Graphic dismantling of a large whale account theft, a professional hacker gang committed
Text: Zhou Fan
Cartography: Hu Lingyu, Zheng Biao
Source: PeckShield
Hidden in the dark jungle of the blockchain world are a group of hackers with strong technical expertise, as well as a group of early ringgits who made a lot of money from investing in Bitcoin.
- Technological Innovation and Exploration of Blockchain Layout in Big Factory 丨 Babbitt Industry Welcome Class
- QKL123 market analysis | Bitcoin plummets, contract liquidation, ETF rejected … Futures market is beyond imagination (0227)
- Holding nearly a million BTC, revealing how the giant whale Coinbase manages them
In theory, if the big guy only revealed his on-chain address, there is nothing he can do about the hacker's technical strength, but if the big guy's off-chain identity is also found out, a long-planned theft case will also begin .
On February 22, a user who claimed to be “zhoujianfu” posted on Reddit that he had been hacked, and stolen 1,547 BTC and 60,000 BCH, worth about 260 million yuan.
According to the victim, his SIM phone card was cracked, resulting in theft of funds. The PeckShield security team believes that the SIM card attack is to bypass the operator's security measures and copy or re-process the victim's SIM card to control the stolen SIM card. Once the control of the mobile phone number of the stolen person is obtained, the majority of the stolen person's account permissions can be obtained through the SMS verification code verification mechanism, which also includes the cryptocurrency accounts of most of the stolen person.
Target
This Twitter ID user, zhoujianfu, was quickly locked down as Josh Jones after claiming to have been stolen. He has a very prominent identity, once the second largest creditor of the largest exchange Mt.Gox, and Mentougou has 43,768 Bitcoin.
Almost at the same time as his Reddit post, everyone knew his real identity. It can be seen that this big man is not low-key in the online world, and it is a well-known fact that he has a large number of cryptocurrencies, not to mention a high-tech hacker.
Therefore, the hacker may have been following him for a long time.
The theft of 1,547 BTC is the largest personal hacking case in recent years. Graphic dismantling: where the stolen assets of the killer whale account go
According to the victim, his address on the BTC chain was 1Edu4yBtfAKwGGsQSa45euTSAG6A2Zbone.
CoinHolmes, a visual digital asset tracking system under the PeckShield security team, includes dozens of exchanges with more than 60 million address labels, involving BTC, ETH, EOS, USDT and other mainstream digital assets.
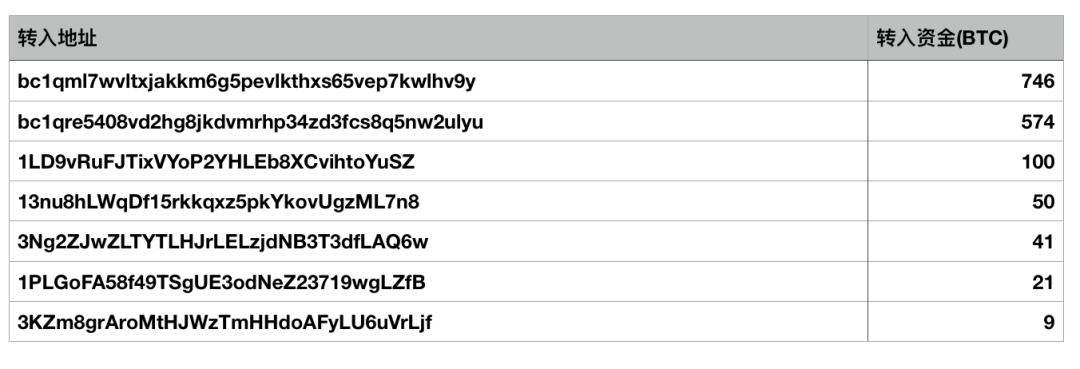
According to the address provided by the victim, CoinHolmes quickly locked the relevant address of the hacker, carried out targeted tracking and analysis, and finally drew a visual path transfer panorama:
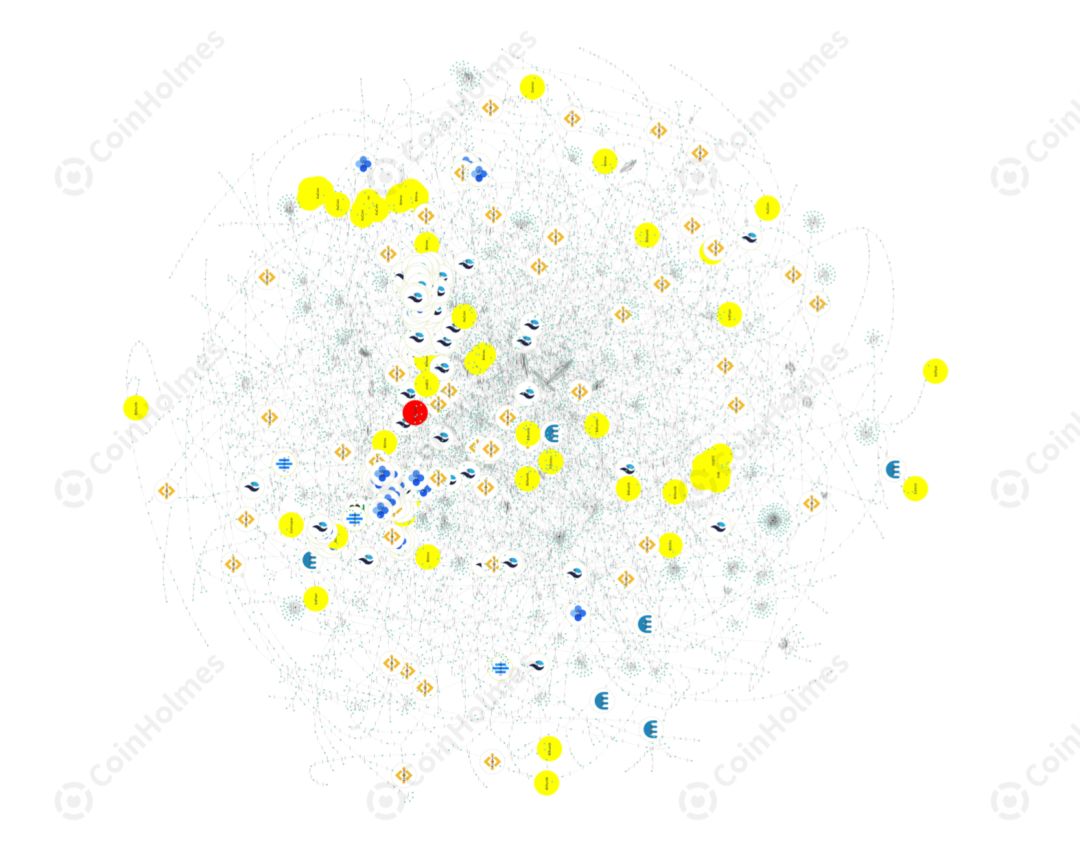
Funds scattered and transferred in small amounts
 Taking the address starting with bc1qre5 as an example, PeckShield used its digital asset visualization tracking platform CoinHolmes to draw its asset flow transfer diagram. From the figure below, we can see that the funds on the address are cut in each transaction and transferred to a large amount of funds. The address will continue to split in small amounts along the forward direction.
Taking the address starting with bc1qre5 as an example, PeckShield used its digital asset visualization tracking platform CoinHolmes to draw its asset flow transfer diagram. From the figure below, we can see that the funds on the address are cut in each transaction and transferred to a large amount of funds. The address will continue to split in small amounts along the forward direction. 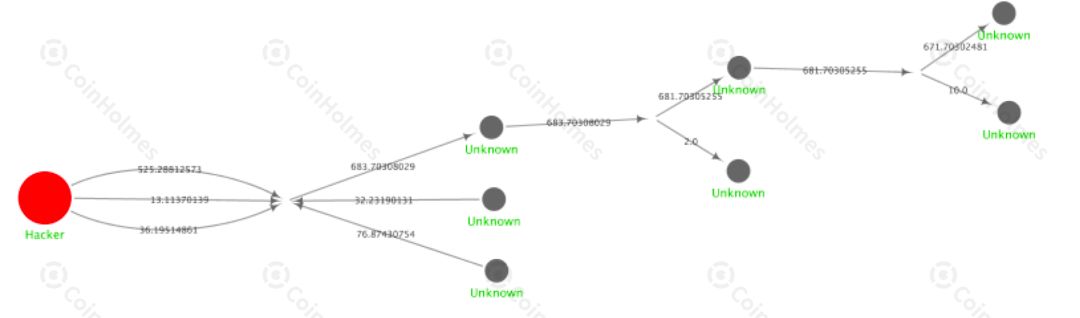
Funds are confused with other transactions
Through the analysis of the 1,547 BTC that the hacker dispersed and stolen for a short time, we can already see the professionalism and complexity of money laundering by the hacker. But after completing this decentralized operation, hackers are still further trying to make asset tracking extremely difficult through more complex obfuscation systems.
PeckShield security personnel's follow-up analysis found that hackers were also mixed with UTXO of other transactions as a confusion during the transfer of funds. The address starting with bc1qre5 analyzed above is taken as an example. The transaction funds marked in the red box below are not stolen Of the 1,547 BTC funds, at the same time, transactions starting with 6ef39b include funds starting with bc1qre and other UTXOs.
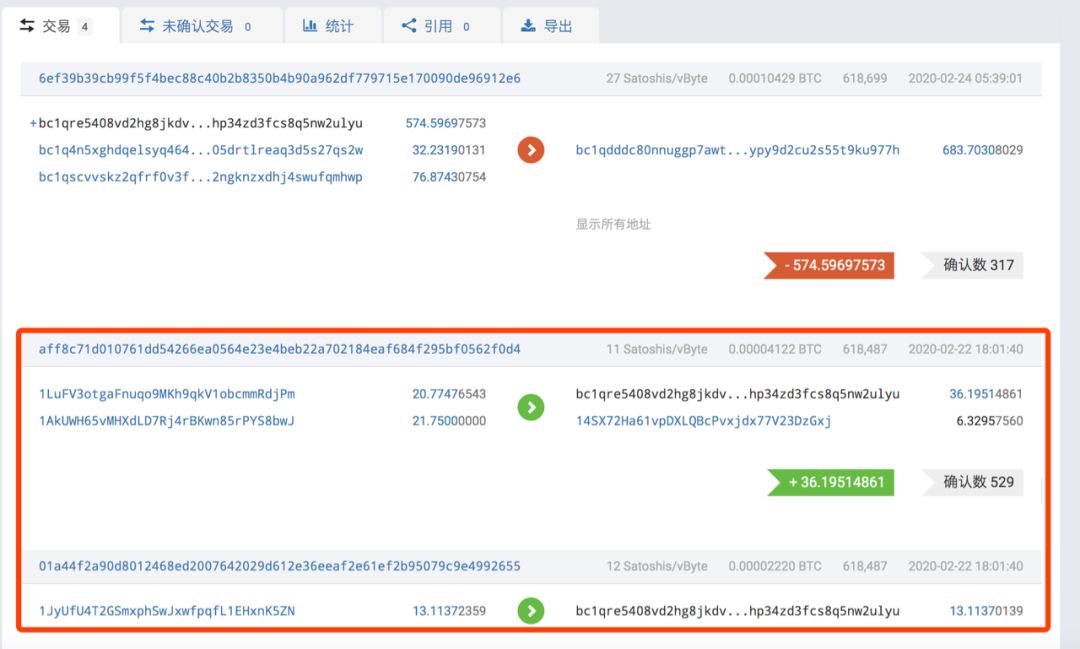
Bitcoin mixing is not a new concept. It originated from the dark web. Hackers or criminals mixed the acquired BTC to avoid being tracked.
Specifically, coin mixing involves a large number of inputs and outputs in a transaction, chaotically breaking up the transaction information, thereby making it more difficult to find out the correlation between input and output. Although the bitcoin address itself is anonymous, the related transaction data is completely open and transparent. Through the transaction address association and analysis of the data, it is possible to track on the chain and lock the identity behind the address.
Therefore, in order to avoid being tracked and monitored, hackers generally conduct mixed operations on stolen bitcoins.
Part of the funds flowed into the exchange
 The key path flow into the Bittrex exchange is shown in the above figure. As mentioned earlier, before the flow into the exchange, hackers have adopted a mixed currency approach. Therefore, PeckShield security personnel judged that some funds may not have been directly transferred to the exchange. , But was cleaned in a way similar to off-site OTC.
The key path flow into the Bittrex exchange is shown in the above figure. As mentioned earlier, before the flow into the exchange, hackers have adopted a mixed currency approach. Therefore, PeckShield security personnel judged that some funds may not have been directly transferred to the exchange. , But was cleaned in a way similar to off-site OTC.
In addition to some of the funds flowing into the exchange, as of now, most of the stolen funds are still in the hacker's address, and PeckShield is also locking in monitoring the further movement of target funds.
Conclusion
PeckShield has reason to believe that this time the hacker should be a professional and skilled hacker gang.
The gang has done a lot of work from the selected target to the on-chain + off-chain tracking and breakthrough for a long time. This seems to be a wake-up call for some of the early profitable bigwigs who invested in cryptocurrencies. Don't be blind when you make money. Someone is staring at you all the time.
Although the asymmetric encryption private key system has blessed personal accounts, with the current on-chain defense engineering that computer computing power is almost impossible to break, personal private key management is actually off-chain behavior, and hackers can use users to use some of the old ones on the Internet. Rough habits make breakthroughs, and this SIM card attack is one of them.
As the saying goes, "If you are not afraid of the thief stealing, you are afraid of the thief."
If you only know the on-chain address, hackers trying to crack the user's private key need to go through several generations of reincarnation for hundreds of millions of years. Once the user's on-chain address and off-chain identity are numbered, the way the hacker performs the attack is also There are undoubtedly tens of thousands more possibilities.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- KYC provokes questions, FOMO gameplay encourages users to "voice": Voice cracks for survival
- When will 1 billion Ethereum transactions occur?
- Is this really decentralized? Community announces the destruction of $ 132 million EOS, Block.one is unaware
- Viewpoint | Does Blockchain Need Traffic Thinking?
- Babbitt Column | Can courts effectively penalize mining pools to roll back bitcoins to correct lost and stolen coins?
- Bitcoin has been hit hard for 14 hours and has fallen by 14%.
- Analyst observations | What is the correlation between Bitcoin and other assets?





