Perspective | Seeing the arrival of the era of intelligent privacy computing from the development of computing platforms

Editor's note: In the development of information technology in the past century, human beings have been pursuing the development of computing and computing power, and the ultimate pursuit has always evolved in the direction of intelligence. With the coming of the digital age of human society, the status and importance of data are constantly rising.
With regard to the development of computing platforms, they have gradually begun to shift from computing-centric to data and privacy and security. Under this trend, what characteristics will the next generation of computing platforms show in the future?
Today, we specially invite Mr. Tang Honggang, Chief Investment Officer of PlatON, with his more than 20 years of experience in computing platforms and system architecture, from the historical development of computing platforms, the urgent needs of data management, the real threat of quantum computing, and so on. Deducing the characteristics that the next generation computing platform should have.
- Interpretation of SEC Commissioner Hester Peirce's "Token Safe Harbor Proposal" (with translation of the proposal)
- Crypto derivatives exchange FTX seeks $ 15 million in funding
- Graphic dismantling: Where did FCoin assets go? Is there a problem with the funding chain in 2018?
Three stages of computing platform
Looking back at the development history of computers, changes in computing requirements have led to changes in computing performance. Each change is a breakthrough, and a new generation of computing platforms has emerged, and new computing platforms have built new operating systems and ecosystems. Ultimately leading a new computing revolution.
The development history of computing platforms has gone through three major stages
These hardware and software platforms are called computing platforms. The computing platform is the basis for the design and development of computer system hardware and software. It has certain standards and openness, and it also determines the performance of the computer system hardware and software. The basis of the hardware is the hardware processor, and the basis of the software is the operating system.
In general, the computing platform has gone through several stages, the PC + Internet stage, the mobile Internet stage, and the artificial intelligence stage. From the early X86 + Windows and Linux, to the ARM-based mobile computing platform Android + IOS, to the current artificial intelligence, many artificial intelligence acceleration hardware platforms and software platforms have emerged, such as TPU, Cambrican, NV, Tensorflow, PyTorch Wait.
Intel first introduced the x86 instruction set and 8086 CPU chip in 1978, which solved the needs of general computing. Subsequently, Intel CPU became the PC standard configuration, and then X86 became the PC standard platform and the most successful computing platform architecture ever. At the same time, AMD also followed X86's big ship and became the second-largest general-purpose processor market. However, the Intel / AMD neglected the technology of low-power processors, which caused them to miss the mobile Internet era, which is full of money.
ARM first designed the RISC-based instruction set in 1990 to solve the need for low-power computing. With the rapid development of the mobile Internet, ARM has finally waited for the glorious mobile Internet era and the processor business has also developed rapidly. And generous returns.
In recent years, as the artificial intelligence technology represented by deep learning has gradually matured and has been used in a large number of business scenarios, Google and other companies have released dedicated acceleration hardware represented by TPU, and the era of artificial intelligence represented by massive data computing has arrived. The Cambrian Period of the Chinese Academy of Sciences also recently launched a powerful intelligent acceleration chip. Naturally, Internet giants such as Ali Huawei will not miss this huge opportunity and have successively launched smart acceleration chips.
The urgent need for data management
At the same time, the rapid development of technologies such as blockchain, the Internet of Things, and quantum computing in recent years has raised the importance of data integrity and privacy in countries around the world to an unprecedented level. This has all raised the issue of data security and data privacy protection. Much higher requirements. We can't help asking whether the existing computing platform is completely suitable for the new requirements?
To tell a true story around me, a friend of mine worked for a large national telecommunications company in the early years. The server is an important core survival information of the enterprise. For a period of time, the boss assigned him to report the air-conditioning temperature in the computer room every day. One day after the report, the boss asked strangely, weren't both of the air conditioners on our roof broken? Why is there still temperature? This is enough to show that under the existing technology mechanism, the validity of data is changing dynamically, and it takes a lot of time and energy to manage.
The new crown virus that has ravaged the country recently has also exposed a large number of data management issues, such as transparency of anti-epidemic materials management, real-time coordination of epidemic situation data, etc. These issues will become more and more widespread with the rapid adoption of a large number of IoT devices and rapid social development severe.
Recently, countries have emphasized the strategic strategic significance of blockchain, and the combination of blockchain and the Internet of Things will also become a direction with great potential. By integrating the technology of the Internet of Things and the blockchain, data can be effectively managed, data tampering can be prevented, and the sharing and collaboration efficiency can be improved, while ensuring the reliability and authenticity of the data.
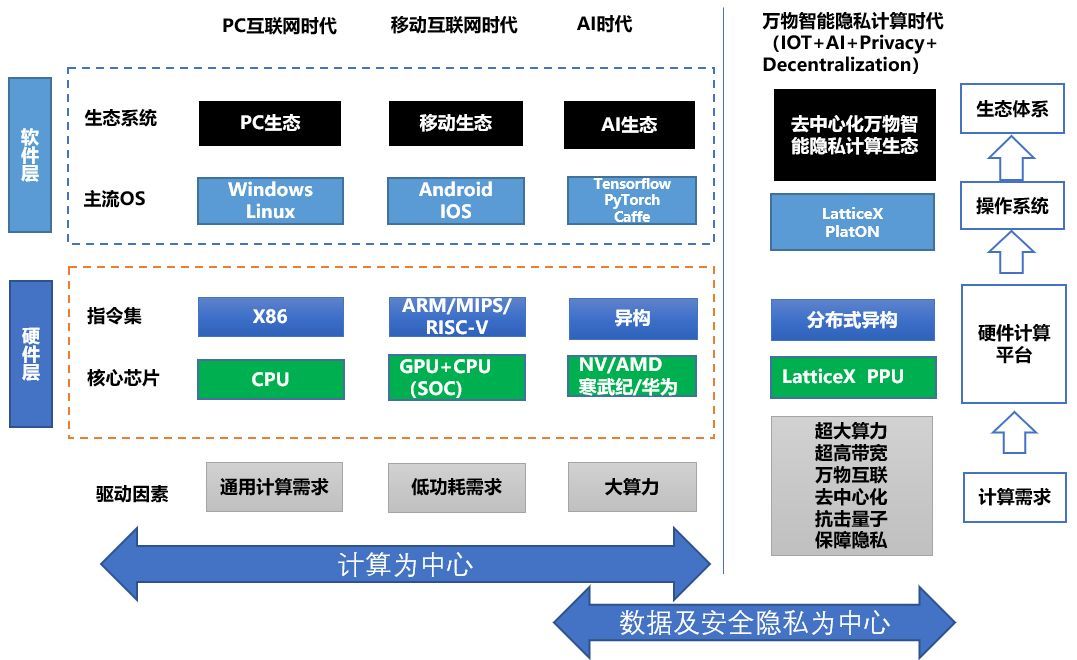
The development of computing platforms has shifted from computing to data and security and privacy
Threats from quantum computing
The rapid development of quantum computing in recent years has made everyone question the security of traditional encryption technologies. For example, RSA based on prime factorization faces huge security risks in front of quantum computers.
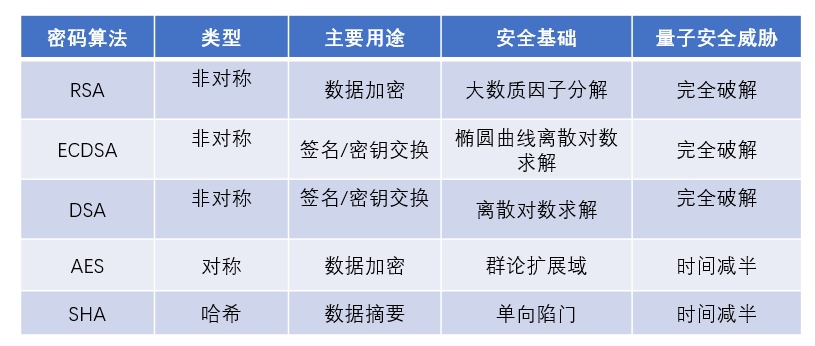
Overview of the security threats of quantum computing to cryptographic algorithms
At present, quantum computing attacks on cryptographic algorithms mainly include Shor algorithm and Grover algorithm. The Shor algorithm is mainly for public key cryptographic algorithms. In short, the public key can be used to obtain the private key, which poses a great threat to the public key algorithm. The Grover algorithm is targeted at symmetric cryptographic algorithms, which can reduce the complexity of exhaustive attacks. Symmetric cryptography doubles the key and is still secure under quantum computing conditions.
The cryptography community has been researching cryptographic algorithms that can resist quantum computer attacks for a long time. The earliest dates back to McEliece encryption and Merkle hashing in the 1970s. However, the threat of quantum computing was not obvious at that time, and the post-quantum concept was only proposed by the cryptography community after the threat has increased significantly in recent years. The National Institute of Standards and Technology (NIST) initiated research in post-quantum cryptography back in 2012.
After implementation, there are four main types of quantum cryptographic algorithms:
First, based on hashing;
Second, based on encoding, it is mainly used to construct encryption algorithms;
Third, based on multi-variables, it is mainly used to construct digital signatures, encryption, key exchange, etc .;
Fourth, based on lattices, it is mainly used to construct encryption, digital signatures, key exchange, and many advanced cryptographic applications.
The lattice calculation is also called the holy grail of cryptography, and its potential is very huge. However, the computational complexity of the lattice calculation is extremely high, and the relevant standards are still being developed. At present, it has not been widely adopted in the industry.
In addition, in terms of technology to ensure data privacy and security, INTEL proposes a hardware safe house solution SGX, but currently there are multiple effective attack methods against this solution, so it cannot be as secure and reliable as post-quantum encryption algorithms.
LatticeX computing platform came into being
In response to the above three requirements, we have proposed our own solution and computing platform.
The era of intelligent privacy computing for all things is coming. We tightly combine the Internet of Things technology, artificial intelligence technology, cryptography technology, and blockchain technology to form a new generation of computing platform LatticeX. The LatticeX platform will evolve along the path of post-lattice quantum technology, combined with hardware acceleration technology.
LatticeX will meet the massive big data calculations and artificial intelligence calculations required by the Internet of Everything in a decentralized environment to resist quantum attacks, protect the privacy, and the large computing power / large bandwidth requirements.
At the same time, we are also committed to developing the corresponding distributed heterogeneous hardware accelerator product LatticeX PPU (Privacy Process Unit). In the PPU, we will innovatively support a variety of post-quantum cryptographic algorithms, and integrate them closely with deep learning to achieve deep learning inference and training in full ciphertext, completely eliminating various security threats in the safe house scheme. At the same time, we support thousands of G-level optical interfaces to support real-time secure multi-party computing with large communication volumes.
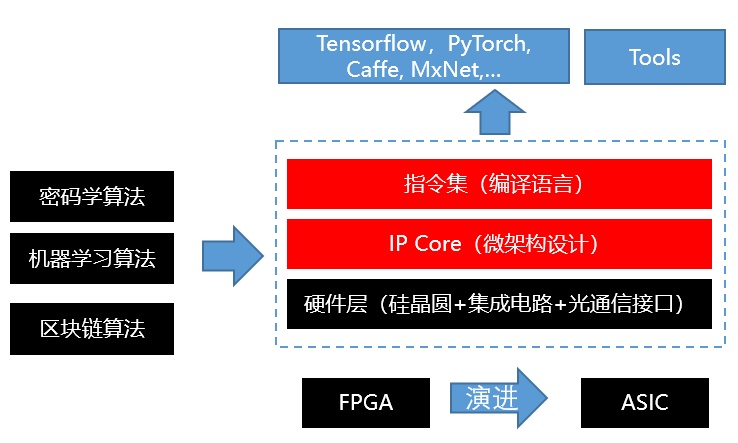
LatticeX computing platform architecture
LatticeX will witness the arrival of the era of intelligent privacy computing for all things. Through deep integration and optimization of software and hardware systems, it will provide the industry with a future with huge computing power and large bandwidth, support massive IoT device connection computing, and resist quantum attacks to ensure full data A distributed and decentralized intelligent computing platform for privacy and security. LatticeX can be used not only in industries with strict privacy and security requirements, such as finance, e-commerce, healthcare, security, etc., but also in various big data industries such as autonomous driving, energy, transportation, and aerospace.
Author:

Tang Honggang
PlatON Chief Investment Officer
Former Motorola System Architect, Baidu System Architect, Alibaba Investment System Architect and Investment Director. He has deep technical accumulation in computing platforms and system architecture and keen insight into industry development. During his time at Alibaba, he led investment in artificial unicorns such as Shangtang and Cambrian, and held more than 20 invention patents authorized at home and abroad.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Cryptocurrency Essence Series: The Rise and Development of the Mining Industry
- Forbes: Bitcoin's rebound this year is more sustainable than 2019
- MakerDao urgent vote to prevent governance attacks, this crisis may be related to the life and death of DeFi
- "The Secret History of Bitcoin": Who is the super-large Bitcoin mining pool with a computing power that approached 51%?
- Babbitt launches | Swedish central bank pilots "e-Krona", what are the characteristics of the world's first retail CBDC?
- Digital Currency Research Institute of the People's Bank of China: Development and Management of Blockchain Technology
- Opinion: Ethereum is promoting crypto market recovery






