Blockchain and Distributed Privacy Computing Industry Report
We selected three different technology paths for distributed privacy computing projects, namely ARPA with secure multi-party computing solution , Trias with Trusted Execution Environment (TEE) hardware support solution, and comprehensive integration with distributed cloud computing and TEE . The program's iExec, as an analysis case.
At present, all three projects have achieved certain results in terms of landing, but there is still a certain distance from large-scale promotion. In addition to the limitations of the level of technological development, how to optimize business-scenario-based, how to improve the industry's awareness and acceptance of new technologies are all limiting factors.
Summary of key points
1. With the development of blockchain technology, its functions have gradually expanded from the point-to-point electronic cash system to different fields. As an important topic in the blockchain, privacy protection is also enriching and expanding its own meaning – from just ensuring the privacy of transaction privacy, it has gradually added privacy protection for data ownership and use rights.
2. In order to keep the calculation process fair and equitable, and to avoid the risk of data leakage to third parties, projects involving privacy calculations often use a distributed system architecture .
- Algorand on the line, which is the market value of 100 billion, is the opportunity still a trap?
- Making money, it’s really related to IQ – Turing Award-level funding Algorand
- Facebook is in a rush, and Ruibo is facing the giants.
3. ARPA is a project for distributed privacy computing through secure multiparty computing (MPC). At present, ARTRA test network version 1.0 ASTRAEA was officially released in March 2019. This version is a Layer 2 privacy computing solution based on Ethereum.
4. ARPA's MPC encryption calculation scheme implements multi-party addition and multiplication calculation in ciphertext state through secret sharing, partial homomorphic encryption, and Beaver circuit randomization technology. However, in the current technical environment, the speed of multi-party security computing and plaintext computing still has a gap of 1-2 orders of magnitude. ARPA defines itself as a Layer 2 solution that can provide privacy computing services in different public chains in the future.
5. Trias is a low-level public-chain project for distributed privacy computing through the Trusted Execution Environment (TEE). Trias first test main network has been launched in Q2 in 2019, the official version of the main network Leviatom layer is planned to be launched in Q4 2019.
6. The total system design of Trias's three-power separation plays a certain role in guaranteeing the fairness and impartiality of the calculation process. It combines the heterogeneous TEE (Trusted Execution Environment) technology and the Heterogeneous Consensus Graph (HCGraph) to construct a trust system that is open to the whole network, which is convenient for users to select the most trustworthy TEE node. Calculation.
7. iExec is a project that provides distributed privacy computing by combining distributed cloud computing with TEE. iExec launched iExec V3 Enterprise Edition in May 2019, allowing customers to access the iExec network to sell personal computing in exchange for rewards. At the same time, the newly added Data Wallet feature also makes it possible for users to rent their own data usage rights.
8. iExec's distributed cloud computing uses the Desktop Grid to collect underutilized computing and storage resources on the network, allowing the client to perform large-scale parallels at a fraction of the cost of traditional supercomputers. And distributed computing. In order to protect the privacy of user data, iExec further integrates with TEE to realize data leasing, trading and realizing.
9. At present, all three projects have achieved certain results in terms of landing, but there is still a certain distance from large-scale promotion. In addition to the limitations of the level of technological development, how to optimize business-scenario-based , how to improve the industry's awareness and acceptance of new technologies are all limiting factors. We will continue to pay attention to the follow-up development of the project.
Industry background
As a new technology paradigm that combines decentralization, transparency, and non-tamperability, the blockchain initially aims to achieve peer-to-peer transactions without third parties. Although privacy protection is an important feature in the initial design, the open and transparent nature of the blockchain determines that anyone can guess the address of the account based on the transaction association record, and it is difficult to truly make the transaction anonymity.
Faced with the increasing demand for privacy protection in the cryptocurrency market, the market has gradually emerged a new pass for anonymous privacy protection through different technology paths. The more well-known ZK-SNARKS-based Zcash, ring-based signature Monero, and based on Innovative encryption protocol MimbleWimble's Grin and Beam.
With the addition of Turing's complete scripting language, developers can begin to design different functional applications on the blockchain, which directly contributed to the gradual integration of blockchain technology with other different fields, such as financial credit reporting, product traceability, The Internet of Things and other fields. At the same time, the concept of privacy protection in the blockchain has also been integrated into the new connotation, gradually expanding from merely ensuring the anonymity of transactions to the privacy protection of ownership and use rights of native data .
Under the premise of protecting customer privacy, the simultaneous collection of data and application data has become a new opportunity and challenge in the blockchain industry. In this context, the current common solution is to discover the value of data under the premise of protecting data privacy through privacy and security computing. Technically, it can be roughly divided into secure multi-party computing (MPC) and secure execution environment (TEE). Kind of path.
At the same time, in order to ensure the fairness and credibility of the entire calculation process, blockchain projects involving privacy computing have adopted a decentralized distributed organizational structure to avoid the risk of data leakage to third parties. Among the projects that have already landed, there are representative ARPA based on MPC pure cryptography, Trias based on TEE hardware technology, and iExec combining TEE and distributed cloud computing. This report will focus on a brief introduction of each project, the technical realization path and project progress.
2. Technical introduction
Distributed privacy computing is inseparable from three dimensions: privacy, performance, and versatility. However, the currently used secure multi-party computing (MPC), secure executable environment (TEE) and homomorphic encryption technologies do not meet the optimal solution of three dimensions at the same time, and are made between many features. A certain trade-off. In view of the design of the iExec project, in addition to the TEE, the table calculation is considered, and the technology used in the introduction of the specific project will be introduced separately.
Homomorphic Encryption
Homomorphic encryption refers to encrypting the original data, and then calculating to obtain an output. After decrypting the output, the result is consistent with the result directly calculated from the unencrypted original data. In the actual operation process, each step of the calculation of homomorphic encryption involves a large number of encryption operations, resulting in a rapid increase in computational complexity as the number of steps increases.
This problem directly leads to the fact that in practical applications, homomorphic encryption can only support the addition of homomorphism or multiplicative homomorphism with a limited number of operations to achieve Somewhat Homomorphic Encryption, but it is difficult to support addition and The multiplication operation completes the Fully Homomorphic Encryption with unlimited number of operations. At present, in the process of secure multi-party computing, some homomorphic encryption will be incorporated.
Multi-Party Computation (MPC)
Secure multi-party computing solves the problem of collaborative computing protection between a group of untrusted participants, enabling the parties to complete the aggregate computing function of the data without revealing any local data privacy. According to the application scenario, the current security multi-party computing can be divided into secure two-party computing and secure multi-party computing. The former is mainly implemented by cryptographic techniques such as Garbled Circuit, Oblivious Transfer and Boolean Circuit, but it is limited by the number of participants, which limits its potential for promotion in practical applications.
The technical implementation path of secure multi-party computing is mainly realized by secret sharing, homomorphic encryption, encryption circuit, inadvertent transmission and the like. However, considering the actual calculation process requires a large number of calculations to achieve homomorphism, at the specific implementation level, multi-party computing will reduce the complexity of encryption operations through inter-node communication, at the cost of increased communication complexity. On the whole, the current multi-party computing scheme has a gap of more than one to two orders of magnitude compared with the plaintext calculation.
Trusted Execution Environment (TEE)
Different from the way of implementing privacy calculation through cryptography, TEE mainly solves the problem of secure computing through hardware settings, and has been widely applied in mobile phones, cloud and other fields, such as Intel's SGX, Huawei HiSilicon. TrustZone, ARM's Trustonic, etc. Specifically, TEE provides an isolated and encrypted secure area Enclave with a trusted random data source and custom computing instructions for data privacy operations.
Compared with the first two digital encryption technologies, TEE has a wider application, and the computing efficiency can reach the level of practical application. However, users need to trust that security vendors that provide TEE hardware will not have “remaining back door”. At the same time, due to the existence of Spectre and Spoiler vulnerabilities, TEE is also facing the risk of buffer side channel attacks, resulting in the data isolation of security and non-secure areas being broken, resulting in the leakage of private data.
3. Project introduction
3.1 Introduction to the ARPA Project
The ARPA project mainly builds a verifiable chain-based multi-party secure computing network through the MPC technology path, breaking the data island phenomenon where data is dispersed among enterprises and institutions, allowing different data providers to not disclose their own data and without trusting third parties. In this case, reliable results are obtained at a lower cost.
In terms of technical design, the secure multi-party computing adopted by ARPA is not specific to a specific algorithm, but is implemented by combining some homomorphic encryption, secret sharing, and confusing circuits. At the same time, as a layer2 architecture, ARPA can access different public chains to meet the privacy and security computing requirements of different nodes in each public chain, which greatly expands the application scope of ARPA.
3.1.1 ARPA system design
As a layer 2 solution, the computing tasks of the ARPA network come from various blockchain networks. ARPA will deploy proxy intelligent contracts on each major blockchain network. Before each calculation is initiated, the ARPA computing network will randomly select a certain number of nodes. The nodes that are selected and willing to participate will need to mortgage some ARPA certificates to formally participate in the calculation. . Random selection has curbed the possibility of pre-calculation collusion between nodes to a certain extent; the mortgage mechanism increases the cost of participating in computing nodes, reduces the intention to steal data, and does not perform computing tasks.
According to ARPA's experimental results, in the case of 100 compute nodes, 95% of nodes need to be colluded to have less than 1% chance of successful attacks. ARPA's cryptographic design combined with economic design can fully eliminate potential attack intentions. When the calculation starts, the data of each participant will be transmitted and calculated in the form of ciphertext fragments in the ARPA network. After the end, the calculation result and the corresponding certificate will be transmitted back to the smart contract that initiated the request. During the whole calculation process, each participant only You will be exposed to the results of the calculations and the data you own. The specific calculation process of ARPA can be roughly divided into two parts – the preprocessing stage and the calculation stage.
3.1.1.1 Chain-based security calculations – pre-processing
The pre-processing stage occupies most of the MPC's entire calculation process, mainly preparing various cryptographic calculations "raw materials" that will be used in the calculation process, including the "ternary and random" required for secret sharing and multiplication operations. Array", used to calculate and validate the global MAC key and distributed MAC key. The MAC key is the source of ARPA network verifiability and is critical to the trusted verification of calculation results. Since a lot of data is consumable, it takes a long time to prepare when there are many arithmetic nodes and the arithmetic logic is complicated. Currently, multi-party calculations are about 1 to 2 orders of magnitude slower than plain text calculations.
3.1.1.2 Chain-safe computing – calculation phase
After the pre-processing is completed, it will enter the calculation phase. ARPA's multiparty calculation involves several steps: secret sharing, computational evaluation, and revealing results.
Secret sharing : Secret sharing will ensure the privacy of data at the level of input data distribution. First, the node participating in the calculation sends a random value to the data provider; then, the data provider adds the received random value to its own random value to obtain the total random value, and subtracts the total random value from the input value. The result is distributed to the remaining compute nodes; each compute node receives its confusing input value and adds its own local random value to get the input value it needs. After this operation, only the data provider has the original input value, and the data provider is guaranteed to be safe if the data provider does not do evil.
Calculated evaluation : After receiving your own input values, each computing node will start local calculations. Because the secret sharing algorithm used makes the input values additive, the addition and linear operations can be performed locally, but the multiplication operations require the parties to perform certain information exchanges. Since the compute nodes cannot directly pass their own input values, the Beaver circuit randomization technique is used to convert the multiplication operations into linear operations and randomized public variables. This process consumes the triples generated during the preprocessing phase. Since the triples are published after use, each triple can only be used once, which means that complex operations will require a large number of calculations in the preprocessing phase. "raw material".
The computing nodes in the ARPA network continuously calculate the information check code (MAC) of the variable during the calculation process to verify the integrity and correctness of the calculation. The message check code can verify that a message is generated from the owner of the corresponding MAC key and that the information has not been changed. If the compute node is not calculated according to the specified calculation process, the generated MAC will not pass the verification.
Revealing the result : After all the participants agree to end the calculation process, the participating nodes will broadcast the secret shared value of the result and the corresponding information check code. After verifying the correctness and integrity of the calculation, the protocol will be global. The secret share values are merged and the plaintext results are reconstructed. At this time, the information check code can achieve the verification process by the calculation of the constant complexity. The decoupling of the verification and computational processes allows the verification process to be easily performed by third parties such as blockchain nodes. After the verification is correct, the calculation result will be submitted to the requester to end the calculation task.
3.1.2 Progress of the ARPA project
ARTRA Test Network version 1.0 ASTRAEA was officially released in March 2019. This version of the test network is based on the Ethernet 2 Layer 2 privacy solution. At the same time, ARPA also cooperated with the top public chain projects in China and successfully implemented privacy calculations on the chain. In the future, the ARPA team plans to launch Testnet 2.0 (ATLAS) in Q2 in 2019, and launch the main network on Q3 in 2019, and continue to exert its strength in enterprise clients. In the application landing, according to the official information released by ARPA, ARPA has already reached cooperation with Sinochem Group, Kongming Technology, Qiming Co., and Yunxiang Blockchain, and actively promoted strategic cooperation with large financial and insurance institutions.
ARPA will provide solutions for industries such as finance, insurance, and commodities in a multi-party joint risk control, blacklist sharing, and joint model analysis based on specific scenario requirements. In addition, ARPA is also involved in the development of data standards for secure multi-party computing. As a core participating company, ARPA has participated in the writing of a number of cryptographic protocols. The standard has been jointly released by China Information and Communication Research Institute, Cloud Computing and Big Data Research Institute in June 2019.
3.2 Trias Project Profile
TRIAS provides a trusted execution environment for native applications by combining heterogeneous TEE techniques with graph calculations. In the design framework, Trias consists of a three-layer sub-system, which corresponds to the three-power separation structure in the real society. Through the mutual cooperation and restriction of power, Trias implements the fairness and justice of the computing environment.
Specifically, Leviatom, the most basic layer, is responsible for administrative power. It can provide a trusted computing power for the Trias ecosystem through heterogeneous technology aggregation, and the combination with graph computing and Gossip protocol provides the Trias trust matrix. The foundation is to help users to filter trusted TEE nodes for calculation.
The second layer of Prometh is responsible for legislative power, providing a traceable software development framework to enable full lifecycle maintenance, documentation and management services for smart contracts from development to formal operation. The third layer of MagCarta is responsible for the jurisdiction, managing Trias' overall contract system, achieving unified programming and scheduling of the entire platform's native applications, and using economic models to motivate and coordinate the interests of the various parties. Specifically, the technical architecture and calculation process of Trias is as follows:
3.2.1 Trias technical design
Leviatom : As a base layer, it provides a secure computing environment for the entire Trias ecosystem. In order to reduce the difficulty of using TEE in blockchain, Leviatom uses the heterogeneous consensus graph algorithm (HCGraph) to realize the full integration of heterogeneous networks based on TEE trusted computing and trust networks based on Gossip protocol. Each node will verify the credibility of the nodes around the record and propagate between different nodes by means of the Gossip protocol. As the verification information is repeatedly verified and verified throughout the network, HCGraph gradually depicts the "conspiracy default" model of the global node. The efficient and accurate positioning of the trusted nodes is realized, and the nodes are suppressed from doing evil behaviors.
Figure 3-1 Schematic diagram of the Leviatom node
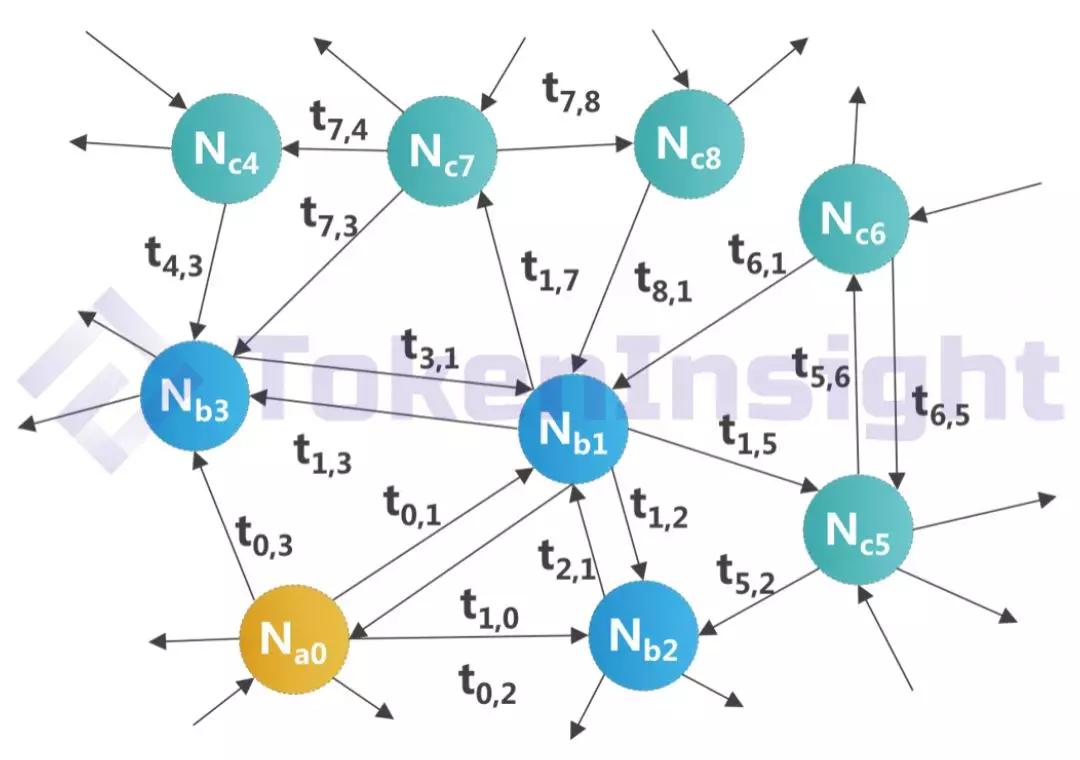
Source: Trias White Paper
Specifically, the Leviatom power network can be visually represented by the above figure. Each dot on the graph can be regarded as a node with a TEE operating environment, and the direction line header indicates the direction of the verification relationship between the nodes. According to the division of labor, each node is responsible for three different types of responsibilities, forming a logical three-tier computing system.
The first layer uses TEE technology to periodically check the correctness of its surrounding nodes and record relevant historical information.
The second layer uses the Gossip protocol (and the Gossip about Gossip protocol) to collect information collected by the surrounding first-level computing nodes and to propagate among other nodes that have obtained their trust, and gradually builds Trias internals during the information transfer interaction. The trust matrix allows users to easily select the most trusted node in Leviatom to handle contract tasks, thus ensuring data privacy. At the same time, the characteristics of the trust transmission mechanism also has a strong deterrent effect on the evil motives of the nodes. To put it simply, whenever a node wants to do evil, it needs the cooperation of the upper-level trusted nodes in the network, and these "cooperative nodes" need to be further cooperated with the trust nodes. As the nodes in Leviatom gain more trust, the more nodes that need to be coordinated, the higher the cost of doing evil.
These high-trust nodes form the third layer in Leviatom. This layer node can execute arbitrary programs, perform consensus verification on the execution results, and participate in the competition of the final billing rights. In the Leviatom network, any node can implement different combinations of three types of responsibilities, and realize the flexibility and efficiency of the entire network through the market adjustment mechanism.
Prometh: The DevSecOps framework for general-purpose applications on the Leviatom platform, which enables traceability, verifiability, and zero porting of applications, and is responsible for the quality and standards of smart contracts on the chain. Prometh plans to monitor and manage the software developed from Trias on the whole life cycle from design, development, testing, operation to destruction. It realizes the automatic winding and automatic security analysis of the code, and builds a universal and timely software for the software running under the Prometh framework. The traceability system of feedback facilitates the customer's verification of all aspects of the contract used, and also helps build confidence in the security of the software running in the Trias system.
MagCarta : It is the application layer of Trias, supporting Turing's complete set of smart contract languages for developers to write smart contracts to implement complex business logic. Specifically, the Leviatom network can be understood as a base.
Basic operating system. The Prometh framework is a different kind of development tool on the operating system for developing various basic software modules. The MagCarta language is a contract language that splices the different modules developed in Prometh into Decentralized Enterprise Services (DSaaS). At the same time, MagCarta is also responsible for paying compensation fees and insurance fees for Leviatom nodes and Prometh program developers, to achieve incentives and security for computing power, procedures, and data contributors.
3.2.2 Progress of the Trias Project
In terms of technology development, the first version of Trias test main network has been launched in Q2 in 2019. The official version of the main network Leviatom layer plan is launched in 2019 Q4. On the application landing:
In December 2018, Trias (Beijing Eight-component Information Technology Co., Ltd.) and Fujian Association of Southeast Asian Marine Economic Research Institute reached a cooperation to jointly establish a joint research and development of the blockchain research center of Fujian Province ASEAN Marine Economic Research Institute, the initial plan to blockchain technology Upgrade the China-ASEAN Seafood Exchange platform. This cooperation has promoted the combination of marine economic industry and blockchain technology, and has important applications in the fields of product traceability and privacy calculation.
In March 2019, Trias (Beijing Eight-component Information Technology Co., Ltd.) reached a strategic cooperation with Jiangbei Dou Substation Technology Co., Ltd. (hereinafter referred to as Beidou Substation). The cooperation process will use Trias' trusted network technology to assist Beidou to establish a substation big data IoT system, including substation big data platform and substation equipment sales platform. This cooperation is an innovative model that combines blockchain technology, multi-party security technology, big data, data traceability and other emerging technologies. It also pioneered the blockchain + substation industry and successfully realized the blockchain technology. Entity economic empowerment has also accumulated valuable practical experience for the future of Trias in other fields.
In March 2019, Trias (Beijing Eight-component Information Technology Co., Ltd.) and Soochow Securities jointly hosted the topic of "Intelligent Information-based Financial Information System Trusted Operation and Maintenance System". After completing the scientific research and exploration, the prototype has successfully landed the Soochow situation-aware platform. The platform is based on three key technologies: Trusted Computing (TEE), blockchain, and artificial intelligence. It is a comprehensive intelligent security operation system (DevSecOps) that integrates defense, detection, response, and prediction. Application and infrastructure security and partial security gateway automation needs.
3.3 Introduction to the iExec Project
iExec is a distributed cloud computing project based on Ethereum, which aims to create a secure and scalable decentralized virtual computing platform. iExec allows DApp developers, data providers, power providers and users to be fair and free on their platforms. Trading. In response to problems such as network transmission congestion, rising usage costs, and huge heat loss in data centers, iExec proposes to use the Desktop Grid to collect underutilized computing and storage resources. Allows the client to perform large-scale parallel and distributed computing at a fraction of the cost of a traditional supercomputer.
After the iExec V3 Enterprise Edition upgrade in May 2019, the new version allowed the personal computer to join the iExec ecosystem and become a computing provider, lending computing resources for revenue. On top of this, iExec further implements support for Trusted Execution Environment (TEE) solutions, enabling data owners to run data on computers with remote built-in TEE components without fear of privacy leaks.
3.3.1 iExec Technology Framework
The core of iExec's distributed cloud computing technology relies on a mature, reliable, open source desktop grid computing middleware – iExec Core. The technology was developed based on XtremWeb, which was published by the company's founders during the French National Institute of Computer and Automation (INRIA). As the core component of the distributed computing system, iExec Core implements the functions of network resource aggregation, high fault tolerance, and shielding of the underlying heterogeneity of resources required for distributed computing.
Figure 3-2 iExec Plane Structure
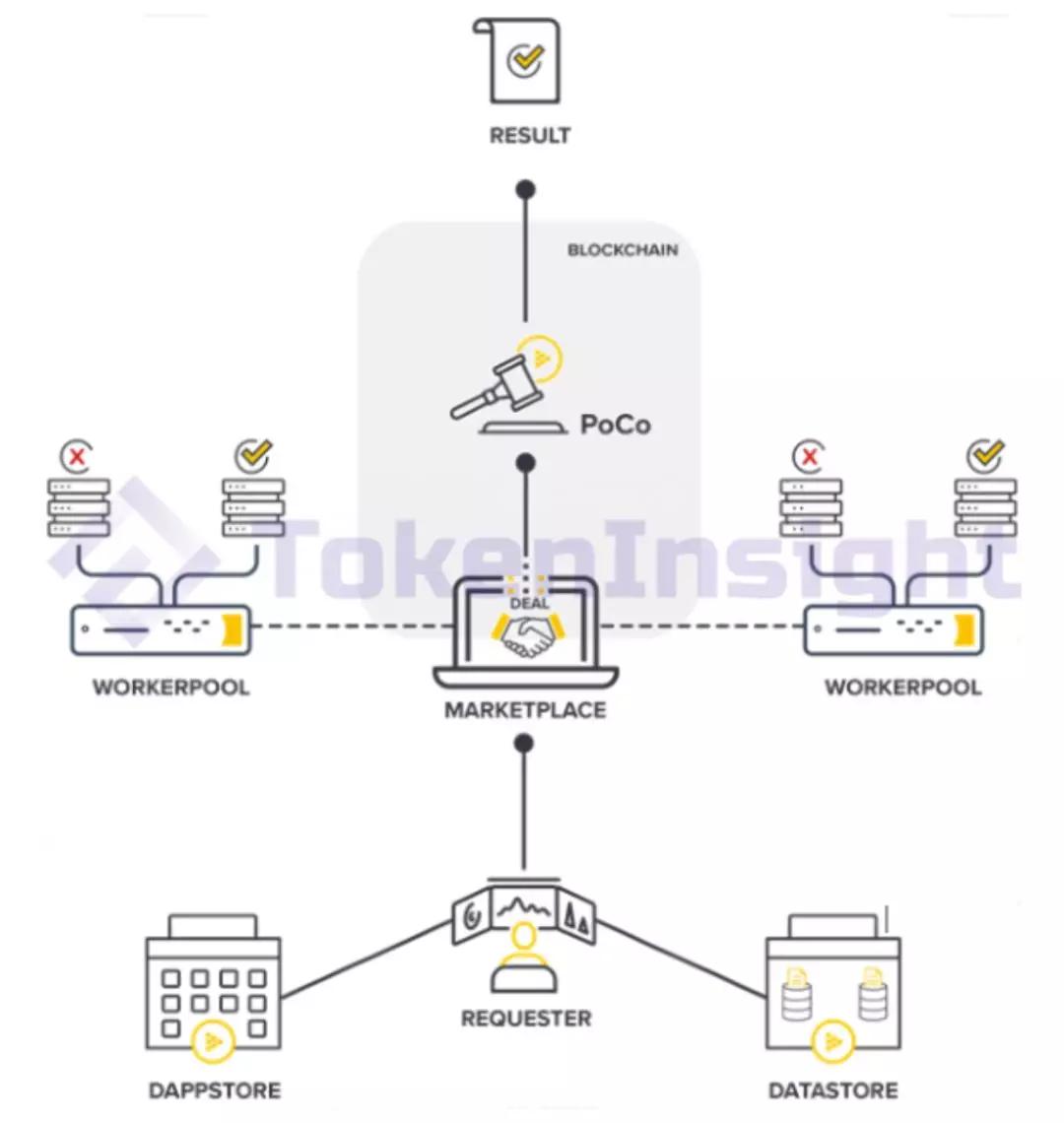
Source: iExec White Paper
Proof of Contribution: Using the characteristics of blockchain not to be tampered with, information transparency and decentralization, iExec also designed and built its own Proof-of-Contribution (PoCo), which established a set of publicity for the entire computing power. Traceable credit and settlement system.
Specifically, PoCo can be seen as a bridge between the virtual computing trading platform and the distributed computing system middleware (iExec Core). Whenever someone initiates a computing task on the platform, each node that meets the calculation conditions can participate in the pass through the pledge part of the iExec platform. If the node withdraws from the calculation, or even deliberately commits evil, it will lose the pledge certificate and its credit value will be impaired. After the calculation is completed, PoCo will determine whether the calculation result is valid based on the credit value of each node, and give a matching pass stimulus to the node providing the effective contribution.
Domain Specific Sidechain : As a general-purpose development platform, optimization of specific scenarios is not considered in the design process. If iExec's entire calculation process runs on Ethereum, there will be problems such as high cost of gas and low transaction processing efficiency. To better serve different business scenarios, iExec will specifically design a Domain Specific Sidechain to meet specific requirements that may arise during the computing process, such as parallel computing processing, low latency interaction, and so on.
Data Wallet, TEE : In the upgraded iExec V3 Enterprise Edition, a new data wallet feature has been added to allow data owners to monetize their holding data through leases. At the same time, the Enterprise Edition also provides Intel-based SGX privacy protection solution, the combination of the two greatly guarantees the security and effectiveness of the data rental market, allowing data owners to rent data usage rights without losing ownership. Ensure that data running on remote and untrusted computers is secure.
Even valuable and sensitive private data can be rented out through this technology, which can be widely used in medicine, 3D rendering, IoT data processing and other fields. At present, a number of "computing pools" that provide trusted execution environments have been deployed for users to choose from, including those in Alibaba Cloud, IBM, TF Cloud, and the like.
3.3.2 Progress of the iExec project
In terms of technology development, since the beginning of the iExec project in January 2016, the development progress has been in line with its roadmap plan. Has successfully included functions such as power lease, data lease, and trusted computing environment. At the same time, iExec also announced that the iExec V4 version will be released in late 2019, which will be a super-computed version that fully integrates GPU computing power. In the application landing, iExec not only extensively cooperates with industry companies such as Intel, IBM, etc., but also the development of iExec has received the attention and support of the French Power Group and the French National Investment Bank. The relevant events that are more significant are listed below:
In May 2019, iExec teamed up with Intel and the Enterprise Ethereum Alliance to release the Trusted Computing Standard V1.0.
In May 2019, Electricite De France partnered with iExec to test the operation of related programs on the blockchain. As the largest power company in Europe and the fifth largest in the world, the cooperation with the French Power Group will accumulate rich industry experience for iExec and also serve as a model for the blockchain + power industry.
In February 2019, the French National Investment Bank (Bpifrance) invested 2 million euros in iExec to support the commercialization of distributed computing.
In November 2018, iExec integrated IBM Cloud
In January 2018, iExec announced cooperation with the Shanghai University of Science and Technology's fog computing laboratory.
In January 2018, released an end-to-end solution for Intel SGX
4. Summary
Comprehensive analysis, the three projects have adopted different technical paths to achieve distributed privacy computing, and achieved some success in project landing. However, in the process of further promotion, the three also face different problems. Specifically,
ARPA is an MPC project based on pure cryptography and has many cryptographic studies as technical guidance. However, as a cutting-edge technology of cryptography, MPC is still in constant development. The more mature applications in the world are still limited to the use of MPC technology to distributed key management (such as the US unbound tech and Danish sepior).
In addition, from the cutting-edge theoretical research to the industry landing, especially to meet the needs of specific business scenarios, it often takes several years to transform, which puts high demands on the ARPA project's research and development capabilities, technology conversion capabilities and business understanding capabilities. .
Trias is an innovative project based on TEE for distributed computing. The consensus mechanism of heterogeneous TEE and graph computing will create a trusted computing environment with high trust. The concept of separation of powers also ensures the computational process on the Trias platform. Fair and just. But at the same time of innovation, Trias also faces many problems and uncertainties.
The first is TEE's own technical vulnerabilities (such as Spectre and Spoiler). The way Trias uses to avoid this kind of problem is unknown. Secondly, in the node that chooses to execute the code, although the node selection itself is built on trust. Basically, but this design will continue to be centralized in the long run.
iExec uses a combination of distributed cloud computing and TEE to implement privacy computing. Its core component, iExec, was developed based on the XtremWeb released by the company's founder during the French National Institute of Computer and Automation (INRIA), which guarantees the successful development of the iExec project. However, the main application of distributed computing in the past is still limited to large-scale scientific computing in specific fields. It is still unknown how much iExec can apply it to diverse business computing scenarios. At the same time, iExec still relies on a centralized and trusted organization such as Alibaba Cloud, IBM, TF Cloud to provide a secure and trusted computing environment, which means that iExec will face the same problem of centralization of power nodes as Trias.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- The "Six Gods" started, the net red ALGO was actually the Turing Award level "funds"?
- Yibang International IPO application failed, and the three major mining machine manufacturers failed to go public
- Coindesk: Monroe password punks made a final blow to ASIC
- The country's first blockchain government service platform is on the line
- Market Analysis: Before the Bitcoin 10,000 Yuan mark, the FATF issued a guidance on the encryption industry.
- Institutional capital flows into record highs! CME Bitcoin futures contract hit a record $250 million
- Getting started with the Facebook Move programming language






