Lightning Loan: New DeFi Project Gameplay, How to Attack MakerDao for $ 700 Million
Source | medium.com
Author | Dominik Harz
Compilation | First Class-Mark
Without delay in introducing a new governance contract, you risk stealing all of Maker's collateral ($ 700 million) and using Lightning Loans to issue any number of Dais.
- Rational understanding and perceptual practice of blockchain: How to correctly understand blockchain and choose the correct technological development route?
- The court acquiesced that Gram tokens are securities? Telegram's fight against regulation is coming to an end
- Benefits escalate again! Babbitt Industry Orientation Starts Knowledge Officer Program
Anyone can perform the attack, paying only transaction fees (a few dollars) without having to hold any MKR.
· If Maker does not introduce a delay before the liquidity pool of the Lightning Loan Pool exceeds the threshold, there is little chance to stop the attack (race condition).
· Maker knew the attack and held a vote on February 21 to prevent the attack.
Introduction
Maker and its Dai stablecoin are the most popular decentralized financial (DeFi) project on Ethereum, with smart contracts locked at about $ 700 million. The Maker protocol relies on governance processes encoded in smart contracts. MKR token holders can vote to replace existing governance contracts, and voting is proportional to MKR's holdings. The total number of MKR tokens is approximately 987530, where the selected wallet or contract holds a large number of tokens:
· [Maker governance contract: 192910 MKR] · Maker Foundation: 117993 MKR · a16z: 60,000 MKR · 0xfc7e22c6afa3ebb723bdde26d6ab3783aab9726b: 51291 MKR · 0x000be27f560fef0253cac4da8411611184356549: 39645 MKR
Note: The Maker governance contract contains multiple parties' MKR tokens.
Governance attack
In December 2019, Micah Zoltu pointed out how to attack governance contracts. The basic idea is to accumulate enough MKR tokens to replace the existing governance contract with an attacker's malicious governance contract. In this way, the malicious governance contract can give the attacker complete control of the system and withdraw the system and any collateral in Dai.
To reduce the number of MKR tokens required, he suggested performing an attack when voting on new governance contracts. Currently, 192,910 MKR tokens have been locked in the governance contract. However, if two or three contracts are voted in parallel with similar token distribution, the attacker will need fewer tokens.
As shown below, this situation used to happen:
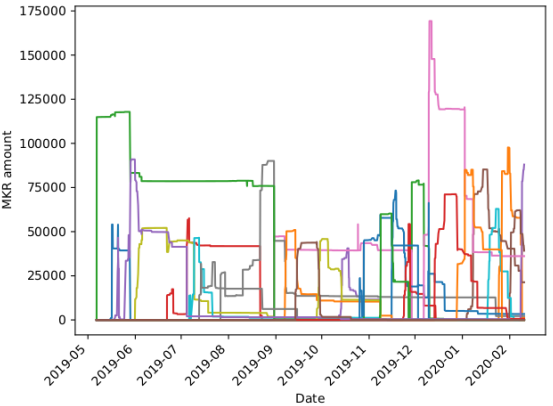 The obvious attack strategy is to crowdfund the required MKR tokens through smart contracts and pay a certain share of bonus to each attacker. However, an attacker may need to accumulate about 50,000 MKR tokens to have the opportunity to attack the system without Maker's attention to these actions.
The obvious attack strategy is to crowdfund the required MKR tokens through smart contracts and pay a certain share of bonus to each attacker. However, an attacker may need to accumulate about 50,000 MKR tokens to have the opportunity to attack the system without Maker's attention to these actions.
New attack strategy: Lightning loan
However, if we consider using Lightning Loan, the requirement for a large number of MKR tokens can be completely eliminated. Lightning loan is a fairly new concept, so it is briefly explained here. Generally, lenders must provide collateral to obtain a loan in a DeFi project. For example, in Maker, A can borrow Dai by depositing ETH. This is required, and it operates under a model of weak identity and economically reasonable agents.
Lightning loan canceled this requirement because it only happened in a single transaction:
1.A draws a loan from a Lightning Loan liquidity provider (such as Aave or dYdX).
2.A performs some actions (for example, carry trades on Uniswap, Fulcrum, Kyber, etc.).
A repaid the lightning bolt of interest.
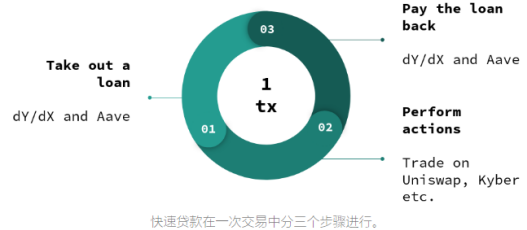
The reason why Lightning Loan works is because of the way the Ethereum virtual machine is designed:
Manipulating arbitrage with Lightning Loan and Oracle
On February 14 and February 18, two incidents involving lightning loans occurred, causing bZx to stop the platform. In the first transaction, a single Lightning Loan would earn a profit of 1,193 ETH (about $ 298,250). The transaction was executed using a smart contract that opened a short position in Fulcrum on wBTC. In the same transaction, this transaction lent a wBTC loan from Compound, and conducted a wBTC transaction on Kyber's Uniswap reserve, resulting in a slippage that eventually reduced the price of Fulcrum, which can be found in bZx's post hoc evaluation Full details.
(First-class warehouse note: Fulcrum is a product that provides a simple and effective method of loan and margin trading, and claims to be the first and only margin platform that requires no trust at all, free of authorization, free of charge, and no account creation.)
Similarly, the second event took place on February 18 and made a profit of 2378 ETH (about $ 600,000) in a single transaction. The transaction involved an initial borrowing of 7,500 ETH to buy a long position on Synthetix's sUSD.
Oracle Manipulation to Reduce Required Liquidity
For the attack, assuming 50k MKR is sufficient. Even in practice, the number of tokens may be even more, how the concept of Lightning Loans makes Maker's security difficult to guarantee without causing delays in governance. In a naive approach, an attacker could borrow a small loan to buy 50,000 MKR tokens.
At the current exchange rate, the attacker needs about 485,000 ETH to purchase this amount of MKR, and only one exchange Kyber has enough available capacity. However, attackers can also use multiple exchanges to purchase 38k MKR from Kyber, 11.5k MK from Uniswap, and 500 MKR from Switcheo, for a total of 378,940 ETH. This number is still high, but has been reduced by almost 100,000 ETH!
Attackers can use the above Oracle operation strategy to effectively reduce the price of MKR on Kyber and Uniswap. These are the two largest providers of MKR, and have been shown to be susceptible to oracle price manipulation, and further analysis is needed to determine how much MKR prices can be reduced. However, on less liquid tokens like wBTC, attackers are able to manipulate price fluctuations by about 285%.
Get enough liquidity
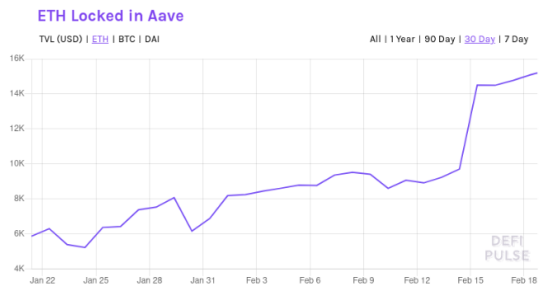
Even with oracle operations, a large amount of ETH is required to perform an attack on Maker. Attackers can increase their liquidity by withdrawing two lightning loans in the same transaction. Aave and dYdX protect themselves from re-entry and allow only one lightning loan in a single transaction, but attackers can borrow ETH from both protocols in the same transaction.
Combination plan
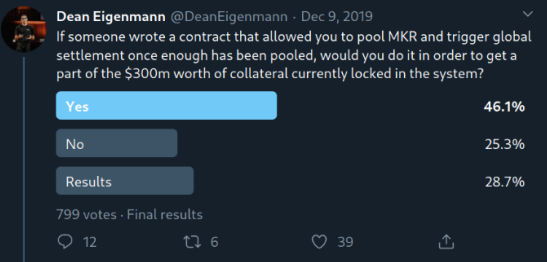
Obviously, crowdfunding and lightning loans can be combined. With about 107k ETH of available liquidity, it is possible to get about 10800 MKR from Kyber. As a result, multiple attackers can reduce the total required number of 50k MKR to approximately 39.2k MKR. As the informal Twitter survey revealed, it seems that some people are indeed interested in this attack:
It should also be noted that the top four account holders (actually five, irrespective of the current Maker governance contract) are able to perform attacks without crowdfunding.
Best time to attack
Once sufficient liquidity can be obtained through the Lightning Loan Pool (a combination of operations with or without Oracle), anyone can take over the Maker governance contract. When the liquidity pool reaches this threshold, once the Maker starts voting, the Maker needs to ensure that MKR tokens are distributed as little as possible. If distribution of MKR at any time during this voting process could exploit this vulnerability, any collateral could be taken away.
Attackers will be able to steal $ 700 million worth of ETH collateral and be able to create new Dais at will. Since Dai is used as a supporting collateral for other protocols, this attack will spread throughout the DeFi project. In addition, the attacker could use his Dai to trade other currencies worth about $ 230 million.
Countermeasure
Maker should revise the new governance contract to prevent Lightning Loan from attacking its systems. Specifically, the Maker Foundation should be able to check for malicious code in new governance contracts and allow enough time to respond. At a minimum, new governance contracts should not be effective in a single transaction. In this way, the attacker may not be able to profit from the attack and thus be unable to repay the Lightning Loan.
If the attacker fails to repay the Lightning Loan, the attack will never happen.
Maker will vote on such contracts on February 21, 2020. The proposed contract will activate the Governance Security Module and prevent such lightning loan attacks.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- The plunge was caused by Binance shorting after losing coins? Let the data on the chain tell you the truth
- Data: Bitcoin investment traffic is expected to exceed Visa after next halving
- Lawyer's interpretation | Blockchain's application in supply chain finance faces three major legal risks
- In the era of "Black Swans", learn to use blockchain thinking to improve anti-fragility
- SERO destroys half of the unmined tokens, and the public chain also changes the total amount like the exchange?
- Israeli Attorney General: Israeli banks should not refuse to serve cryptocurrency companies
- Large-scale technology companies collectively enter the financial sector, EU securities regulators issue risk warnings





