storing private key mnemonic phrases and associating them with passports or ID cards, which clearly violates the privacy values of the crypto community. The content manager of Bitcoin tool development company Foundation has pointed out the “danger” of Ledger’s latest cryptocurrency custody solution in a post.
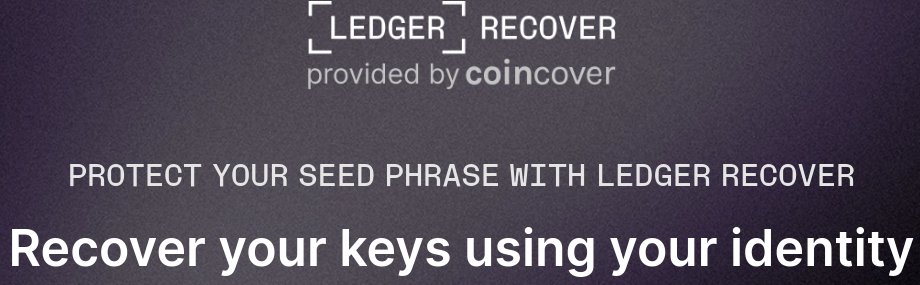
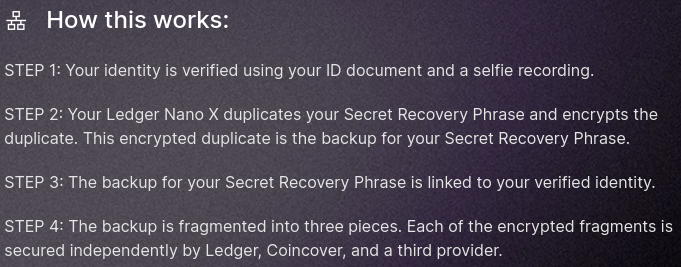
It is said that the core of Ledger’s new product is to fragment the user’s mnemonic phrase, divide it into three parts, and then encrypt it, while also requiring the user to provide their ID and a selfie. Then, trust three trustees to protect these fragmentary information for you.
However, there are problems with what Ledger is doing.
First, in order to use this “mnemonic phrase recovery” system, you must associate and bind your ID identity information with the Ledger account, which creates a KYC pain point and raises issues such as data leakage, hacker attacks, and scrutiny and surveillance.
Secondly, you also need to trust third parties and give them your ID information and information related to encrypted currencies. In this case, data leaks or hacker attacks are likely to occur, after all, Ledger user data is very valuable (both now and in the future), and any “authorized third party” may decide at any time to use your data as a source of income.
More importantly, the Ledger Recovery service also compromises user privacy. Currently, most Ledger users choose to use the Ledger Live software service, which uses Ledger nodes to synchronize all wallets, including all details of cryptocurrency activity within the wallet. Compared to binding one’s own ID with the Ledger account, users who use Ledger Live are at higher risk.
According to disclosed information, all KYC data is collected by a company called “Onfido”, which will handle KYC information verification, etc. When a Ledger user uploads/verifies their identity, they will retain the user’s ID, images/videos/sounds in the selfie video, and overall images of the user’s device and current activity.
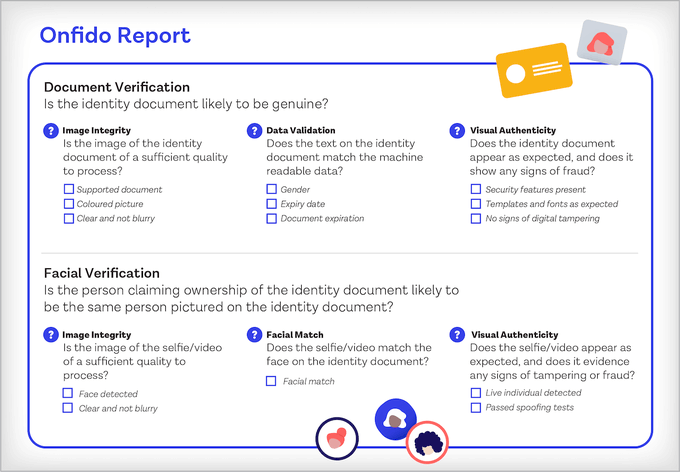
This means that Onfido will have full access to your ID and the fact that you are a Ledger user. Of course, they definitely know that you hold cryptocurrency. Onfido will also have full access to your device information used for identity verification, so now you not only trust Ledger and “authorized third parties” to use your identity data, but also trust Onfido to have more information about your device and other information.
All of these operations are easy to trigger new threats. Next, let’s further analyze from a technical perspective.
From a technical perspective, users must “100%” trust Ledger, because the entire process code is closed and cannot be verified. Although Ledger co-founder Nicolas Bacca said that his team plans to open up its code in the future to let users see how Ledger’s recovery service encrypts user data securely and runs securely at the bottom, and Ledger is also making its recovery service fully optional and transparent about its cooperation with third-party hosting institutions, at least at the time of writing this article, Ledger has not open-sourced the relevant code, which means that no one can verify what actually happened/security except for Ledger itself.
If everything is as stated above, theoretically, the user’s mnemonic words will never leave the device unencrypted. However, we cannot verify this and ensure that these mnemonic words have been securely completed or correctly encrypted. But one thing can be confirmed, that is: the code is running on your Ledger now, and your mnemonic words can be sent via USB/BT. From another perspective, at this time, your wallet will no longer be a so-called “cold wallet”, but a “cold-to-hot” wallet. Moreover, if your wallet can be turned “hot” with a few keystrokes, it will also open up a large number of new attack media for phishing and malware on the network, and hackers may unknowingly gain access to your mnemonic words.
At present, we cannot confirm whether Ledger has built-in security measures to prevent someone from sending all the encrypted fragments of the mnemonic phrase to one person or sending them to three different custodians, nor can we determine whether the mnemonic phrase fragments can only be decrypted by the user themselves.
Here’s another issue – you can’t know how the recovery process, or decryption process works. Users must log in to Ledger and verify their identity, but if decryption can only be done on their own device, how can a new device obtain the decryption key?
In an end-to-end encryption (E2EE) scheme, there is usually a method to approve a new device and send it the decryption key, but in the case of a lost Ledger, the user cannot do this, so someone else must have a copy of the Ledger decryption key they sent you in order to recover the mnemonic phrase.
In this case, who has these decryption keys? Is it Ledger? Or is it encrypted and stored somewhere after logging in to Ledger Recover and verifying your identity? If so, how are the decryption keys stored, what technology is used to encrypt them, and how are they verified?
One more thing, if someone knows that you are using Ledger Recover and has obtained your ID, theoretically they can steal all your encrypted currency, even if your Ledger is safely stored in a drawer somewhere.
It is worth mentioning that Ledger Recover’s custodian CoinCover, as well as Onfido mentioned above, are located in the UK. The other custodian has not been disclosed in the official documentation, but it is rumored to be EscrowTech in the United States. If the rumors are true, it means that your information will be within the jurisdiction of the “Five Eyes Alliance”.
Summary
It may not be a good idea for Ledger to introduce the Recover service because it breaks all the principles of using hardware wallets (cold storage) and introduces KYC into it, while the “non-open source” mechanism also makes it difficult for many Web3 users to trust its claims.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- What would happen to Bitcoin if the black swan of US debt occurs?
- Inventory of the top 5 Ethereum GAS consumers
- Future Development History of NFT Derivatives: From Commodity Speculation to Financial Speculation, Gradually Abstracted Asset Symbols
- Why did Ethereum have two brief outages in a row? An analysis of the causes of the incident.
- After the explosion, searching for the past of BRC-20
- Facebook’s issue of stable currency is likely to fail
- Vitalik: Radical Market, ZK, Privacy and more






