IOSG Ventures In-depth Exploration of New DeFi Unleashing the Potential of Data
IOSG Ventures Explores New DeFi, Unleashing Data PotentialOriginal author: Momir, IOSG Ventures
Smart contracts have limitations because they lack the ability to interact with the environment, which limits the development potential of decentralized applications (dApps). In order to achieve more complex functionality, DeFi protocols have two options: they can adopt flexible designs, such as allowing players to personalize the handling of various scenarios; or they can introduce external dependencies – relying on off-chain infrastructure such as oracles, keepers, or off-chain computation – to maintain a simple user experience.
In a recent thought-provoking article titled “Why DeFi is broken and how to fix it – Part 1: No oracle protocols,” Dan Elitzer advocates for the use of DeFi primitives with zero external dependencies to minimize attack vectors. The idea is to eliminate the need for trust in third-party institutions. However, a zero-dependency DeFi ecosystem will inevitably require higher specialization. Most users lack the time, expertise, or resources to become liquidity providers on Uniswap v3 or evaluate the quality of collateral in protocols without external dependencies, so they have to rely on trusted intermediaries to participate.
Therefore, the pursuit of zero dependencies may bring us back to square one, or worse, force non-professional users to trust complex entities or deposit funds into transitional smart contracts, which increases the insecurity. Instead of striving to completely eliminate external dependencies, it is better to consider more practical methods, such as stricter scrutiny of external dependencies and limiting potential black swan scenarios. We must recognize that some degree of dependency is inevitable and crucial for the industry’s development.
- Opinion Transitioning from SNARK to STARK is the inevitable path to zkSync’s multi-chain vision.
- Opinion 5 Reasons Why UniswapX Will Change the Rules of DEX, MEV, and Interoperability Games
- Chainlink Cross-Chain Interoperability Protocol (CCIP) goes live on the mainnet, how does it bring security to cross-chain?
In well-known DeFi projects, early versions of Uniswap come closest to achieving zero dependencies. However, the recent introduction of Uniswap v4 indicates a trend towards a modular approach (“Hooks”) to drive the advancement of this field.
Data Primitives
The discussion about external dependencies mainly revolves around the ability of smart contracts to interact with external data. Today, data interaction typically relies on oracles to access off-chain information, although the scope is limited (mainly including the prices of major cryptocurrencies).
As more and more activities migrate to the blockchain, a large amount of valuable on-chain data can be used to enhance mechanism design in an algorithmic and transparent manner. However, despite the transparency of on-chain data, integrating it with smart contracts is not easy. Reading, processing, and delivering meaningful data requires the establishment of a complex and trusted infrastructure. Therefore, developers often rely on existing tools to meet their data needs. However, most existing data solutions are rooted in Web 2.0 frameworks, and even many Web 3.0 native protocols cannot guarantee the accuracy of the data they provide.
Sushiswap Discussion on the Inaccurate Data of Polygon Sushi-Matic Subgraph
Considering that smart contracts can manage billions of dollars in deposits, it is neither acceptable nor practical for them to directly connect to a trusted API source, as this dependency would undermine the decentralized nature of the blockchain ecosystem.
Building Tamper-Proof Data Solutions
Our investment philosophy revolves around the fundamental belief that tamper-proof data will be the cornerstone of the next generation of DeFi protocols. However, achieving tamper-proof data is not a simple task, as it requires complex infrastructure and extensive optimization to make it economically viable.
In this context, SLianGuaice and Time have emerged as pioneers in building tamper-proof data infrastructure. A key component is its SQL proof, which is an improvement on SNARK proofs specifically designed for querying data from relational databases. This approach provides guarantees to ensure that the queries and their underlying data are not tampered with. Furthermore, it provides data integrity guarantees when retrieving data from archival nodes through RPC calls.
Other well-known projects in the field of trustless data primitives include but are not limited to Nil Foundation, Axiom, Brevis, Herodotus, etc.

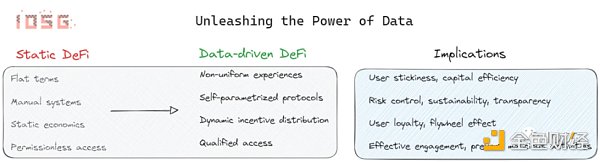
Tamper-proof data opens up new possibilities for DeFi protocols, enabling them to break through the limitations of functionality and drive further growth and innovation in the industry.
Below, we will discuss data-driven protocol design optimizations in the following cases:
1. Personalized user experience
2. Self-parametrizing protocols
3. Protocol economics
4. Qualified access
1. Personalized User Experience
In the field of technology business, providing customized services to users is commonplace. However, smart contracts (essentially code strings representing certain business logic) often result in a unified user experience, which is typically equivalent to a poor user experience. For example, on some lending platforms, User A is a novice, User B is a long-term protocol user, and User C is a seasoned trader. This lack of differentiation fails to explain user behavior and misses opportunities to enhance user stickiness, incentivize positive behavior, and optimize capital utilization.
Protocols have a vested interest in identifying user behavior and making corresponding adjustments. For example, by leveraging credit ratings, offering cheaper credit or lower collateral ratios to well-performing customers. Such a project would naturally attract users away from platforms with uniform terms. Additionally, this approach provides users with implicit incentives to exhibit good behavior in order to obtain more favorable conditions.
Thinking from the perspective of fintech, companies like SoFi have gained market share by rejecting standardization, and DeFi dApps can learn from this approach. For example, SoFi identified the inefficiency in the student loan market, where Stanford University graduates were charged the same loan rates as other borrowers, despite having a higher likelihood of securing high-paying jobs after graduation. By adjusting rates to better reflect users’ risk profiles, SoFi achieved significant success.
Similarly, in the DeFi field, we envision an opportunity for an innovative protocol that incorporates user risk into interest rates and collateral factors. However, caution must be exercised not to rely solely on existing historical data for undercollateralized lending, as historical data becomes irrelevant when game theory changes.
It is worth mentioning that projects like Spectral and Cred Protocol are attempting to establish credit scoring models from on-chain data. However, these projects operate on centralized databases, so as long as the data and models they serve come from centralized sources and are easily tampered with, major DeFi protocols are unlikely to connect to their APIs. On the contrary, if these projects adopt tamper-proof solutions, they have the potential to become ubiquitous DeFi oracles, powering a range of innovative applications.
2. Self-Parametrizing Protocols (Minimizing Governance Intervention)
Many DeFi protocols still rely on manual governance processes, typically guided by off-chain consulting firms, to adjust their parameters. For example, AAVE pays hefty sums to external consulting firms to monitor and guide protocol risk parameters.
However, this approach raises several issues:
1. Lack of real-time support: The system lacks the ability to respond to constantly changing market conditions or emerging risks.
2. Manual system: Dependency on human intervention introduces latency issues and potential inefficiencies when adjusting protocol parameters.
3. Trust in off-chain entities: Relying on external consulting firms raises concerns about transparency and the methods used when making recommendations.
This static approach was exposed in an attack on AAVE, resulting in bad debt that could have been avoided with appropriate lending parameters that better reflected the liquidity of borrowed tokens. Additionally, the risk of using circulating tokens as collateral in lending protocols has not been fully addressed.
To address these limitations, projects should transition towards designs that are real-time, automatic, transparent, and trustless. For example, lending protocols can leverage infrastructure similar to SLianGuaice and Time to monitor data in real-time. This would enable them to dynamically adjust collateral, lending parameters, and other key parameters.
Similarly, exchanges can introduce dynamic fee structures based on volatility or impermanent loss. Many liquidity pools built on Uniswap v3 struggle to achieve sustainable operations mainly due to the inability to dynamically charge LPs. With Uniswap v4’s Hook or Valantis modules, dynamic fees become possible.
Furthermore, aggregators can adapt to the constantly changing risks and returns of underlying protocols without being influenced by manual and fixed fees. The collaboration between Spool and Solity is a step in this direction, with Solity using big data methods to analyze pool risk-reward.
3. Protocol Economics
Data-driven approaches have the potential to enhance protocol economics and token economic models in DeFi, where projects can share incentives with eligible users.
For example, a DEX aggregator seeking user stickiness and loyalty can allocate slippage profits to users who meet certain conditions, such as executing a specified number of trades and reaching a minimum trading volume.
Such incentives incentivize early users in large numbers, build loyalty among user communities, and directly provide incentives to existing users to promote the protocol’s use within their own groups.
4. Qualified Access
Although blockchain has the nature of permissionless, it also allows for selective freedom. In multiple cases, permissioned access at the application layer can ensure that the protocol is not used for malicious purposes or effectively interact with the target user group.
For example, privacy protocols like Tornado Cash are under scrutiny by regulators because they can be used for money laundering or other illegal activities. To prevent money laundering, protocol developers can take measures to prevent bad actors from interacting with their platforms.
In addition, it is valuable for market makers to know their counterparties, but DEXs usually cannot obtain such information. Assuming it is possible to use data to construct proof of human, DEXs can only allow non-bot addresses to interact, and this type of problem can also be solved.
Requirements for Verifiable Computing
By integrating with trustless data primitives, the contents discussed above can be fully realized. However, others will require additional resources to perform statistical calculations or machine learning. For example, a credit scoring project can leverage tamper-proof data, but still requires machine learning algorithms to generate credit scores.
Or under the premise of a Risk Oracle, obtaining data on the circulating supply, quantity, transaction count, number of holders, time since TGE, etc. for the relevant specific tokens is crucial for determining appropriate collateral and lending factors. However, machine learning techniques require precise calculations based on this data.
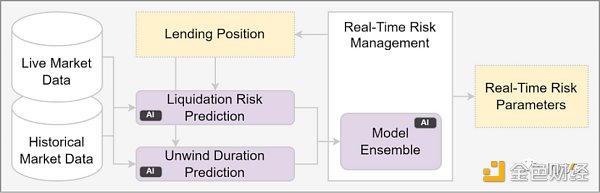
source: https://chainml.substack.com/p/web3-needs-ai-to-realize-its-potential
Other areas in DeFi that require more complex calculations include but are not limited to:
-
Yield aggregators: estimate the yield and risk of underlying protocols and find optimal allocations.
-
Portfolio optimization: calculate the allocation of the target investment portfolio based on predefined criteria, change directional exposure based on technical indicators, etc.
-
Decentralized derivatives exchanges: systematic risk management, funding rate adjustments, derivative pricing, etc.
-
Advanced trading execution algorithms
-
Liquidity pool market-making logic
-
Clearinghouse
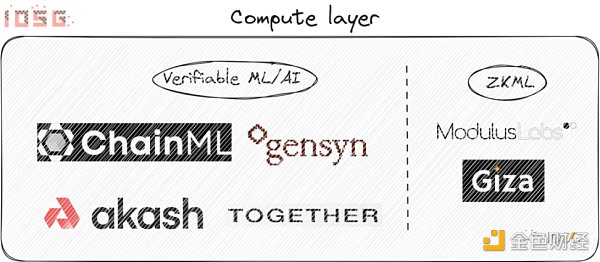
Projects like ChainML meet this demand by providing a verifiable off-chain computing layer and are supported by specially designed consensus mechanisms. Others building distributed machine learning computing layers include but are not limited to GenSyn, Together.xyz, Akash, etc.
Similarly, ZKML provides an interesting opportunity where ZK proofs can compress computations into succinct proofs that can be verified on-chain or demonstrate the use of specific models without revealing their attributes. Examples of ZK projects include Modulus Labs, Giza, etc.
However, implementing machine learning in ZK is currently very expensive, which increases the challenges of actual implementation. While hardware acceleration and circuit optimization may improve performance in the future, the computational demands of artificial intelligence are expected to grow at an even faster rate. This limits ZKML to niche computational methods and makes it unable to accommodate state-of-the-art artificial intelligence models. Therefore, approaches such as the consensus-based pessimistic approach or the fraud-proof-based optimistic approach provided by projects like ChainML may be the best opportunities to integrate the latest artificial intelligence algorithms into Web 3.0.
Summary
The fusion of tamper-proof data, advanced computing power, and data-driven decision-making has the potential to unlock new innovations, improve efficiency, and enhance user satisfaction in the DeFi ecosystem. Although this article focuses on optimizations that can be performed on-chain data primitives, we are also optimistic about the opportunities brought by integrating various off-chain data through zk proofs. We believe that data will enhance the interoperability between on-chain and off-chain, facilitating the integration between decentralized finance and the traditional financial system.
As the industry continues to evolve, protocols must embrace emerging technologies, collaborate with leading projects, and prioritize transparency and trustlessness. This not only establishes a strong and sustainable future for DeFi but also has the potential to have a profound impact on the global financial landscape, fulfilling the vision of DeFi’s desire to make a significant impact.
Disclaimer: SLianGuaice and Time, ChainML, Nil Foundation, and Solity are portfolios of IOSG.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Who is Tom Emmer? Majority Whip in the US House of Representatives active in the cryptocurrency field.
- Official Interpretation of UniswapX and How Does UniswapX Work
- The growth of RWA is driven by US Treasury Bonds.
- Venus 2023 Q2 Report Reasons and Outlook Behind Revenue Growth
- LianGuai Morning News | Aave’s USD stablecoin GHO surpasses a market value of $2.5 million within 48 hours
- LD Track Weekly Report ETH Staking Rate Breaks 20%, Layer2 TVL Breaks $10 Billion
- Ethereum EthCC officially opens, conference highlights (continuously updated)