Introduction to blockchain | The key technology for blockchain to trust: asymmetric encryption
In "Want to safely keep assets, you must first know the knowledge of the wallet", we can understand what is the private key and what is the public key in these wallets in the blockchain.
The public key can be compared to a bank account, and the account address is similar to the bank card number, and the private key can be viewed as a combination of the bank card number and the bank card password . Such an analogy seems to have a clearer understanding of the terms of the private key, public key, and address in the blockchain, but in fact the theoretical support behind these nouns is asymmetric encryption technology. What kind of technology is it today? Dabai will give you a popular science.
First, let's talk about symmetric encryption before talking about asymmetric encryption.
Symmetric encryption, also known as single-key encryption, refers to encrypting and decrypting information with the same key. Simply put, locking and unlocking are both a key.
- Developers propose a bitcoin test network alternative, Signet or solve many problems with the current version
- Babbitt Column | How Cross-border Financial Blockchain Service Platform Achieves Cross-border Receivables Financing and Trade Linkage
- If you are optimistic about the PoC project, you should buy the stock of Seagate hard drive directly.
For example, in real life, you want to send a letter to your friend. In order to not be plagiarized by others, you will think of using a key to lock the letter in a safe cabinet, and then send the item together with the cabinet. To a friend, and your friend can only use this key to open the cabinet and take out the letter. This ensures that the letter is not seen by others during the mailing process. The above process in cryptography can be understood as follows:
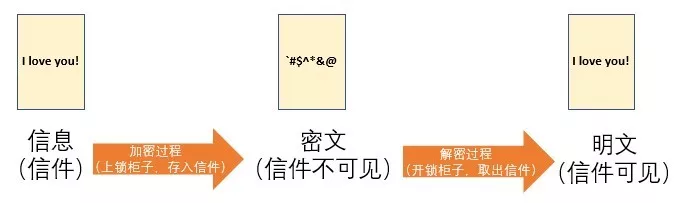
In the process of the above figure, the same key is used for both “locking” and “unlocking”. This key is equivalent to the “private key” in symmetric encryption, and the process of “locking” and “unlocking” is equivalent. "Encryption" and "decryption" process, "letter" is the information we want to encrypt, after the information is encrypted, it is "ciphertext", and after decryption, it is "clear text".
However, the careful little partner may think that it is safe to lock the letter into the cabinet, but the key to use the lock must be used to open the cabinet. The question is how to give this key to a friend? Once the key is selected for mailing, there is a security risk, unless the key is given to a friend, so why not give the letter directly to a friend. So one problem with symmetric encryption is the difficulty of key distribution.
For the problem of key distribution, the great invention in the history of cryptography, asymmetric encryption, has emerged.
Asymmetric encryption has a pair of keys, a private key and a public key. The public key and the private key are in one-to-one correspondence. The private key needs to be kept secret, and the public key can be made public. Encryption and decryption do not use the same key.
Going back to the previous example, your friend went with a pair of keys (key A and key B). After the key A locks the cabinet, the key B must be used to unlock the cabinet . Your friend mailed the key A to you. You use this key to lock the letter to the cabinet, then mail the cabinet to your friend. Your friend uses the key B to open the cabinet and take out the letter. The careful little friend thinks again. When a friend sends the key A to himself, the courier may steal the key, but even if the courier holds the key A, he cannot open the cabinet because the key A locks the cabinet. Only the key B can unlock, the whole process, the key B has been in the hands of friends, as long as the friend does not lose the key B, this cabinet can only be opened by friends.
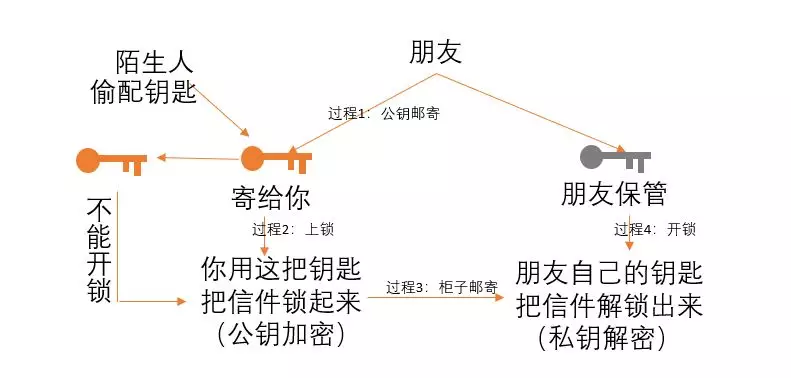
In asymmetric encryption, the key A is equivalent to the public key. It is irrelevant to know that the key B is equivalent to the private key. It needs to be carefully preserved by the holder and cannot be lost. "Locking cabinet" and "unlocking cabinet" are relative to "encryption process" and "decryption process", and in asymmetric encryption, the most important thing is that encryption and decryption are not the same key, but a pair of keys. , the private key and the public key. The bitcoin public key is derived from the private key. The public key continues to be converted into an account address, and the private key cannot be deduced . The private key and the public key are a pair. The user needs to properly keep his private key. The public key and account address are publicly available.
The above process reflects public key encryption and private key decryption . In the blockchain, when someone else transfers you, your payment address (public key) is open to others, and the transferred asset can only "decipher" it if you hold the private key, and freely control it. .
Another case is private key encryption and public key decryption . A typical application scenario is digital signature. A encrypts the file information with its own private key and sends it to B, and sends the public key to B. B uses this public key to decrypt the information. If C and D also have this public key, then C and D can also decrypt this file information, but only A holding the private key can encrypt this information, so it can be ensured that this file information is indeed issued by A, which is more suitable for some company CEOs to do electronic signatures. To ensure that the signature is signed by the boss. In the blockchain, your payment address is equivalent to the public key, which everyone can see, but if you want to transfer your assets to a friend, you need to enter a password (private key) to digitally sign the asset. It is indeed from you.
Through the above explanation, I believe that everyone has realized the importance of the private key. How do you generally save your private key? Welcome to leave a message in the message area!
——End——
Author | Tang Yuxing
Produced|Baihua blockchain (ID: hellobtc)
『Declaration : This series of content is only for the introduction of blockchain science, and does not constitute any investment advice or advice. If there are any errors or omissions, please leave a message. 』
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Will Libra with multiple currencies/assets be more “stable”? – Libra operating mechanism conjecture
- The fissure of the world economy – the civil war, the foreign war and the full battle of money
- Research | Model currency principle analysis and prevention guide
- Economic Daily | Libra, is the super currency coming? Zhou Xiaochuan said this
- This college student can help you forge the transaction volume, online CoinMarketCap, only 15,000 US dollars
- Carry out the cryptocurrency road to the end! The Japanese government is creating a global cryptocurrency payment network similar to SWIFT
- At the Libra hearing, I found an alternative member of the book about Ben Satoshi and Bitcoin.