What does Schnorr's upcoming multi-signature era mean?
" Without Schnorr, Taproot won't let you go where you want to go."
– Pieter Wuille This article is about 4,000 words, and it takes about 10 minutes to read the full text.
"Schnoor signatures, Taproot, and signature aggregation with multiple signatures are likely to be added to Bitcoin as an upgrade package. This is some very exciting encryption innovation," Andreas M. Antonopoulos mentioned bitcoin earlier this year. It’s hard to hide the excitement of the next upgrade.

- R3 history: from the most beautiful scenery in the past, to the current crisis
- Heavy! The SEC issued the first blockchain token supervision guide, whether it is a securities to see four major points
- Opinion: The non-exchange channel of the currency circle is essentially a brokerage and investment bank.
Well-known bitcoin evangelist Andreas M. Antonopoulos
Antonopoulos is the author of Mastering Bitcoin and an important technologist and respected person in the cryptocurrency world. He predicts that Bitcoin upgrades will be implemented in soft forks in six months, and upgrades including Schnoor will provide users with privacy benefits that Bitcoin does not currently have.
The upgraded BIP has been created and the relevant specifications are being finalized. Bitcoin core developer Pieter Wuille and other developers have written implementation code, and the first prototype has been created. The bitcoin luxury upgrade package with Schnoor as its core is on the road.
So, what exactly is Schnoor, which is popular with Bitcoin developers? What is it bringing?
01
What is the Schnoor signature?
Bitcoin is a digital signature that unlocks the unspent balance in UTXO to complete the transaction.
The following figure is an example. In transaction B, Bob transfers Carol a bitcoin. Bob needs two steps to complete the deal:
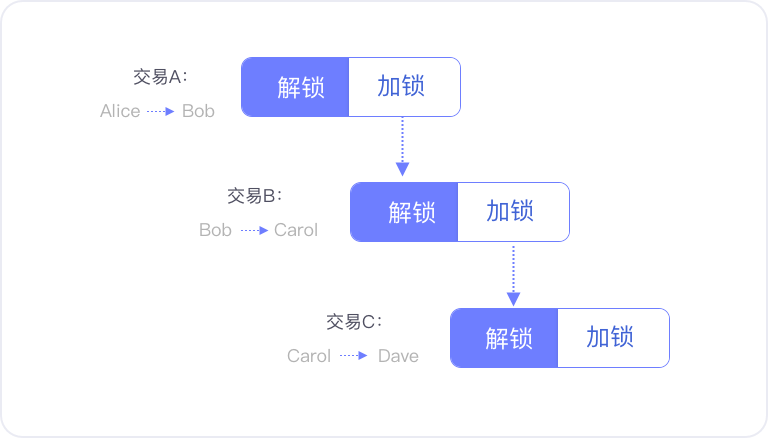
1. Prove that you own this bitcoin.
Why did Bob own this bitcoin because Alice gave him this bitcoin; Alice locked Bob's bitcoin with Bob's public key hash in the "locked" part of transaction A, which It is also Bob's wallet address.
Bob provides his own public key and the signature created with the private key in the "Unlock" section of Transaction B to prove that this bitcoin is his own, thus unlocking and using this bitcoin.
2. Give this one bitcoin to Carol.
Bob locks this bitcoin with Carol's public key hash in the "locked" portion of transaction B, indicating that the bitcoin belongs to Carol.
When Carol wants to use this bitcoin, for example, if you want to transfer to Dave, Carol will need to create a transaction C. First unlock the bitcoin with its own public and private key signature in the "Unlock" section, and then "lock" Part of the bitcoin is locked with Dave's public key hash.
It is not difficult to find that Bitcoin needs to be locked with a public key and unlocked with a private key signature to realize the transaction of cryptocurrency. How are public keys, private keys, and their signatures generated? Through a digital signature algorithm.
Schnoor is a digital signature algorithm that will replace the signature algorithm ECDSA currently used by Bitcoin in the next upgrade. Schnorr was proposed by German mathematician and cryptographer Claus Schnorr. The algorithm can use the same elliptic curve as ECDSA: secp256k1, so the upgrade will not change much.
The most striking feature of Schnorr is that it is "linear", that is, it can aggregate multiple public keys or multiple private key signatures into a new public key or a new signature (also known as multiple A lock that needs to be unlocked at the same time becomes a lock, a string of keys for unlocking is turned into a key, and the new public key or signature also satisfies the linear feature.
To make a metaphor that is not particularly suitable but can explain the problem, in a multi-sign transaction using Schnorr, if the public key or signature of the participant Alice is 1, Bob is 2, Carol is 3, and Dave is 4. Then the public key or signature displayed on the transaction is 10 (1+2+3+4=10) instead of 1, 2, 3, 4.
02
Benefits of the Schnoor Signature Algorithm
Schnorr developer Andrew Poelstra believes that people are interested in Schnoor because it increases the scalability of Bitcoin and allows people to create multi-tap transactions with very many participants. The participants here not only refer to multiple people. It may also be a Liquid network, a lightning network, a smart contract, and so on.
In addition, Andrew believes that Schnorr signatures, when combined with Taproot and Scriptless Scripts, will make all Bitcoin transactions look the same, whether it is a normal transaction or a complex transaction, which will greatly improve the privacy of Bitcoin.
These advantages stem from the fact that in the case of multi-signing, if ECDSA is used and N public key is used for locking, it is necessary to have N signatures corresponding to it for verification and unlocking, and the verification work needs to be performed N times; Using Schnorr, N public keys can be aggregated into one public key, and only one aggregated signature is used for verification during verification.
This "linear" trait makes Schnorr superior to ECDSA in terms of performance, size, and privacy.
Performance: Schnoor's performance advantages are obvious, it reduces the verification workload of a multi-sign transaction, and it is also possible to implement batch verification of multiple transactions, that is, verify all transactions at once with the aggregate signature of all transactions in a block. Thereby improving the verification speed of Bitcoin.
Volume: Schnorr uses aggregated public keys and aggregated signatures, which reduces the size of multiple signatures. By moving extraneous data out of the blockchain to increase system scalability, nodes will have more bandwidth while reducing storage. Andrew believes that if everyone adopts this method, it will equal the disguised increase of bitcoin capacity by 10% to 20%.
Privacy: Schnoor's privacy advantage is that it uses the aggregated public key and the aggregated signature to complete the locking and unlocking operations in the transaction script. A user's original public key and original signature are not exposed. The outside world can only see 10, but can not see 1, 2, 3, 4, the outside world can not even know whether this is a multi-sign transaction or a non-multi-sign transaction.
Schnoor signatures have more interesting uses, such as it can be used after being adjusted. One can multiply an aggregated public key by 2 as the new aggregated public key to unlock it. When unlocking, you only need to multiply the aggregate signature by 2 to complete the unlock. This way others can't know what the original aggregated public key and the original aggregated signature are, and they don't see if the public key or signature has been adjusted.
03
Combination of Schnorr and Taproot
Pan Zhiyi, the founder of the coin-printing pool, also believes that this upgrade is of great significance. He wrote in his personal Weibo: "MAST, Schnorr, Taproot, combined, burned to the explosion", how does Schnorr combine with Taproot and other technical means? What benefits does this combination of punches bring to Bitcoin?
Start by understanding what they are. Schnorr is the signature algorithm, which is the most basic and core of these technologies; MAST, Taproot, Graftroot, Scriptless scripts, etc. are script structures that can be used to make the most of their functions by using Schnorr.
Bitcoin scripts are the carrier of bitcoin transactions: a bitcoin transaction is implemented by executing a bitcoin script, unlocking is the execution of the "input script", and locking is the execution of the "output script". The script structure refers to the data structure of the Bitcoin script.
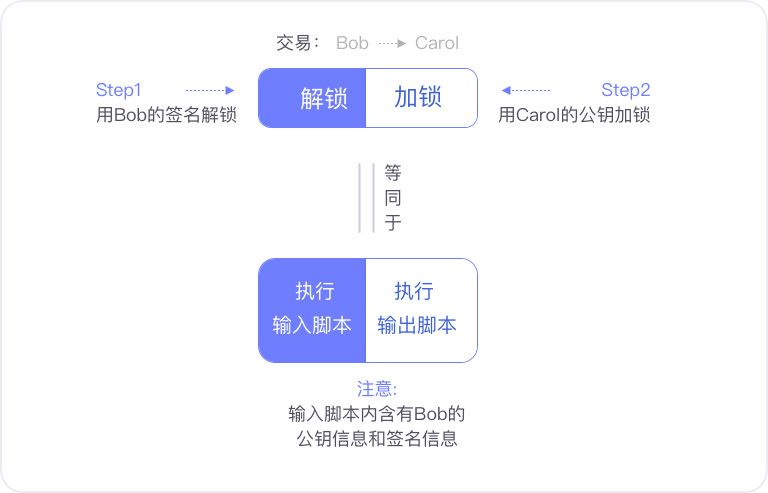
As mentioned earlier, when people use their unspent balance for Bitcoin transactions, they need to provide their own public and private key signatures in the input script section to prove that they own these balances.
P2SH is the most basic script structure of Bitcoin. It displays the contents of the entire script, including the information of the public and private key signatures. The node uses this information to verify the transaction. But at the same time, the node and anyone can get the full details of the deal.
So we say that bitcoin is transparent. Although it can isolate the physical entity's individual from the Bitcoin account and realize the physical individual's anonymity, if the P2SH does not provide privacy for the account from the perspective of the Bitcoin account, everyone can know which fund is/ Which accounts are used in what way.
Because of the shortcomings of P2SH, developers have proposed a new script structure MAST, which is a tree structure, specifically a Merkel tree, that is, a hash tree, stored in each node of the tree. Both are hash values. Its structure is shown in the figure below.
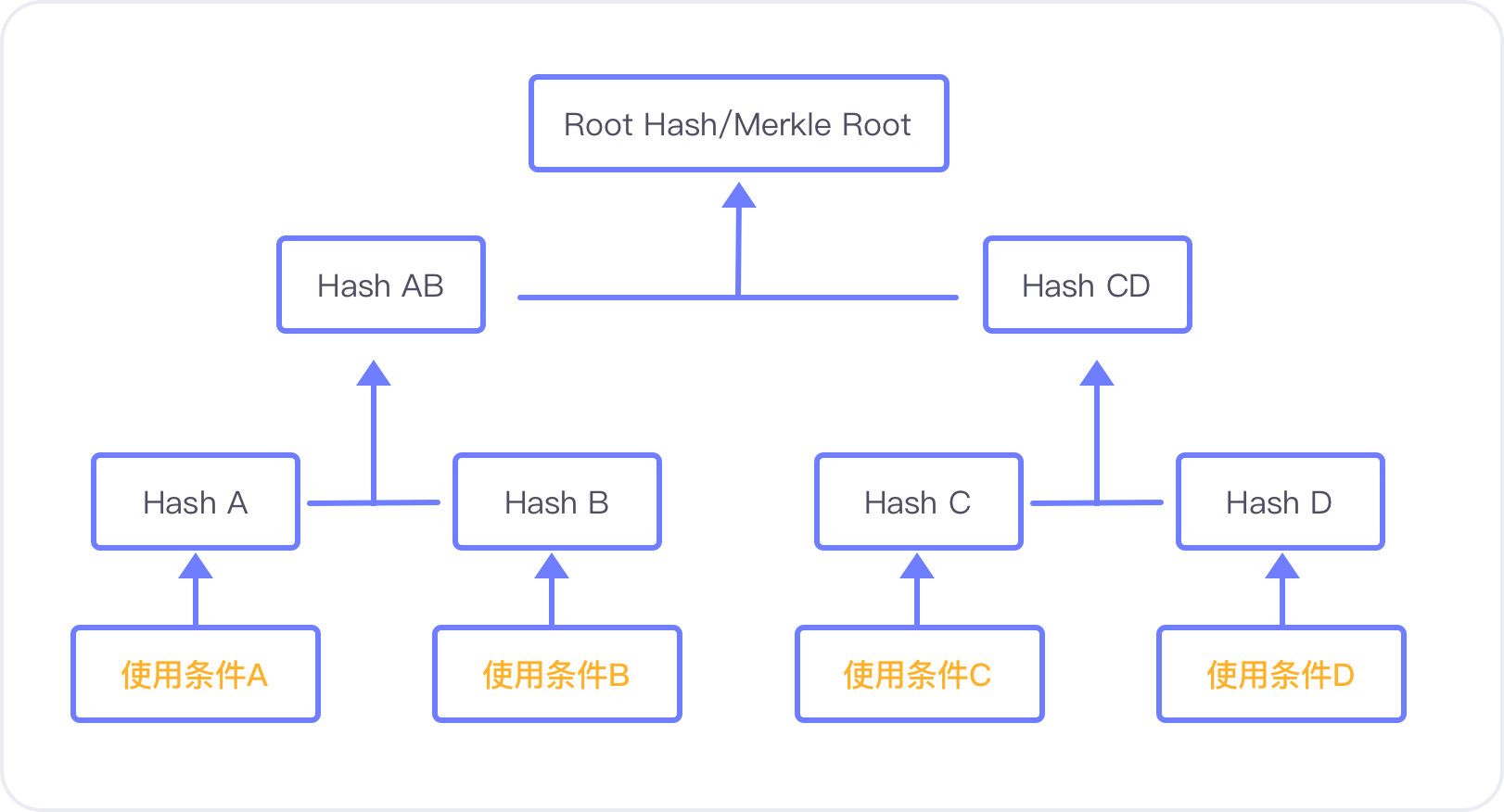
Tree
The use of the MAST structure in bitcoin transactions means that in the case of multi-signing, a different use condition of a fund is separately hashed, and a hash value is generated and stored in the leaf node of the tree; these hash values are layer by layer. Recursively, a hash value is finally generated in the topmost node of the tree, that is, in Merkel root.
In this way, when verifying a transaction, you don't need to expose all the script information. You only need to provide Merkel root and the data on the Merkel path that arrives at a certain usage condition. The other information is still in the hash cipher state. The MAST script structure not only provides privacy but also increases data processing efficiency.
Now you can talk about Taproot.
Taproot is a special MAST based on the Schnorr signature. It can contain complex trading conditions and capital usage details, just like MAST, and then provide all of this content as a new capital use condition (new lock) to the outside world, this new use condition and the conditions of use The unlocking method (new key) is supported by the linear features of Schnorr.
In the final presentation, Taproot does not need to disclose any script information, nor does it need to expose the original public key, the original signature, its output is an aggregate signature lock, and only use an aggregate signature to unlock.
Do another metaphor that is not particularly suitable but can explain the problem. Sun Wukong can turn monkey hair into a monkey, and Taproot does it to turn a monkey into a monkey hair. That is to say, we regard the ordinary transaction as a monkey hair and regard the complex transaction supported by MAST as a powerful monkey. Taproot can turn the MAST monkey into a monkey hair, which Andrew said makes all bitcoin transactions look the same, no matter how complex it is.
This has greatly improved the privacy of Bitcoin, including account privacy under multi-signed transactions, smart contract privacy, and the privacy of Liquid, Lightning, and more. Because smart contracts, Liquid networks, lightning networks, and more expansion plans are all multi-sign, a complex transaction.
04
Combination punch opens multi-checkout
In real life, we often advocate a kind of "lifestyle". In the world of cryptocurrency, perhaps we should advocate multi-sign as a way of life, let multi-sign as the common sense of cryptocurrency. Habitual use of funds.
The increase in transaction privacy based on Schnorr and Taproot has been described in the previous section. It can hide the public and private key signature information of participants and hide the details of the funds being used.
Another benefit of multi-signing is to increase security. Whether it is the death of the founder of Canada's Quadriga CX exchange, the $160 million cryptocurrency lock event, or the ongoing exchange of wallet stolen from Mt.gox, it can be improved through multiple sign-offs.
Multi-signing provides a "recovery" method for cryptocurrencies, which allows us to unlock other ways when we can't unlock Bitcoin through a certain path or some way. It's like in real life, if we lose the savings card and can't get the money, we can use the passbook to withdraw money.
(Note: Of course, the savings card is now reissued, but the method of replenishing the card is completely different from the way of multi-signing. The cryptocurrency does not have a supplementary card, because the private key itself is the ultimate unique certificate, unlike the bank. Above the account voucher there is also a layer of credentials for the user identity that can be used to replenish the card).
Multiple sign-offs can also provide harsh cryptocurrency "use" conditions, which are normally only unlocked when these conditions are met at the same time. It's like entering the bank's vault, you need to swipe your card and brush the retina to open the vault door, you need a password and a key to open the safe.
These are the benefits of multi-signing, and the combination of Schnorr and Taproot further upgrades this benefit, allowing multi-signs to be implemented in a more efficient and privacy-oriented manner.
It should be noted that even after the upgrade, a common transaction that does not use multi-sign is unable to get the benefits of Schnorr and Taproot, and the privacy level is the same as before the upgrade.
Therefore, on the one hand, it is necessary to promote multi-signing. On the other hand, even if ordinary transactions do not use multi-sign, multi-sign is required in a large number of application scenarios, such as using bitcoin through smart contracts, through Liquid network, lightning network, and more. Bitcoin is used in a way that expands outside the chain. The status of multi-sign is itself becoming more and more important.
The combination of Schnorr and Taproot – which may also include more multi-sign scripting structures such as Graftroot – will greatly enhance the performance of multi-sign, making complex transactions on Bitcoin possible.
Complex transactions can be easily identified in the past, but after upgrading they will look the same as regular transactions, and transactions will become private. For example, when a user opens or closes a lightning network channel, no one knows except the participant. What, what others saw was just a normal locked public key. Wuille said that Schnorr and Taproot are bitcoin's great victories in privacy.
Wuille also believes that Schnorr and Taproot are huge wins for Bitcoin smart contracts. They will allow the creation of multi-tap transactions with complex usage conditions, and with the support of Schnorr linear features, many new applications and under-chain innovations may be derived.
In addition, with the support of Schnorr and Taproot, complex transactions not only have high execution efficiency, but also do not need to occupy extra bitcoin blockchain space. Schnorr uses aggregated public keys and aggregated signatures, requiring only one verification; Taproot supports a large script tree, but takes up very little space.
It's not hard to find that although Bitcoin supports multi-sign before, the bitcoin upgrade package including Schnorr and Taproot will undoubtedly open the multi-issue curtain. The multi-sign is not only a safer and more The privacy, more scalable Bitcoin blockchain is also an infrastructure that supports smart contracts, Liquid networks, lightning networks, and more Bitcoin applications in the future.
This is a better future worth looking forward to.
————————
The author is particularly grateful to Mr. Pan Zhiwei, founder of the coin-printing pool, for his help with this article.
reference:
1. "Understanding Bitcoin Scripts", Wang Haibo
2. "Introduction to Schnorr Signature", "Introduction to Taproot", Bitcoin Lab
3. "Taproot Is Coming: What It Is, and HowIt Will Benefit Bitcoin", Aaron van Wirdum
4. "Exclusive dialogue Schnorr signature developer Andrew Poelstra: Schnorr will expand Bitcoin by 10%-20%", Babbitt
5. "What is Bitcoin's Graftroot? CompleteBeginner's Guide", Brian Curran
– END-
Author: Lee draw (money letter freelance writer)
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Public chain development combat: local environment preparation virtualbox articles
- Symbiosis of 5G, Internet of Things, and Blockchain: Record of 2019 IT Leaders Summit
- The highest rate is 5 ups! Blockchain concept stocks are the rise or fall of the bubble or the return of value?
- Opinion: "Unable Triangle" of Stabilizing Coins
- The story behind the resurgence of the venture capital Andreessen Horowitz
- What is the mission of Bitcoin? Why did Coinbase start crazy online assets? The answer is here
- Is the mine-based “guaranteed” income product really low risk?





