Trojan attacks, 5,000 computers reduced to mining "black labor"
Text: Kyle
Source: Hive Finance
Editor's Note: The original title was "Five Thousand Computers Reduced to Mining" Black Labor "! 》
The rise of the cryptocurrency industry has not only brought an emerging market, but has also lured profit-making black gangs, one of which is a mining Trojan.
- Big Brothers Call | Chain Node's 2nd Anniversary Special Show Talks Tonight
- Babbitt weekly election 丨 Beijing takes the lead in piloting the "fintech supervision sandbox"; Europe and the United States appear to have divergent views on central bank digital currencies
- Bank of China releases 2020 Economic and Financial Outlook Report: Blockchain empowers the banking industry in all directions
Recently, the Tencent Security Mi Jian Threat Intelligence Center issued a document saying that they detected a "Tiger" mining Trojan (LaofuMiner) spread through social engineering deception. The attacker disguised the remote control Trojan program as "hot news", "pornographic content" and other file names, and spread it on the Internet. Accidental clickers will immediately be recruited, and the computer will become abnormally stuttered and become a black property The gang's labor for mining.
According to statistics, the "Tiger" Trojan has infected more than 5,000 computers. It was found through traceability that the predecessor of Tiger was the Grizzly Trojan that appeared in 2018. At that time, the Grizzly had infected nearly 100,000 hosts and obtained at least 380,000 yuan in illegal income by mining Monero.
In addition to "Grizzly" and "Tiger", Trojan horse mining programs such as KingMiner, BlueHero, and "Quick Go Miner" are common. Some security sources have revealed that since some Trojans have been open sourced in the black industry circle, the cost of malicious acts has been reduced, and the harm of viruses has intensified, and everyone may become a "victim".
Industry insiders have called for the founders of the industry to work together to resist evil practices, strengthen security, and increase the safety factor when developing the cryptocurrency industry.
Trojans hit, 5,000 computers changed to "mining machines" in seconds
Company clerk Zhao Lu impatiently clicked and moved the mouse, but the mouse arrow did not listen at all, and he moved quickly on the computer screen to draw a ghost.
The day before, the computer was fine, and suddenly "turned into a brick", Zhao Lu was anxious. He opened the Explorer and found that the CPU usage reached 97%. He did not run any large software and restarted repeatedly. The problem was still not solved.
Encountered by a severely stuttered computer system, Zhao Lu didn't know, at this time the computer's high-speed CPU was performing a lot of calculations to "mining." This is an industry with some distance from his cognition-cryptocurrency mining. In the past ten years, the industry has become popular in a relatively small currency circle.
From a technical point of view, this is an indiscriminate attack that spreads on social networks.
Tencent Yujian summarized some phishing attack file names, including "a gaming company was attacked", "Miss Sister Video", "Member Profile" and "Voice Changer". These eye-catching file names are not directly related to the cryptocurrency industry. The owner of the poisoned computer may become a "black laborer" who helps the gangs to make money after clicking out of strange hunting psychology.
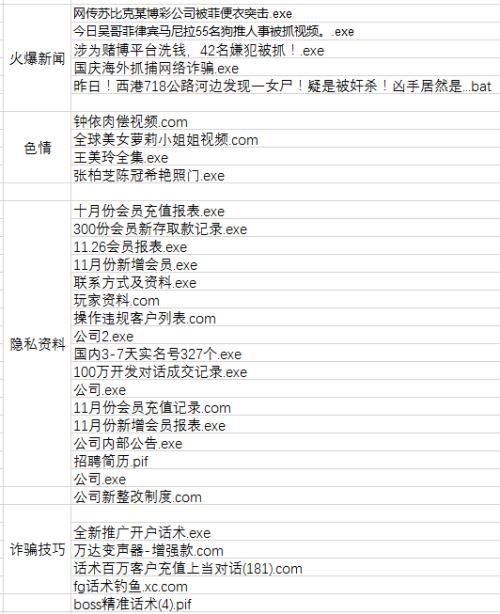
Part of the phishing attack file name (Source: Tencent Yumi)
Tencent Yujian disclosed that the virus attacker was very cunning. After the mining Trojan file is implanted into the computer, the file will be disguised as an audio equipment company "Waves Audio". After the first execution, it will "fat" 150MB with junk data to avoid detection by antivirus software.
The miner program file is disguised as a driver from the graphics card manufacturer NVIDIA. Generally speaking, computer users think that Nvidia's drivers are safe and necessary and will not be deleted at will, so it is difficult to detect and handle them.
At present, it has not been known what coins the above-mentioned black gangs dug through the "Tiger Trojan". Although the "laofubtc" character appears in the mining program, people in the crypto industry believe that it is unlikely that a computer CPU will be used to mine Bitcoin (BTC). "Now the era of computer mining of Bitcoin is over 5,000. The distributed mining pool composed of computers may not be as good as dozens of good mining machines. "
"Grizzly Bear" mutation, black gangs continue to do evil
Tencent Yumi's source tracing query found that the IP address of the file server baihes.com of the "Tiger" mining Trojan was 46.4.156.44. This IP has attracted the attention of security people in 2018. At that time, a mining Trojan named BearMiner called "Grizzly" and its domain name miner.gsbean.com was also directly related to the above IP.
Tencent Yujian speculated that "Grizzly" and "Tiger" belong to the same gang. "Tiger" replaces "Grizzly" mining Trojans, showing a new active trend.
In July 2018, Shenzhen Convinced Security Experts (hereinafter referred to as "Shen Convinced") first exposed the "Grizzly" mining virus. The Grizzly camouflage works the same way as the Tiger, bypassing mainstream antivirus software, and lurking for months.
"Grizzly" is more harmful. According to the statistics of Convincing, nearly 100,000 "Grizzly" infected hosts, and most of the poisoned hosts show abnormal stuttering, which seriously affects the performance of the host.
We are convinced that this virus is classified as "high-risk" and the killing difficulty is "difficult." According to reports, at the time the "Grizzly" mined coins were mainly anonymous coins Monero (XMR). Unlike Bitcoin, Monero's mining threshold is low and easy to use. With a home computer, you can mine using the CPU and graphics card.
In addition, because all Monroe transactions use hidden addresses to protect the privacy of the recipients, it is difficult to track the coins mined by the gangs.
According to the statistics of Sangfor last July, the Grizzly virus had mined 420 Monero coins at that time. According to the currency price of 927 yuan at that time, the attacker gained over 380,000 yuan through illegal mining of Trojan horses, and this cost was not high.
In the black production circle, the remote control Trojan named "Big Wolf" is a more popular remote control tool. It is through this remote control tool that the "Tiger" virus implants a virus into the victim's computer.
It is rumored that the original author of "Big Wolf" has died, but the relevant code has been in the black circle, and is also open sourced and shared. After customized modification by different virus Trojan horse gangs, many variants were derived, which virtually reduced the cost of developing gangs to develop viruses.
In addition to "Grizzly" and "Tiger", in recent years, Trojan horse programs such as KingMiner mining Trojans, BlueHero mining worms, and "Quick Go miners" are common. At the end of 2018, the Shigu Branch of the Public Security Bureau of Hengyang City, Hunan Province, also cracked a virus mining case. A computer graduate graduated by installing a Trojan horse in a computer in an Internet cafe and earning billions of dollars in remote mining.
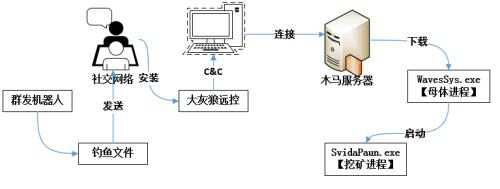
Today, with the development of social networks, people are exposed to a large amount of information every day, and if they are not careful, they may become hackers' "mining labor". When you find that your computer suddenly has a severe freeze, your computer is likely to create improper profits for others.
Security experts advise Internet users not to open files of unknown origin at will. Before clicking the file, it is recommended to open the Explorer folder option, "View extensions of known files". When it is found that the file icon is Office, music, video file, and the file extension is "exe, com, pif, bat", it can be immediately judged as a dangerous file, and it should be deleted immediately and checked with antivirus software.
The rise of blockchain and digital currencies has made "mining" an emerging industry and gradually booming. Benefits are often prone to evil, and incidents such as mining trojans, hacker coin theft, and dark web transactions are endless. "Black production" is also the "coin back" of this emerging industry.
Industry insiders urge that when new technologies and new industries are born, industry participants should jointly improve the security technology reserve and jointly resist the malicious acts of hackers and hackers; professional security teams may wish to establish a security alliance to popularize basic network security to the general public Common sense, strengthen the publicity and early warning of new viruses, so as to prevent the public who do not understand cryptocurrencies from becoming "black laborers" of mining.
Have you encountered a mining Trojan?
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Guo Yuhang: Call on the country to pilot a special tax for bitcoin mining, and to nurture the development of blockchain technology
- Babbitt Column | Is Quantitative Trading in the Blockchain Really Reliable?
- Babbitt Column | A Clear Understanding of Dapp from Multiple Perspectives
- South Korea: Taxes on cryptocurrency transactions expected to start in 2020
- Perspective | 170,000 Ethereum and 400,000 ENS Domain Names
- Undercurrent surging, ERC-20 BTC is stirring the market
- The "fetters" of the blockchain: the public chain and the alliance chain finally have a battle





