HD Wallet Soul Check! Which wallets can stand the test?
I believe that all students who have used the "decentralized wallet" are no strangers to mnemonic words .
Whether it is a hardware wallet or a software wallet, there are two ways to create a wallet:
- Create mnemonics : The wallet randomly generates a set of mnemonics, and users need to copy the backup
- Import mnemonics : users import a set of existing mnemonics into the wallet to restore assets
So how does the mnemonic become our master private key, and then all the child private keys are generated in HD?
it's actually really easy. A set of mnemonic words, after 2048 rounds of HMAC-SHA512 algorithm abuse, generates a master private key, and then derives a set of HD wallets.
- Hardcore PK gold: Bitcoin and gold, who is the better hedge asset? (on)
- Ethereum developers: ProgPoW is more ASIC friendly than current algorithms
- Hardcore PK Gold: What is the history of abandoned gold, what can it inspire Bitcoin? (under)
Therefore, there is a one-to-one correspondence between the mnemonic and the master private key. A set of mnemonics corresponds to a master private key, that is, an HD wallet.
Have you thought about a terrible question here:
Let's say these are the 12 mnemonic words in the shopkeeper's hand:
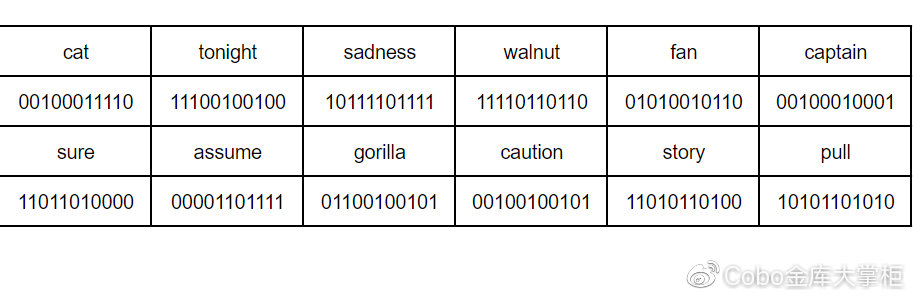
cat tonight sadness walnut fan captain sure assume gorilla caution story pull For convenience, we call this set of words [cat 助 记 词]
However, when the shopkeeper imported [cat mnemonic] into the wallet, the first word was shaken and entered into dog, so the mnemonic became:
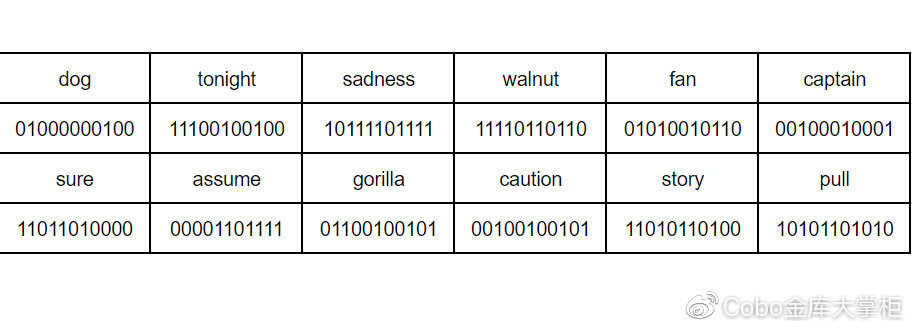
dog tonight sadness walnut fan captain sure assume gorilla caution story pull
This is the beginning of the tragedy.
As a pure 24K coin hoarding party, the shopkeeper has worked hard and saved money, and recharged all beliefs to the address under [dog Mnemonic].
Then one day, it may be because the mobile phone or hardware wallet is broken, or the wallet app may be deleted with shaking. In short, for various reasons, it is necessary to come up with a mnemonic to restore assets.
At this time, the shopkeeper took out the long-established [cat mnemonic] and imported it into the wallet.
As mentioned earlier, a set of mnemonic words corresponds to an HD wallet one-to-one. At this time, the address recovered using [cat mnemonic] is different from the address of [dog mnemonic]. In other words, under [cat Mnemonic], there are no assets.
Because a mnemonic dog was entered by mistake, all assets and beliefs of the shopkeeper were lost.
Is it scary?
In fact, wit Bitcoin developers have long thought of all this. They define a standard protocol for mnemonics, which verifies the validity of all mnemonics.
Before talking about "verification principle", the shopkeeper popularizes a basic knowledge about mnemonic words.
BIP39 defines the standard for mnemonic words, which contains a vocabulary of 2048 words (refer to link 1). As long as all wallets follow BIP39, the generated mnemonics are obtained from this 2048-word vocabulary, and all the words of [cat Mnemonic] are no exception.
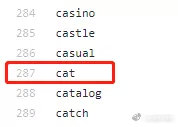
Each word in the 2048 vocabulary is numbered, from "0" to "2047". The largest serial number "2047" in binary representation is exactly 11 bits "11111111111". So for each word in the vocabulary, we can correspond to an 11-bit binary number according to its sequence number. For those that are less than 11 bits after converting binary, we add "0" before its binary number until 11 bits are satisfied.
For example, cat is the 287th word, the serial number is "286", and the corresponding 11-bit binary number is "100011110". We make up the 11 bits and express it as "00100011110".
Next we look at the specific "verification" steps :
Step 1: We follow the method above to find [cat mnemonic] according to the 2048 vocabulary. The 11-bit binary number corresponding to the 12 words .
Step 2: We string together the 11-bit binary numbers corresponding to these 12 words to get a 132-bit binary number :
001000111101110010010010111101111111101101100101001011000100010001110110100000000110111101100100101001001001001011101011010010101101010
Step 3: We split the 132-bit binary number into two parts , 128 bits on the left, and 4 bits on the right.
128 bits on the left: 00100011110111001001001011110111111110110110010100101100010001000111011010000000011011110110010010100100100101110101101001010110 4 bits on the right (check value): 1010
Step 4: We begin to verify the validity of this set of mnemonics.
The principle of judging validity : The first 4 bits of the SHA256 result of the 128-bit binary number on the left must be equal to the 4-bit binary number on the right.
Let's check the results of [cat mnemonic].
Put the left 128-bit binary number into an online SHA256 calculator (see link 2)
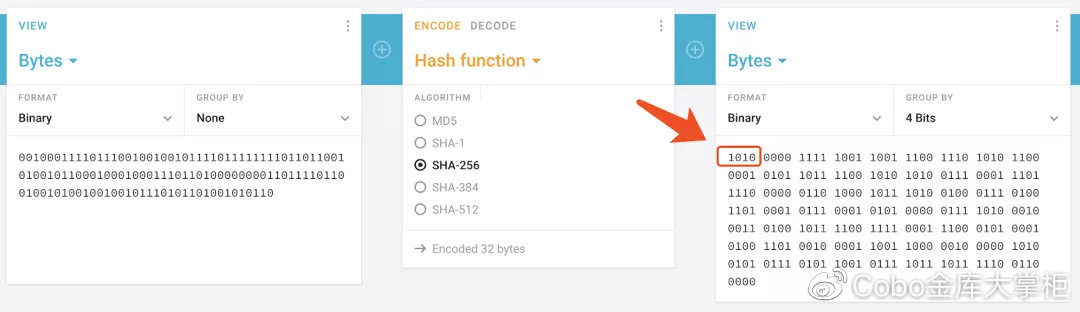
(Do not use online tools to verify coined mnemonics !!!)
It can be seen that the first 4 digits of the SHA256 result are exactly "1010" 4 digits to the right of the 132-bit binary number.
This shows that [cat mnemonic] passed the verification and is a set of valid mnemonics , and then it can enter the subsequent master and private key generation process.
Then let's do an exercise right away and see if the [dog mnemonic] entered a wrong word can pass the check:
Step 1: [dog mnemonic] The 11-bit binary number corresponding to the 12-word vocabulary is as follows:
Step 2: String the 11-bit binary numbers corresponding to the 12 words together to get a 132-bit binary number:
010000001001110010010010111101111111101101100101001011000100010001110110100000000110111101100100101001001001001011101011010010101101010
Step 3: Split the 132-bit binary number into two parts, 128 bits on the left, and 4 bits on the right:
128 bits on the left: 01000000100111001001001011110111111110110110010100101101100010001000111011010000000011011110110010010100100100101110101101001010110 4 bits on the right (check value): 1010
Step 4: Put the 128-bit binary number on the left of [dog mnemonic] into the SHA256 calculator.
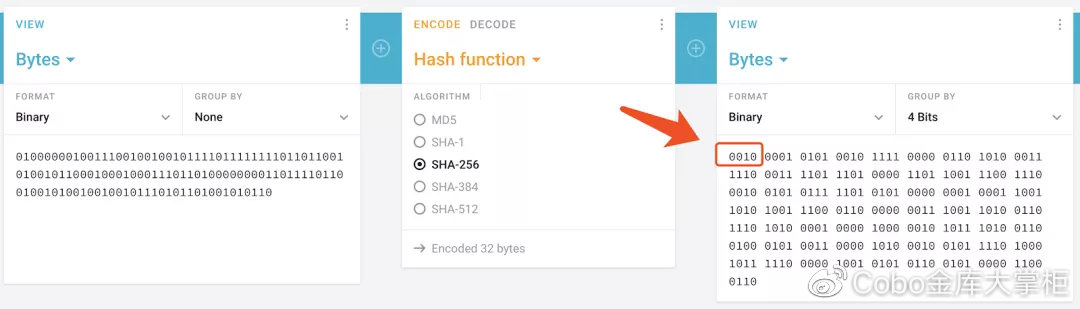
(Do not use online tools to verify coined mnemonics !!!)
It can be seen that the first 4 digits of the SHA256 result are "0010", which is inconsistent with the 4 digits "1010" to the right of the 132-bit binary number.
In this way, this group of [dog mnemonic words] can not pass the verification , and the wallet app developed in accordance with the standard BIP39 protocol will remind users to check their mnemonic words. At this time, the user will find an error, and change the "dog" to the correct "cat" to pass the verification and complete the creation of the wallet, and to avoid the tragedy.
Finally, let's check the homework to see if the well-known HD wallets at home and abroad will check the mnemonic errors according to the standard BIP39 protocol when entering a set of invalid mnemonics.
Because you only need to enter a set of invalid mnemonics, you can achieve the purpose of checking, so for convenience we do not enter complex mnemonics, and directly enter 12 cats (this is a set of invalid mnemonics). The inspection results are as follows:
First: imToken
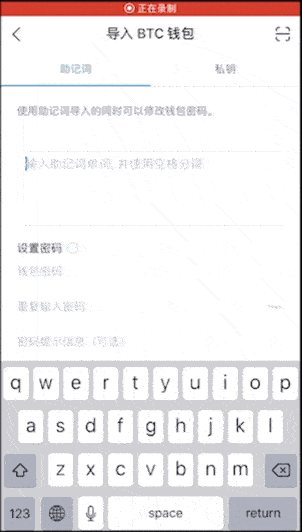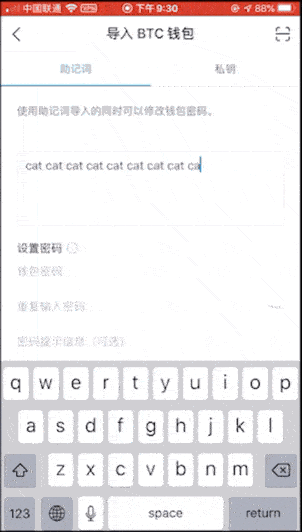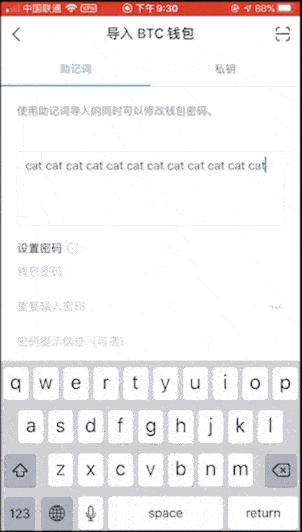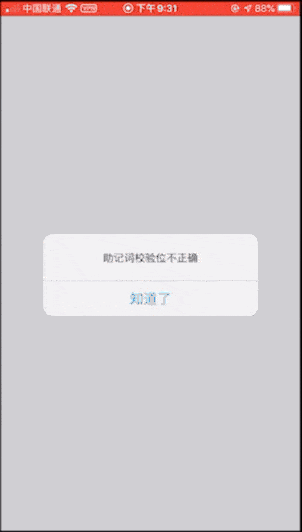
Second: Huobi Wallet
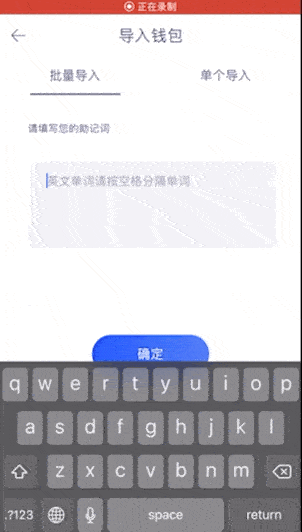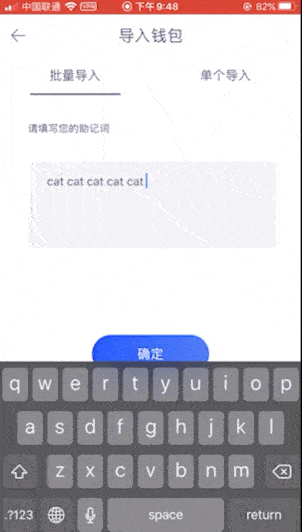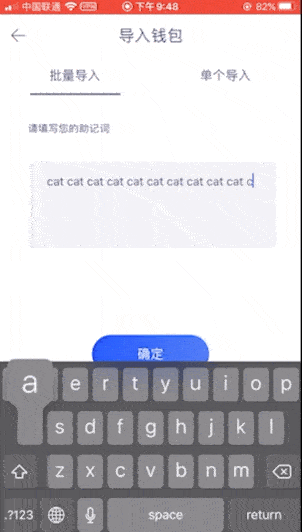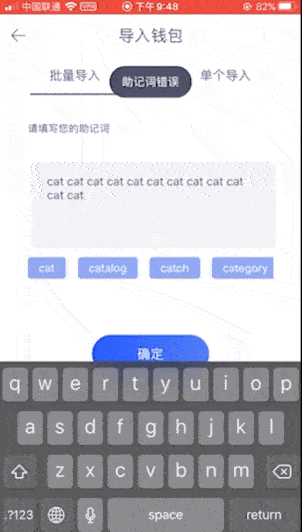
Third House: Trust Wallet
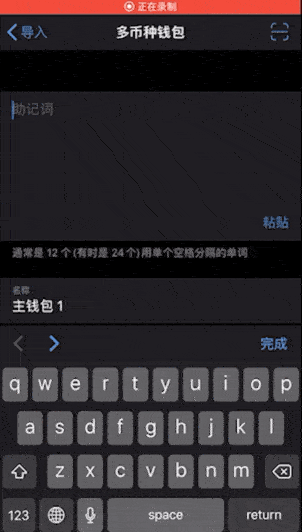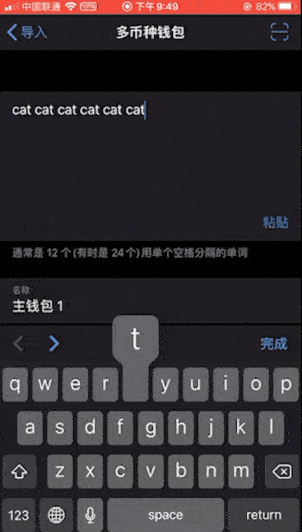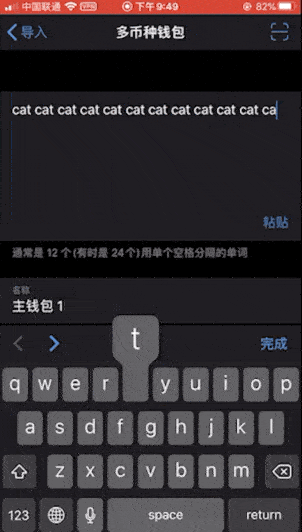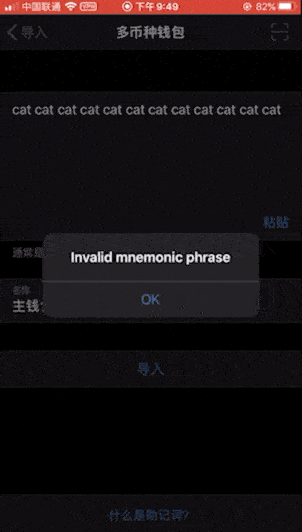
Fourth house: BRD
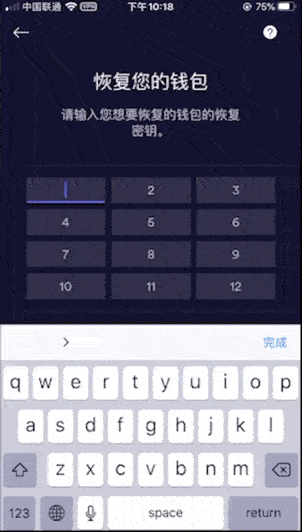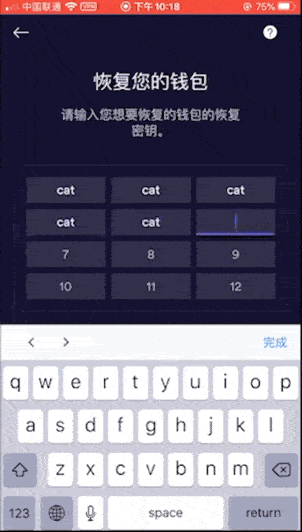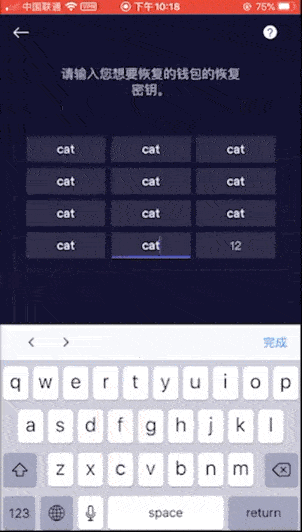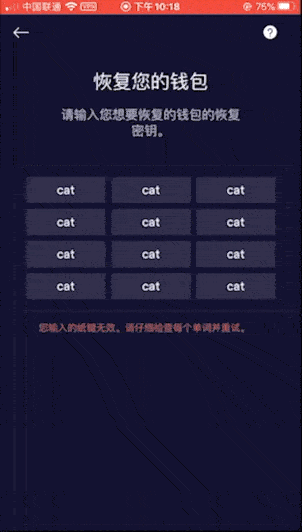
Fifth house: BitPay
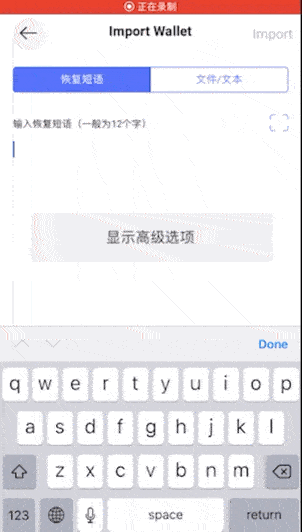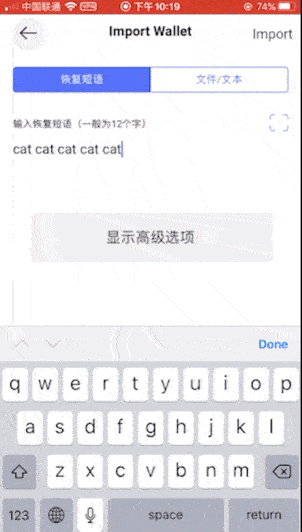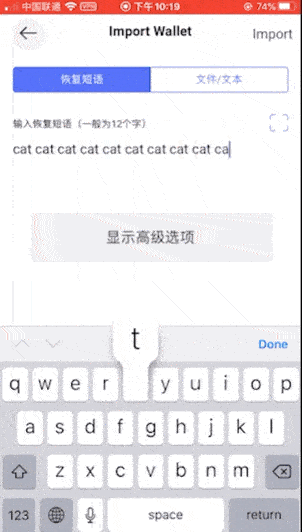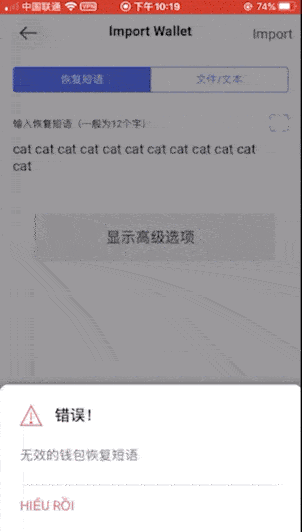
Sixth house: imKey

Seventh: Cobo Wallet and Cobo Treasury
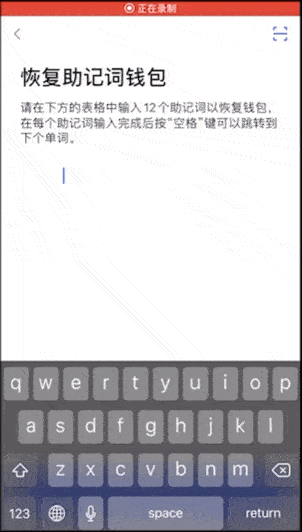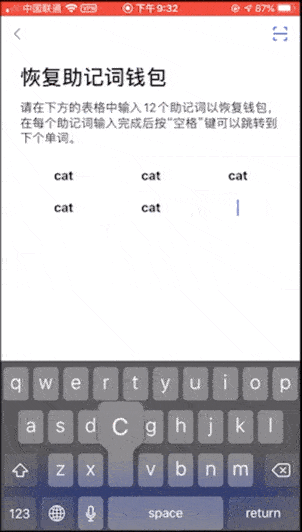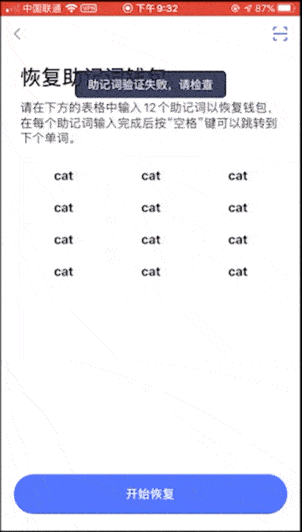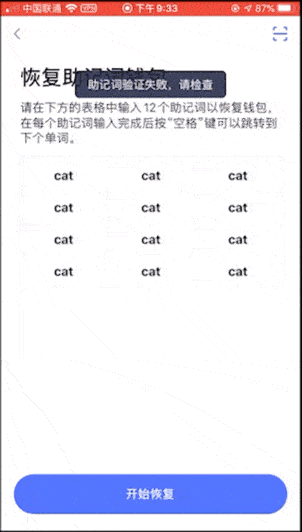
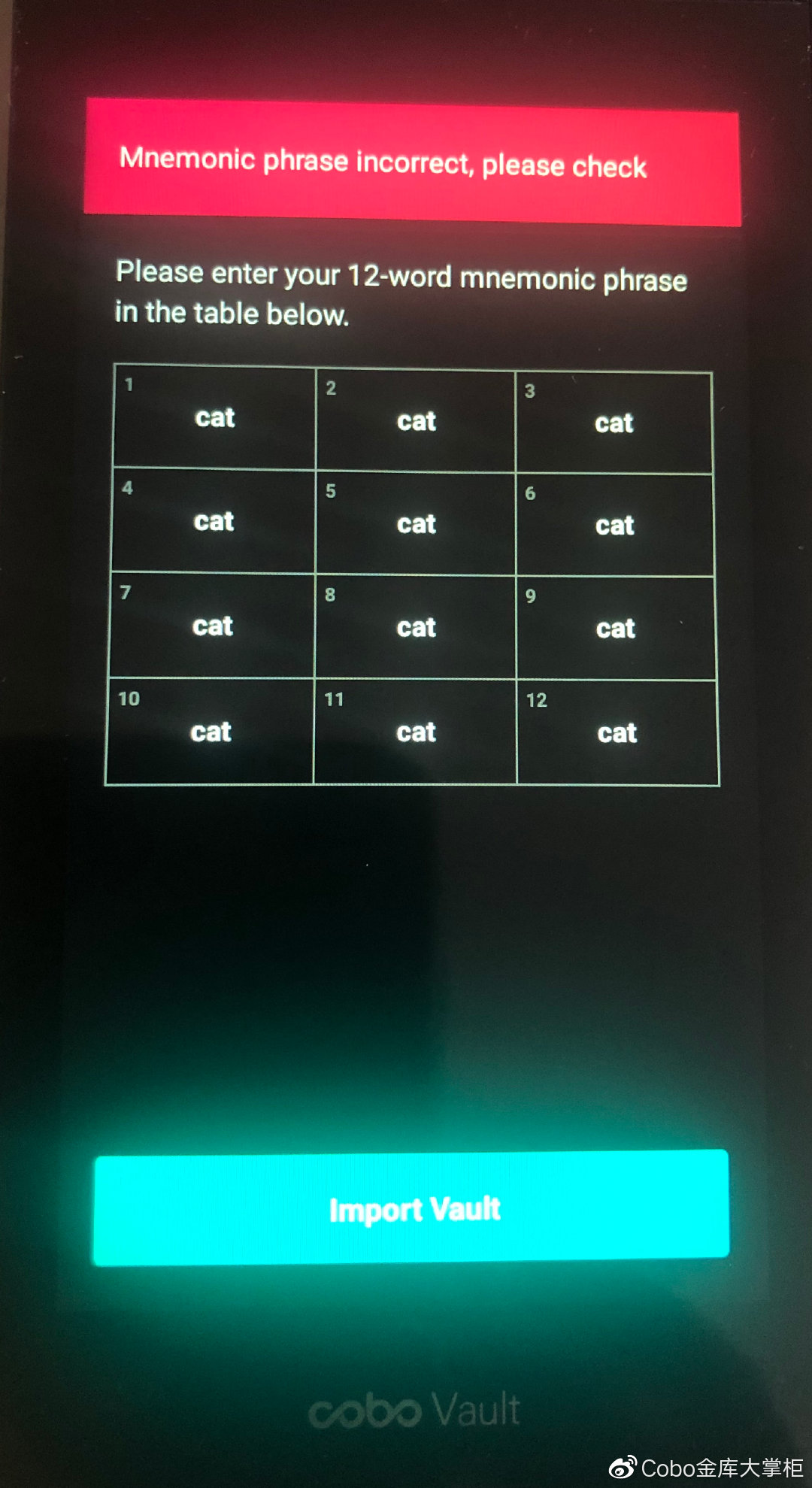 Cobo Treasury
Cobo Treasury
Eighth: Bitpie Wallet and Hardware Wallet Bit Shield. Bit shield's mnemonic is entered on the mobile phone. There will be confusing words when entering 12 mnemonic words, but not when entering 24 mnemonic words, so we enter 24 cat (this is also an invalid mnemonic word) ) Tried it, and it turned out that the mnemonic was wrong.
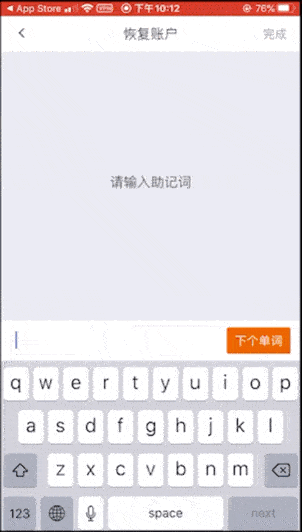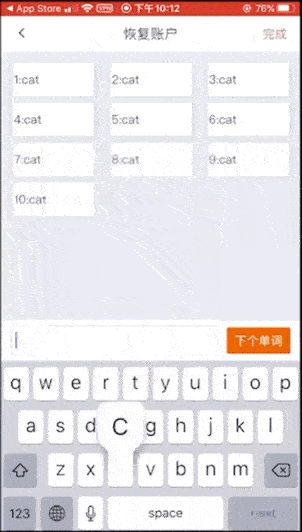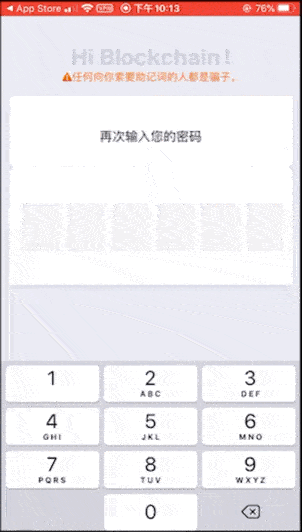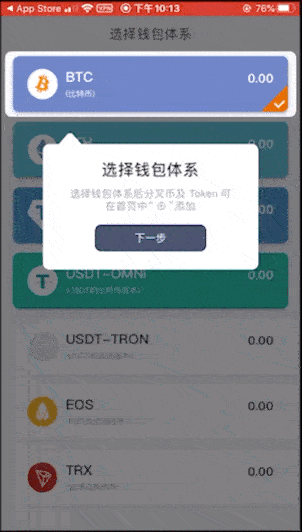
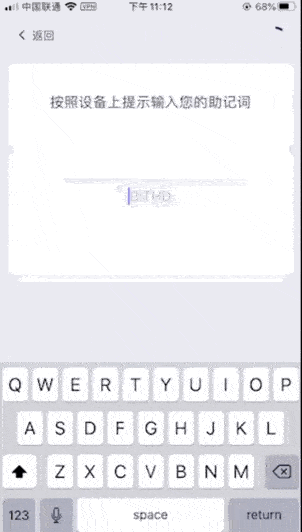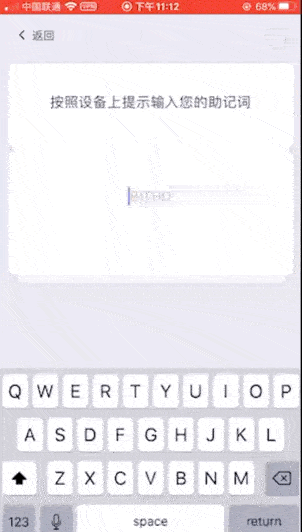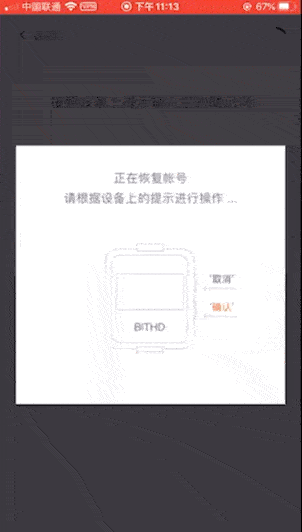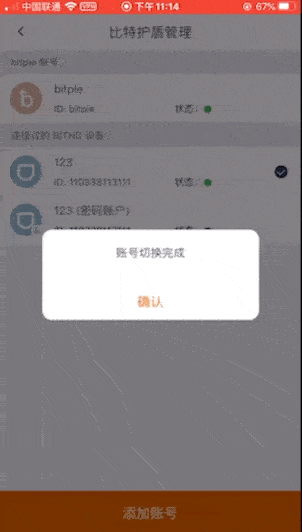
Finally, let me remind you of a hardware wallet risk point :
When the shopkeeper checked the operation of each mnemonic check, he found that some hardware wallets completed the mnemonic input on the mobile phone .
The reason we use hardware wallets is to save the mnemonic words / private keys off the Internet. Entering mnemonic words on networked devices completely loses the meaning of hardware wallets.
Here is a solution: When importing mnemonic words into the hardware wallet on the mobile phone, shuffle the word order and add confusing words on the mobile phone. The working principle of the confusing words is: for example, our mnemonic is 11 abandon + about ( This is a set of effective mnemonics). When we enter a mnemonic on the mobile phone, the cold end will prompt:
Please enter the 3rd mnemonic in the mobile phone (enter abandon)
Please enter cat on your phone
Please enter the 12th mnemonic on your phone (enter about)
Please enter dog on your phone
…
Please enter the 6th mnemonic in the mobile phone (enter abandon)
Please enter region on your phone
cat, dog, region are confusing words
But is confusing words + shuffle word order really useful?
If the 12-word mnemonic, plus 12 obfuscated words, are hijacked by the hacker, the hacker brute-forced the correct mnemonic through the form of checking the validity of the mnemonic mentioned above. Hash, this number looks great, but the computing power of Ant S17 + has reached 73000000000000 hashes per second. It only takes 18 seconds to brute force the correct 12 mnemonics.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Repeated mistakes | Can cryptocurrency prevent the next recession?
- FCoin releases latest announcement: funding gap of approximately 90 million USDT
- Vitalik Buterin: Ethereum 2.0 Phase 0 is expected to start this summer, and PoS will eventually become a reality
- Airdrop BTC! Billionaire Tim Draper asks you to learn blockchain
- Opinion | Analyst Willy Woo: Bitcoin will reach $ 135,000 in a bull market, but the worst is also planned
- Observation | How did Ripple's performance with the payment giant MoneyGram 8 months after its alliance?
- SheKnows | Thunderstorm, Attack, Vulnerability! What will protect you, my BTC?






