An article to understand the investment logic of the Web 3.0 era: the analysis of the investment philosophy of the famous American digital currency fund Fabric Ventures
Fabric Ventures is a well-known digital cryptocurrency fund in the United States. It is a fund focused on the Web 3.0 ecosystem. Its investment objective is to transform the Internet from a centralized to a people-centered decentralized computing.
Throughout the portfolio of Fabric Ventures, we can see a large number of Web 3.0 projects, such as Polkadot, Blockstack, Ocean Protocol, Decentraland, Orchid Orchid Agreement, Raiden Lightning Network, Staked.US and other projects. And the fund is also keen to organize Web 3.0 related activities, they held an offline event called CogX in London in June this year, which covers almost all Web3.0 ecological projects.
Fabric Ventures can be understood as one of the investment kings of the Web 3.0 era, but how does the fund understand the paradigm shift logic of Web 3.0, and how do they pick the blockchain team? The following article is translated by block block rhythm BlockBeats translator 0x4 for exclusive article translation.
Intergenerational platform transfer
Recap history
- I just visited Huaqiang North, I found that ants and horses are out of stock.
- The final is coming, Bitfinex responds to the allegations in detail, the last fight before the hearing
- Why do institutional investors use the exchange Bakkt as the gateway to the world of encryption?
We are at the beginning of a paradigm shift in software architecture: the wave of decentralized data networks is on the rise. In the past few years, we have witnessed the significance of this revolutionary movement beyond the scope of Bitcoin and other cryptocurrencies, and even beyond the open source software and blockchain. From a broader perspective, this is a victory based on an open-standard peer-to-peer data network that reflects the power of appropriately tuned economic incentives that begin to take advantage of everyone's pockets, desktops, cars, living rooms and wrists. Personal data center. The popularity of high-speed wireless broadband access, rapid and mature localization software, and machine learning technology have made rapid progress in recent times, turning this paradigm into a thriving technology popularization campaign.
Over the past few decades, advances in technology architecture have enabled the commercialization of computer operating systems and software packages, which are accessible globally through data centers and cloud infrastructures for commercialized operating systems and software packages. . In this new wave of technology, data centers are being extended to the most marginal areas of the network, and the data itself is being "open sourced", and commercialization is also being used in reusable and trusted block building. Distributed users and machines interact with data through the underlying peer-to-peer network. These peer-to-peer data networks are themselves a "structure" that allows third parties to authenticate and manage information input while providing their users with data in an available, secure, and flexible manner.
Supreme individual rights
By providing users with their own data, the decentralized data network wave is deriving the huge “shafts” that are guarded by technology giants. These data “shafts” were the lifeblood of Internet companies, but they are now becoming technology giants. We can't afford the burden. Equifax's data breach led to the disclosure of 145 million Americans' privacy, and according to Facebook's disclosure, Cambridge Analytica used personal data on 87 million accounts, and recently, 50 million personal accounts of login accounts were leaked. These endless leaks have made users increasingly tired of storing personal data in the centralized data storage architecture of these technology giants. Although Google has quietly discarded the motto of " doing no evil", we are more interested in building a new software architecture in the Fabric Investment Fund. Its motto will become "can't do evil" : in this architecture, all Local users can control their own data, and high personal rights can rise. (* Block Rhythm BlockBeats Note: Blockstack's slogan is also Can't be evil.)
Yuval Harari recently mentioned in a TED speech that totalitarianism is not an evil ugly power defined in the retrospective review. On the contrary, totalitarianism will package itself as a solution to the present. The simple solution to complex problems seems quite tempting, and resisting such a solution seems stupid. Harari believes that within a specific business or government organization, a centralized data storage architecture may induce these organizations to master the data, and based on this technology, the targeted development and use of personal data, the degree of utilization Will reach the level that has not been imagined so far . We need organizational structures, data architectures, incentives, and technologies to eliminate this danger. In addition to eliminating the possibility of third-party evils, building applications based on distributed data networks will improve the intimate trust between people and improve computer services through increasingly sophisticated data encapsulation facilities. (* Block Rhythm BlockBeats Note: Yuval Harari is the author of A Brief History of Humanity, A Brief History of the Future)
Turn to people-oriented computing services
Although building trust in computer systems has become a consensus between the individual and the technology community, it turns out that when humans interact with hardware devices and software applications, it is difficult to fully trust them. As the potential of various types of software continues to expand, they begin to serve us in an increasingly intimate and personalized way, and the need to build trust between people and software is increasing. When a person shares personal genetic and physiological information, relying on algorithms to make trade-offs when humans are at risk, and even by filtering the information flow that forms the basis of our daily decision-making, the establishment of a trust relationship between people and programs becomes Mandatory.
In "Sapiens", Yuval Harari also explores the idea that, on the historical scale, it is the ability of human beings to conceptualize abstraction and share common beliefs through language, making strangers unfamiliar. People can cooperate and the community can rise . Nowadays technology can abstract this kind of trust, and with the correct incentives being coded at the protocol level, this mechanism allows people to cooperate and trade on a global scale.
In the upcoming wave of decentralized data networks, we will shift from zero-sum game capitalism to the composite interest of collaborative communities. Perhaps there is a good way to imagine this technological feat of coordination under minimal central control, which is the development of modern cities. Decentralized autonomous organizations based on blockchain technology can achieve a balance between flexibility and efficiency, coordination and incentives in a range of new areas. Replacing the interests of the owners with the common interests of the network, and aligning the incentives between network builders, service providers, and users: top-down command and control power structures (the structure is highly corrupt) ) Replaced with an emergency structure.
Looking back, looking to the future, see how the latest platform examples are converted
In order to understand where value may arise, and where we are likely to focus our efforts as investors and company builders, it is necessary to look at how technology can be subverted in the past few decades.
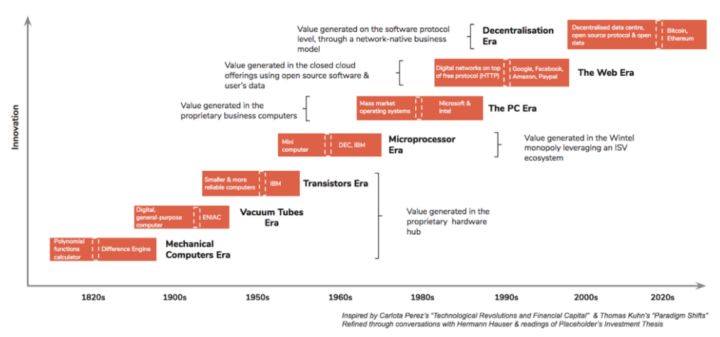
Let us recall the great prosperity that the United States created in the 1950s and 1960s after World War II. At the time, as American companies became multinational corporations, the business models of these technology companies were mainly to make profits on the production of expensive proprietary computer hardware. The result of this business model is that computers are held in the hands of a small number of users, including governments, businesses, and wealthy individuals. As the cost of microprocessor production plummets and the US economy continues to improve, a new computing architecture shifts the power of the industry from proprietary hardware systems to chipmakers and software companies. When Tom Watson, IBM's then president, couldn't imagine a computer other than the practitioners, Bill Gates of Microsoft knew that every family would own it in the future. Your own personal computer.
In the 1970s and 1980s, with the popularity of personal computers, technology companies set off a new wave – shifting their business model to selling cheap computer hardware with licensed operating systems. With the rise of Microsoft and its unremitting efforts to win developers, consumers naturally choose the platform with the most compatible applications, Microsoft's Windows operating system, which begins to spread among hardware vendors, and it will almost All packages are unified under one system. Until 2000, Microsoft's market share exceeded 90% of all PCs sold, most of which came from the operating software and application software layers.
However, despite Microsoft's dominance of the user's desktop, it has never protected servers in the wiring closet and data center—these are still the most successful Unix workstation companies in the 1980s (Sun, Silicon Graphics, and IBM). Controlled. In the early 1990s, Linus Torvalds tried to break this expensive hegemony with a cheaper, more open alternative, Linux, an open source version of the Unix operating system for software servers. The system combines common hardware with the Linux operating system, Apache web server, MySQL and PHP to create a new wave of technology business. By 2012, Microsoft's share of the computer market had fallen to 20%, and by 2017, Linux-based Android systems had an 85% share of the mobile computing market.
Over time, cheap software has become more popular and networks are available everywhere. This social reality has driven technology companies to shift their business models to providing free software and networks in order to convert the user data they collect into currency. Today's technology giants have absorbed open source software and combined it with a large number of monopolistic user data silos to create a competitive technology moat to defend their trillions of dollars in company market capitalization . However, as today's technology companies face increasing data usage issues, users are beginning to scrutinize ownership of their data, and the government is pushing for broad data protection regulations (such as GDPR).
With the democratization of hardware, operating systems, software, and networks, the new paradigm shift we are observing will open up access to data within the network. With the disintegration of existing monopolistic data silos, we will observe that the data itself and access to the data will be packaged into commodities for sale. But such a paradigm shift still leaves people with the question: Once the data monopoly is weakened or lost, where will the business model of existing technology companies turn?
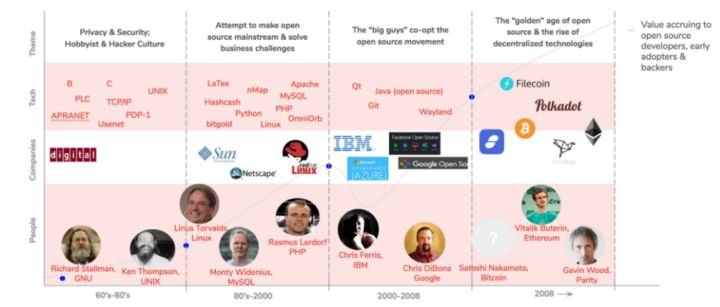
To answer this question, we reviewed the history of open source software development and the associated engine and profitability methods. In the beginning, the open source software movement emerged between privacy enthusiasts, hackers, and government entities that realized that the public software they used could not be commercialized. The movement relies heavily on a moral belief that software should be open and accessible and accessible to all.
Developers realize that the open source software movement fundamentally improves the software development process in addition to making the software freely available. Different online communities have been built around open source projects, and their reputation has accumulated in these communities, creating exponential growth among technology contributors, software maintainers and users . The advent of open source software has enabled people to distribute software around the world, and developers have begun to form companies that add a very thin monetization layer to a vast distribution network. In 1993, Bob Young founded ACC to sell Linux and Unix accessories, which later became Red Hat. Around the same time, Monty Widenius (Fabric Ventures consultant & founder of OpenOcean) began working on MySQL in 1994, working to consolidate MySQL with the same open source Linux, Apache, and Python to form LAMP, making it in 2008. It was the most popular database in the world before it was acquired by Sun Microsystems for $1 billion.
Over the past 20 years, as large technology companies have become aware of the viability and benefits of open source, the world has become dependent on open source software. React and React-native JavaScript development tools are primarily maintained by Facebook, and Google has made countless contributions to Android, Kubernetes, and Go . Less than 20 years ago, Microsoft was considered a major opponent of open source software. Today, Microsoft has transformed into a company that supports the most open source developers in 2017, and recently it has acquired Github for $7.5 billion. These tech giants have chosen open source software, basically stopping the charging of software, and instead monetizing user data to build their entire business path: creating numbers by using software without ownership and data not belonging to them. The market value of trillions of dollars.
Unfortunately, in this third wave of open source software development, developers have not only lost the moral ambitions and romantic motives that drive the first wave, but often do not have the economic benefits that have driven the second wave or Reputation return.
With Nakamoto reporting the Bitcoin white paper in 2008, we have entered the fourth era of open source software development: by solving the "double spending" problem and creating "digital scarcity" in distributed systems, Nakamoto Satoshi It lays the foundation for integrating the digital value transfer layer in a peer-to-peer network. This breakthrough in basic architecture enables open source networks to reward and motivate contributors without central authority or sponsors. Unlicensed innovation and “don't trust” peer-to-peer networks on open platforms, coupled with a pass-driven incentive and governance system, have triggered explosive growth in developers and ecosystems around open source projects. The open source development movement eventually discovered its elusive "business model" – a model that does not necessarily reward a single-centric entity, but rather equitably encourages all contributors and participants to create distributed numbers in each network. economic.
Paradigm shift driven by three major trends
Over the past 20 years, the success of the Web 2.0 era has been largely dominated by three basic technologies: cloud storage, socialization, and mobility. We believe that technological innovation in the coming decades will be driven by the interaction between edge computing, machine learning and distributed data: edge computing captures millions of data points in a large number of devices, and progressive machine learning algorithms absorb these rich The data, located at the bottom of the decentralized data will support security, flexible communication and fair incentives.
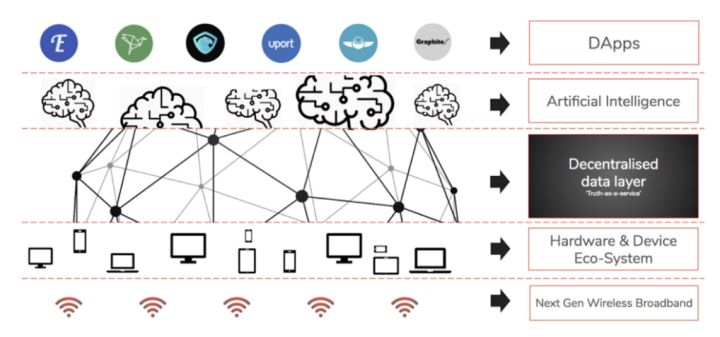
Combining these three technology waves will produce a large amount of data, but these data are still blocked for privacy, trust or competition. In 2010, the world produced approximately 1 terabyte of data. According to McKinsey & Company's research, 16 Zebytes of data were produced worldwide in 2016, however, only 1% of them were analyzed. By 2025, the world is expected to generate more than 160 megabytes of data. Due to the emergence of data sources that have never been used, privacy sources and fine-grained value distribution, there will be unimaginable technological breakthroughs in the world, such as personalized medical treatment through genetic data, coordination of distributed autonomous agents and Unlock the data generator for monetization methods that have never been explored before. (Block rhythm BlockBeats Note: Ze byte is 2^30 times TB, ie 1ZB=10.7TB)
However, if today's isolated data structures cannot be rapidly upgraded, the proliferation of available data and the efficiency gains of machine learning algorithms may soon lead us to a nationwide monitoring of capitalism, a dystopian future: politicians not only Being able to predict how things will happen, we can also use our emotions to “being kindly” to make decisions we have not yet made. In fact, they can act in the most accurate way for the future they foresee, and their goals are not necessarily disclosed to the public, nor necessarily to our own goals. Decentralized data architecture will not only prevent technology giants and other data monopolies from gaining such universal power, but will also enable individual participants to take advantage of this new wave of applications to improve their quality of life . At the same time, users of new applications can control their privacy and participate in financial returns.
The novelty of TOKEN and cryptocurrency economics
A fundamental problem that has plagued various network architects has been the mismatch between the value created by the network and the value acquired by the ownership structure. The value of the shareholding structure comes from future cash flows, which are net profits generated by the ability of centralized companies to generate revenue from customers. This is a system that works well for commercial companies that sell goods and services: Apple sells high-end hardware, Netflix and Spotify sell monthly membership. However, when equity models are applied to networks where core value lies in low-cost distribution and user-driven content creation, there is a real risk of differentiation: Twitter has difficulty realizing the content created by its users, and Facebook has to turn to a near-reverse Utopia's panoramic prison, in order to truly realize its value based on the user base and open source network. When the online community begins to generate valuable content, users of the online community are transformed from the customer into the product itself. At this time there is a fundamental mismatch between the value of community users and commercial companies: a business entity attempts to capture the full value created by the user community, while the user community itself does not receive any financial rewards.
Jumping out of the centralized network of equity-controlled equity firms in the control network, and instead modeling the network as a digital economy model with local certification, we can not only increase the value gained from it, but also distribute the value it generates to the real Value creator. In this digital economy, network scarcity is represented by a certificate, which is used to motivate distributed people, machines, and other participants to reward their contributions to the network, such as managing valuable resources, work content, and utility. Expressing the digital scarcity of the network (such as computing power, labor, content contributions, or community governance) as a digital pass allows for continuous network upgrades and unlimited flexibility. These certificates become programmable digital software that connects humans and the assets they own – both virtual (such as personal data) and physical (such as real estate). What these passes can achieve is a smart balance between users, developers, resource providers (such as miners) and capital providers (such as investors) through virtual currency economics, a cutting-edge approach to incentive design. Intrinsic benefits and utility. Clarifying the scarcity allows people to subvert to the subversion of ownership, which in itself transcends purely digital assets, and existing assets will have the potential to improve liquidity, transparency, access, compliance and taxation. This will promote the existing assets to pass the certification and ultimately lead the new encryption capital market.
A few decades ago, we witnessed the transformation of data and communication content from analog signals to digital distribution. Everything from data creation and distribution to monetization can be reimagined. The impact of digital on newspaper, television and film content is obvious: new giants like Netflix and Spotify have emerged, and companies like Blockbuster and Kodak have either been marginalized or completely gone. We are now convinced that the impact of the pass on ownership is as great as the impact that digital has had on content.
Classification of certificates
Into the world of pass, we can divide it into three core categories according to different characteristics: currency and commodity, utility-based and security. Considering that individual pass tokens may have several features at the same time, or evolve different characteristics over the life of their underlying network, we now summarize these features as follows:
The value of a value-based storage (SoV) certificate relies on its characteristics of confrontational review and equal transactions to ensure that its stored value is completely unrelated to any other market, commodity or currency. For example, Bitcoin, Monroe, and Zerocoin are slightly different in terms of transaction speed, network security, and network privacy. These value-storage cryptocurrencies are closest to the equivalent of real money. When considering the quantitative theory of money, they can use the exchange equation (MV = PQ) to understand their dynamics.
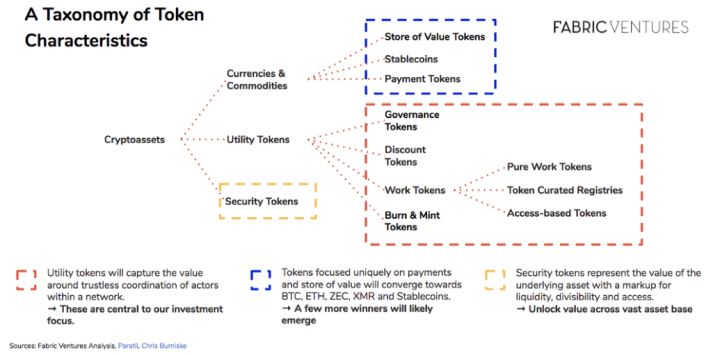
The goal of Stabilizing Coins is to separate volatility from cryptographic assets and to provide a digital asset that can be linked to fiat currencies such as the US dollar, which are primarily used as accounting units and trading medium. Three of the categories include:
b. Collateral – over-collateralized by cryptographic assets such as Ethereum.
C. Coinage Tax Shares – Re-create an algorithmic central bank that maintains stability by controlling supply and demand leverage.
Payment-based certificates are the simplest and most iterative types that are often enforced into the network as the only way to provide digital assets on the network . As a result, payment-based certificates have almost become the “money” in the virtual digital economy, even though they have not become more investment, liquid or stable enough to be a means of value storage. Conversely, in the future equilibrium, the payment pass will be closer to a working capital, and users will try to minimize working capital due to the opportunity cost. Therefore, they are likely to have very high rates, but the value accumulation is very low. Due to the nature of the source code (replicable and divisible), these VSI models are highly risky to run, they may be forked or replaced by the same protocol, which also allows them to pass appropriate value Save the pass for payment.
A securities pass is a representation of the virtual currency of an asset, which includes traditional commodities, stocks, art, and any kind of encrypted collection . The former relies on a strong guarantee of ownership of the underlying asset, can be valued based on the value of the underlying asset, and has a premium in terms of liquidity, severability and availability. The latter often represents a scarce encrypted digital asset that is as if it were an art or real estate, meaning that the value of the asset itself is limited, and the creator's reputation, its position in the digital landscape, and the overall demand for the asset. Determined its price. (block block musicBlocks Note: CryptoKitties belong to this category)
Governance Pass allows its holders to vote on how the network works, where developers are going to focus, and when software upgrades should be implemented . As the number of companies running on the network and the number of transactions processed continue to increase, the value of the network will increase, and the impact on network development will become a scarce resource. In fact, in such a network, the price of voting rights is likely to grow exponentially as the value of the network it protects increases. This type of pass feature usually needs to be combined with other types of pass-through designs mentioned earlier.
The discount pass gives the owner the right to discount when purchasing assets provided by the digital network. Buying a discount pass is equivalent to buying a coupon and is entitled to a fixed discount percentage of all economic activity within the network. As the value of the network increases and the number of transactions increases, the holder of the certificate can demand a greater discount. This pass-through design actually simulates a usage fee that can only be provided in the form of a web service (not involving money payments).
Work-based certification is based on the idea that service providers need to “share risks” to encourage them to provide high-quality work for the network. Whether it is an objective job (such as computing resources) or a subjective job (such as a qualitative rating), the service provider is obliged to invest a certain amount of the certificate into the network in exchange for the right to provide profitable work. If the job can be completed "correctly", the service provider will receive the fee paid by the user (not necessarily the local pass). Conversely, if the service provider misbehaves, their share will be cut and assigned to other service providers. As the amount of network usage grows, there will be more jobs that are immediately profitable or profitable in the future, which will increase the number of service providers who wish to deliver these jobs. Therefore, the demand for these work-type certificates will increase, and because their supply is relatively fixed, the price of such certificates will increase with the use of the network. (block block musicBlocks Note: PoW class tokens belong to this category)
The architecture of the Destruction & Foundry Equilibrium is based on two simple features: network users use the pass to pay for the service, but they do not pay for the pass, but destroy it (in dollars); The new pass (calculated by local pass) will continue to expand. The users of the network refer to the service provider for each of the destroyed certificates, and they will receive the newly generated certificate distribution as the paid fee. Therefore, when the usage of the platform increases and the number of passes consumed by users exceeds the number of passes issued through inflation, the supply of certificates will be reduced, thus pushing up the price of each pass. (block blockBlocks Note: USDT belongs to this category)
What role does the investor take?
Investors who invest in this large-scale pass-through model must assume a role that shifts from a simple capital distributor to an active participant in the network. From community building to pass-through projects, to actively operating nodes, to actively managing mobile positions, venture capital funds active in this area will soon be required to participate in network operations. This is not only fulfilling their fiduciary responsibility, maximizing the return on capital of their investors, but also helping to guide their investment network on the right track. The ambitious founders are well aware that the road to lasting success is tortuous, and they will first choose patient partners with patience. These patient collaborators will inject capital into their networks and work, and only when the number of nodes available in the network is at a minimum will they attract a specific user group or other stakeholders through targeted sales or short passes.
The most active investors will continue to participate in all aspects of the network during the investment period:
Staking: As the equity certificate (PoS) or the entrusted equity certificate (DPoS) network goes online on the mainnet, the holder of the certificate can provide the bank with a profitable job as a share (transaction verification, calculation, arbitration, transcoding) Or provide security) and receive rewards from the network (such as block rewards) or users (such as transaction fees). In a DPoS network, an operator within the network can perform the work as a service to obtain a portion of the payment, and the pass holder can delegate/bind the pass to the operator. (Blocked BeatBeats Note: You can check out the current popular Staking project at https://www.theblockbeats.com/pos)
Voting: Many networks are using their passports as a governance tool, whether through simple pass, second vote or mobile democracy, the pass gives their holders a say. Long-term investors will participate in the governance process of the network and direct it to the direction that they are most interested in.
Management: Through the General Management Registry (TCR), early investors in such networks need to actively participate in the management process while maintaining the high quality of the registry and marking the quality of the people involved in the management.
Running nodes and simple network usage: Since investors themselves may also be users of the network, they may actively build early use case iterations for the network. Their use of the network includes running nodes in the network for data-driven tracking purposes and actively participating in the network economy (such as purchasing services/assets), which will be one of the first to build an ecosystem on top of the network.
Europe: Where the Force is located
The number of developers is big and the academic strength of more than a hundred years
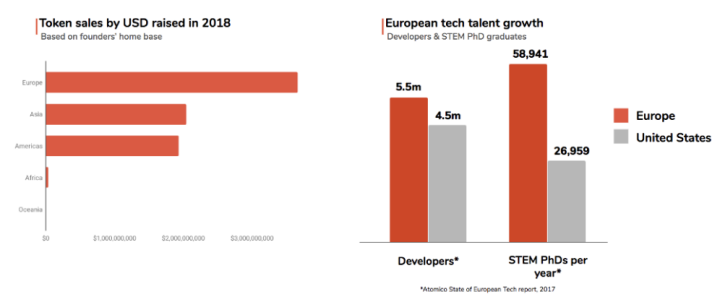
A large number of blockchain developers and technical talents come from Europe with a strong academic tradition, where hundreds of years of technical academic achievements have been born. Among the top 10 technology universities in the world, Europe has 5 exclusive schools, and the number of PhDs in STEM in Europe is twice that of the United States. According to Stack Overflow, Europe has 5.5 million developers, compared to 4.4 million in the US. Europe has not lacked technical talent, but historically, the main employers of these developers and technical talents came from the banking industry. It was not until the financial crisis of 2008 that these technical talents decided to flee the industry. Now, with the wave of democratization of this capital, these European technical talents no longer need to emigrate to the United States to raise funds and establish global companies. The result is that entrepreneurs from different corners of Europe have created significantly more value than any other region in the world: in 2018 alone, entrepreneurship projects in Europe raised $4.1 billion, while in Asia and the United States. The project raised $2.3 billion and $2.6 billion, respectively.
Use distributed teams from the beginning
As a continent of 50 distinct countries, European startups have become accustomed to working in a distributed team and building teams from a global perspective . From the outset, any European startup has recognized the need to develop an international expansion roadmap to avoid falling into the trap of its own small domestic economy. Diversified and multinational teams have become the standard setting for European startups, and London, Berlin, Paris and Amsterdam have become centers of technological innovation. We call this phenomenon "the technological renaissance of European city-states."
Deep-rooted counter-culture tradition
The greatest advantage in Europe may be due to the history of the past few centuries it has. Although the centralized business model is in line with Silicon Valley's ideals, namely a dense capital pool and a narrow and consistent ideology, the decentralized network model is more in line with Europe's deep-rooted history of political division and the consequent counter-cultural movement. Europeans have experienced two unimaginable catastrophic world wars in their own homes. European families have experienced communism and/or fascist dictatorships, and Europeans have split in the Cold War for more than 40 years. Europeans have always lived under the rule of totalitarian regimes that destroyed the notion of privacy and freedom of expression and regularly seized personal belongings and assets from their citizens. Decentralized networks will of course give individuals practical operational benefits, but at the same time have the hope of curbing the nightmare of the entire European society, which Europeans have experienced directly and violently in the past century.
Supervisory first
From a regulatory perspective, the EU has been at the forefront of its efforts to promote GDPR, such as the right to protect consumer digital data, and to open the financial system's PSD2 for the benefit of its users . In addition, competition between countries in the blockchain sector has begun to provide the clearest and most popular regulatory framework for new business models and governance structures for decentralized networks. The French Minister of Economy publicly stated that France will not “miss the revolution in the blockchain” and will become the global center of ICO. Switzerland has published a very clear regulatory framework for a pass-based network. The Chancellor of the Exchequer has published an Encrypted Assets Task Force to create a constructive regulatory framework for the CV. The small European countries, Malta and Liechtenstein, are pushing the management approach more fully at full speed, trying to become the global hub for decentralized networks and related businesses. In the more common use of data, the United States is known for its unregulated use of artificial intelligence for business-driven use, while China is known for the excessive expansion of totalitarianism that artificial intelligence can cause. There is now a saying about the "third way", that is, moral artificial intelligence, Europe may take the lead in trying this new way. This path builds on the framework provided by GDPR and combines the power of artificial intelligence to actively absorb the innovative cryptography to provide more personalized service while still respecting personal privacy. (block BlockBeats Note: EU Payment Service Revision Act 2 (English Payment ServiceDirective 2: PSD2))
The Fabric's Action Plan

As a venture capital fund, our primary goal is to select the best and most discerning entrepreneurs and technicians as partners in the areas of concern. In the next chapter of this article, we will briefly outline our approach to achieving this goal and how to increase the value of the network over time.
Grassroots procurement
The wave of technology has enabled new business models to thrive on new technology platforms, but the shift to decentralized data networks can enable monetization within the framework of the network's basic protocols, that is, in the application and business layers. Can make a difference. Thus, contrary to the wave of technology in the past, this new wave of technology allows more early value creation to be concentrated in the technology infrastructure layer built by developers for developers.
As major technological advances between Web 2.0 and Web 3.0 are gradually integrated into successful applications, consumer-facing applications can be iterated at minimal time to increase usability . Consumers will overcome some of the psychological barriers that previously felt unnatural in use cases, thereby fostering new usage habits. New market strategies and distribution formats will provide full support for new products and new markets, such as financial incentives, token airdrops and decentralized app stores.
We believe that in the next 2-3 years, most interesting projects will be concentrated in the infrastructure layer : development tools will serve development teams in areas such as smart contract libraries and data management frameworks; basic tool innovations for these blockchain networks will Drive Web 3.0 transformation for individual and institutional investors and provide underlying protocols for computing, storage and data privacy. (* Block Rhythm BlockBeats Note: In 2018-2019, a large number of underlying public chain projects appeared, and they did very well)
Therefore, as investors we will focus on sourcing innovative projects from developers, refer to their Github project, use this as a basis for judging whether they have the ability to develop and adopt leading technologies, and evaluate their decentralized applications. Fit in the stack. Our venture capital team will continue to catch up with the times and actively transform. In the future, our biggest investment will be invested in (and contributed to) the hackathon, rather than through entrepreneurship promotion activities. In this era of software control and open source, the developers are the new behind-the-scenes, and they are the ones we will spend time with.
The time to subvert the industry is ripe
It is undeniable that Bitcoin introduces a viable digital value storage method that can even serve as a substitute for government legal currency and gold. By combining a limited supply with a constant ledger book, we believe that this wave of technology will bring a host of new opportunities, not just a new currency. In the financial sector, we believe that compliance will be automatically embedded in the transfer of each asset. Credit scores and premiums will be dynamically adapted to a large number of data sources distributed across the globe, and the concept of the entire capital market will be modular. Processed as a basic programmatic financial element: an open, unlicensed building block that can be easily assembled into any financial application, using data sets that can be imagined by anyone Assets in the market.
Similarly, there are significant opportunities in redefining supply chain management, including inventory tracking and origin verification across multiple vendors, as well as automated credit financing and auditing. Especially in the automotive sector, this shift has opened up a set of operational and interactive systems with new possibilities across automotive data sharing and vehicle tracking across manufacturers. Online, the universalization of universality makes it possible to make global ownership of digital assets. Although it involves only simple encrypted collections at first, the process will inevitably evolve towards subject identity and certification. Peer-to-peer data, software licenses, and work providers can be revived into their true form, without the need for AirBnB or Uber to get a slice of each transaction.
Because of the lack of trust between people, there are still a large number of middlemen in our transactions today. By abstracting the elements of trust, decentralized networks will not only fundamentally change our business operations for all existing departments. The view, and will also introduce a new business model based on the original business model generated by the P2P environment.
Active network participation
As we mentioned earlier, the role of investors in this area is also undergoing fundamental changes. Simply locking and regulating our assets will not only miss the potential rewards of a dramatic increase in the network, but in many cases, even the negligence will damage the project itself. These digital assets are designed to motivate all participants to participate in the process of value creation: from providing capital to working and actually using it.
Proactive network engagement can take the form of block verification in a PoS network transaction in exchange for block rewards, or mining a pass in the Merkle mine. In addition, you can focus on providing the network with the ideal resources available in exchange for user fees, such as storage resources, data resources, or registry management. By designing appropriate incentives in these networks, individuals and professional service providers will quickly deliver services to earn returns and expenses. In a competing decentralized network, network providers will follow the footsteps of network participants, who are likely to flock to a network of many network providers to form a chicken or egg. The problem of raw chicken. In addition, if you look at it from a vacuum, you will find that there is a risk that participation in early network development is not an economically viable option: relying on transaction costs in a network without transactions, or before there is no buyer. The ocean protocol network (the ocean protocol is a block-based data exchange protocol for unlocking data and providing users with fair results) provides data streams that will incur losses. Except for early investors, no rational actor will cater to this particular scenario. Because the return on venture capital funds is mainly achieved by maximizing the likelihood of exceptional success for each investment, the potential for us to achieve exponential results in the network exceeds the supply and development network. The sunk cost. Therefore, we intend to help the network we invest in to crowdfund their supply providers, not limited to internal selection or proxy, and we will openly commit ourselves to the network projects we invest in, the networks they build. Active participation. We've outlined how to run nodes in the Ocean Protocol, provide data for data streams, and work with the companies we invest in to prepare for their network startups.
Accidentality in acceleration
We believe that extraordinary things can happen by actively participating in community value creation and connecting smart people together. By immersing ourselves in this community, we not only find the best opportunities at an early stage, but we also create a network that contributes to the successful growth of our portfolio. To this end, we have organized a series of events with different forms and purposes. The purpose of each activity is to bring together a specific group of people to solve specific problems, including:
Large conferences like CogX: Focus on introducing Web 3.0 to a wider audience, showcasing the latest in research and development, and helping businesses, governments, and investors adapt to emerging business models;
Founder's Annual Summit: An intimate gathering to showcase the progress of each project in the portfolio and proactively match these projects to other partners in the ecosystem;
Talent Dinner: We will take the initiative to match talented engineers, product designers, cryptographers, community builders or operational stars with projects in our portfolio.
Fabric House
We are building a Fabric home and are firmly committed to bringing together the smartest developers in London around us and working together to build a decentralized data network. Due to the nature of open source software development, most projects are distributed teams, and there is no solid foundation. We believe that for developers building decentralized networks, flexible collaboration spaces not only provide opportunities for inspirational collisions between projects, but also become one of our most valuable resources. Similarly, whenever we stay in Berlin, we are residents of FullNode – a space for collaboration between Gnosis and Cosmos for blockchain projects.
General Market Status Report
In January 2018, we released a regular release of the Census Market Status Report, focusing on the quantitative trends of the CIS ecosystem, as well as qualitative analysis of major developments in the field, in-depth studies such as the evolution of funding mechanisms, and insight into the global cryptocurrency center. Trends, understanding development activities that leverage market corrections and regulatory environments in emerging markets. This report not only helps us stay ahead in the ever-changing European and global arena, but also enables us to be attracted to them by attracting mature and emerging projects, exploring the talents of the ecosystem, academic and industry associations.
The report has been translated into 4 languages and has been cited by more than 100 media publications and well-known interviews, including university lectures. The reports of these two versions have become an important reference for understanding the development of this field. In the future, we intend to supplement the report with more regular newsletters (including selected pieces of data).
How does Fabric recruit?
As in the Web 2.0 era, talent is the driving force for innovation in the decentralized Web and the scarce resource for the best projects to compete directly with each other. Since our goal is to invest in the project at the beginning, recruiting for the team will be one of the top priorities we can participate in. We are building a well-planned community of talented engineers, product managers, and community builders to programmatically match them to related projects in our portfolio. First, we use an internal social mapping platform to proactively identify potential candidates through Github, Twitter, Reddit, and other networks, and tailor them to the projects, locations, interests, and reputations they have previously participated in. recommend. In addition, we regularly host a series of events and dinners for developers, with a focus on further cultivating offline physical communities and allowing projects in our portfolio to share their vision and collaborate.
Not limited to known investment vehicles
We have been keeping pace with the rapid changes in investment tools over the past two years, and certainly will not evade further tool iterations in the future. From equities, certificates to SAFTs, SAFTEs and securities passes, the milestone value-adding investment tools that can promote governance are still being improved. In order to avoid being tied to any technical constraints in the future, Fabric Ventures insists on the agnosticism of asset forms. We will not ignore new investment tools, and naturally we will not miss opportunities. We will try more tools and apply them to network participation, regulation and liquidity management.
Correctly treating liquidity
Despite the considerable liquidity of the market, Fabric Ventures will be patiently investing in digital networks for a long time . We have invested in teams that are building significant technology and continually improving user adoption, which can take decades.
However, a highly liquid market does provide our portfolio with day-to-day pricing and double the value of the undervalued positions we already hold . Unlike holding traditional stocks, as the venture capital fund ends at the end of a project's life cycle, the certificate will be easier to sell and will not have a negative impact on the project. As cryptocurrency exchanges are fully regulated and may include a chain compliance framework, we are fully capable of selling passes to qualified investors in the open market without having to promote IPO or project acquisitions while retaining over-the-counter transactions. Larger buyers are buying options for the pass. It is because of this liquidity that our venture capital funds also have the opportunity to make way for strategic participants in capital or networks with different risk/reward perspectives, which may ultimately increase the value of the remaining certificates. If we believe that a team or project has deviated from our direction during our investment, or is unable to promise a return corresponding to the level of risk, then we may also choose to sell a successful project, or be forced to quit quickly. These “liquidity models” are still in areas that require further development and iteration, just as these investment instruments are like a “bifurcation” in the broad sense of the venture capital model itself.
in conclusion
The new wave of technology-centric waves centered on blockchain technology not only represents the intergenerational transformation of computing architecture, but also the transformation of organizational principles. A new wave of people-centric services intertwined our unprecedented intimacy with our daily lives. In order for humans to believe that their machine partners will not abuse the ever-increasing data torrent, we need privacy and incentives driven by cryptocurrencies. mechanism. We believe that building a Web 3.0 with flexibility, security and privacy protection from the technology infrastructure, development tools and data management framework has a long way to go. To support this vision, Fabric Ventures is adapting the patient risk investment model to make our investments more responsive to development projects for decentralized networks – selecting the most daring technicians and communities at an early stage, in their overall project development and The operational phase provides full support and is an active participant in the network they are building.
Original author: Fabric Ventures-The Fabric Ventures Investment Thesis
Translator: Block Rhythm BlockBeats 0x4
* Block Rhythm BlockBeats prompts investors to guard against high risk.
Editor's Note: The original title is: Web 3.0 Era Investment Logic: The Investment Philosophy of Fabric Ventures
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Read the article Bakkt: cryptocurrency of the New York Stock Exchange
- After approving cryptocurrency mining, will Iran become a global “mining paradise”?
- Viewpoints | Several major issues that Bitcoin still needs to solve in 2019 (I)
- Zhu Jiaming recommended: CFMI pass financial model and stable currency mechanism
- Bitfinex and Tether insist that there are no New York users, and their IEO projects are falling.
- Academic to big coffee | Hu Jie: Blockchain is just a tool, awesome for finance
- I read through Ethereum 2019: Ecological development is too fast like a tornado






