Blockchain Technology Index | Defending Privacy: The Rise of Anonymous Technology
Guide
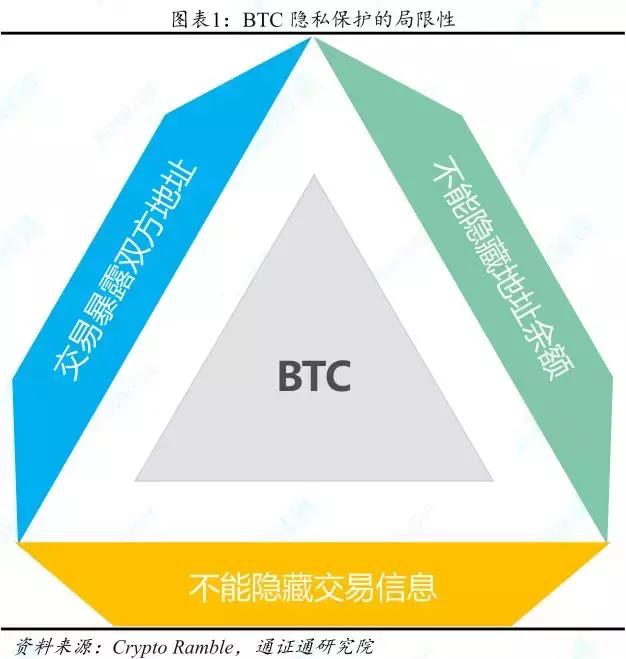
In response to the privacy issues of BTC, various anonymous certificates emerged as the times require, and quickly occupied a place in the digital pass market.
Summary
As a pioneer in digital certification, BTC has experienced ups and downs for ten years, and it has a good robustness and gradually reveals the limitations of privacy protection. In recent years, with the development of blockchain technology, privacy computing technology, cryptography technology, etc., anonymous certificates created by various emerging technologies to protect transaction privacy have emerged.
In December 2012, the first agreement on digital pass privacy issues, CryptoNote, came out. The protocol introduces two technologies: privacy address technology and ring signature technology, which provide privacy protection for data receivers and senders, respectively.
- We counted the price of Bitcoin in the past two years and found that it fluctuated the most during this time period.
- Security Events | MyDashWallet Online Wallet User Assets Theft Details Disclosure
- The US congressman candidate wants to send money, and the Federal Election Commission has promised.
In January 2013, BTC developer Gregory Maxwell proposed Coinjoin technology to improve the privacy of BTC. Coinjoin uses multi-signature technology. Traders need to independently distribute their signatures. Only those transactions that provide all signatures can be judged legally. Network reception.
In May 2013, Johns Hopkins University professor Matthew D. Green and others proposed the Zerocoin protocol. This agreement proposes to allow the destruction and re-generation of digital passes to ensure that the pass transactions are anonymized and that no trusted third parties are involved. In May of the following year, Matthew D. Green and others created Zerocash on the basis of Zerocoin and proposed a classic zero-knowledge proof method – zk-SNARKs .
In October 2015, Shen-Noether of the Monero Research Laboratory proposed RING-CT, a technology developed based on the CryptoNote protocol, which is a technology that conceals transaction amounts and speeds up transactions.
In July 2016, Tom Elvis Jedusorand proposed Mimblewimble, which retains the superior features of BTC based on the PoW consensus and is optimized for UTXO collections, which greatly increases the anonymity while greatly saving blockchain storage space.
Risk warning: regulatory uncertainty, anonymity or performance impact
table of Contents
1 Anonymous at the beginning – BTC's "Tier Feng"
1.1 BTC Privacy Policy
1.2 BTC's "Tier Front"
2.3 “Anonymous Pass” came into being
2 common anonymous technology
2.1 CryptoNote Protocol – the first digital pass privacy protocol
2.1.1 Privacy Address Technology
2.1.2 Ring Signature Technology
2.2 Coinjoin – Decentralized "coin" scheme
2.3 Zerocoin, Zerocash – a high-level proof in the field of cryptography
2.4 RING-CT – Successor to CryptoNote
2.5 Mimblewimble – Optimizing BTC's Magical Spell
1 Anonymous at the beginning – BTC's "Tier Feng"
In 2008, Nakamoto published the famous "Bitcoin: A Peer-to-Peer Electronic Cash System" (BTC: a peer-to-peer electronic cash system) and unearthed the first BTC in the following year. The second is from reality to reality. At that time, when the financial crisis broke out, people’s confidence in legal tenders was greatly reduced, and BTC’s characteristics of decentralized, anti-inflation, openness, irreversibility, and anonymous seemed to be in line with people’s The idea of an ideal currency.
1.1 BTC Privacy Policy
At the beginning of the BTC, the media and investors are mixed about digital certificates. Some people's concern is whether digital pass is a new type of "Ponzi scheme"; while others focus on the various superior characteristics of BTC, including decentralization, anonymity, irreversibility and so on. With the deepening of the understanding of digital pass, the public has gradually formed a consensus on the former – open source sharing, free viewing BTC does not have the typical characteristics of Ponzi scheme. However, BTC has gradually exposed some problems during its operation, one of which is privacy.
BTC transactions do not need to provide real information, just provide virtual information (address) that is not related to real information, but since the blockchain records the relevant address and amount of each transaction, the tracker can match in multiple transactions. The same address and associate them. For this reason, BTC's privacy policy is called "Pseudonymity."
In September 2017, the US federal authorities arrested the French drug lord Gal Vallerius at the Atlanta airport through the BTC address, which caused widespread concern at the time. Investigators found that OxyMonster, the dark drug, used the same BTC address several times to collect money, and 15 of the 17 outbound transactions of the address were associated with French citizen Gal Vallerius. Law enforcement noticed this clue, further analysis of open source data and then positioned Vallerius's Instagram and Twitter accounts, and compared the writing styles of OxyMonster and Vallerius to determine their identity.
In addition to privacy issues, the "kana" strategy also undermines the BTC's Fungibility .
1.2 BTC's "Tier Front"
Substitutability means that the independent units of an item are essentially interchangeable. Both gold and French currency are replaceable. The same weight of gold and equivalent denominations are equivalent, not because of gold. Whether pirates or banknotes have been circulated in the black market (the banknotes are numbered, but few people pay attention to them) and change their value.
BTC's "Kana" strategy has caused it to lose the "replaceability" feature. The openness, traceability and non-tamperability of transaction records is a feature of BTC's acclaim as a digital pass. The blockchain holds all transactions from the Genesis block to date.
But these characteristics have now become the "Tier Feng" of BTC. The holders never want to get into the trouble of being frozen by the relevant authorities. Therefore, the recipient of the transaction usually rejects the BTC whose income is “pollutiond” (for example, has had an illegal trading history), and is more inclined to hold a clean BTC, the most valuable of which is the BTC that flows out of the miners for the first time.
Note: Tyre Feng: The magic sword in Norse mythology, without any indestruction, but also cursed the owner to demise.
In order to strengthen the privacy of digital pass transactions, ByteCoin, a cryptographic certificate based on the development of BTC, came into being.
1.3 “Anonymous Pass” came into being
As the first anonymous certificate based on the CryptoNote protocol, Bytecoin uses the Private Address Technology (Stealth Address) and Ring Signature (Ring Signature) to address BTC's privacy flaws. Since Bytecoin, various anonymous certificates have sprung up and attracted many investors. The market value of anonymous passes such as Monero and Dash ranks among the top in all digital certificates (according to the market value of CoinMarketCap on June 24, 2019). Monero is in the thirteenth and Dash is in the fifteenth.
At present, the representative anonymous certificates on the market include Monero, Dash, Zcash, etc., which have been verified for several years, Zencash, etc., which are hard- shared by anonymous certificates , and digital pass circles such as Grin, Beam, and Dero . New darling. These anonymous certificates have breakthroughs in information technology, anonymous technology, cryptography, etc. The following will introduce the common anonymous technologies currently on the market.
2 common anonymous technologies
In response to the privacy issues of BTC, scholars around the world have conducted research, and many well-developed solutions have been proposed so far and have been applied in actual blockchain projects.
The more common anonymous technologies at present include CryptoNote, Coinjoin, Zerocoin (and Zerocash developed from Zerocoin the following year), RING-CT, Mimblewimble, and so on.
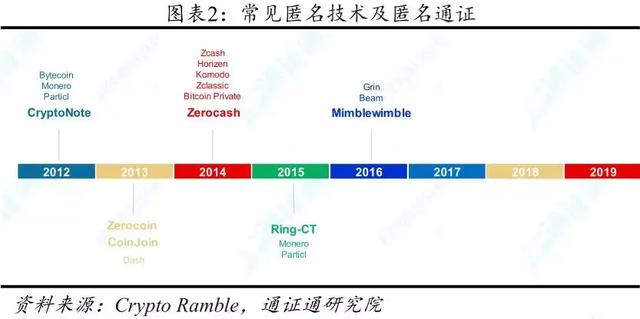
2.1 CryptoNote Protocol – the first digital pass privacy protocol
In December 2012, the first agreement on digital pass privacy issues, CryptoNote, came out. The protocol introduces two technologies: privacy address technology and ring signature technology, which provide privacy protection for data receivers and senders, respectively. In October 2013, the nominal author Nicolasvan Saberhagen updated the second edition of CryptoNote. There are many anonymous digital certificates based on the CryptoNote protocol, including Bytecoin, Monero and Particl (Monero and Particl use the RING-CT protocol, which is based on the development of CryptoNote).
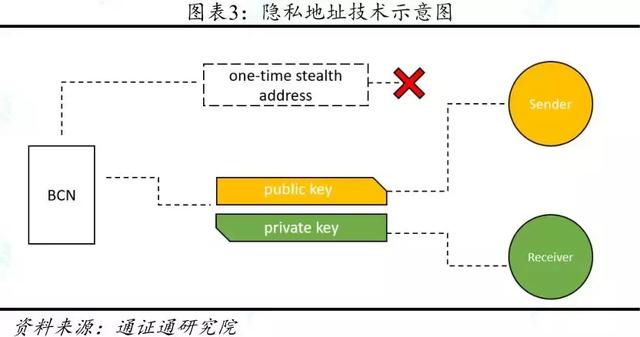
2.1.1 Privacy Address Technology
Privacy address technology is a technology that hides the actual transaction address. This technology mainly provides privacy protection for data receivers.
When a user conducts a BTC transaction, a standard BTC transaction record is generated on the public blockchain. The transaction record contains the recipient's address, and the BTC uses the pseudonym technology to protect the recipient's address privacy, but the blockchain's public transparency enables tracking. The ability to correlate all transactions for a particular pseudonym, which in turn may be traced to the actual trader in conjunction with other information and methods.
CryptoNote's private address technology uses a one-time occult address ( hereafter referred to as a confusing address) to reduce the association between different transactions, and the sender and receiver can confirm whether the transaction is valid by key.
Compared to other privacy policies, privacy address technology has the characteristics of multiple keys . The receiver has a private key b and a public key B (B=bG) , and G is a point on the elliptic curve. The sender obtains the recipient's public key B at the time of the transaction, and generates an obfuscated address P. The address consists of two parts, a part of which is generated by the receiver's public key B. This process adds a random number r owned only by the sender; part of it is the recipient's public key B.
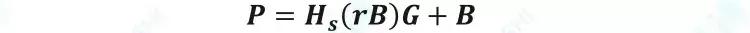
At the beginning of the transaction, the payer Alice obtains the public key B of the receiving party Bob, and combines the random number r to obtain the obfuscated address through the hash and ellipse algorithm. After the confusion address P is generated, it is recorded by the miner. The receiver can obtain the R(R=rG) of the random number r after the ellipse algorithm operation on the chain, and bR=brG=rbG=rB , according to which the receiver can generate the R , the private key b and the public key B. The same obfuscated address:
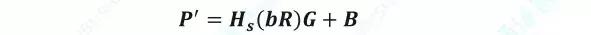
The receiver checks all transaction addresses on the blockchain with R , private key b and public key B to confirm the existence of its own transaction. Check the equation as follows:
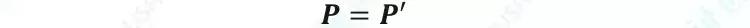
The privacy address technology uses a one-time hidden address, which greatly enhances the security of the transaction recipient and ensures the information privacy of the communication recipient.
2.1.2 Ring Signature Technology
Compared to privacy address technology, ring signature technology can provide privacy protection for data senders . Ring signature technology uses digital signatures that cannot be traced back to achieve digital pass-through transaction signature confusion . The signature is a signature of a group of senders of information, one of which is the true initiator of the message, and the rest comes from the blockchain network. The latter is extracted from the myriad signatures that have been recorded in the blockchain and is called decoy .
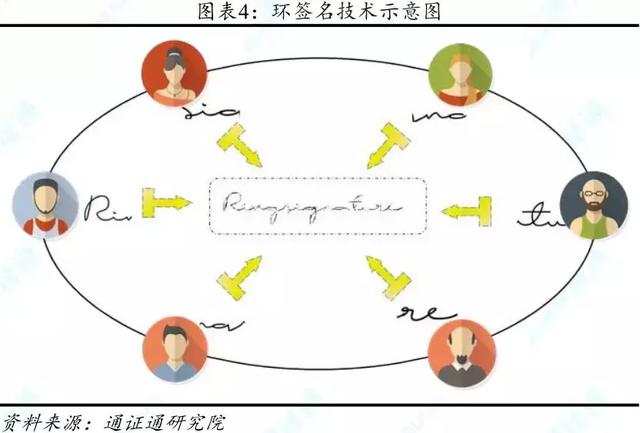
The ring signature technique involves a one-way trapdoor function in cryptography. The function is first a one-way function, which guarantees irreversibility through asymmetric algorithms (ie, forward calculation is easy and reverse calculation is difficult, such as function y=f(x) If it is known that x is easy to find y , it is difficult to know that y wants x=f^-1(x ). Secondly, it has a specific trapdoor (also called backdoor). If you know the trapdoor m, you can easily calculate x=f^-1(x) . In a public key cryptosystem based on a one-way trapdoor function, the public key is publicly identifiable and can be used to encrypt information, and only the recipient having the private key can decrypt the encrypted information using the private key.
Generate a signature. The ring signature is formed by computing the private key of the sender with a random public key on a set of blockchains. First, the sender obtains r confusing public keys Pi(i=1,2,…,r) from the blockchain , generates a random number xi(i=1,2,…,r) and encrypts it by r public keys. Generate yi(i=1,2,…,r) . Then select the random number v and generate ys by a specific algorithm (in this algorithm, v and yi are parameters). As the owner of the private key, the sender can easily calculate the xs using the private key and ys . The final ring signature P consists of the following parameters (where Ps is the sender's public key):
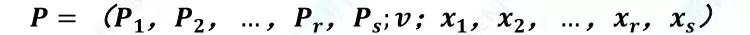
Verify the signature. The verifier uses the parameter xi(i=1,2,…,r) in the ring signature, and xs passes the corresponding one-way trapdoor function (ie, Pi, Ps ) to obtain the corresponding output value yi (i=1). , 2, …, r), ys , finally yi, ys through the inverse of the above specific algorithm to get v' , compare v = v' in the verification ring signature, if the equation is true, the ring signature is valid.
The ring signature technology adds indiscernible invalid information to the information transmission link, thereby protecting the sender's information privacy. The validity of the transaction information can be confirmed by verifying the overall signature in the signature verification process.
2.2 Coinjoin – Decentralized "coin" scheme
On January 28, 2013, BTC developer Gregory Maxwell proposed Coinjoin technology to improve the privacy of BTC, based on the “coin” technology.
"Coin" is a relatively simple pass-anonymous technology that combines the inputs of multiple traders and outputs them. Observers are unable to correlate to the transaction input based on the output of the coin, thereby confusing the flow of digital certificates. However, the early “coin” required the participation of trusted third parties and there were centralization risks and trust issues. Coinjoin developed on this basis is a decentralized blending scheme.
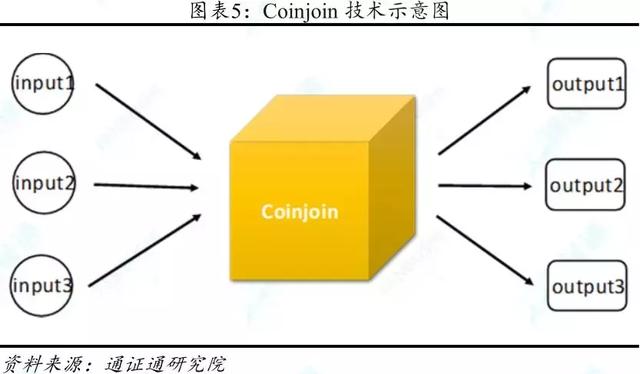
Coinjoin uses Multisig, and traders need to independently distribute the signatures. Only transactions that provide all signatures can be legally determined and received by the network. Otherwise, they will be returned to the individual assets.
Compared with the early hybrid service, Coinjoin can effectively resolve the third-party trust risk and avoid the possibility of third party theft and disclosure of mixed currency information. CoinJoin is the basis of the decentralized hybrid mechanism, which is applied by Dash in the mainstream anonymous certificate.
However, even if Coinjoin is not designed to be trusted by a trusted third party, a sufficient number of digital passes is required to ensure the effectiveness of the currency. This still leads to a dependence on the holders of the digital pass. The Zerocoin protocol proposes improvements to this problem.
2.3 Zerocoin, Zerocash – a high-level proof in the field of cryptography
In May 2013, in order to improve the shortcomings of Coinjoin's need for third-party participation, Johns Hopkins University professor Matthew D. Green et al. proposed the Zerocoin protocol. This agreement proposes to allow the destruction and re-generation of digital passes to ensure that the pass transactions are anonymized and that no third party involvement is required.
In May 2014, Matthew D. Green et al. created the Zerocash protocol based on Zerocoin. The agreement complements and improves Zerocoin with a high-level proof in the field of cryptography, the zero-knowledge proof method . Zerocash proposed a classic zero-knowledge proof method, zk-SNARKs.
As mentioned earlier in this series, zero-knowledge proof is a high-level proof of cryptography (see "Privacy Computing: Dynamic Encryption Technology – Blockchain Technology Vol. 8"). The certifier can prove to any third party that he or she does have specific data without revealing the private data. The zero-knowledge proof is characterized by completeness, stability, and zero knowledge. In theory, zero-knowledge proof is the best privacy computing technology with anonymity, and its academic capital is strong.
Zk-snark (Zero-knowledge succinct non-interactive arguments of knowledge) is a classic zero-knowledge proof method. The sender can prove the legality of the transaction to the verifier without revealing the details of the transaction amount and address.
The verification process of zk-SNARKs mainly consists of three parts.
First: abstract coding. The prover needs to prove to the verifier that he knows a fact, and this logic is abstracted in the first step as the prover needs to prove to the verifier that a polynomial holds. E.g:
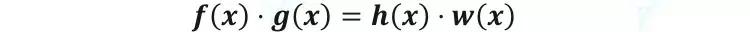
Second: simple random sampling. Although the verifier cannot directly confirm that the polynomial is true, it can be evaluated using the evaluation point. The verifier selects the random evaluation point s. If the equation is established at the evaluation point (ie f(s)⋅g(s)=h(s)⋅w(s) ), then the parametric polynomial has certain credibility. . Credibility can be continuously improved by selecting evaluation points multiple times.
Third: Zero knowledge proof. To ensure that the prover does not disclose security information by revealing the values of f(s), g(s), h(s), w(s) , the prover encrypts the above values using homomorphic encryption techniques. For example, the homomorphic encryption function E is used to encrypt the above values into E(f(s)), E(w(s)), E(h(s)), E(w(s)) , and the verifier is authorized to verify the encryption. After the value, if the encrypted value meets the following formula, the verification is successful.
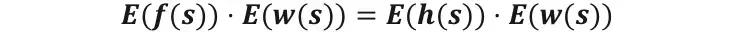
However, zk-SNARKs have two distinct drawbacks. First, it relies on a trusted initial setup. A digital pass transaction based on this method requires each pair of provers and verifiers to provide a set of common parameters for zero-knowledge proof, and this set of public parameters is set by the protocol developer. Having these public parameters means owning The right to falsification. In other words, zk-SNARKs cannot avoid developer risks, and developers may leak public parameters for different reasons. Second, the encryption technology of zk-SNARKs is based on elliptic curve ciphers, and current computers cannot be brute force hacked. But with the improvement of computer performance, especially the advancement of quantum computers, this method of not having quantum resistance may be violently cracked in the future.
ZK-stark (Zero-knowledge Scalable Transparent Argument of Knowledge), a knowledge-based, scalable, and transparent knowledge argument is under study. This method ensures that all parameters that generate proof are publicly and randomly generated, as well as quantum resistance.
2.4 RING-CT – Successor to CryptoNote
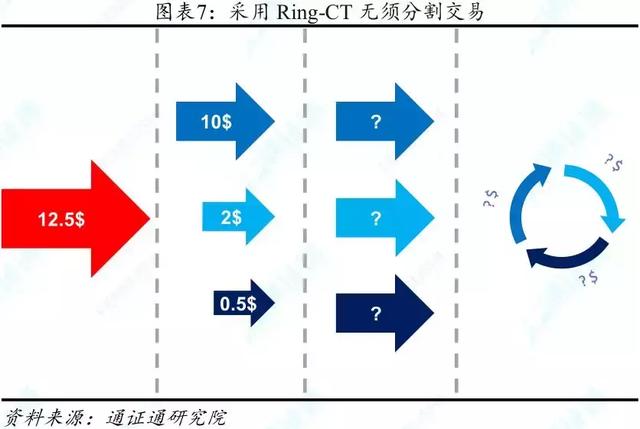
RING-CT (Ring Confidential Transactions) is a technique for stealing transaction amounts. The technology was presented in October 2015 by Shen-Noether of the Monero Research Laboratory. In the original Monero transaction, in order to ensure that the ring signature has sufficient data sources, the transaction often needs to be split into specific denominations to ensure the confusion of the ring signature technology.
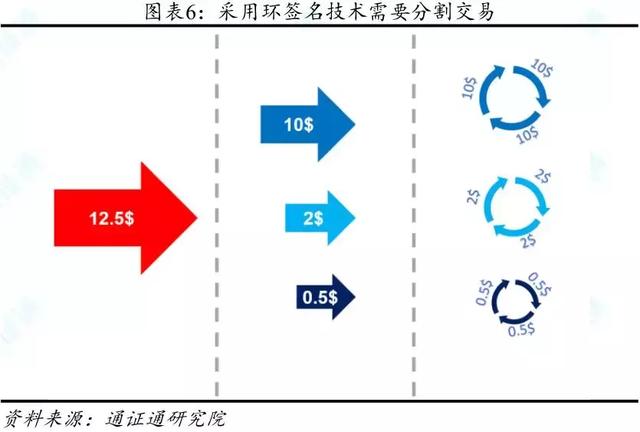
However, the amount of the transaction is also the privacy of both parties to the transaction. Based on this concept, RING-CT technology has been proposed and widely used. After applying the RING-CT protocol, the digital pass will only display the amount when it is awarded to the miner from the blockchain , and all subsequent transactions will mask the transaction denomination and convert to provide a number RCXXX as the transaction amount in the transaction.
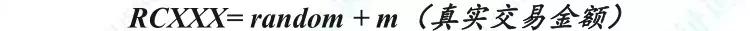
The transaction output consists of two parts, one is a random number, which is used to mask the real amount, which is automatically generated by the wallet; the other part is the real transaction amount. The miner cannot get a specific amount of the transaction from RCXXX , but can verify that the transaction input is equal to the transaction output according to RCXXX to confirm that there is no forgery to produce a pass. Throughout the process, neither the miner nor the rest of the observers know the exact transaction amount information.
RING-CT also solves the problem that ring signature technology needs to split transactions. The amount of public transactions weakens the confusing ability of the ring signature, and the hidden transaction amount can make up for this shortcoming. At the same time, since the transaction amount is hidden, there is no need to split the transaction, so that the transaction concealment can be improved, and the speed of digital communication can be accelerated.
2.5 Mimblewimble – Optimizing BTC's Magical Spell
Mimblewimble named the magic spell in Harry Potter and was proposed by anonymous writer Tom Elvis Jedusorand in July 2016 and further expanded by Andrew Poelstra in October 2016. The purpose of its research was to improve the privacy of BTC while saving storage space. Mimblewimble is optimized for UTXO collections while retaining the superior features of PoW based on BTC. The current digital certificate based on Mimblewimble is Grin and Beam, the new darling of the digital pass.
Confidential Transactions is a core technology of Mimblewimble. Its main principle is based on the following formula:
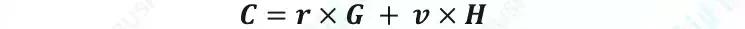
Where C (Pedersen Commitment) is the encrypted transaction amount obtained by the elliptic algorithm ECDSA. The miner uses the homomorphic encryption feature of Pedersen Commitment. Even if the specific input and output amount are not known, the encrypted value can still be used to confirm the input value is equal to Output the value to confirm the validity of the transaction.
Second, the miner used Range Proof to verify that the transaction value did not overflow, that is, the two parties did not create additional passes in a vacuum. For example, if Alice holds 5 BTCs and Bob holds 0 BTCs, then Bob cannot have more than 5 BTCs after the transaction.
Finally, Mimblewimble designed the Cut-through feature to optimize the miner's storage space, reducing the size of the blockchain. Over time, the blockchain will inevitably expand and bloat, but Mimblewimble can use the Cut-through to remove unwanted information and effectively compress the blockchain size. For example, BTC records two pieces of information on the blockchain:
1. Alice pays 1 BTC to Bob
2. Bob pays 1 BTC to Charlotte
In this example, the BTC blockchain records two transactions, the first transaction records the input from Alice and the output sent to Bob, and the second transaction records the input from Bob and sent to Charlotte. Output information. But after the transaction is completed, Bob's output and input information is expired invalid information. Cut-through technology allows the deletion of intermediate invalid information, which can greatly compress the blockchain volume, and the discarding of intermediate information also increases the privacy of the transaction.
However, it should be pointed out that although the current Mimblewimble-based projects Grin and Beam have achieved Cut-through, miners can eliminate the corresponding code as needed, so Cut-through does not conceive the idea of enhancing the privacy of digital pass transactions by deleting intermediate information. Fully implemented.
This article details the main privacy transaction techniques. In the follow-up topics, we will compare various privacy-passenger technologies and analyze the living environment and future development of anonymous certificates using various private transaction technologies.
Note:
For some reasons, some of the nouns in this article are not very accurate, such as: pass, digital pass, digital currency, currency, token, Crowdsale, etc. If you have any questions, you can call us to discuss.

General Education Institute × FENBUSHI DIGITAL
Text: Song Shuangjie, CFA; Tian Zhiyuan; Jin Jiahao
Special Adviser: Shen Bo; Rin
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Blockchain Xiaobian Adventures, I never thought I was picked up by the police…
- Diversity is a trend in Staking
- Dry goods | Shanghai Jiaotong University Professor Hu Jie dismantled Libra Libra: This is a new thing in the sun
- Blockchain financing in the first half of the year: the United States overtakes China, Hong Kong dominates Greater China, and Hangzhou presses Beishangguang
- Say that Staking doesn't make money, why do so many people play?
- Buy Starbucks with Bitcoin and hit Uber, this lightning network payment app will do it for you.
- 180 degree turn! The godfather of emerging market investment: If bitcoin goes up again, I will go buy it.





