Japan-Korea exchange stolen, U.S. sanctions Chinese OTC money changer? 3800BTC transaction reveals the process behind
Recently, the U.S. Treasury Department's Office of Foreign Assets Control (OFAC) announced that two Chinese citizens have been sanctioned for helping North Korean Lazarus hacking team to launder money through the Bitcoin OTC business. According to information disclosed by OFAC, the amount involved has reached 9,100 Ten thousand U.S. dollars. A sanctioned Chinese citizen stated that he was unaware of it. After he purchased bitcoin from the accused another Chinese citizen on the Coca-Cola OTC market, the assets were frozen by the platform at the end of 2018, so he But also the victim.
According to public information, this case involved the USD 250 million worth of digital assets stolen by Lazarus. The hackers transferred the relevant Bitcoin assets to four exchanges, and the two Chinese citizens involved in these cases participated through OTC services. In the process of money laundering.
Naturally, people have speculated about the digital asset theft case involved. In the article disclosed to the media, OFAC did not mention the specific exchange name, but did mention the relevant process. In April 2018, employees of an exchange A malicious program distributed by Lazarus in the email was downloaded, allowing hackers to hack into the system and steal keys. Then, the exchange's $ 250 million worth of digital assets were stolen, accounting for half of the total digital assets that Lazarus was expected to steal that year, and 2018 was also considered the most active year for the hacker group.
- Market analysis: market trading sentiment has recovered, and the bulls have begun to exert their strength?
- World Economic Forum: Can the blockchain get rid of the speculation in 2020?
- Top conversation! Coinbase CEO's Fireside Talk with A16z Founder: Blockchain and the Internet Resemble Each Other
According to publicly disclosed information, after April 2018, the exchanges that have admitted to stealing large amounts of digital assets are mainly Coinrail, Bithumb, and ZAIF. The theft of these Japanese and South Korean exchanges has been speculated to be related to Lazarus. Of course, we also do not rule out that although some exchanges have been stolen, they have not disclosed them to the public and instead report cases directly to law enforcement.
According to relevant information, Beijing Chainan tried to restore the relevant process to a certain extent through ChainsMap on-chain traceability system, and revealed the current industry's challenges in anti-money laundering of digital currency illegal activities.
OFAC announced on its official website 20 addresses of two Chinese citizens involved, of which LI, Jiadong (hereinafter referred to as LI) involved 12 addresses, and TIAN, Yinyin (hereinafter referred to as TIAN) involved 8 addresses. It can be found that they belong to at least four exchanges such as Coincola and LocalBitcoins. The first transactions of these addresses occurred as early as July 2017, and the latest occurred in October 2018. At present, the relevant addresses are no longer active.
We further counted the number of bitcoins flowing into the relevant addresses. It should be noted that this is only a concept of one-way transaction volume and does not rule out repeated ingress and egress. Although LocalBitcoins accounted for at least 9 of the 20 addresses involved, most of these addresses were only used once or twice, and the total historical amount involved was only 67. Coincola has become the main OTC transaction exchange for the two involved in the case. The historical inflow of bitcoin from one address of LI on the exchange reached 1449 BTC, and the total inflow of historical bitcoin involved in TIAN's five addresses on coincola exceeded 8000 BTC. Here, we again emphasize that the BTC inflow mentioned here is a concept of historical transaction record accumulation. At the same time, these bitcoin amounts are also the total amount after the first transaction of the relevant address, and the money laundering transaction accused by this OFAC is only part of it.
So what are the characteristics of transactions involving Lazarus? Based on the historical transactions of these addresses, we found a batch of related transactions through backtracking and correlation. Here we just give an example.
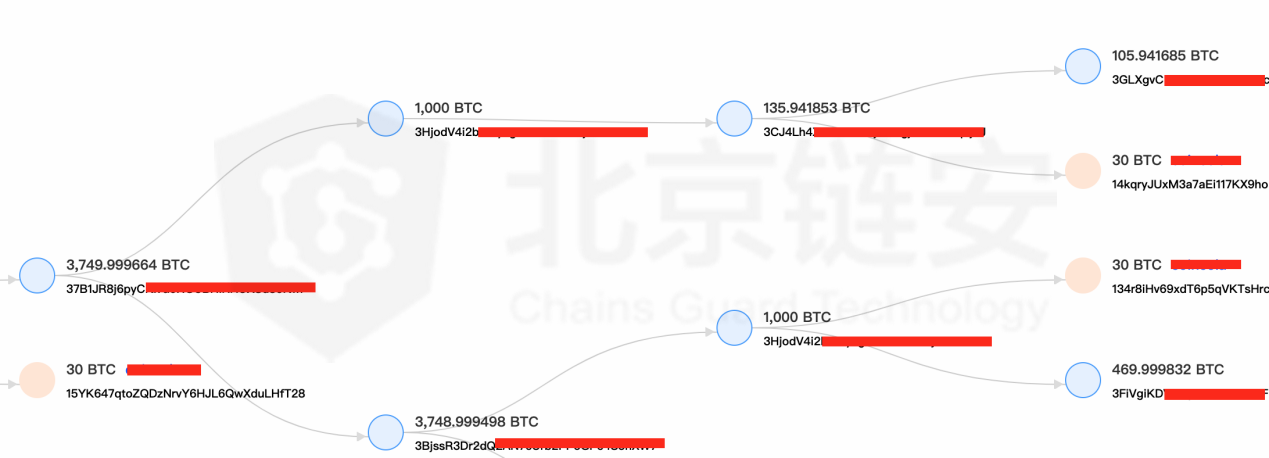
On December 12, 2018, a large bitcoin-related UTXO of 3800 BTC began to continuously transfer and divide some bitcoins into the exchange. As we can see in the figure, OFAC's public address is included, and each inflow of 30 BTC.
From the source of 3800BTC, most of them come from HitBTC's transfer from June 25 to July 5, 2018. So was HitBTC hacked? From the perspective of these transactions, this possibility can be ruled out, because they are all initiated by hot wallets and simultaneously initiated to multiple unrelated addresses with a large amount of difference, that is, the typical currency exchange transactions that meet users' withdrawal requirements . In the involved LocalBitcoins address, most of the bitcoins received were directly from the withdrawals of some exchanges.
Since the digital assets stolen by the exchanges previously attacked by Lazarus are not only bitcoin, but also involve multiple types of currencies, we can speculate that during their money laundering process, there are some exchanges that enter other exchanges to exchange other currencies for bitcoin on the exchange. After that, it will be transferred to other exchanges for OTC cash realization. At the same time, according to the disclosed information, after the relevant bitcoin was realized, not only did it not only enter the bank account, but even 1.4 million US dollars flowed into Apple iTunes gift cards, and digital currency money laundering has been closely combined with traditional multiple money laundering methods.
Taken together, although the information released by OFAC involves a specific theft of an exchange, the actual digital assets involved in the case are likely to originate from multiple hacking incidents of hackers, and have undergone on-site transactions in the middle, flowing to more Multi-industry and service funding channels. Beijing Lianan believes that the current digital asset money laundering is a complex process across exchanges, currencies, and industries. Whether from the perspective of industry or government regulation, professional technical means, laws and regulations, and industry consensus and collaboration are urgently needed .
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Viewpoint | Reveal the truth of Bitcoin's "halving market", will history really repeat itself?
- Ethereum founder Vitalik Buterin: digitalization is inevitable with or without blockchain
- Beam Sync: a new way to synchronize Ethereum nodes
- Depth | Legal and regulatory allowance, why hasn't Japan succeeded in an ICO?
- China's banking industry has landed dozens of blockchain applications, who is providing technology for financial giants
- New York Greenidge Power Plant installed 7,000 miners, daily mining value of $ 50,000
- Crypto investment fund Trident hacked, data leaks of 266,000 users






