Online Salon: Privacy Security Computing, Value Geometry?
On June 21st, this "Conversation Chief" invited Trias CTO Wei Ming, ARPA co-founder & CEO Xu Maotong and TEEX co-founder Yu Wei as the main guests.
Three media observation groups : Chain Wen Gong, Chain Ade and Mars Finance Sun Hao. At the same time, "Dialogue Chief" also welcomes the chiefs of various blockchains such as exchanges, wallets, mining, etc., and participates in our activities to jointly contribute to the development of the industry.
The following is the [Dialogue Chief] text finishing version:
/The first link: chain smell question /
Chain Wen Gong: The privacy topic of this discussion has a Facebook incident that has been raging before. Regardless of the implementation of the General Data Protection Regulations (GDPR) of the European Union or the publication of the “Data Security Management Measures (Draft for Comment)” by the China Internet Information Office, the focus on data privacy protection continues to increase worldwide.
- Libra: The ambition of the social empire Facebook
- Billion International Hong Kong failed to list: a new round of bitcoin rose failed to rescue the third largest miner
- Bitcoin once again rushed for 10,000 US dollars a year, chasing high or clearing?
The first question: As a pioneer in the field of privacy and security computing, I would like to ask what is the original intention of entering the industry. What are the considerations when choosing the current technology path?
Trias CTO Wei Ming: Original intention: because of the experience of working before. It is found based on conventional security technologies such as DLP, AES encryption, HTTPS encryption, UEBA user behavior portraits, and the like. In fact, the effect of data leakage and illegal tampering has not been ideal . If you look at the annual safety news, you can know that it must be a year-to-year loss due to data security issues.
When I was not starting a business, my classmate was also the founder of our Trias. After returning from Oxford, he brought TEE technology to the show. At that time, I felt that this technology can be compared with many existing security technologies. Better solve the problem of data privacy. So this is the original intention.
Technical road selection:
(1) From the experience we are now landing, data security issues, regardless of the use of any single powerful security technology, such as XX encryption, XX wall, XX artificial intelligence analysis. We don't think we can solve the problem very well. It is necessary to select the corresponding combination to solve according to different security technology characteristics and characteristics;
(2) Based on (1), we chose the TEE+ blockchain approach. Because TEE can solve the trusted operating environment, the blockchain can solve the data authenticity will not be illegally tampering, it is just a very good combination of left and right complement.
ARPA Co-founder & CEO Xu Maotong: Thank you, Teacher Wei, and I also talk about my own opinion:
(1) First of all, data is the most important asset in the Internet era . Nothing. The security and privacy issues brought by massive data are always the opposite of angels and devils. If the data can be efficiently transferred and utilized, how big is this market? I think there are ten trillions .
(2) There are endless leaks of privacy. You can clearly feel that the voices of data supervision and protection have become more and more high in the past two years, and each leak is closely related to our lives.
For example, the hotel opened data of the hotel (laughs), such as Facebook was exploding before the 2016 US election, leaking 50 million user data, and also accepted the SEC's inquiry. Of course, Facebook is now leading the Libra estimate to be asked. Including the supervision of KYC and transaction data obtained by Libra, I think it is worth considering and discussing.
▲ Image source: Guest sharing
So when it comes to the creation of ARPA: I did early investment in Fosun Group before creating ARPA. The investment industry is mainly financial technology and big data. When you look at projects, do your best, and do large business interviews, you often encounter situations where companies face data silos and cannot effectively use external data to solve business problems . For example, in the current direction of To B, the "data in the middle" is to open up the data island inside the enterprise . And the disconnection of data islands between enterprises will be many times larger than the data in the middle of the platform!
ARPA's vision is to become the infrastructure for secure sharing of private data . Through the ARPA privacy computing network, every company, government department, and individual can choose who their data is used, and at the same time get rewards, and any confidentiality or privacy throughout the process. The data will not be exposed.
Choice of technical path:
First of all, this is related to our team. Our cryptography institutes Alex Su, Dragos Rotaru and Mark Simkin are experts in the MPC field, following top professors such as Ivan Damgard and Nigel Smart. So we chose the MPC with pure cryptographic algorithm, and the technical path is secret sharing.
Secondly, we do think that MPC and blockchain have a lot of similarities. For example, they are decentralized. The blockchain is a decentralized ledger, while MPC is a decentralized operation on encrypted data. It is a natural combination, and it will not encounter the problem of TEE comparative centralization and engineering loopholes. Mathematics is more beautiful.
Of course, I will also say that the end points of TEE and MPC are the same, and the usage scenarios are very different. They are all very good technical paths.
TEEX co-founder Yu Yu: Ok, thanks to the two teachers. Everyone knows that our team is mainly from the academic research background of colleges and universities. Our earliest contact with the blockchain was also at the end of 17th, because the blockchain has been particularly hot, and the team itself is doing system security and trusted computing. The nature of the blockchain is related to security and trust, so we began to conduct in-depth research on blockchain technology.
We find that due to the nature of the blockchain itself, it will cause great problems in its privacy and scalability. The technology of using TEE, which is the trusted execution environment, can be well matched with the blockchain. Combined, through a layer-2 scheme of Layer-2, the existing trust model can be partially reconstructed , which can greatly improve the scalability of the blockchain and protect the privacy of data and computing.
Based on this research, we also published the first domestic and international academic papers on privacy calculation and privacy intelligence contracts in the first half of 18 years, and which are professionally reviewed by peers (unlike the direct placement of arXiv), which is also official. Stepped into this field.
Then, as the data protection laws of GDPR are launched, we are also thinking more about how to combine the blockchain with the real world to make it truly valuable. We all know that the blockchain itself is a closed autonomous system, without I/O, unable to interact with the real world, and our data, whether it is personal data in the Internet world or data in the enterprise information system, will be When they are combined with blockchains, they need a bond and a bridge. I think this is a trusted calculation.
We can ensure the authenticity and privacy of the uplink data through the security hardware, ensure the data through the blockchain, and then share and share the data without guaranteeing the privacy, so as to generate greater value. This is a reflection and original intention we have always had.
There are also two main reasons for choosing a technology path:
First of all, of course, because our team has a deep accumulation in the operating system and TEE field. Our team has more than ten years of research and development experience in the TEE field, and there are countless top papers. We have published the first peer-reviewed ARM TrustZone TEE-based paper in China, the first peer-reviewed Intel SGX TEE-based paper.
At the same time, we also have a wealth of experience and accumulation in the commercial landing of TEE, we believe that we can use TEE technology, but also hope to use our unique TEE technology, can solve the current data privacy issues.
Another reason is that considering TEE has a big advantage in performance, versatility and popularity , we judge that it is easier to commercialize.
As mentioned before, we have been designing and developing the TEEX platform since 17 years. At the time, TEE technology was widely used. The fingerprints, irises, faces and other identity authentications that everyone uses in their mobile phones are supported by TEE technology. Not only on mobile platforms, but also in face and fingerprint recognition on personal computers, they are protected by TEE. TEE technology has been tested and demonstrated by a large number of commercial cases, and TEE hardware has also been widely used in user equipment. Therefore, we believe that the privacy computing platform based on TEE technology can be commercialized and landed faster.
Chain Wen Gong: The second question, in which areas do you currently have mature projects?
Trias CTO Wei Ming: The areas we are now landing are mainly in the financial and government requirements for data security .
Specific scenarios, I will give two simple examples:
(1) The first case of our financial securities was to help the securities company's shared document data service . At that time, the biggest feature was that after the ransomware virus, many of the server data protected under the traditional security technology had problems. However, one of the shared documentation services supported by our Trias blockchain was not destroyed by the ransomware.
(2) After the securities company saw the irreversible characteristics of the blockchain on the basis of (1), we made an electronic contract with them . Friends who are concerned about the chain should know something about it and see relevant news. The project we and the securities company did was one of the only four blockchain display projects at the Shanghai and Shenzhen Stock Exchange technical exchange conferences last year.
ARPA Co-founder & CEO Xu Maotong: Thank you, Teacher Wei, ARPA's current landing scenario is similar. The main industries are financial, identity, credit and other data comparison standards, high degree of data, and high data value. Such as data security calculations, sensitive information query, joint data analysis, etc.
At present, ARPA has reached strategic cooperation with more than 20 large domestic and foreign enterprises, completed POC of multiple scenarios and converted into orders, including the world's top 100 enterprises, large trading institutions, financial and insurance institutions, big data marketing agencies and so on. ARPA's current products include multi-party joint risk control, supplier joint KYC, blacklist sharing, security model analysis and other solutions, focusing on vertical areas such as finance and transactions, and enabling data collaboration between enterprises .
Such scenes are also divided into two-party scenes and multi-party scenes. In the two scenarios, we implemented safety analysis of VaR and other risk control models for a top three large financial technology companies. Under the condition of protecting model parameter privacy and financial institution customer position data privacy, we obtained wind control analysis results. Localized deployment.
In the multi-party scenario, we can effectively check whether the newly entered suppliers are on the blacklist of a member institution and protect the privacy of suppliers and members' blacklists in the chain of commodity trading alliances led by a chemical giant. At the same time, we can do joint analysis of indicators such as debt ratio and joint calculation .
I think the multi-party scenario is a big trend in the future, and it is also the place where trusted computing can be combined with the blockchain. As Mr. Yu said, the blockchain is doing data deposit and confirmation, while trusted computing is about extracting the value of multiple data.
TEEX co-founder Yu Wei : TEEX's landing scene has two main aspects:
First of all, To Chain , we have deep cooperation with top public chain projects such as Conflux, Zilliqa and Ontology. Among them, we have reached a strategic cooperation agreement with Conflux, TEEX will help open the data under the chain, and provide trusted external data for Conflux and Zilliqa's chain contracts.
In addition, as a Layer-2 solution, we can provide privacy contract support for existing public chains . Currently we have created a privacy intelligence contract for Ontology based on the TEEX platform.
In the case of to B , TEEX provides a distributed privacy computing platform that can help open data from different data sources . We have provided TEE technical support for data security products of some traditional cloud vendors. These data security products have begun to serve some big data owners including operators and public security agencies to ensure privacy and help them. Data Fusion.
At the same time, we can also create a privacy protection and data security protection system for the enterprise . For example, an artificial intelligence unicorn enterprise has a large amount of user privacy data inside. Based on our TEEX platform, we have created an internal data security training platform that enables efficient data model training while maintaining data privacy. In addition, TEEX also has mature landing plans and experience in trusted data collection, security, medical data sharing, and financial data protection.
/ Second link: The chain has to ask questions /
Adelaide: At present, regardless of the safe multi-party computing (MPC) or Trusted Execution Environment (TEE) track, there are certain technical problems that limit its large-scale application (such as MPC calculation efficiency is too slow; TEE side channel) Attack), then what kind of countermeasures are commonly used in the industry for these problems. Do you have any unique solutions for your projects?
Trias CTO Wei Ming: Let me first say what I think, not necessarily right. First of all, TEE is already a large-scale application . It is only domestic use and perception is relatively late, because the Chinese government is signed in 2016 for the use of chips related to trusted technology. This technology can be used domestically, but it has been used for a long time in foreign countries, and the scope is very wide, so there is no large-scale application of TEE. The simplest mobile phone that everyone uses now is Qualcomm 845, 855. It is useless to use the castzone. Then every day, the payment, fingerprint recognition, face recognition running program will use this piece.
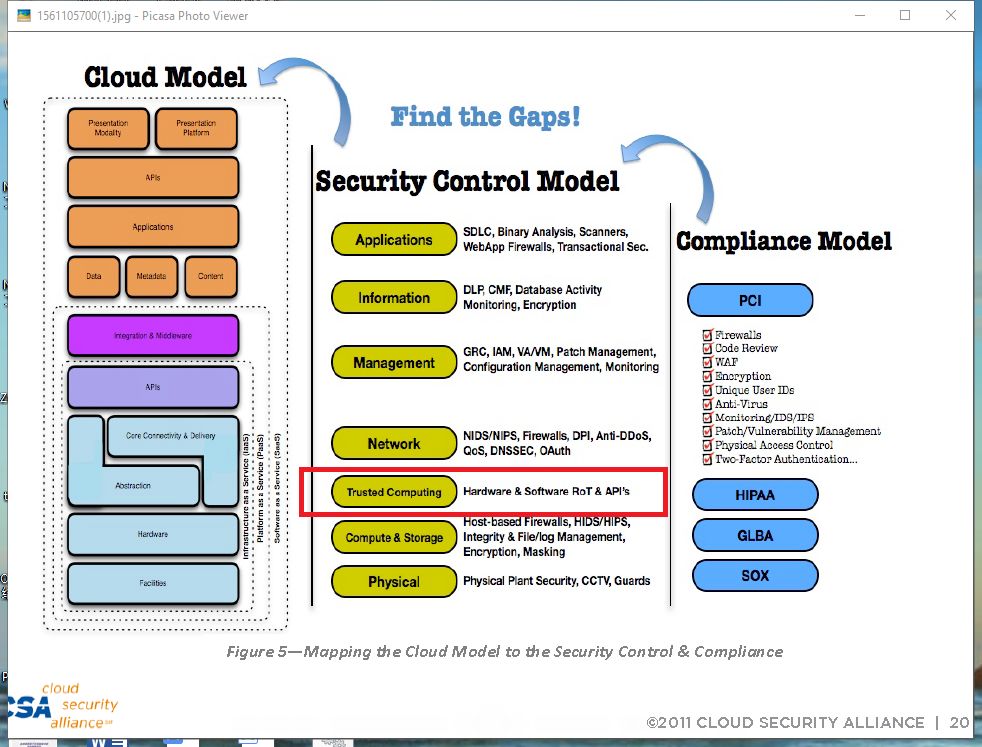
In addition, from the traditional cloud computing environment, the cloud security model started as early as 2012 requires that the highest security underlying hardware must use TEE-compliant computing hardware. Wait a moment, I will find out the security model map of csa-star.
▲ Image source: Guest sharing
You can look at it, this picture may be familiar to everyone. Because the cloud security model in China is actually borrowed directly, the content written inside is slightly modified. In the 11-year version, all cloud service providers must be secure. The bottom layer must have Trusted Computing. At that time, the hardware basically used TPM.
In addition, the current definition of TEE side channel attack may be a bit problematic. It should be mainly intel SGX. TEE is an industry specification.
At present, this kind of hardware-level vulnerability, the unified processing method, the best effect is one, just like the ghost and the fuse problem. Mainly by the hardware manufacturers to patch, or wait for them to produce a new processor to fix this. Otherwise, it is like the fact that Intel's now announced Core 5 generation does not matter whether the ghost is blown. You can only wait for yourself to change the CPU in the future, or wait until you are disgusted. Because this hardware bug is the level-1 hardware layer under the operating system level 0 kernel driver layer.
So this kind of thing is that software vendors update patches in time, and strengthening cooperation with hardware vendors is a good cost-effective solution. However, if someone provides pure soft to solve this problem, I feel very good and can have a big market. Now the old machine of the N cloudy calculation formula is aimed at the ghost, and does not know how to do this kind of hardware BUG. I don’t think the problem is big when I sell it as a product.
ARPA Co-founder & CEO Xu Maotong: Thank you, Teacher Wei for sharing. ARPA is doing a safe multi-party computing MPC. It is a solution based on pure cryptographic algorithm. However, there were indeed many people who wanted to combine TEE and MPC. For example, Dom Williams of DFINITY looked for us last year.
TEE and MPC do have their own advantages and disadvantages. TEE relies on hardware vendors to provide authorization, which is more centralized, but faster, more language-friendly, and more general-purpose algorithms. Therefore, it is more suitable for commercial landing and large-scale application.
MPC is mainly used in small scenarios to process sensitive data for specific algorithms and high security requirements. Since the MPC is completely decentralized, the data secret share on each node is ciphertext, and the entire operation process is not decrypted, so the encrypted calculation of the complement on encrypted data is also called the holy grail of cryptography.
However, MPC has many problems: (1) slow calculation speed, (2) high communication burden, (3) perfect theory but still early engineering, and to D is not friendly enough. Let me explain one by one.
First of all, it is well known that the cost of high security is the decline in efficiency . At present, the speed of MPC is about 100 times that of plain text. In recent years, the computational efficiency of MPC has been greatly improved. The MPC calculation throughput vs. the plaintext calculation has dropped from a slow n orders of magnitude to two orders of magnitude. In our actual operating environment, with a normal computer and a 30 millisecond delay network environment, Different algorithms are about tens to 200 times slower than plain text.
Second, the communication overhead is the main bottleneck affecting the speed of the MPC. Especially with the increase of participants.
For these two issues, ARPA has done a lot of optimization and refactoring:
(1) Since the current MPC cryptographic protocol was still written by scientific researchers, we have basically reconfigured a set of protocols for one year, which has made his efficiency higher and supported more algorithms.
(2) In different scenarios, we will optimize the function when compiling the MPC circuit. For example, some steps require ciphertext calculation, and some steps can be calculated in plain text. This can greatly increase the speed of calculation.
(3) Communication burden, there is no good way at present, but time is our friend, 5G will greatly reduce the threshold of MPC use.
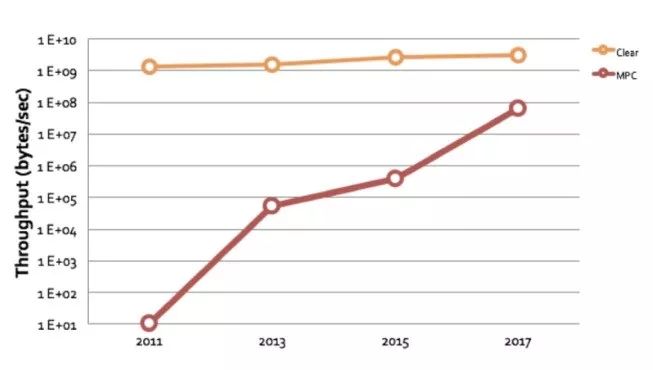
From a longer-term perspective, the MPC calculation unit can be used as dedicated hardware, and we predict that it can increase the speed of MPC by 10 to tens of times!
▲ Image source: Guest sharing
The research progress of MPC is also very rapid, which can be said to be the hottest topic in the field of cryptography. As you can see from the above picture, in just a few years, the calculation speed has increased by 10,000 times, which is why we started all in MPC last year!
I think everything is considered from two aspects, (1) market demand, and (2) technology maturity.
From the perspective of market demand, it is clear that demand is still in its infancy, and individuals and even enterprises have just begun to understand the value of data, mainly promoting large-scale enterprises and governments. Nowadays, everyone is working side by side to set standards. For example, ARPA has deeply participated in the formulation of the “Big Data Security Transfer Standard” of China’s Information and Communication Institute under the Ministry of Industry and Information Technology, and has done a lot of work for the “Secure Multi-party Computing” part. So it's not that the technology is mature enough to land on a large scale soon, and the time is a little earlier.
From the perspective of technology maturity, MPC still takes several years to engineer , but I think it matches the market demand. Everyday peace and harmony are the considerations for us to do this.
I personally see that the trusted computing industry is similar to the AI five years ago. Everyone knows that it will take off. The market is infinite, but the entry points are different. The technical path has its own merits. It is a very benign development trend.
TEEX co-founder Yu Wei: Most of the current TEE technology relies solely on commercial TEE hardware technologies: ARM TrustZone, Intel SGX and AMD SME/SEV. However, TEE that relies solely on the implementation of such hardware features has certain problems. We roughly fall into three categories:
(1) relying on specific hardware and corresponding platforms;
(2) Technical limitations of the hardware characteristics themselves;
(3) Hardware technology does not consider the traditional side channel, Meltdown, Spectre, L1TF and other new types of attacks.
Let's see one by one:
(1) How to get rid of the dependence on specific platforms due to specific hardware?
There are currently some cross-platform generic TEE solutions in the industry, and the more famous one is Microsoft's OpenEnclave SDK. It requires developers to write applications using a specific SDK and proactively divide the application into trusted and untrusted parts. OpenEnclave compiles the application and protects the trusted part of it in the TEE. Currently OpenEnclave is only able to support Intel SGX.
Unlike OpenEnclave, our self-developed hardware and software collaboration cross-platform generic TEE solution (features a bit long..) – HSTEE, can provide a universal, TEE abstraction that is directly compatible with existing applications. HSTEE can build a trusted execution environment that meets the common POSIX standard based on different TEE hardware technologies (TrustZone, SGX, SME/SEV, etc.), directly protect existing programs, without re-development, and get rid of the existing TEE's dependence on specific hardware. .
(2) How to break through the functional limitations of the hardware features themselves?
At present, both ARM TrustZone and Intel SGX have their own functional limitations. TrustZone lacks the resilience to physical attacks, while SGX cannot safely use external devices. At present, there is still no very good way for the industry to solve the functional limitations of these hardware technologies. TEEX's underlying security technology can make up for the lack of security features of these existing TEE hardware.
ARM TrustZone does not currently support memory encryption, which makes TrustZone-based TEEs resistant to physical attacks. For this problem, we use the cache execution technique to limit the TEE memory plaintext to appear only in the CPU cache and to implement runtime memory encryption. This provides the same level of TEE memory encryption as Intel SGX, effectively defending against physical attacks against TrustZone.
The Intel SGX feature limitation is currently mainly due to the inability to securely use any external device, especially since the GPU cannot be safely used, making SGX-based trusted model training difficult. In order to solve this problem, our HSTEE directly builds TEE for trusted computing within the GPU through software and hardware collaboration technology. In other words, our TEE solution can support GPUs, which is also an urgent need for data security technology in the AI field.
(3) How to resist side channels and various new types of attacks?
At present, the commercial TEE hardware technology does not consider the defense of the contralateral channel attack. In recent years, there have also been some new attack methods combining hardware vulnerabilities and side channel transmission, such as Meltdown, Spectre, L1TF, Zombie, and the like.
The existing feasible side channel attacks are mainly cache side channel attacks. The main solution in the industry is to modify the algorithm of the protected program itself. It can be understood that such a scheme requires ordinary programmers to develop programs that resist side channel attacks, which is undoubtedly an overly demanding requirement.
For side channel attacks, our HSTEE uses system-level side channel blocking technology to fundamentally eliminate the construction of side channels. The traditional scheme requires that "the program does not have information that may be leaked when viewed by the side channel", while HSTEE solves the side channel attack from the source, directly blocking the side channel of the TEE, and does not require additional modification of the program by the user.
In view of the new attack methods that combine hardware vulnerabilities and side channel transmission in recent years, the current mainstream practice in the industry relies on hardware vendors' vulnerability patches. This approach does have an effective defense against attacks that have already been discovered. But it is difficult to defend against the same types of attacks that may exist in the future.
Our main idea is to "prevent problems before they happen." By analyzing the existing attacks, we find that they mainly use the existing hardware TEE isolation in the case of out-of-order/guess execution, and combine the traditional cache side channels to attack. Therefore, HSTEE uses the above-mentioned side channel blocking technology to block the information transmission channel of the new attack mode. On the other hand, through the hardware and software co-design, the isolation of the existing TEE is further enhanced. Even in the out-of-order/guess execution mode, the attacker's instructions cannot access the data of the target TEE.
/ Third link: Question /
Sun Wei, Mars Finance: After listening to the discussions of the three teachers, we next focused on the actual implementation of privacy security computing. There are three questions:
1. Do you think that comprehensive consideration of various factors will predict how long before the privacy and security calculations will be promoted on the B side?
2. In addition to technological developments, what other factors hinder the spread of privacy and security computing in this process?
3. Will this technology lead to new business forms beyond the inter-enterprise privacy and security calculations? Will it eventually go to the C side?
Trias CTO Wei Ming: (1) In fact, privacy security computing has been promoted on the B side , but the technology used is constantly iterative and upgraded, and the scope is also wider. Just like the tools that most people used in the enterprise before, such as DLP. But the biggest problem, I think, is still like the business needs of the two big coffees. If you just say face recognition and payment, it is now a large-scale promotion. But to say anything else, it depends on the specific needs.
(2) I think the biggest is the management and industry interest groups . Let's take a real example of what we have encountered. A company has engaged in the blockchain project of the securities, and we went to the SSE expert group for acceptance. Then the company is fully adopting the SGX. Everyone knows that SGX has a feature. That is, you have to be authorized by Intel. Although you can also deploy it privately, you still need Intel.
As a result, this project was miserable, and the industry will not be promoted again because the authorization can only be issued or deepened. Not allowed to do Intel.
(3) Yes, for example, Trias hopes to implement economic models based on TEE . Will definitely go to the C side, otherwise everyone does not want to use TEE, right?
ARPA Co-founder & CEO Xu Maotong: 1. Do you think that considering the various factors, how long does it take for privacy and security computing to be promoted on the B side? 2. In addition to technological developments, what other factors hinder the spread of privacy and security computing in this process?
I expect privacy computing to be on a large scale in the enterprise to be 2-5 years, and the landing of personal data should be 5 years or more. In fact, we just said that market demand is in its infancy. Although we have seen many scenarios, we may not be a P0 task, but more like a medium-term exploration direction. The reason is that companies' knowledge of the value of data has only begun for a few years. For example, if we invest in the past, the best project is to provide corporate or personal applications, free of charge, data needs to be given to him, and then the data can be used to model or realize.
Data mediation, whether it is systems, tool providers, big data and AI companies, is now facing the dilemma of corporate customers not giving data.
Data fusion is to better serve the business, so enterprises need the support of external data. Contradictions have arisen. On the one hand, many financial government agencies' data is "only inaccessible", and on the other hand, they need to work together. The need for trusted computing comes along.
But I think the demand still needs at least 2 years to ferment, the pain point is enough pain, for example, you can't do a certain business without trusted calculation. At present, most trusted computing can do, data mediation can do, it takes time to replace them.
2. In addition to technological developments, what other factors hinder the spread of privacy and security computing in this process?
Data security exchange is actually the ultimate problem in the data field, and technology is only a small aspect. Other factors include the safety of the manufacturer that Wei just said, and we will also be questioned about the security of the MPC algorithm. In addition, who is the right to data? Whether it is a company or a person, not seeing does not mean that it can be realized, how to ensure the authenticity of the data to prevent garbage in garbage out, is a problem.
Mars Finance Sun Wei: So the current pain point is not enough to support him to replace the existing computing business? After all, the cost of capital, manpower, and learning costs for replacing a computing system are enormous.
ARPA co-founder & CEO Xu Maotong: Yes, even a pure software solution like MPC is costly because it involves the synergy between two or more enterprises and the same problem as the blockchain. .
3. Will this technology lead to new business forms beyond the inter-enterprise privacy and security calculations? Will it eventually go to the C side?
Certainly, let me give a few examples. To C, from a personal point of view, if I can secure my website, get more accurate advertising, enjoy better financial products, and get real material returns, then if you can ensure safety, then you can get real material returns. Will be willing to contribute their own data, the result is the network effect of the data, the real potential of liberating the data. And solve the problem of attribution of data rights.
The long-term vision of ARPA is that personal data can be securely hosted on certain nodes, and enterprises in need can call for payment to realize the secure management of personal data assets.
Another important use of MPC is the key management KMS. MPC-based threshold signature technology is currently available for demos, and has begun to be discussed with some hosting organizations, exchange design products, and our team and CZ and CTO.
At present, the limited use of wallets on a large scale is that private keys are difficult to keep , and I am too lazy to support the words. The threshold signature can realize that the key is distributed at the beginning of the generation. Each time the verification is done, the mpc specific function calculation is performed, and all participants are not required to participate. For example, 2/3 can be decrypted, then I will save it on the exchange, one in my hand, one in the custodian, and my own part will be lost. Significantly reduce the threshold for use.
TEEX co-founder Yu Wei: Ok. Just Wei’s tutor is very good. We are also very touched in this regard. There is a very important issue that is trust. Large enterprises will say that I trust your algorithm and trust Intel hardware. We have to do it. Many times, we should start from their real reasons and try our best to dispel some of their concerns. For example, we will provide them with a complete set of software and hardware integrated products based on domestic CPU and independent controllable. Large-scale promotion still requires a lot of effort and a long way to go.
In fact, TEE technology has been born more than ten years ago and has been developing rapidly, and has been widely promoted on the mobile side. However, unlike the mobile terminal scenario, the B-end often needs to operate on a large amount of data from multiple parties, which has great challenges in terms of security, performance, and versatility.
Fortunately, however, TEE technology is now mature . Compared with other privacy computing solutions, the comprehensive ability of TEE technology in these aspects is the closest to the practical scenario, and the implementation of privacy protection policy and the huge prospects of the privacy computing market are also inspiring. The more people are involved.
I don't think there is a so-called technical ceiling for the promotion of TEE technology at the current stage. More considerations are the exploration of commercial scenes and the advancement and optimization of engineering . I believe it will not take long, maybe within a year or two, based on TEE's privacy computing technology will have a scale-of-use application on the B side.
Will this technology lead to new business forms beyond the inter-enterprise privacy and security calculations?
In addition to technical factors, I think the important aspect is the public's recognition of privacy and security computing technology . Because technology is in the hands of a few people, we are now trying to use this "minority understanding" technology to incite the whole society. The trust system, this must be difficult.
History has repeatedly proved that the birth of a revolutionary technology can not be achieved overnight. Just as many people could not understand the Internet at first, but the Internet has developed step by step, and most people still cannot understand today. The principle, but it has indeed subverted our way of life.
And we are also working hard to popularize privacy computing in a variety of ways, including a variety of popular science-oriented science, and we will release some public offensive and defensive rewards in the future to prove to the public the level of security we can achieve through TEE technology, and to enhance the public. Trust in TEE technology.
In addition, many companies in the implementation phase are not willing to put all the security on a certain hardware manufacturer, as mentioned before. Therefore, we have built a TEE solution that is compatible with all platforms, providing a common system environment for upper-layer applications, in order to eliminate the concerns of enterprises on hardware vendors.
Will it eventually go to the C side?
That must be yes. As mentioned earlier, TEE technology has actually been widely used in mobile C-side, such as secure payment, secure storage, identity verification, trusted communication, and so on. When the TEE technology matures into the general computing scenario, there will be a greater market prospect, and it will undoubtedly be popularized on the C side.
For example, the privacy protection of individual users has become a social problem that needs to be solved urgently. While users enjoy some services, they will inevitably expose some personal data or even sensitive data, which may even affect normal life.
A common view now is that personal data should be owned by individuals and the value generated should belong to the owner. No third party should have personal data. Privacy security computing technology can solve this problem well. We can allow users to verify that third-party services do provide services in a private computing manner, so users have reason to believe that their data can be safely processed and destroyed, and will not be compromised in any way.
We can even provide users with a complete set of personal data management services, build their own data stations and a small black box to securely process data. With these, how to realize data value is another more grand business story. It is.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Bitcoin prices have broken through 10,000, according to the ratio model analysis will rise to 60,000 US dollars in 2020
- How to successfully reach the hot spot of libra and create an atmosphere that I know very well
- Morning comment: The outbreak continues to BTC rises over 10,000 US dollars to lead the mainstream currency
- Bitcoin stood on 10,000 US dollars, gold, crude oil rose, the dollar fell
- Bitcoin broke through $10,000 again after more than a year, and halving will probably continue to rise.
- Wallet TokenStore thunder, how to identify the funds to avoid risk?
- BTC monthly report 丨 BTC has the highest volatility relative to other assets, and derivative trading activity continues to increase