Analysis | How will fragmentation technology achieve blockchain expansion?
In this paper, we will take the fragmentation technology on the Ethereum blockchain as an example to analyze how the fragmentation technology will achieve blockchain expansion.

In this paper, we will take the fragmentation technology on the Ethereum blockchain as an example to analyze how the fragmentation technology will achieve blockchain expansion.
As we all know, the most commonly used blockchain is Ethernet, so understand why the Ethereum developer community wants to use fragmentation technology in Ethereum to help understand what fragmentation technology is and why fragmentation technology is a Welcome expansion solution.
- Heavy Coinbase plans to launch the IEO platform, while waiting for the opportunity to launch STO products
- Order Pizza Win Bitcoin Award, Domino's plan gives 100,000 Euro BTC
- Futures Exchange Industry 2019 Phase II Research Report
According to ETH Gas Station, in the Ethereum network, it takes about 1.78 minutes to add transactions to the Ethereum blockchain, 32 seconds to generate a new block, and an average of 15-20 transactions per second. It can be seen that the Ethereum ecosystem is an environment that is beneficial to miners, not to the user. If users want to prioritize their transactions, they must increase the cost of the transaction.
Low throughput, high latency and high transaction costs are the main problems facing Ethereum. Some services and applications that require scalability are not suitable for Ethereum network. The main reason for the low throughput of Ethereum is that each node has to deal with all transactions in the system.
What is the fragmentation technique?
Simply put, sharding is a partitioning method that distributes the computational workload and storage workload to the P2P network, so that each node is not responsible for processing all transactions of the entire network, but only processes its own partition (or Tablet) information.
To further understand the sharding, we start with the easiest way to achieve sharding. V God called this method "scaling by a thousand altcoins" in his article.
In this sharding approach, we don't just run a single blockchain, we run multiple blockchains, and instead of calling each chain a blockchain, we call it a shard. Each shard will have an independent network of certifiers or nodes, ie, a PoW mechanism mining or pledge voting mechanism to verify transactions and generate network participants for the block.
Some of the main challenges facing fragmentation technology
The first problem we found in trying to use the sharding technique was that since each shard had its own certifier, the security of a single shard was worse than the entire chain. For example, a blockchain with X certifiers and no shards, decides to hard fork into a sharded chain, and spreads X certifiers into 10 shards, the number of certifiers in a single shard It is X/10, so only 5.1% (51%/10) of the total number of verifiers is needed to destroy a slice.
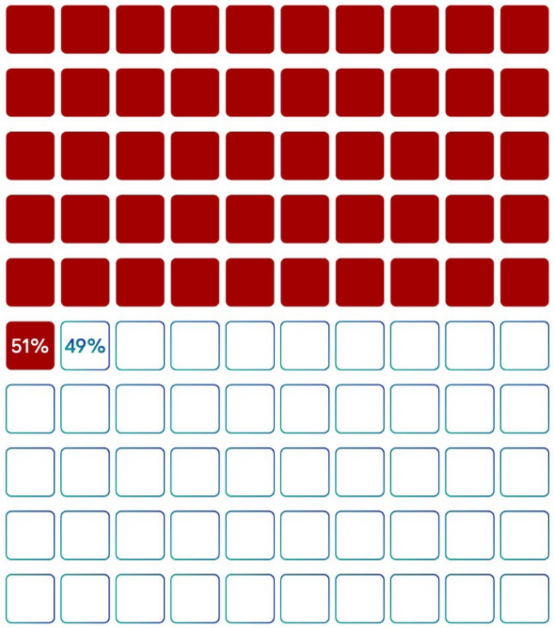
The second question we encountered was: “Who is choosing the verifier for each shard?” For a bad participant, if all 5.1% of the certifiers are in the same shard, then control 5.1% of the verifiers will cause bad conditions. If the verifier cannot choose which slice to verify, it is highly unlikely that the 5.1% verifier's participants will get all the verifiers in the same slice, greatly reducing their ability to compromise the system.
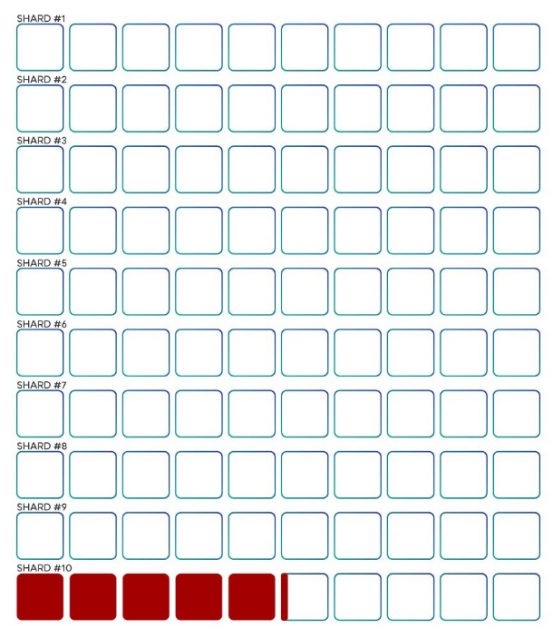
In fact, almost all slice designs rely on some randomness to assign nodes to slices, and both randomness and verifier allocation require calculations that are not specific to any particular slice. To achieve this calculation, almost all existing designs include a separate blockchain that performs the operations required to maintain the entire network.
This chain is called the Beacon Chain in Ethereum. It is responsible for generating random numbers, assigning nodes for fragments, receiving information updates (and creating snapshots), processing proof of rights (PoS), and various other functions. .
The beacon chain also has some shortcomings. Because the beacon chain needs to do some accounting calculation work, and these calculations are proportional to the number of fragments in the system, the more the number of fragments, the greater the computational workload of the beacon chain. This has the same problem as when no fragmented network is used: low throughput and high latency, so there is an inherent scalability limitation in fragmented networks.
However, the structure of the slice network does have a multiplicative effect on any improvement of the node. Because any increase in node efficiency will enable nodes to process transactions faster, and if all nodes running the network process transactions at a rate that is four times faster, each shard can handle four times the amount of transactions. And the number of fragments that the beacon chain can maintain will be four times that of the previous one. From this point of view, the throughput of the entire system will become the previous 4×4 = 16 times.
How to split data into pieces?
Let's first look at the nodes that perform most of those transactions on the blockchain:
1. Process / verify transaction
2. Propagating verified transactions and completed blocks to other nodes
3. Store the history of all transactions
As the network evolves, nodes need to be able to keep up with the demands of the network and grow as the network grows;
1. As the number of transactions that need to be processed continues to grow, each node is required to add more computing power.
2. As the number of transactions that need to be relayed continues to grow, nodes need more network bandwidth when relaying transactions and blocks;
3. As the state increases, nodes need more storage space when storing data.
It can be seen from these three points that data storage will increase regardless of whether the transaction volume per second and the transaction volume of the relay increase.
Although many people have proposed sharding storage instead of sharding transaction processing, some projects have implemented sharding of transaction processing (rather than storing shards). The most common shard type is called For "state sharding", in the state shard, the nodes in each shard are building their own shard chain. The transactions contained in this chain will only affect the local state in the global state of the shard. This means that the verification in the shard only needs to store the local state and only need to execute and relay those transactions that affect the local state.
Source|hackernoon
Author | Tiaan Wolmarans
Translation|First Class Warehouse Annie
Compile|First Class Alonso Chen
The copyright of the article belongs to the original author, and the translation is provided by the first class. Please keep the preface information for any reprint.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- QKL123 market analysis | Bitcoin risk avoidance highlights, long-term still bullish (0911)
- Hong Kong's anti-acquisition new deal will take effect, and the "coin stock" of the fire currency will be renamed as a risk
- Ling listen to the micro-public bank blockchain open source observation: throw the code out, take the trust back
- Jimmy Song: All those who are not optimistic about Bitcoin will eventually escape the "true incense" theory.
- Blockchain expansion is booming, and CasperLabs has completed $14.5 million in Series A financing
- The big discriminating concept of hard disk mining: PoC VS IPFS (Filecoin)
- Suppose you have 500,000 DAI, would you choose to deposit in Compound?




