Demystifying the IOTA mainnet suspension, bZx and SIM being hacked, doing so can improve account security
The computing power said: the global epidemic crisis, distributed office, since February alone, there have been multiple exchanges, mainstream public chains and popular DeFi projects bZx and even personal digital assets have been stolen. In the field of digital assets, security is an eternal topic. In this issue, the University of Computing Power invited blockchain security expert Yu Manx, the founder of Slow Fog Technology, to share the focus of digital asset security protection. Cosine explained how to protect the security of digital assets from the perspective of the use of private keys, the determination of project security, and the choice of hardware wallets. It stated that from the management of private keys and wallets, there are many details that will create loopholes.
We are talking about the security incidents of some exchanges, public chains, wallets and individuals, and more importantly, how can we better protect ourselves afterwards. We hope this sharing will let everyone know where the possible threats will occur. It is possible that the audience we are participating in this live broadcast is not only individuals, but also some exchanges, or contracting and even supply chain, I hope to also get some inspiration through my sharing.
1Private key, wallet, SIM card hacked, security vulnerabilities exposed by recent security incidents
Let's talk about some security incidents disclosed in the past month.
- Sue against FB, buy spaceship tickets with BTC, bitcoin career of billionaire "Gemini" brothers
- Front Running: The Achilles heel of decentralized trading
- 18 felonies and up to 20 years in prison! Former Microsoft employee convicted of digital currency scam
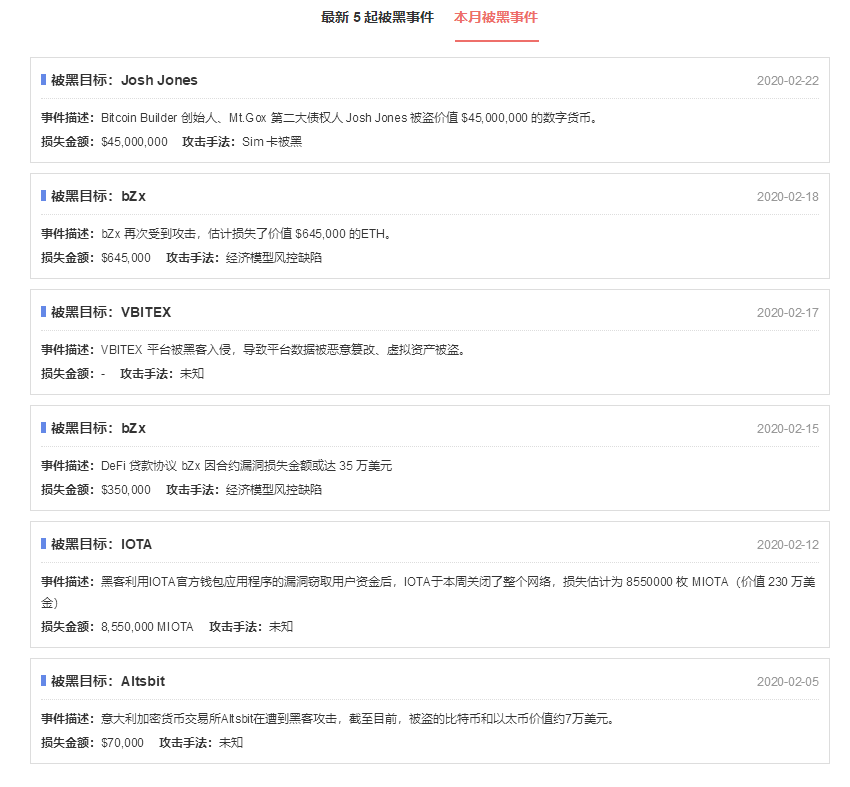
The first is that the Italian cryptocurrency exchange Altsbit was hacked. Although the amount is relatively small and it is a relatively new exchange, this exchange originally had a relatively small amount of funds. The amount of stolen funds actually accounted for them. About half of them, so they declared bankruptcy.
The second is IOTA. We noticed that this event was mainly due to the suspension of the entire mainnet due to this event.
Everyone can imagine a well-known public chain that can suspend the mainnet. What will cause them to do this kind of thing?
At the beginning of this incident, the entire community and the official were very frightened. They didn't know where the problem appeared, but just received complaints from many users that their coins were lost. To investigate this, they had to suspend the entire mainnet.
In our opinion, this influence is a very far-reaching incident, but in China, apart from the fact that we have taken the initiative to follow up and disclose it, and tweeted to the official and some relevant people in the community Apart from related interactions, basically no other security teams were seen to respond to this incident.
At that time we discovered that the reason it was hacked was because the official wallet released a new version with a built-in transaction module, which is equivalent to the function of an exchange in the wallet.
Such a wallet, its desktop version uses a very well-known JavaScript development framework. His access to third parties is also embedded via a remote call from JavaScript. This will cause a problem. If the third party is hijacked or hacked, and the content of JavaScript is changed, it will directly affect IOTA's wallet, because its entire operating environment is JavaScript.
So basically you can think that there is a problem with the third party. As long as the user opens the wallet and connects to the Internet in parallel, your private key, your password, and some related information you may be operating are able to give this malicious JavaScript code to Obtain. This is a very real attack case. We also output research reports in Chinese and English.
Next is bZx. BZx is a DeFi project. In fact, before it was hacked, we heard very little. After all, it was not particularly publicized in China, and it was used by relatively few people. We did it because it was hacked once and then hacked a second time, so we were very concerned about why it was hacked?
In fact, the fundamental reason is that the entire economic model is flawed in risk control. Including the mutual flow of some funds on these agreements and so on, in our opinion, it is a risk control defect in an economic model of the system as a whole and outside the system. So this matter is in our understanding, it is not a very traditional, such as a loophole that appeared in the smart contract, or a very simple vulnerability such as excessive authority, unauthorized power, etc.
This fluctuation is an attack event that can occur only when the inside and outside of the system are combined on the entire economic model. Before they were attacked, other teams had actually reminded them that there might be such a problem. But one of the enforcement rules that these underground hackers follow is to do it. What you want to do is to show people that you can really do it, not to say what kind of problems it may have.
Of course, such an early warning is also good, but it is said that many times they will feel that they are very familiar with smart contracts and very familiar with the world of DeFi, but they are too proud. When they are really done, everyone knows that this theoretical risk will actually happen. This is a revelation from bZx.
It seems to us a representative of this decentralized label. However, there are risks associated with decentralization and centralization.
The last time, everyone should be very impressed. This was Josh Jones on the weekend a few days ago. We have also made relevant speculations. At the time, he said on Reddit that he had been stolen, probably more than 1,500 bitcoins, and nearly 60,000 BCH. He said that his SIM card was hacked . The SIM card is a very important module in the mobile phone. If the SIM card is hacked, for example, my SIM card was copied by a hacker, which is equivalent to owning my mobile phone number. Receive any information, such as the verification code of the relevant platform can directly lead to the risk of these funds on my platform will be affected.
Why he said that the SIM card was hacked, we would be more convinced, because last year, there were many users of the Coinbase exchange because the SIM card was hacked, which led to the theft of their funds on Coinbase. This seems to us. The risks that can be attributed to the same category are third parties.
In fact, IOTA feels very similar to the previous one. IOTA was hacked because the wallet was embedded with a third-party exchange. This and Coinbase and Josh Jones were hacked because of third parties .
The SIM card attack method is actually quite popular, but you don't have to worry too much in China, because the domestic operators have gone through all kinds of confusion in the early days of the operator, and even the operators have done bad things, including some of our related laws and regulations. , Everyone's mobile phone number will not be easily copied by others.
This phenomenon was quite common in our country about 10 years ago. However, the strength of foreign operators may not be as strong as ours. Everyone knows that the level of infrastructure in our country is very strong. Many overseas operators are private companies operating, and their technical strengths are not necessarily so high, including related internal agreements, which may be very old versions, and risk control management may be backward, and there will indeed be overseas Mobile phone number was copied by social engineering and other methods.
We will remind you that if you are an overseas user, in addition to using the mobile phone number as a two-factor, it is best to use a secondary authentication app such as Google Identity Authenticator, or some hardware-level solutions.
These are some of the things that have been publicly disclosed in the recent month. In fact, there are many undisclosed.
How to manage your private key?
We have seen a lot of problems in the past month. For example, everyone knows that the private key is the identity. There are very important assets in the private key. There are three key points involved in this. From the generation, storage, and use of the private key, if any one of the links is not vigilant, it may be over time. When some risks are exposed, the possibility of going back or investigating is very low.
We generally mention the private key, and we will also mention multi-signature, including a popular algorithm called secure multi-party computing, but in the early days, many people actually needed them to manage some heavy assets, especially In some currencies, his support for multi-signature is not very reassuring.
For example, Ethereum, everyone knows that Ethereum's popular multi-signature solution is implemented through smart contracts. However, in the history of multi-signature smart contracts, there have been security issues. We cannot 100% believe that the multi-signature absolute security is achieved through the on-chain smart contract.
Even if I do not pass the smart contract, I can generate multi-signature on the protocol set and go down the chain, but it cannot guarantee absolute security. But here we will be more at ease. The reason is that this method has been checked numerous times in history. If there is a problem, basically everyone can think that the entire public chain or the infrastructure of these well-known public chains has very, very big problems. At this time, it is not some cases, it is definitely a very large-scale incident.
Therefore, from the probability and related code audits, including the frequency of use, many people will prefer a native and transparent solution similar to BTC, rather than multi-sign smart contracts written by third parties, although these smart contracts also We passed the security audit, but we don't trust the smart contract and the virtual machine underlying the smart contract itself.
So in the early days, many people's private key generation was a very Stone Age way. After the private key is generated, such as the private key or the mnemonic, through multiple copies and copying, there are multiple people in charge. In the beginning, these people may trust each other very much. For example, three people, any two people get the private key, or a fragment of the mnemonic word, they can form a complete private key.
But the first question is, who will do it when generating the private key? Is the environment he made safe? He said that after he finished it, he deleted it. There is a certain way to restore these deleted data. If there is no solution to the credibility problem in the first step, a seed of doubt or suspicion will be planted. Since these problems are early, it is very difficult to investigate clearly.
Then comes the storage, how to keep the private key in a safe place.
The other is to use it. You still have to use it. You have to play these coins out, or you have to transfer them. As long as you use it, whether you are directly or indirectly, you will have the possibility of networking, or is your operating environment at that time safe?
In recent several internal cases, in fact, many are centered on private keys. The private key just mentioned is very core at the level of the blockchain, and it is also a very basic and very low-level thing.
At the level of the entire system, such as an exchange or a wallet, there are various business modules to run, such as currency transactions, fiat currency transactions, transfers between wallets, recharge, manifestation, and so on. Including some new ways of playing now, such as contract trading, leverage, and you may have funds escrow, you may use a third party.
When we look at security issues, the greater the complexity of a security, the higher the level of a thing, the more user-oriented it is. Therefore, we also find that there are many cases of hacked, or stolen coins, where the higher-level risk control is missing, or the related management platform is hacked.
Many people may think that my management platform, how can a hacker see? In fact, as long as you touch the Internet, your computer's permissions may be stolen due to being implanted with a Trojan or virus.
When we analyze a hacked or stolen coin incident, our approach is definitely to split many layers from top to bottom, many modules, we will use the simplest method, called the exclusion method. Every piece, every piece of exclusion, finally determines its root cause.
But this process is actually very time consuming, and the most time consuming is probably more than two months before we discover the truth. The moment our entire team knew the truth, the tears were almost falling, and I immediately felt boring.
We know very well that any event, in our opinion, is like solving a case. We need to use the exclusion method to list any possibility, and then exclude it one by one. And many times, the descriptions of many people are problematic. If you want to scrutinize, his memory may also be problematic, and even if he deliberately makes bad, you have to scrutinize.
Because everyone knows that cryptocurrency transactions are transparent and visible on the chain, but this transparent visibility is limited to transactions, and does not record your IP, your privacy in the real world.
When tracking on the chain, there is an interesting point in the end. He will definitely convert these coins into fiat currencies in the end, but it is only a matter of time.
I may wait a few years later, I can come back after the storm, you will eventually convert into fiat currency. In many cases we found it was anxious to redeem it.
If we are underground hackers, no matter what method is used, the currency is stolen through the vulnerabilities of these exchange wallets, or various users are phished to steal other coins, or ransomware is used to steal your server and Your computer is encrypted, you have to pay me Bitcoin or Monero and so on. No matter what, I stole these coins and I will find a way to cash them out.
This involves that your coins will go to the exchange. Before entering the exchange, more and more professional practices now go through a mixed currency platform. The existence of these mixed coin platforms is a game for others who need to launder coins. The amount of money I wash in it, I ca n’t surely increase it every time. This ca n’t be more means that my speed will be slow. The other one may find a few more houses to wash together, because if you are in trouble, Now, I can find all the evidence chains of laundering on you, and even you will record my IP and so on.
None of these methods are particularly effective in the face of some superpowers. So you can see that laundering is also an art. It is not easy. The greater the movement, the more it may be exposed.
In the end, after you come out of the mixed currency, you have to enter some well-known exchanges, because they have fiat currency channels to come out. Here again, you are involved in your identity and account number on this exchange. Professional hackers will never use their own identities to register with these exchanges. Their various KYCs, various identities and even video identification can be fake.
3 How to judge whether the project is safe?
As long as you don't lose too much, or you don't have an evil or opaque mentality, you can actually win the wider support of the community.
This is also the fourth point we said. Core members are needed. They should be open to security and admit their mistakes if they have problems, instead of just shouting slogans.
For example, we see that there are many project parties, and their official website writes that my security is very strong and very good. Even at the Zeus level, it feels that various noun adjectives will come out, of course, these slogans are actually meaningless. We know where his problems may appear, because we are a very professional security team. Of course, for those professional underground hackers, they can also know that they can make your slogan important to your face in the future. Basis.
Fifth, we have awe and respect for safety. In fact, I think this thing is not only about safety. In this industry, no matter what you do, the entire industry chain goes up and down, everyone in the middle link must be full of awe, including due respect.
4What kind of hardware wallet is safe?
Recently, we also reviewed some hardware wallets. After doing an audit of these hardware wallets, we made a summary of what kind of hardware wallets are secure and powerful.
1. It is better to support enough mainstream currencies;
This is not absolute, we just consider it from the perspective of peace of mind, because a person's hardware wallet in principle will not exceed two types, because you are too much is not necessarily a good thing, and it is really safe Not to say absolute security, there are very few really secure hardware wallets.
2. The relevant hardware modules used at the hardware level are the top international standards and the production and delivery supply chain is also top;
Many teams that make hardware wallets are definitely not completely top-level and professional for various chips, modules and components of hardware. At this time, you have to rely on a lot of international top standards, even if you can't do it, you have to use it well. Including your choice of supply chain, your production, including your delivery, all have to choose these top quality.
11. The hardware wallet security team has sufficient strength to analyze the deficiencies of its peers, and the disclosure has obtained extensive technical reputation in the industry;
12. The private key is generated, stored, and used. The almost absolute security of the private key is the most basic requirement;
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- What does De in DeFi mean and what does it mean for the blockchain industry?
- Bitcoin fell below $ 9,200, and the entire network was over $ 300 million in short positions. Is the halving quotation not over yet?
- Over 43% of Ethereum addresses are profitable, and researchers are optimistic that Ethereum will become a new hedge
- Comprehensive interpretation: What is the impact and value of the US SEC Commissioner's "Token Safe Harbor Proposal"?
- Why is FileCoin delayed again?
- Winklevoss brothers support Filecoin, how long will it take us to raise $ 257 million?
- QKL123 market analysis | At the tip of the iceberg of crypto assets, Hurun's wealth list ranks sixth (0226)






