Buckle attack, the infernal of the mine pool
Concerned about the small partners of the power of Jun, the power has not met with you for several days. Today, I want to talk to my friends about the things under the desktop in the mine. The so-called desktop is the means that can't be seen in the circle. The most used ones are when they attack each other.
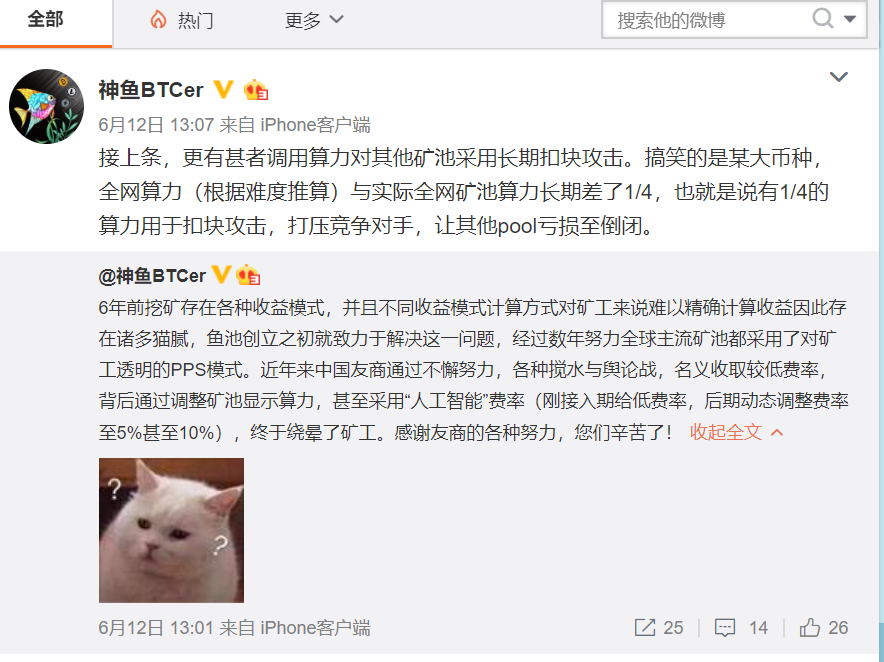
On the 12th, that is, yesterday, the founder of the famous mine pool (f2pool), the sacred fish, screamed, angering the power of the poor commercial competition in the mining pool in a “cuckle attack” attack on competitors’ mines. . Can let an industry amnesty can not help but publicly reprimand, the destructive power of the matter will certainly not be small, today we will talk about this "cuckle attack" that makes the mine ring can not help but what is it?
- Market Analysis: Bitcoin broke through the $8,000 mark, and the market sent out again
- The exchange was attacked on the line and was only attacked by John McAfee.
- Lightning Network helps mobile communications, how to send decentralized text messages?
One: People are floating in the rivers and lakes, there is no sickle.
Before we talk about the principle of “cuckle attack”, we need to understand the working mechanism of the mining pool. The so-called mining pool is a collection of decentralized computing power. The miners will focus on switching to the address of the mine pool and contribute to the share of the mine pool according to their own calculations. The most important role of the mine pool is to equalize the opportunity risk (lucky value) of miners mining, so that the income of small miners can be quantified.
The “cuckle attack” occurred when the miners in the pool had successfully dug up new blocks, and the miners chose to deduct the hash value and not announce it to the whole network. In this way, the overall mining output of the mining pool will be less than the theoretical output of the actual computing power. In the short term, it seems that the lucky value of the mining pool is decreasing. As a result, the income allocated to the miners in the pool will be significantly reduced, and of course the losses will include the miners who launched the attack. But the biggest impact is the reputation of the mine itself.
For the mining pool, such an attack can happen anywhere, anytime, but it is impossible to prevent. There is no way for the miners to directly identify the miners who initiated the "catch attack". It is only after the attack that you will be able to identify the abnormalities that have not been blocked for a long time. Because of the randomness of mining, this kind of screening often has the possibility of large-scale accidental injury, pushing their own users into the arms of their opponents, and finally discovering how they are all suffering from the enemy.
Almost all mines have suffered such attacks, and every successful attack is bound to cause huge economic losses to the mine. In the middle of this, whether it is a malicious attack or a counterattack party after being attacked, the rational choice of the mine pool is to take an indiscriminate blow on the premise that the enemy and the enemy cannot be locked. As long as the same loss occurs in other mines, I will not be at a disadvantage to retain the miners. Finally, the entire industry can only be in a situation where the melee is in a terrible balance.
People are floating in the rivers and lakes, there is no knives, some knives are for themselves, some are for friends, and some are inexplicable. Sometimes you may be right, but it is a victim of collective melee.
Two: The injured one thousand lost eight hundred, what is the picture behind it?
Although the "cuckle attack" is hidden and difficult to prevent like a river and lake killer, it does not mean that miners can do evil. After all, this is a war that kills one thousand people and loses one hundred. The first thing to premeditate an attack requires a lot of computing power to enter the target mine pool to achieve the desired effect. Secondly, in order to conceal, it must be calculated that it must be lurked for a period of time before it can be launched. Attacks, in the end, even if the successful investment of the attack itself will cause a lot of damage to the attacker planner.
The “cuckle attack” is demanding and costly, but according to the sacred fish, some of the mainstream public chains even have up to a quarter of the computing power dedicated to launching “cuckle attacks” against the mine. There is some hidden motivation behind it.
On the surface, the "catch attack" of the mining pool and the guidance of timely preferential activities, through the internal and external pinch-off methods can indeed induce many small miners to shake their positions and switch to the enemy camp. Isolated, it seems that this behavior is at best a well-planned business war.
However, if they are linked together, the same forces are always being manipulated behind the attack, and the different mines that accept the miners’ transition are actually in the hands of the same group of people, and things may be much more complicated. This means that large consortia that occupy the advantages of capital and scale can already indirectly grasp the computing power of retail investors through leverage, and form an actual monopoly of computing power.
In fact, in any public chain, in addition to representing income, computing power also represents the voting right of this community autonomy, playing a decisive role in the choice of major directions. Retail investors are usually used to collectively exercise voting rights on major issues in units of mining pools.
When a large number of retail miners are scattered in the many mining pools in the hands of the same consortium, the consortium can control only 51% of the calculation power in each mining pool, and obtain the voting rights of a large number of retail miners, so that there is no flaw. Take a public chain in your own hands.
The rivers and lakes have always been bizarre, and the offensive and defensive warfare against the “cuckle attack” is still going on. The heavy responsibility of guarding the essence of the blockchain to decentralize has already fallen on every shoulder of the miners. I hope that everyone will maintain enough vigilance and awe.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Is Bitfinex's platform coin LEO more valuable than BNB?
- Many startups are paying close attention to what kind of model will Singapore's virtual banking licenses adopt?
- Market Analysis: Bitcoin failed to form an effective breakthrough at 8130, and the market outlook remains to be seen
- Ethereum comes out and the story behind it
- Yang Guang, Research Director of Conflux: From Modern Cryptography to Blockchain
- In line with policy, Block.one hires former head of Congressional Relations to support its blockchain activities
- Twitter Featured: How many bitcoins are left for you before halving?