One article understands that the 200 million yuan digital currency of the giant whale was stolen, and it is impossible to retrieve it
Text: Huang Xueyi
Produced by: Odaily Planet Daily
The depository security of digital currencies has once again attracted attention.
- Babbitt Column | PoW agreement reasonableness, PoS meets humanity
- Ethereum mining may usher in huge changes, core developers tentatively upgrade ProgPoW in July to resist ASIC miners
- Will ICO investors get compensation? U.S. regulators reach agreement with companies
On the morning of February 22, Beijing time, a user claiming to be "zhoujianfu" posted a message on Reddit.com for help, claiming that he had just lost 1547 bitcoins and less than 60,000 bitcoin cash (currently totaling 260 million yuan) , And PO gave out his own address. Coin Seal founder Pan Zhibiao confirmed his signature, confirming that "the address is indeed his". At the same time, the security team found that the stolen Bitcoin was currently being split into small amounts and flowing into the exchange.
In addition to paying close attention to the flow of funds, it has become a hotly debated topic about who the loser is, how hackers can attack stolen coins through the "SIM hack", and whether BCH miners can help the giant whale to roll back the transaction and recover losses.
 SIM hack: Behind or because of
SIM hack: Behind or because of
Blockchain.info security system flaw
The distress message released by zhoujianfu on Reddit suggests that the implementation of this attack was suspected to be through a SIM card.
The slow mist security team speculated that the attack process might be as follows:
"The big customer should use a well-known decentralized wallet service, and this decentralized wallet actually requires SIM card authentication, which means that there is a user system that can turn on two-factor authentication of SMS based on SIM card. It is speculated that it may be Blockchain.info, because it fits these characteristics, and historically the SlowMist security team has received several threats of stolen coins from Blockchain.info users, and Blockchain.info's security system is not good enough. " The Slow Mist security team said.
So how do hackers get SMS verification codes?
According to industry insiders, when we lose our SIM card, we usually go to the carrier to apply for a "portable" SIM card, which allows customers to transfer that phone number to a new SIM device. In most cases, this is completely legal. request. Hackers use this vulnerability to technically port victims' SIM cards to phones they control. The attacker then initiates a password reset process on his email account, a verification code is sent from the email provider to the phone number, and since the attacker now controls the SIM card, it can be easily tampered with.
Once the attacker has control of the victim's primary email account, they will start trying to monetize online services (bank accounts, social media accounts, etc.) managed by email addresses. The attack process is shown in the figure:
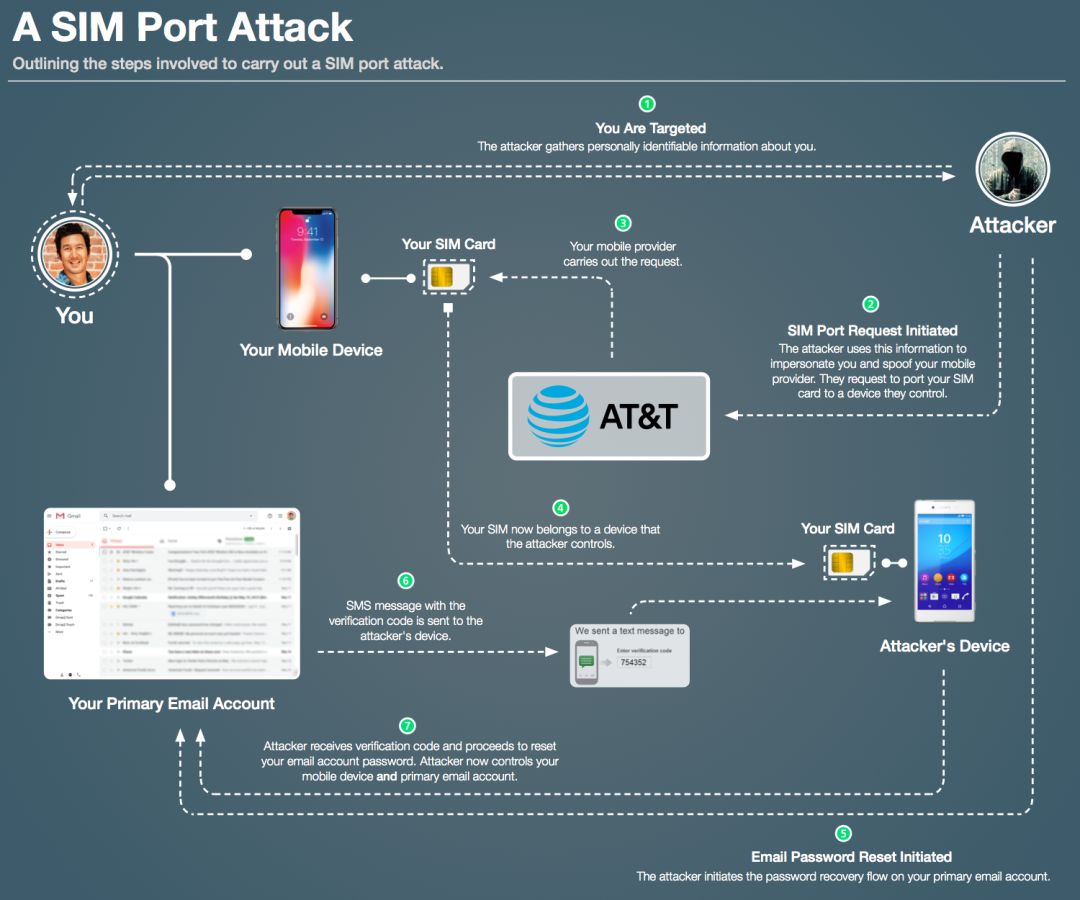 Therefore, secondary authentication based on mobile phones and emails is not a completely secure and effective method. In response, industry insiders have called for us to try to use services with higher security settings such as 2FA. (Note: 2FA is a set of dynamic passwords based on natural variables such as time, history length, physical objects (credit cards, SMS phones, tokens, fingerprints), etc., combined with a certain encryption algorithm, which is usually refreshed every 60 seconds. Cracked, relatively safe.)
Therefore, secondary authentication based on mobile phones and emails is not a completely secure and effective method. In response, industry insiders have called for us to try to use services with higher security settings such as 2FA. (Note: 2FA is a set of dynamic passwords based on natural variables such as time, history length, physical objects (credit cards, SMS phones, tokens, fingerprints), etc., combined with a certain encryption algorithm, which is usually refreshed every 60 seconds. Cracked, relatively safe.)
 Killer whale: once the second largest creditor in Mentougou
Killer whale: once the second largest creditor in Mentougou
The owner is Josh Jones, whose Twitter ID is zhoujianfu, which is consistent with the stolen signature (it is reported that he took a Chinese spelling name because his wife is Chinese).
According to public information, Jones is an open source software and alternative currency technology expert. He is also the founder of Topcoin and Bitcoin Builder. Jones was a member of the company's board until Inktank was acquired by RedHat. Previously, he was co-founder and interim CEO of DreamHost, a web hosting company. He also founded ePub Bud and serves as a director of Group B Strep International.
It is worth mentioning that this is not the worst loss for Jones. Jones claims to own 43768 Bitcoins in Mt.Gox (some belong to him personally and some belong to his website users), and his company is the second largest creditor of Mt.Gox .
Industry insiders said that he might have been spotted long ago. The real names and emails of the people in the Mentougou incident were public, and the risks were very high.
 Is it possible for Shuanghua to find coins?
Is it possible for Shuanghua to find coins?
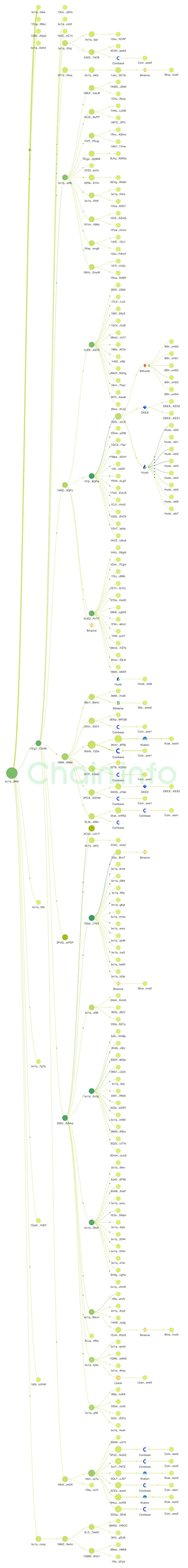
The latest news, Chain.info tracked the owner ’s address and found that one of the stolen funds of 1500 BTC was split into two approximately 750 BTC funds after entering the two addresses. After the amount is split, the remaining 746.64 BTC enters a new address and the flow is suspended. The other one enters an address that was activated on 2019.12.13. After tracking, the address was historically transferred to multiple exchanges within three to five days. Funds. At present, the address has been emptied and most of them have entered a new address. The remaining funds are being split in small amounts and mixed with other transactions.
If it is not frozen in time after entering the exchange, I am afraid that this asset of zhoujianfu will be hopeless.
Earlier, Coinprint founder Pan Zhibiao proposed another possibility of recovering on Weibo, "Begging BCH miners to help him recover 60,000 coins (BCH) in double spend. Technically speaking, it is still time to restructure the double spend."
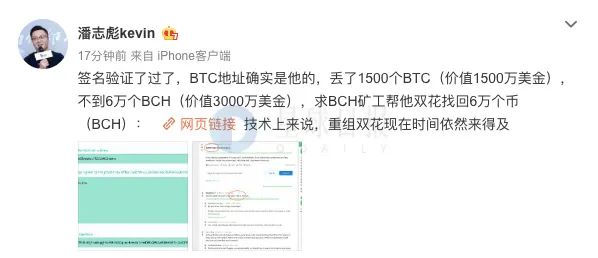
But BCH supporter "Rail Tracker" told Odaily Planet Daily that this possibility is now zero.
"In theory, it is possible to retrieve lost BTC through double spending, but the market value of BTC is huge and many stakeholders are involved, so there is only a theoretical possibility; and the double spend through BCH may not even have a theory."
The Railway Tracker added that after BCH and BSV separated from each other at the end of 2018, in order to prevent attacks, BCH added a setting of more than 10 confirmations that cannot be rolled back. Therefore, although the BCH computing power is small, it has a strong resistance to double flowers. For example, if there is only 100 P hash power left on Bitcoin after a hundred years, and suddenly there is a 4000 P hash power, guess where you can roll back? Theoretically, it can return to the height of 618466, which is now.
Finally, put a tracking chart of Chain.info on the lost coin address.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Financial giant Fidelity invests more in crypto, invests $ 14 million in HKL OSL operator
- PAData: FCoin potential victims or more than 2000 people, per capita loss or more than 25 BTC
- The last predictable halving bull market in the currency circle?
- Chengdu chain security: stolen killer whale users may have sustained attacks
- Opinion | Satoshi Nakamoto's idea of multi-client proves correct?
- CoinGeek Conference 2020 | Satoshi Omoto: You have a misunderstanding about Bitcoin!
- Why did Facebook create the Move language for Libra? Calibra digital executive tells the inside story





