Community Perspectives | Reflections on the MOV patrol officer system
In the 01 session of the ChainNode White Paper Declassified Reading Club, Liu Qiushan, a senior researcher at the original chain, led a white paper on "MOV: The Next Generation Decentralized Cross-Chain Layer 2 Value Exchange Agreement", which attracted the attention of many fans, including the reading of gentledog. "Thoughts on the MOV patrol officer system" won the first place in reading activities.
The text is as follows:
According to the white paper, there is a patrol officer in the MOV to prevent the Bytom side chain from doing evil. I was wondering if there is a loophole in this system? After some thinking, it seems that there are several ways to attack:
The inspector found the problem and initiated a transaction on the main chain. After someone obtained the transaction, he increased the handling fee or concealed the transaction directly from the network, and then initiated a transaction of the same content, thereby stealing the labor of the inspector. Results. In this case, the benefits that the inspector can obtain are almost zero or even negative, so there is no incentive to patrol.
- Research | Bitcoin mining and video games: Who consumes more power?
- Observation | China blockchain builds a peak in global public opinion
- Views | Next vent: More DAO than Token
This kind of attack has countermeasures. There is one thing that the perpetrator can't copy: the wallet address! The model of the proposal (commitment) + evidence can be adopted, and the inspector can submit the promise (the hash value of the data + wallet address) first, and then publish the data after the block is confirmed (the wallet address can be published). This will solve this problem perfectly.
This type of attack can be taken when the reward given by the gateway node is greater than the damage suffered by the side chain stalker. The side chain sinister can pretend to be evil, and then collude with the inspector to pre-empt the evidence of evil, and defraud the reward from the gateway node. When the reward is greater than the punishment of the perpetrator, the perpetrator will profit. This kind of attack shows that the reward given by the gateway node is capped, it can't be greater than the punishment of the perpetrator, and it is not necessarily equal to the degree of evil.
When the side chain is evil and involves a large amount, the garbage transaction is initiated on the network, temporarily blocking the network, so that the inspection cost of the patrol officer is much greater than the reward he can obtain (due to pretending to be a bad attack, the reward is limited, it is not evil. Degree of equality), once the dispute period has passed, the perpetrator will have to smash. DOS attacks are not impossible (see etheric cats and EIDOS airdrops), and the perpetrators can choose to launch attacks to reduce costs when the network is congested.
Let's start with the DOS attack. Let's try to analyze the patrol officer system from an economic perspective. First take an observation period, which is set in this observation period. The inspection cost of the inspector is U, the reward of the gateway node is V, the loss suffered by the perpetrator is R, and the gain obtained when the evil is successful is S. The probability of doing evil is p, the average number of inspectors is q, and the probability of a single inspector is t. It is assumed here that the chances of the inspector are equal, that is, when the number of inspectors of the inspector is q, the probability of successful proof is 1/q. The game between a single inspector and the perpetrator is as follows:
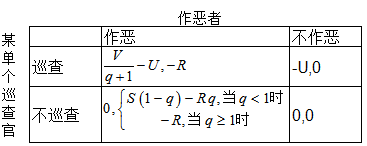
The expected payment of a single patrol officer is 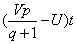 .
.
Under perfect competition, the expected payment of a single inspector should be close to zero. This can be inferred 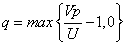 .
.
This shows that when 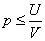 When q=0. Further, we can calculate the best probability of doing evil for the perpetrator. Here you may wish to set
When q=0. Further, we can calculate the best probability of doing evil for the perpetrator. Here you may wish to set 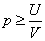 And
And 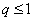 ,then
,then 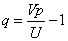 ,
, 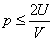 .
.
The expected return of the perpetrator is
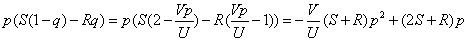
In the interval 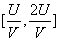 On the top, the formula is monotonically decreasing. So, at
On the top, the formula is monotonically decreasing. So, at 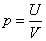 Get the maximum value. Therefore, the best chance of doing evil is
Get the maximum value. Therefore, the best chance of doing evil is 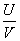 At this time, no one is inspecting! The above "observation period" refers to a sufficiently small, inseparable period of time. If it is a long time period T, how to calculate the probability of doing evil? Here, the patrol officer's inspection cost per unit time is u. The time period T is equally divided into n (sufficiently large) hours. Then the probability of doing evil in each small time period is about
At this time, no one is inspecting! The above "observation period" refers to a sufficiently small, inseparable period of time. If it is a long time period T, how to calculate the probability of doing evil? Here, the patrol officer's inspection cost per unit time is u. The time period T is equally divided into n (sufficiently large) hours. Then the probability of doing evil in each small time period is about 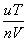 . Then the probability of evil occurring in n time periods is about
. Then the probability of evil occurring in n time periods is about 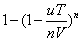 .
.
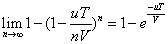
Therefore, in the longer time period T, the probability of evil occurring is 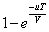 .
.
We can draw the following conclusions:
1. The patrol officer system can reduce the probability of side chains doing evil;
2. The probability of the side chain doing evil is related to the inspection cost U of the inspector and the reward V of the gateway node. Decreasing U or increasing V can reduce the probability of doing evil;
3. The probability that the side chain will be evil is not related to the income S obtained when the evil is successful, that is to say, reducing the assets managed on the side chain does not help to reduce the probability of doing evil;
4. The probability of side chain doing evil is irrelevant to the loss R suffered by the perpetrator when it is proved (if V ≤ R is ignored), that is, only the margin of the side chain operator is increased without increasing the reward of the gateway node. Does not help to reduce the probability of doing evil;
5. Due to pretending to be a bad attack, the reward V of the gateway node cannot be increased indefinitely. The patrol officer's inspection cost U cannot be reduced indefinitely. The patrol officer system cannot prevent the occurrence of evil.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Encrypted wallet MoA v1.0 officially released, three features make digital asset adoption easier
- Twitter Featured|Reddit Hot Post: 79% down for two years, do you still have faith?
- QKL123 market analysis | The market quickly fell, and then the boundary between the bull and the bear (1119)
- Prophecy Machine Governance Attack in Maker: How to make Maker's mechanism more perfect?
- The US SEC re-examined the Bitwise Bitcoin ETF proposal. When was the first encrypted ETF approved?
- Local government's "chain" marathon: Who is the "blockchain capital"?
- Visa develops a blockchain-based joint computing system for processing large-scale private data






