The finale of the American drama "Silicon Valley": a crisis caused by a blockchain expansion
Author: Hu Peng,
Source: A Plus Community
This article tells the author's thoughts on the development of cutting-edge technologies such as blockchain and AI after watching the American drama Silicon Valley.
The American drama "Silicon Valley" finally ushered in the finale. After watching it, I sighed endlessly. Like all great comedy works, there is a complex and profound tragedy core.
- Reuters: Netherlands' largest bank to enter digital asset custody industry
- Medical data of 40 million members will be protected, Anthem, the second largest health insurance giant in the United States, uses blockchain like this
- Zhu Jiaming's latest sharing: Understanding the evolution of blockchain paradigms from a futuristic perspective
Just when I thought that Pied Piper's entrepreneurial story was just like "Silicon Valley" in 1999. The founders are now wealthy and free, but the screenwriter reversed strongly in the last episode and proposed a more ambitious philosophical proposition— —If human society is not ready for a technology, what should you do as its creator?
Plot review
A company with a valuation of nearly $ 8 billion returned to zero overnight. How did all this happen?
Why PiperNet, which provides users with data control, threatens the peace of the world, and why does the core team give up its billions of stature and reputation and ruin its own company?
If you want to understand the finale (S6E7), you may need to review the key moments that the Piper has experienced since the first season.
01
Divergent compression algorithm (Middle-Out Algorithm)
The origin of the entire series is that Richard, a programmer who is not satisfied with working at the big company Hooli, found a few friends in his spare time, founded a company called Magic Flute Player, and developed a Music copyright retrieval application, but failed to impress investors.
Inadvertently, the compression algorithm he invented for this application is several times better than the best algorithm in the industry-in fact, a fictitious index in the play to measure the compression ability, Weissman score, Richard Germany's algorithm brought him close to the theoretical limit (2.9) to 2.89 points.
This algorithm has won the favor of the old owner Hu Li and angel investor Peter Gregory. Richard chose to accept the angel investment money, quit his job at a large company, and began an ambitious entrepreneurial journey.
In the end of the first season, the magical pipe player's algorithm engine was reverse engineered by Foxit, which created products with the same performance but richer functions (in recent years, the Internet has also exploded similar giant plagiarism incidents).
Under tremendous pressure, Richard came up with a new algorithm, Middle-Out (although the idea source is very yellow and tainted), and broke through the previous theoretical limit. The magic flute player immediately became a popular fried chicken in Silicon Valley.
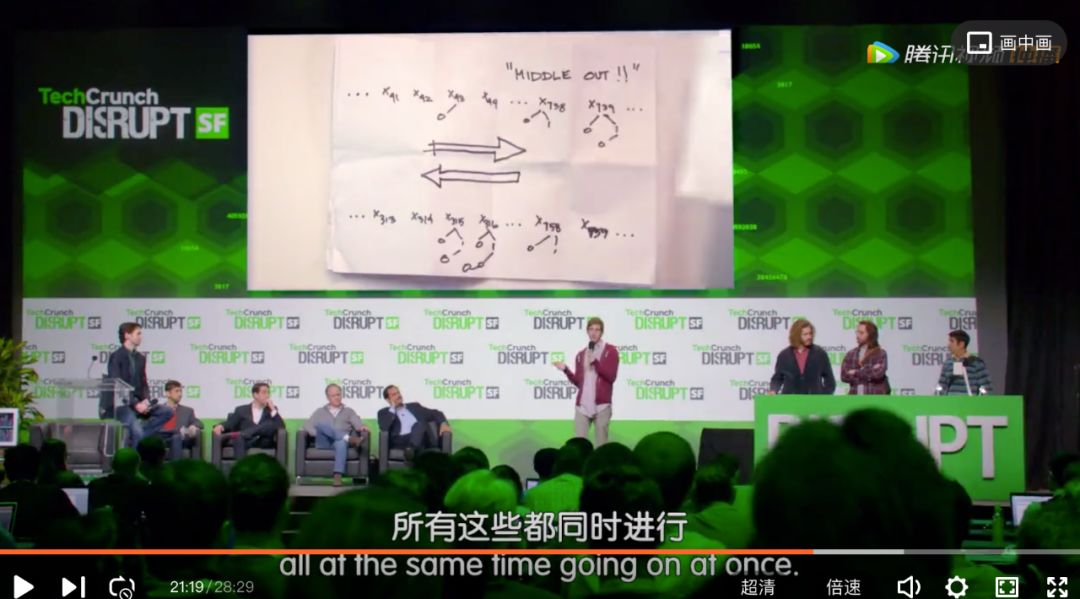
Richard demonstrates revolutionary divergence algorithm at TechCrunch startup competition
02
Decentralized internet
After experiencing several transformation failures, Richard realized that what he really wanted to do was a new Internet-using billions of mobile phones with excess performance as nodes to build a decentralized, point-to-point, and anti-regulatory Internet.
It was found in the survey that Peter had a similar idea earlier, to build an Internet that is not controlled by the giants, an "Internet that we deserve", but the theoretical limit of the compression algorithm at that time could not be achieved, and Richard The divergence algorithm invented by Germany just cleared this obstacle. 
Peter's Early Exploration of Decentralized Internet
After the first generation network was developed by the magic pipe player, they persuaded an insurance company FGI to purchase their own decentralized storage network service. Before they can find enough mobile phone users, they have to store data on the Azue cloud, and the cost is high.
Ghost (Gilfoyle), when cracking the smart refrigerator, implanted the Magic Piper Warehouse code into the firmware. These codes upgraded 30,000 refrigerators along the network to form a decentralized storage network and backup. With FGI data, the company is back to life.
When the fourth quarter was launched in 2017.4, a round of cryptocurrency was brewing. In the second half of this year, Bitcoin reached a historical peak of nearly 20,000 US dollars. More and more people began to pay attention to cryptocurrency and blockchain. The Internet form conceived this season coincides with the decentralized Internet concept advocated by the blockchain.
In the fifth quarter, in order to solve the financial crisis, even the first token sale was made-the issue of PiedPiperCoin. As a practitioner in this industry, I have to be refreshed by the keen sense of screenwriting and bold practice. This is no coincidence. The show did invite many founders in the blockchain field to act as consultants, including MaidSafe, Blockstack, etc.
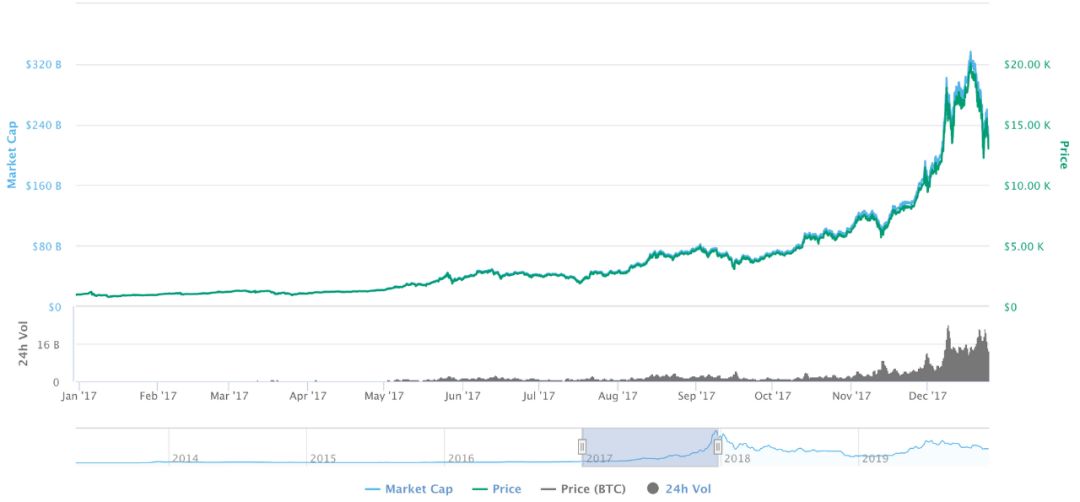
Bitcoin price trends in 2017
03
Son of Anton
Anton, derived from G's "nickname" for the server cluster he maintains, the word itself comes from Satan worship. In the fourth quarter, Anton was unfortunately physically damaged and sacrificed. In the sixth season, G God developed a deep learning network and named it the son of Anton.
At first, this network was just an AI chatbot, and G God used it to deal with the daily encounters of Dionych. But this AI has the ability to learn by itself. Set tasks for it, and the network will evolve by itself.
G God even asked it to help fix the bugs in the code-the son of Anton made the decision to delete many code repositories. Maybe it thinks that the best way to fix the bug is to delete the buggy code.
Gathering the three main levels above, the plot came to one of the biggest technical challenges before PiperNet went online-network expansion, and created a monster that the creators could not understand.
Blockchain expansion triggers major crisis
Magic Piper won the big customer AT & T in the seventh season, and PiperNet is expected to run on hundreds of millions of devices. Before that, they need to make a pilot release, and set up a test network at the Rose Festival site in the desert for evaluation.
Unfortunately, with the increase in attendees, transactions on the network began to block, and the divergence algorithm did not achieve the expected results to improve network throughput, and tourists could not send messages, pay, or even go to smart toilets. 
This may be the difference between the white paper and the product release hhhhhhh
Expansion has always been the biggest bottleneck since the birth of the blockchain. Bitcoin's security has stood the test of ten years, but 3 to 7 transaction tps per second has limited it as a means of payment. In traditional software architecture, the performance of services can be improved through vertical / horizontal expansion. In order to ensure decentralization in the blockchain network, the threshold for running full nodes must not be too high.
How to increase the transaction volume that the entire network can handle without increasing the computing resources of a single node has become a huge challenge in the field of blockchain.
Richard, as always, has exerted his creativity under extreme pressure. He transformed the son of Anton with a divergent algorithm and created a new AI robot to optimize the blockchain network.
This bold idea successfully increased the capacity of the network and also allowed them to defeat rival Yao Network, which has a valuation of $ 8 billion.
The story ends here with a happy ending, but obviously the screenwriter wants more. So, something unexpected happened.
A few days before the official product delivery, Richard discovered that the encrypted message he had sent was missing a point from the text messages Morika accepted.
After querying the network log, it was found that the amount of data sent by the network was inconsistent with the amount of data received. All data is encrypted and cannot be compressed anymore (based on the infeasibleness of encrypt-then-compress).
Then the only possibility is that the network's encryption is bypassed or broken! 
God G: "It's a feature, not a bug"
G God then confirmed that in order to improve the efficiency of the network, the AI in the network developed an algorithm to calculate the discrete logarithm problem in polynomial time, and broke the elliptic curve including P256, Curve25519 and so on. God G then demonstrated the use of the Internet to crack the Tesla car of Dienich, ordering it to drive to a car wash shop automatically.
what does this mean? I have been dealing with cryptography for most of the past year or two. I know how modern society depends on encryption systems, from transmission networks, financial institutions to nuclear weapons launching passwords. Once these cracking tools flow into the hands of criminals, it will undoubtedly endanger society. peace.
Can this part of the cracking ability be eliminated from the network? No, because AI based on deep learning is like a black box, it is not yet possible to explain how it works effectively.
It is still not practical to solve the problem with AI in the plot, but the development of quantum computer and other technologies has made the development of new cryptographic systems more and more urgent.
Close Pandora's Box
After understanding the situation, the founders of Magic Piper began to face a severe test: on the one hand, after six years of rough business, on the verge of bankruptcy, and finally, they won billions of orders, and the scenery was unlimited; on the other hand, the network was about to be released There is a huge destructive power, and the world is not ready to meet it, and may even go to jail for it. 
Richard's tough test
After weighing, Richard and others decided to close the Pandora's box, and carefully planned a failed product launch in an effort to achieve "open and gorgeous ugliness"-for the following considerations, just closing the network and canceling the operation is not enough of.
PiperNet is already well-known, and someone will imitate and reverse engineer their achievements, so they created the product launch as an unexpected failure, conveying serious technical flaws, interrupting latecomers to copy their ideas.
To be honest, I was moved to see this place. This tragic feeling is no less than Batman in "The Dark Knight" bears all the infamy, just to keep the image of the bright knight Harvey in the hearts of the people of Getan.
The founding team finally reached a consensus
In the end, they "successfully" smashed the press conference, the company was dissolved, related code was cleared, and the founders went their separate ways.
The fiercely defeated Magic Piper is even better known than pets.com (the failed company during the dotcom bubble of the 1990s), Theranos (blood testing company scam), and wework (a shared office industry giant. This year, it was caught in a financial scandal and its valuation dived ) Even more failed tech companies.
Gates ’surprise cameo, no sense of disobedience, hahaha
A friend and I put forward a point of view during the discussion: "This should not be a technology, a possible choice of a team of scientists … this is a relatively obvious plot loophole." Indeed, if things really come to this stage, especially in the blockchain field, it is difficult to cover up or even erase these traces.
As a fictional drama, there are many logical loopholes in the plot of "Silicon Valley", but the problems it raises are real and represent people's concerns about the increasingly black-box technology.
Difficult entrepreneurship
The magic flute player has been in business for six years, and it has been full of hardships. The company has undergone several transformations, from music copyright applications to cloud storage services, from video chat software to decentralized Internet; every season, CEO Richard goes to the doctor to check the body and talk about his troubles, which truly reflects Entrepreneurs face tremendous physical and mental stress.
"Silicon Valley" started broadcasting in 14 years. At that time, I was still a computer professional apprentice. From MIPS processor to C language compiler, I stayed up late to program for each class. The magic flute player has been in business for six years. It is a stage of rapid development of China's Internet. From mobile Internet to artificial intelligence, to the ever-growing blockchain, attracting a number of young people to join the wave.
I was fortunate to have been involved in the entrepreneurial process since I was a student, and participated in a breakthrough from a dozen people's small workshops to billions of dollars in financing. After graduation, I also made "screws" for O2O giants with tens of thousands of employees. , In the nascent blockchain industry, explore interesting things.
Although "Silicon Valley" happened on the other side of the ocean, in the same fast-paced, high-density information flow industry, Chinese Internet practitioners can easily feel the same, whether it is achievement or frustration. Compared to the Chinese in the 1990s-who may not understand "Silicon Valley Legend", several college dropouts started from the garage and built legends like Apple and Microsoft Empire-we are happy.
Appendix: Technology Popularization
This section is aimed at some readers who are interested in technology, to verify the rationality of the technical settings involved in the play.
01
Weissman score
The Weissman Score is a fictitious measure of lossless compression. It is defined by the technical consultant of Silicon Valley and Professor Weissman of Stanford University.
It mainly combines two indicators: compression ratio (r) and compression time (time, T). The underlined are standard compressors. In simple terms, the higher the compression ratio, the shorter the compression time, The higher the Siman score.
The basic principle of data compression is to use the statistical redundancy of the data. An inaccurate but intuitive example is that "aaaab" can be represented by "4ab".
Lossless means that the integrity of the information is not compromised after compression, and includes two basic steps:
1. Statistical model for generating statistical data;
2. Use statistical models to represent high-frequency characters with shorter bit sequences and low-frequency characters with longer bit sequences. The most classic coding algorithm is probably Huffman coding.
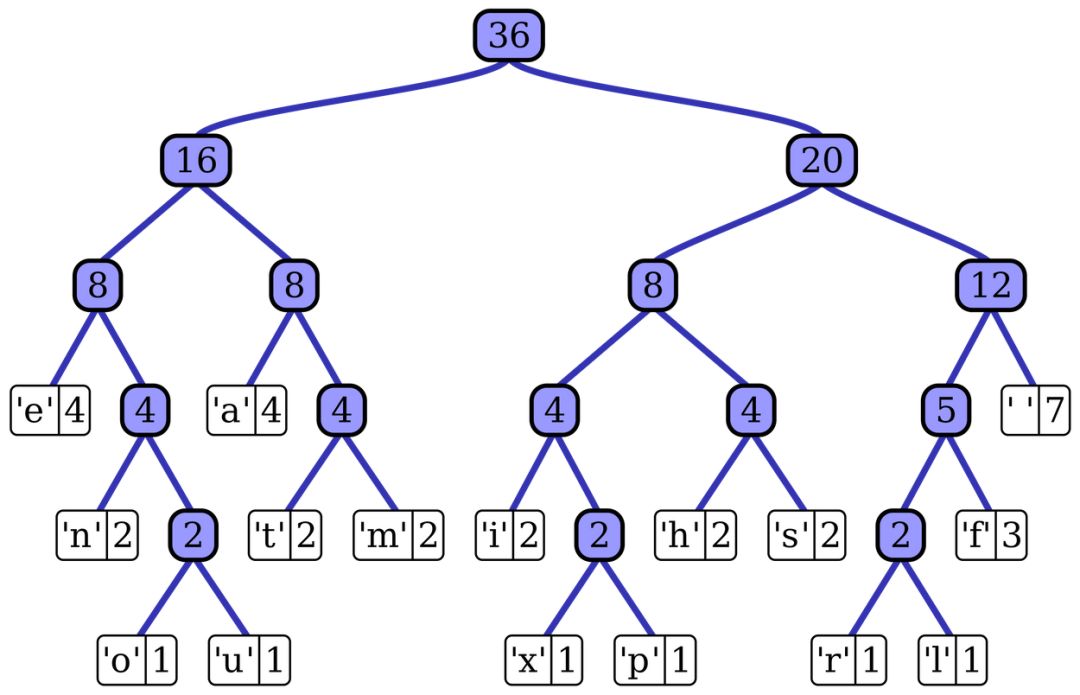
Huffman tree
It is difficult to say which compression algorithm is the best-scholars or the underlying theory of compression, engineers are more concerned about the overall performance of compression. Sometimes algorithms with higher compression ratios take longer to run, which can also affect industrial applications. Although the Wissman scoring is fictional in the play, it takes both the compression ratio and the time into consideration, so it has begun to be taken seriously by industry and academia in reality, even in Stanford and UC classes. There is it. 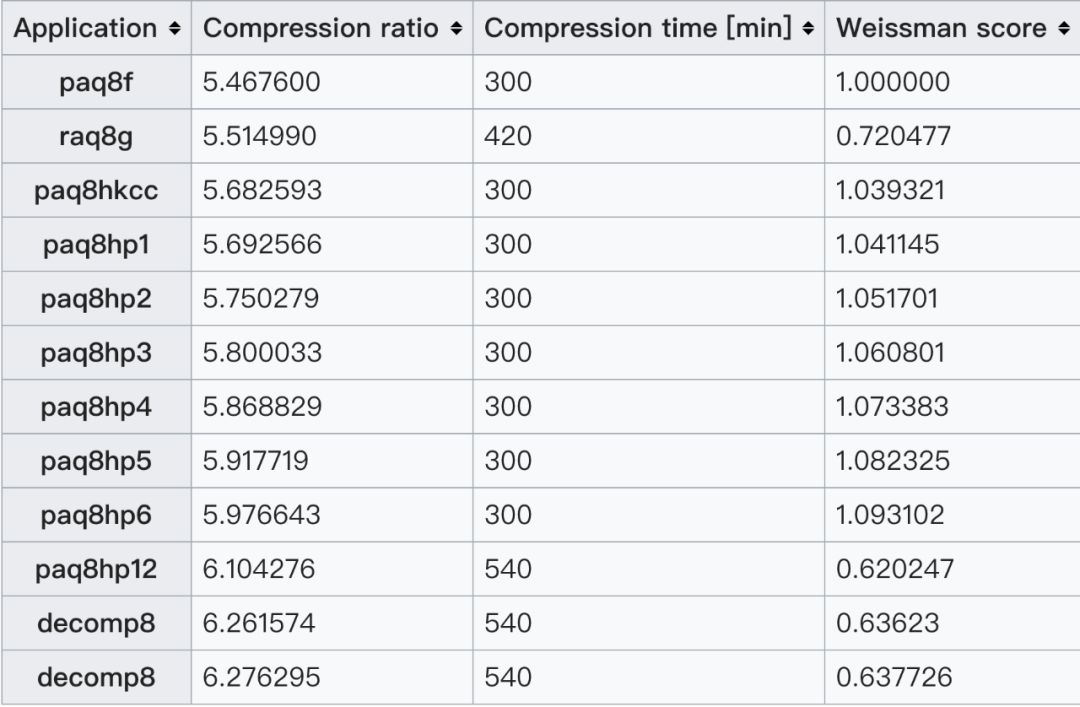
Weissman score of partial compression algorithm
02
Discrete logarithm problem
The play claimed that the son of AI Anton found a polynomial time solution to the discrete logarithm problem, and thus cracked a series of cryptographic infrastructure.
For non-computer professional friends, this may be relatively unfamiliar, and there are even some misunderstandings:
1. Solved the discrete logarithm problem, then proved that P = NP;
2. That's true. All cryptographic systems are no longer secure.
Here are some instructions:
First of all, the discrete logarithm problem is now considered difficult-under the classic Turing machine model, no algorithm in polynomial time has yet been found-but it is not an NP-complete problem, only the NP-complete problem is found Polynomial solution can prove all P = NP problems;
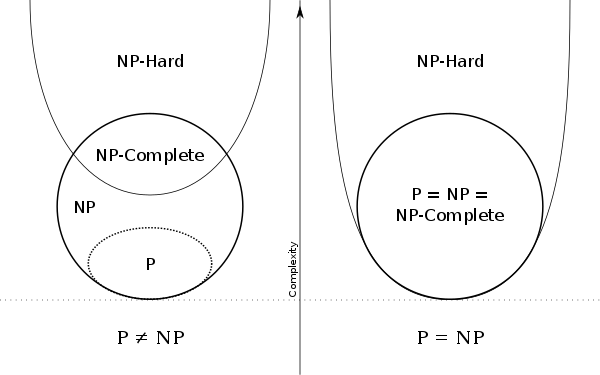
Euler diagrams for P and NP problems
Secondly, the elliptic curve cryptography listed in the play is based on the difficulty of discrete logarithm problems, such as P256 considered by God G to be outdated, and the most secure Curve25519 mentioned by Dinich. These elliptic curve calculations can be converted into A cyclic group over a finite field constructs a discrete logarithm problem. (A famous stalk here is that the parameters of the P256 curve are set by NIST. Cryptography students are worried about the existence of backdoors, so most cryptocurrencies including Bitcoin are not used.)
But there are many cryptographic systems based on completely different security assumptions-large number decomposition problems, hidden subgroup problems, pseudo-random number generators, cryptographic secure hashing, and are not subject to the discrete logarithm problem in the play. Impact of being cracked.
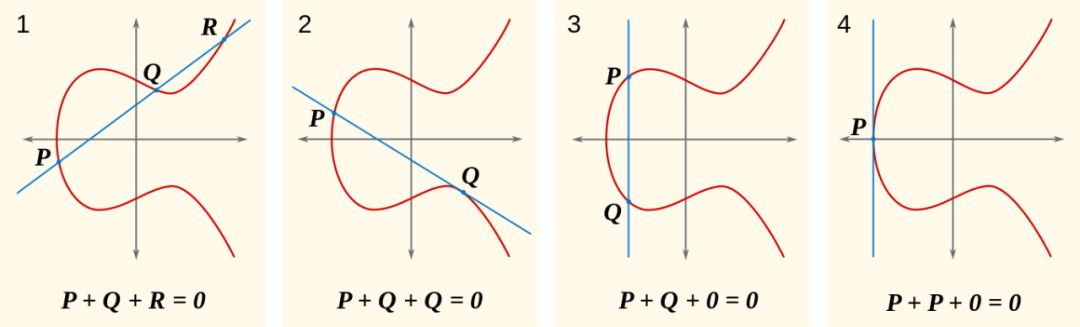
Example diagram showing the computational characteristics of an elliptic curve

Elliptic curve P256 shown on the screen: an outdated standard
03
Son of Anton Super AI
The topic of super AI threatening humans has been discussed a lot in recent years, among them are Musk, Bill Gates and Hawking.
After being given the order to optimize network performance, the son of Anton in "Silicon Valley" continued to evolve towards this goal, including solving the discrete logarithm problem. It is only a way to optimize the network, and no one can guarantee it for this goal. What else will happen.
Similar concepts include the hand-written robots in the famous series of comics by Xi Qiao, BetaCat and Tim Urban's "AI Revolution: The Road to Super Intelligence." They are all about solving a problem, and accidentally developing the ability or behavior that humans consider "unfriendly". Compared with artificial intelligence with emotion, it is more terrible without emotion. 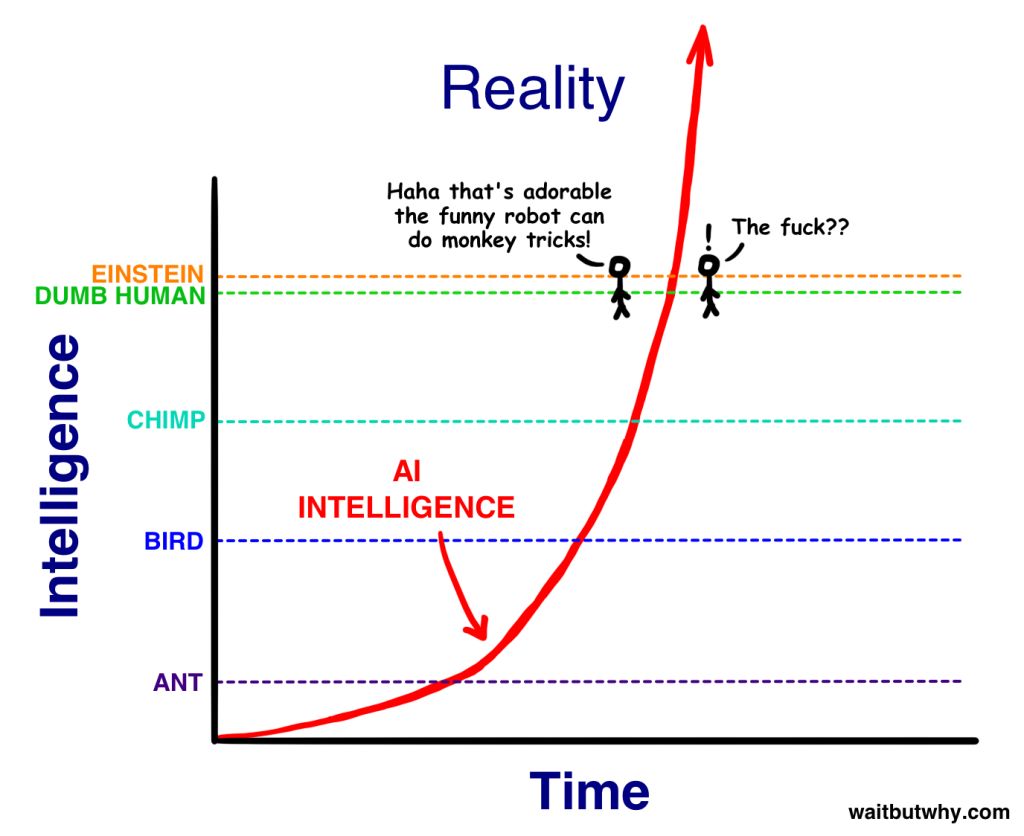
If it is said that the current AI only reaches or exceeds the level of humans on certain specific tasks (image recognition, natural language), most of the AI may be artificially retarded.
But because of the recursive self-improvement strategy, it will accelerate evolution, and a smart explosion will occur at certain nodes. Once it exceeds the scope of human cognition, the only thing left for humans is WTF?
This AI has beyond the speed and quality of human thinking and can undoubtedly help humans solve many complex scientific problems, but what will the emergence of this ultimate ability be? This is an open question and the source of inspiration for countless science fiction works.
Regardless, ignoring the emergence of super AI is not a wise choice.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Alliance Chain Player Consensus: Take orders, card position, live, there is still a long way to go!
- Wikipedia Lightning Network Entry Critical? Bitcoin was deleted 9 years ago
- European Central Bank President: Suggests Digital Euro Targets to Ensure Central Bank Leadership in Digital Currency
- Bundesbank Executive: Fintech and large tech companies and the central bank-conflict of interest or a common mission?
- Observation: Bitcoin computing power and mining difficulty hit a record high in 2019, but miners have experienced the most difficult year in 5 years
- Experts say that the blockchain is in the 2.0 phase of four aspects to empower the manufacturing industry
- Towards the eve of the outbreak of application: What's so bad about the accelerated landing of blockchain technology?





