Chengdu chain security: stolen killer whale users may have sustained attacks
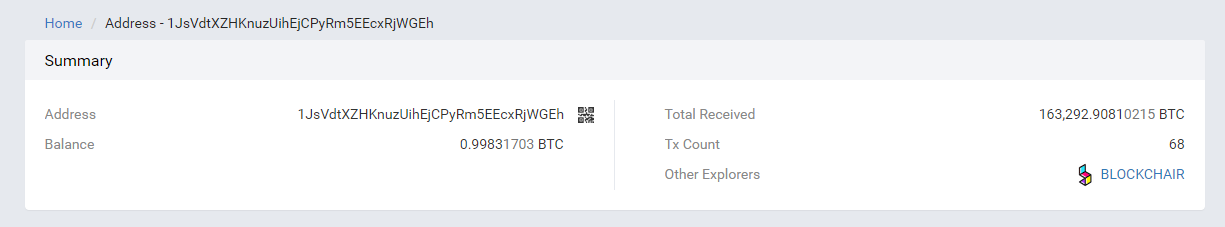
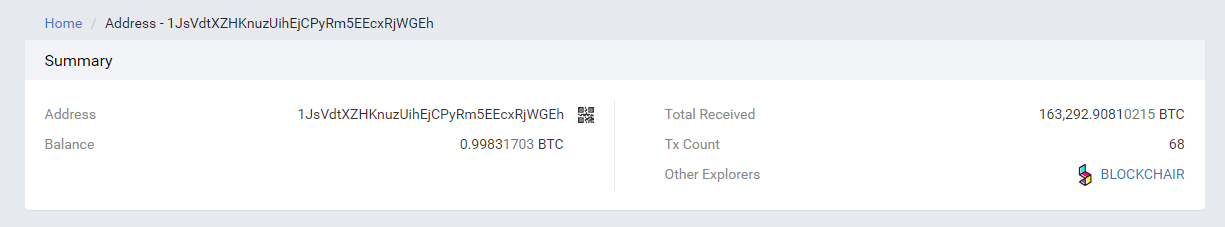
Today, large households who were stolen at least 1500 BTC and about 60,000 BCH may have been selected by hackers as the target of the stolen address 1Edu4yBtfAKwGGsQSa45euTSAG6A2Zbone. Since January 23, 2018, a total of 5,423 BTC have been received, most of which come from long-term holding of BTC. The top 50 addresses of the big names 1JsVdtXZHKnuzUihEjCPyRm5EEcxRjWGEh:
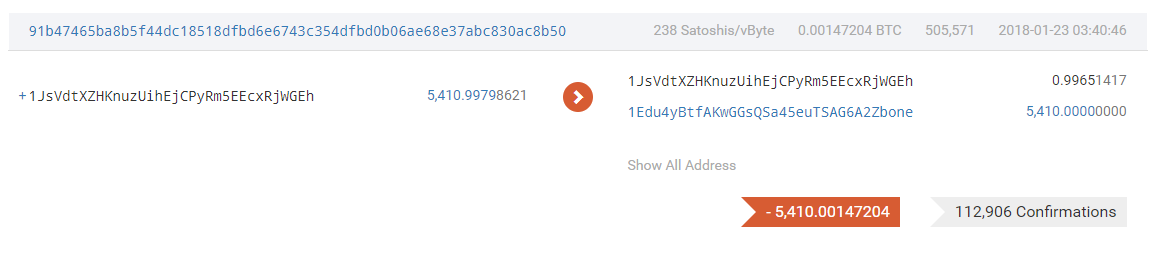
On February 8, 2019, the user generated a huge amount of 1662.4 utxo and used the funds to break out small amounts for trading multiple times in 19 years. We guess that the hacker may contact the fund of 1JsVdtXZHKnuzUihEjCPyRm5EEcxRjWGEh through this address and confirmed The identity of the user, the hacker may have targeted and carried out a persistent social engineering attack in 19 years,
- Opinion | Satoshi Nakamoto's idea of multi-client proves correct?
- CoinGeek Conference 2020 | Satoshi Omoto: You have a misunderstanding about Bitcoin!
- Why did Facebook create the Move language for Libra? Calibra digital executive tells the inside story
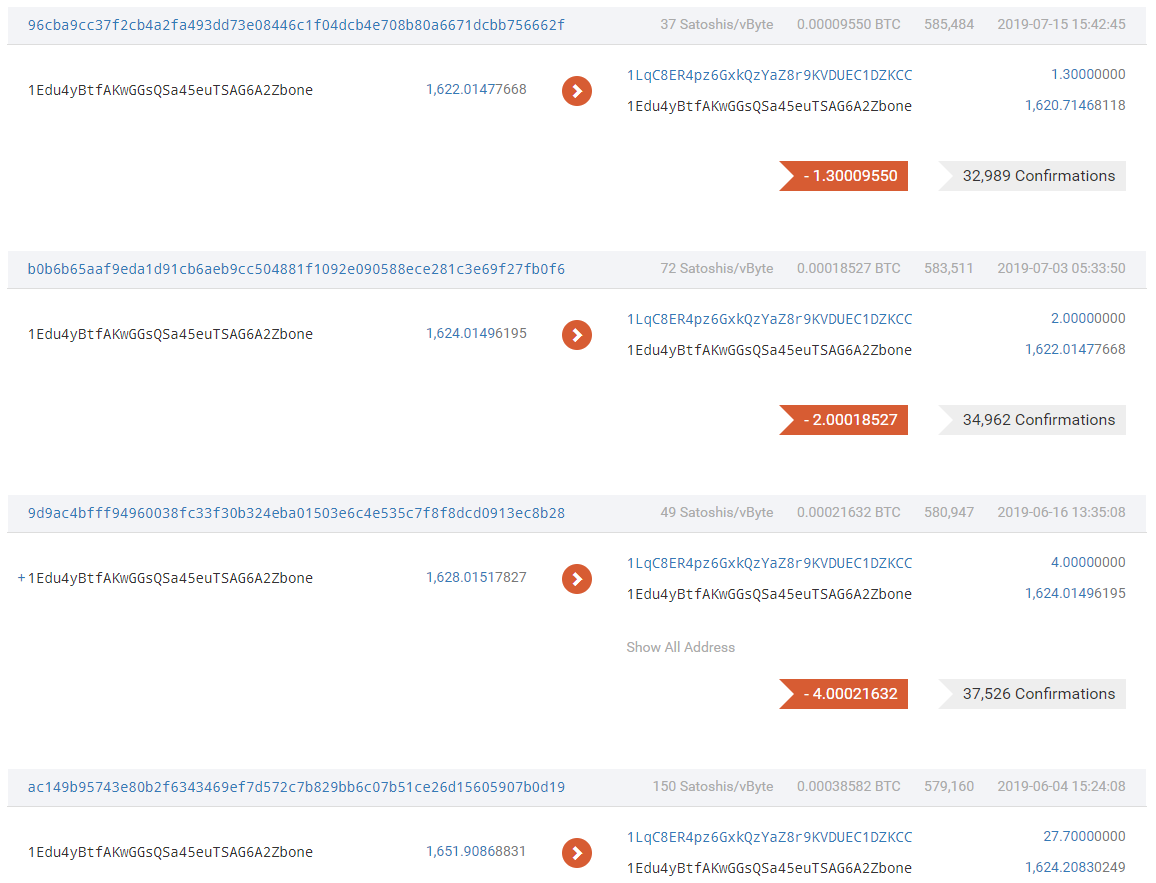
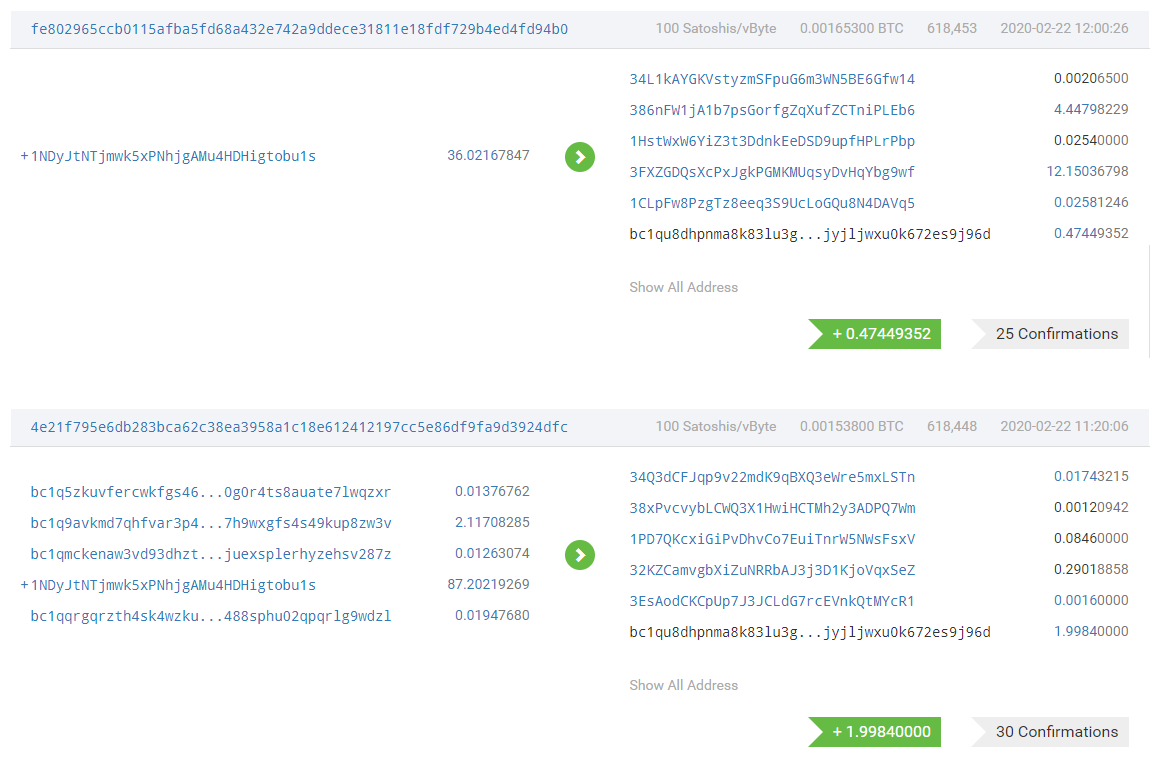
The attacker immediately started mixing coins and transferring funds after the attack succeeded
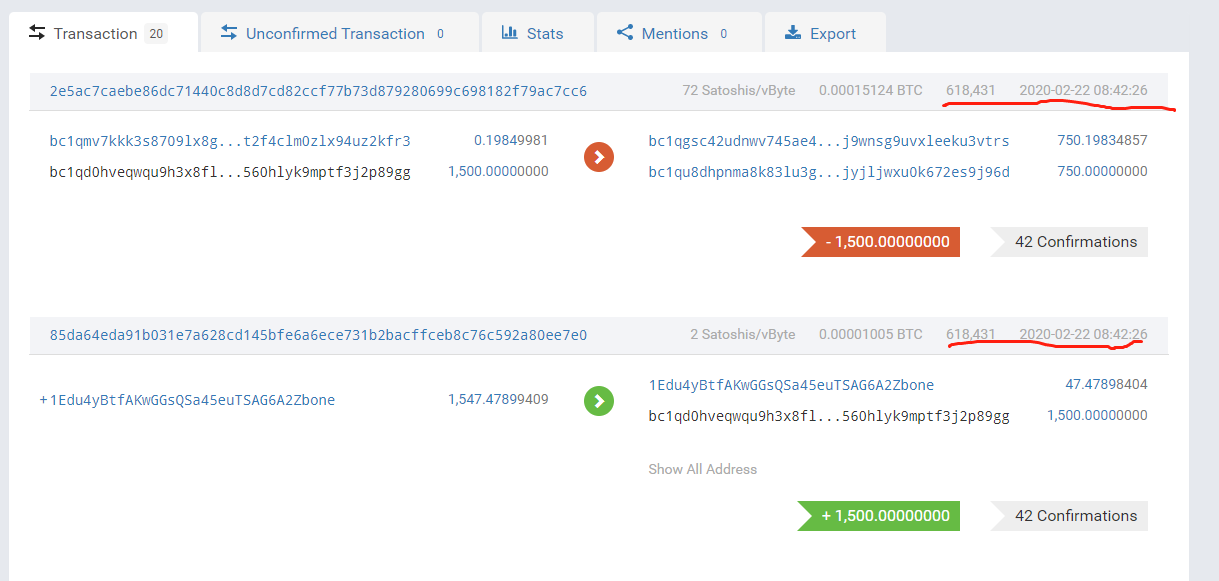
It is worth noting that one of the two addresses used by the attackers to split funds was quite active in 19 years. Analysis of the Chengdu Chain Security AML system found that some of the funds came from exchanges such as Binance. These exchanges may have relevant withdrawal For the record, Chengdu Chain Security is following this lead.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Interpretation | FCoin Shutdown: A Quick Look at the Exchange's Death Stance
- Communication blocked? IRS invites cryptocurrency companies to summit
- Don't wait for the road to wake up: the key points of blockchain project compliance review
- Baidu, Ant, and Tencent on the Forbes Blockchain Top 50: Industry Blockchain Weekly Highlights
- To achieve a 10,000-fold expansion of Bitcoin, what is the new agreement Prism created by MIT and Stanford?
- Flash loan strategy: Can an attacker take Maker's $ 700 million collateral?
- Data analysis of 731 companies worldwide: How does the market react to companies involved in blockchain?





