What is the technology of Long Wenda's summary of anonymous cryptocurrency?
The purpose of this article is to provide a brief overview of the anonymous mechanisms implemented in today's mainstream cryptocurrencies.
Blockchain anonymity is a particularly difficult task because the design of the public blockchain makes all transactions transparent, and the supply of cryptocurrencies can be publicly verified. Even if there is a conflict between protecting privacy and maintaining public verifiability, the anonymity mechanism must ensure that these two elements are preserved. To understand the innovation behind Sigma and Lelantus, we need to study the history of blockchain anonymity.
1. Money pool mix coin and coin blender
Used for: Dash Dash, Bitcoin Coin
- The coin circle is playing the role of Call, the circle of friends is the biggest marketing field.
- QKL123 market analysis | Bitcoin shock convergence, short-term callback risk is greater (0809)
- BTC high-level dishwashing, the mid-line market still retains hope
advantage:
· Run on most cryptocurrencies without a specific consensus
· Relatively simple to implement
·Lightweight
Disadvantages:
· can only provide basic anonymity
·Requires online coin
· Early applications require trusted third parties
The first way people try to achieve anonymity is to achieve the goal by mixing the coins of themselves and others in the pool of funds. It is difficult to prove who the coins originally belonged to after mixing, thus providing some degree of anonymity. Of course, the premise is to believe that others will not steal your money.
The blender is an improvement of this hybrid concept, eliminating the possibility of anonymous initiators stealing coins, which is widely used in Darkcoin (now called Dash). But the coin still has a lot of drawbacks.
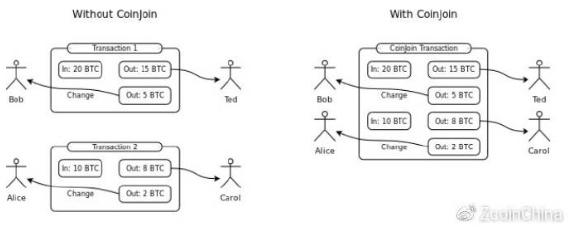
(1) Because the background can record information and know the input address of each user and the address they are receiving, you need to trust the anonymous initiator. This problem can be avoided by using anonymous digital signatures, so the agility of the coin is strongly dependent on logging in anonymously (for example via the Tor network).
(2) Require the people involved in the coin to conduct the coin online. If the parties cannot agree on the amount of the coin, they must be postponed.
(3) Anonymity is limited by the number of people. Dash's private transactions only involve 3 participants, but the process can be repeated.
(4) A recent study (https://arxiv.org/pdf/1708.04748.pdf) shows that even after a multi-round blender, if the user’s wallet does not clear the browser cookie when making a payment, it can pass the technology. The means to identify the user's wallet, because the currency will only cover the transaction links between the addresses, but will not completely destroy them.
(5) It is easy to break the operation of the coin and delay other participants to complete the coin transaction.
More seriously, the application called PrivateSend in Dash is vulnerable to cluster cross-attacks.
Other improvements to the coin, such as CoinShuffle++, no longer require trusted third parties, but are still limited by other shortcomings of the coin, such as limited anonymity, participants must be online, and so on.
The main benefit of the agile anonymity is that they are relatively simple and work on a cryptocurrency basis without the need to use specific consensus rules. With appropriate precautions, the coin can provide basic anonymity.
Tumblebit is also a very promising solution to improve the anonymity of the coin, but beyond the scope of this article. Compared to the other anonymous solutions we will discuss in the next step, this is an anonymous plan that is not implemented at the agreement level, but still requires others to provide funds for the mix. Its main advantage is the same as that of the coin, which can be implemented in Bitcoin or any other digital currency without changing its protocol.
2.Cryptonote and ring sign
For: Monroe Monero
advantage:
·Mixed auto-complete
· Can be automatically anonymized by default
· Anonymity increases as new coins are added and time passes
· Hide transaction amount when using RingCT (or bulletproof proof)
· Fully studied cryptography foundation
Disadvantages:
· Can't interrupt transaction links, only blur them, so they belong to the "bait" model
· Poor scalability due to its blockchain data is huge and untrimmable
· There is a risk of being decrypted due to advances in technology or implementation errors
· Unable to take advantage of the existing Bitcoin ecosystem and require separate work
·The size of the ring is limited
· Simple Payment Verification (SPV) is not available, so you must always run or connect to a full node (no light wallet)
· It is difficult to implement some Layer 2 solutions, such as lightning network
· No supply auditability means hidden inflation may not be discovered
The next anonymous solution we will explore is the ring tag used in the Cryptonote cryptocurrency such as Monero. The ring sign scheme greatly improves the anonymity of the cooperator scheme. In the ring sign, someone signs a transaction and can only track one group and not specifically track the person in the group. For example, it can be seen that a "high-ranking White House official" signed a ring sign, but could not track which official signed the message.
Cryptonote and Rings can automatically implement anonymity without the need for other users to specify who they want to mix with, or wait for others to provide funding because it simply scans the blockchain for output. Because there is no coin, you don't need to trust anyone. Monero also recently implemented RingCT (RingConfidential Transactions), which also hides the transaction amount.
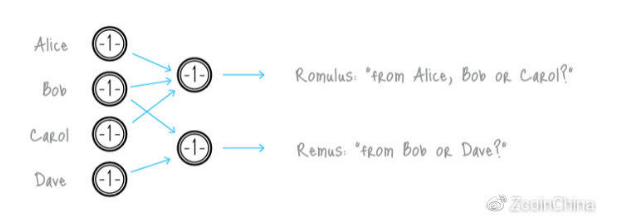
There is also a limit on the actual size of the ring sign (the number of other outputs you use) implemented in the Cryptonote cryptocurrency, as the size of the transaction data increases linearly as the size of the ring increases. This is why by default, Monero's default ring size is 4. In fact, using different ring sizes, by default, may allow you to anonymize. This means that anonymity is limited by the number of ring participants on a per-transaction basis. Blockchain analysts may not be able to prove that transactions are related, but they can calculate the probability of a transaction association. Therefore, the main disadvantage of Cryptonote is that it can't break the link between transactions, but only confuse the two sides of the transaction to make the transaction difficult to track.
In addition, security researchers have found ways to make informed guesses about which transaction is a real transaction by linking the transaction to the transaction time. In any combination of a real coin and a set of fake coins bundled in a transaction, the real coin is most likely the latest coin that moved before the transaction. Prior to the recent changes by Monero's developers, timing analysis correctly identified real coins over 90% of the time, which effectively invalidated Monero's privacy protections. After changing how Monero chose mixins, this technique now has a 45% chance of finding real coins – in this case, identifying the real coin is only about two guesses, far below the expectations of most Monero users.
Another criticism of this kind of encryption technology is that if there is a bug in its ring signing technology or a fairly powerful quantum computer, the entire blockchain record will be anonymized and traceable, and cannot be done afterwards. Corrected. Like the Cryptonote cryptocurrency called Shadowcash, all the block data is decrypted because of the bug. However, the practical quantum computer has been around for a while, and it comes down to whether the transaction data is still valuable a few years ago. In order for this data to be useful, it is likely to need to be combined with external data.
It is also important to note that the use of ring marks to hide transaction amounts sacrifices supply auditability. “Supply auditability” verifies that new cryptocurrencies are secretly generated during the transaction and determines the exact amount of cryptocurrency at a time. In the implementation of Monero's "ring sign", if someone breaks the discrete logarithm supporting the ring sign, he can falsify the cryptocurrency without anyone knowing it, although it is still difficult to do with current technology. This may only exist in theory because discrete logarithm problems are widely used in cryptography, and discrete logarithms are expected to be viable before the quantum computing era. However, code errors can also be counterfeited, and lack of supply auditability can complicate detection of hidden inflation. People have indeed discovered a bug in Cryptonote that allows for infinite inflation, although it has been fixed before anyone uses it.
Using a completely different code base than Bitcoin also means that third parties must do more to integrate CryptoNote into their existing ecosystem. Simple Payment Verification (SPV) is also not supported, making lightweight wallet implementation a problem.
Despite these shortcomings, Cryptonote has proven to be a very good anonymous technology today. The only example of its publicly disastrous defeat is Shadowcash, which was completely decrypted, resulting in a cascading effect by using a Monero transaction that mixed zero transactions, about 87. % of the input was de-anonymized. (Subsequently eased by the new exchange). Therefore, the new technology in blockchain analysis may greatly reduce the anonymity of Cryptonote because it is just a system based on “bait”. This has been demonstrated in a recent FloodXMR paper, which shows that a lower cost attack can be implemented by a large number of fragment transactions that invalidate the mixing of the inputs. Of course, there is still debate about the cost and efficiency of this technology.
3.Zerocoin protocol and Zcoin
For: Zcoin, PIVX
advantage:
· No need to mix coins
· Thousands of casting and retrieving transactions completely disrupt the connection established by each address through the transaction, thus achieving extremely high anonymity
·Reviewability of retained totals
· Use cryptography that has been heavily validated
Disadvantages:
· Zerocoin has been cracked due to one of the proofs of encryption defects. Although it can be fixed, better implementations such as Sigma and Lelantus will replace it.
· Proof size is currently relatively large
· Need a pre-trust mechanism
· Wrong implementation or leaked pre-trusted setup parameters may result in forgery of zerocoin
· When casting and retrieving, you need to pay more attention. To prevent timing attacks, the user must save the recast coins for a period of time before preparing to retrieve the anonymous coins.
Now let's take a look at Zerocoin implemented on Zcoin. Unlike the anonymous scheme that previously only disrupted the input and output of the transaction, the Zerocoin protocol completely interrupted the transaction link between the coins with zero proof of knowledge.
Simply put, a zero-knowledge proof is proof that you are doing something or knowing something, without revealing any other information. For example, to prove that you know the password, you don't need to actually display the password.
Zerocoin works by casting your own cryptocurrency (which we call coin casting) and then redeeming the same amount of new coins (called zero coins). These coins appear without any trading history and appear to be the same as the newly dug coins. This proof is used to prove that you did destroy the cryptocurrency without revealing the specific cryptocurrency information you destroyed, so you have the right to redeem the same amount of SGD.
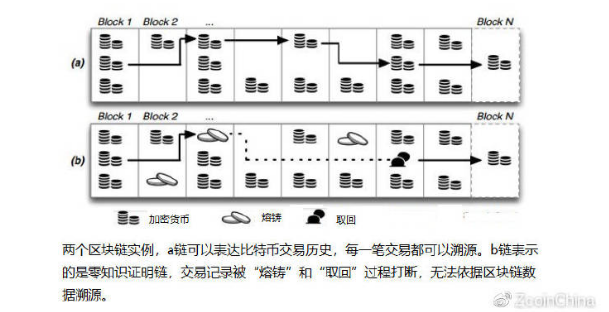
This means that unlike Coco and Cryptonote technology (the size of an anonymous set is limited by the number of participants or the size of the ring), Zerocoin's anonymous set is much larger. Your anonymous set is equal to the total amount of all the same values that have been cast. This allows anonymous people to use zero coins to mint and retract them in thousands of people. In addition, the trading links of these coins have been completely broken, because they seem to be entirely new coins, compared to the previous anonymous method is just to cover the transaction.
This anonymous mode also has some drawbacks. In order to achieve great anonymity while breaking the transaction link, Zerocoin needs a trusted setup to generate the initial parameters. In Zerocoin, there are two large prime numbers that were destroyed. If someone gets these two huge prime numbers, you can fake Zerocoin out of thin air. To solve this problem, Zcoin used the 1991 RSA Prime Challenge, in which cryptographers generated and destroyed two large prime numbers and challenged them to successfully break them down in 16 years. A bonus of $200,000 was provided, but no one can solve this problem. Today, the RSA-2048 method is still the best method we know, and the RSA-2048 method is still widely used until the emergence of a quantum computer that can specifically solve such problems.

It is worth noting that the successful decomposition of these two prime numbers does not affect the anonymity of zero coins, as it only affects casting. In addition, the total amount of Zcoin can be checked so that the coin casting process can be monitored. In the early stage of the project, due to a bug in programming (not RSA was cracked), the coin casting problem occurred, but we detected the bug and repaired it in time, so it can be seen that the total amount is very important.
It is also worth noting that even Bitcoin suffered a hyperinflationary bug in 2010, and because of the supply auditability, people detected 184.4 billion coins produced out of thin air. Recently, in September 2018, another hyperinflation loophole was discovered in Bitcoin, but it has still not been developed.
Another limitation of Zerocoin is that casting and retrieving a currency that can only handle fixed denominations, compared to a ring-trade, zero-coin zero-knowledge proof data size is 25kb. It is worth noting that, unlike Cryptonote transactions (all transactions occupy the same size of data), only anonymously retrieved transactions occupy 25 kb of data, while normal transactions have the same data size as Bitcoin transactions. Compared to other transactions, Zerocoin's retrieval of transactions is also very computationally intensive and takes about half a second to complete.
In addition, improper use or regular use of Zerocoin coins and cost transactions, such as always casting and consuming regularly, or casting and retrieving intervals are too short, or casting and retrieving using the same IP address may damage Anonymous, so you need to be careful. Users are advised to pre-cast coins before they want to retrieve the coins. The longer a coin exists in a cast form, the better the anonymity. This is being alleviated by Zcoin's upcoming GUI, which advises users to keep a certain percentage of coins cast.
All in all, Zerocoin provides very strong anonymity, but in order to achieve this anonymity, you need trust mechanisms, storage space on the blockchain, and additional computing resources. The development of Zcoin is addressing these issues.
4.Sigma
For: Zcoin, NIX
advantage:
· No need to mix coins
· Anonymity is very high, and the anonymous set can be as high as 100,000 or so. Casting and retrieving transactions can completely break the transaction link between addresses.
· Maintain a certain degree of supply auditability, as the transaction amount will not be hidden and the coin must be retrieved to the base layer.
· Use cryptography that has been thoroughly studied.
· Small proof size, only 1.5 kB.
· No pre-trust mechanism is required.
Disadvantages:
· As with Zerocoin, a fixed face value must be used.
• Care must be taken when operating Sigma casting and retrieving. The user should cast the coin before retrieving to prevent timing attacks.
· Anonymous sets are difficult to break through 100,000 before the cryptography foundation breaks.
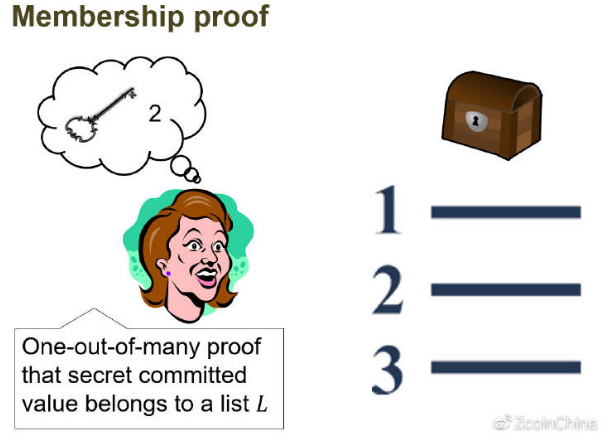
Sigma is an anonymous protocol invented and implemented by Zcoin that works in much the same way as Zerocoin. It has two key differences: it does not require a pre-trust mechanism, and its proof size is significantly smaller, about 1.5 kB (compared to Zerocoin's 25 kB).
Based on the academic paper "One-Out-Of-Many-Proofs: Or Howto Leak a Secret and Spend a Coin" (Jens Groth and Markulf Kohlweiss), Sigma replaced the RSA accumulator with Pedersen's promise and other technologies, making this encryption structure without pre-trust mechanism. The only system parameters required in the Sigma setup are the ECC group specification and the group generator. This structure has been further optimized in "Short Accountable Ring Signatures base on DDH" (Jonathan Bootle, Andrew Cerulli, Pyrros Chaidos, Essam Ghadafi, Jens Groth and Christophe Petit).
Sigma is strictly a deeply optimized Zerocoin. The only drawback is that it still requires a fixed denomination, which means that the caster and the retriever are more easily identified when the user is not paying attention, and the anonymity set is limited to approximately 100,000 with guaranteed performance.
5.Lelantus
Such as: Zcoin (in research and development)
advantage:
· No need for a coin mixer
· Anonymity is very high, with an anonymous set of up to around 100,000, using a cast and retrieve transaction to completely break the link between the transaction addresses.
· Use mature cryptography, only need DDH encryption hypothesis
· Small proof size, only 1.5kB
· No pre-trust mechanism required
· Can use non-fixed denominations
· Coins that can be paid directly and cannot be converted to the base layer
· Good scalability enough to support default anonymous transactions
Disadvantages:
· Anonymous set is difficult to break through 100,000 before the breakthrough in encryption technology
· At present, direct anonymous payment requires the revenue party to retrieve it again and re-cast it to prevent the sender from sending the time to be discovered.
· Still in the early stages of development. Zcoin has completed its encryption library and Monero's Sarang Noether has also completed its initial implementation.
Lelantus further extended Sigma by removing the requirement for fixed denominations and allowed direct anonymous payments, but did not display the amount. Lelantus is the creation of Zcoin's cryptographer Aram Jivanyan and is part of our ongoing improvement of the privacy agreement, the full text of which can be read here.
Lelantus retains all the benefits of Sigma's lack of pre-trust mechanisms, but hides the transaction amount by leveraging double-blind commitments and bulletproof proofs, eliminating the remaining weaknesses that require fixed denominations. Users can burn any amount and redeem any amount, which makes it more difficult to find the connection between casting and retrieval.
If Lelantus has some weaknesses, then its anonymous set is still limited to about 100,000. Exceeding future performance makes it impractical to implement, but we think it is impractical to analyze such a large set of anonymous sets. Compared to almost all other privacy mechanisms, its anonymous set is still higher, except that Zerocash has its own set of trade-offs (pre-trust mechanisms, complex constructs, etc.), which we will explore further below.
Direct anonymous payment in the current research state also requires additional retrieval and re-casting steps to anonymize the sender. We are still working on further research to further improve and expand.
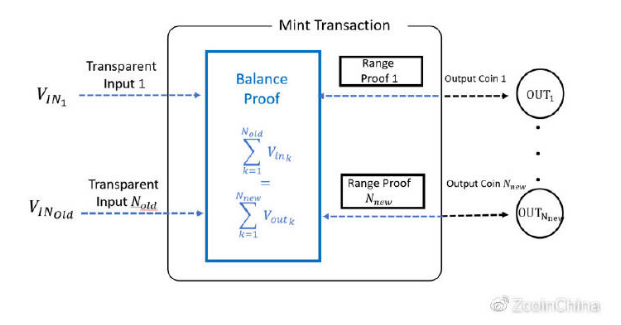
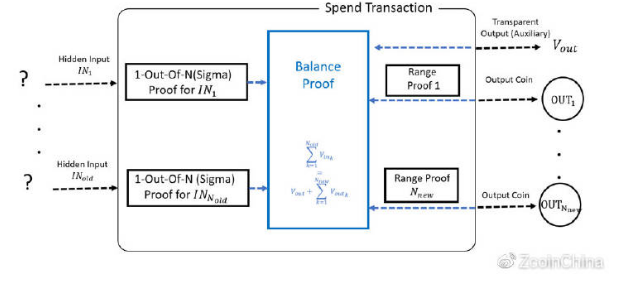
6.Zerocash and Zcash
Such as: Zcash, Horizen, Komodo,
advantage:
· May be the best anonymous technology in the process of casting and breaking the transaction link between addresses
·Verification data is small, verification speed is fast
·Hidden transaction amount
· No need to convert to regular coins in advance, anonymous coins can be sent directly to each other.
Disadvantages:
· Anonymous transactions are computationally intensive (although greatly improved through Sapling upgrades)
· Complex pre-trust mechanisms that must be arranged by the team
• Incorrect implementation or leakage of pre-trust mechanism parameters may result in counterfeit coins.
• Therefore, if the coin is forged and produced out of thin air, the supply cannot be detected, so the supply cannot be detected. Vulnerabilities of this nature can be found either before the release or in the real-time home network.
Use relatively new cryptography and based on the Cryptic Assumptions (KEA) that were criticized.
• It is difficult to understand that only a few people in the full sense can master cryptography and code, and may make mistakes.
The last anonymous solution we discussed was the Zelocash protocol used in ZCash. Zerocash uses zero-knowledge proofs and attempts to improve the Zerocoin protocol. With the Zerocash and zkSNARKs technologies, the anonymous data size is now only 1 kb and can be verified quickly. In addition, all transaction amounts are hidden and do not require a fixed denomination for casting. Zerocash also allows people to transfer Zerocash's "zero coins" directly to each other without having to convert them into equivalent base coins. Its anonymous method is also the largest of all previous anonymous plans, including all coins cast, without considering the face value of the blockchain.
Roughly speaking, it will feel that the Zerocash technology is beyond Zerocoin. However, compared to Zerocoin, it also has some shortcomings.
First, Zerocash lacks supply auditability. Like Zerocoin, Zerocash requires a pre-trust mechanism, but Zeerocash's setup is much more complicated. Zcash used a multi-party ritual involving six people to complete the setup. The only way to disclose the parameters is that all six people collude with each other and retain the relevant parameters. In other words, you must trust any of the six people, believing they destroyed the initial parameters and believe that the ceremony was executed correctly. This is a serious problem and Zcash is organizing a new pre-trust mechanism ceremony.

If there is an error in the code, or if there is a problem with the encryption defect or the multi-party pre-trust mechanism, the attacker may generate an unlimited Zcash, which, unlike Zerocoin, cannot detect this extra supply. Especially in systems that use Zerocoin to operate on a similar principle, allowing new coins to be created, supply auditability becomes more and more important.
In fact, from the release to October 28, 2018, for two years, Zcash has actually patched one of its vulnerabilities on its main network. There is no way to tell if this bug was exploited before it was patched, and there is an eight-month gap between bug detection and patching. This is not the first time such an error has been discovered. Zerocash also had internal collision vulnerabilities early in its development, which also allowed forging coins. Although this bug has never been put into production, it highlights the potential risks.
BTCP, a forked coin based on both Zcash and Bitcoin, also suffered from hidden inflation, which has not been discovered in the past ten months. This inflation can only be detected by checking the UTXO output flow when entering via Bitcoin UTXO. This is not due to a deficiencies in cryptography but a covert premise that highlights potential problems with unaudited supplies.
We emphasize that even highly scrutinized projects like Bitcoin have experienced many hyperinflation errors, such as value spillovers and the recent CVE-2018-17144. Bitcoin retention supply auditability allows these errors to be detected or to confirm that no exploits have occurred.
Another debatable is the use of a new experimental cryptography called zkSNARKs, which is actually only used for Zerocash. It has been reviewed much less, so unlike the RSA, which has been tested in practice, RSA has been used and has been reviewed for many years and continues to be widely used. zkSNARKs use encryption assumptions, which are still experimental. Unlike established encryption algorithms, such as discrete logarithmic hypotheses or decomposition hardness, zkSNARKs security is based on variants of the bilinear group's exponential knowledge (KEA) hypothesis (instantiated by some pairwise-friendly elliptic curves). KEA has not been well researched or deployed and has been criticized. Some experts believe that the cryptography behind zkSNARKs is relatively weak.
Zerocash is also very complex, which means that only a few people can understand and review it correctly. In fact, due to the Zcash assumption, the following phenomena occur:
Discovering vulnerabilities requires a high level of technical and cryptographic complexity, and few people have it.
The vulnerability has existed for many years, but many expert cryptographers, scientists, third-party auditors, and third-party engineering teams have not discovered these vulnerabilities. They have launched new projects based on the Zcash code.
This is actually "based on obscurity security."
Another major drawback of Zerocash is that due to the need for complex mathematical calculations, anonymous transactions are generated much longer on any powerful computer than any previous anonymity, especially for configurations. For low computers, this process is too long. This makes it impossible to widely use its anonymous features, or it may not be suitable for some less powerful systems, such as mobile devices. Zcash has made significant improvements in its latest Sapling upgrade by using the new BLS12-381 curve, reducing generation time to a few seconds and requiring approximately 40 MB of memory, which makes it ultimately available for mobile devices. However, it is still the most computationally intensive compared to the other anonymous solutions in this article.
Therefore, although Zerocash has the best possible anonymity, it comes at the expense of the total amount, but also includes the following shortcomings: complex pre-trust mechanism, using too new encryption technology, creating anonymous transactions takes a long time .
However, the Zcash team is working on zkSTARKs, an alternative to zkSNARKs, which does not require a pre-trust mechanism and uses encryption algorithms and simpler encryption assumptions. However, so far, zkSTARKS is currently unusable due to its large size, and the computational requirements for creating zkSTARK are still high. There are other interesting variants of zkSNARKs that have not yet been implemented, such as Sonic and Spartan, which solve the pre-trust mechanism in different ways, but it has a set of trade-offs beyond the scope of this article.
7.Mimblewimble
For: Grin, Beam
advantage:
·All transactions are anonymous
·Use perfect cryptography
·Hidden transaction amount
Blockchain can be reduced in size because it only retains UTXO
· There is no problem with reusing addresses
Disadvantages:
· The interaction between the recipient and the sender is required. Unable to leave the address and then wait offline for reception. There are problems with multiparty transactions because parties need to communicate to create a transaction.
· Do not break the transaction links, just blur them, so it is a "bait" model.
• The monitoring network can reveal details of how the transaction was added.
· If there are too few transactions in a block, the anonymity will be greatly reduced because it depends on other transactions to join.
· Cold storage in hardware wallets is difficult to achieve
· Developing smart contracts on Mimblewimble is harder because there is no scripting language and only some of the features can be done through development in "no scripting"
· Relatively early development and sharing of Bitcoin core code to borrow Bitcoin community consensus and integrate it into the infrastructure requires independent development.
Both Grin and Beam are applications of MimbleWimble. Mimblewimble works by two main methods, first hiding all transaction values, and then by trading all the transactions into a large transaction, so that in the block it looks like a huge transaction with many outputs and inputs. View it only from the blockchain, even if there are only a few transactions in the same block, you can only guess which output comes from which input. Mimblewimble also allows another feature called pass-through. If A pays B and then pays it all to C, the blockchain can record A to C without displaying B.
A simpler way to understand this is to compare the trading methods in the trading bitcoin with the trading in the Mimblewimble.
Imagine A being sent to B and C. In a separate transaction, D is sent to E and F.
In Bitcoin, this will be considered
(input) A> (output) B, C
(input) D> (output) E, F
They will also have the value of further trading that makes them unique.
In Mimblewimble, all transaction values are hidden and these transactions are aggregated, so once the transaction is connected in a block, it will look like this:
(input) A, D> (output) B, C, E, F
Now I can't specifically know who sent it to whom!
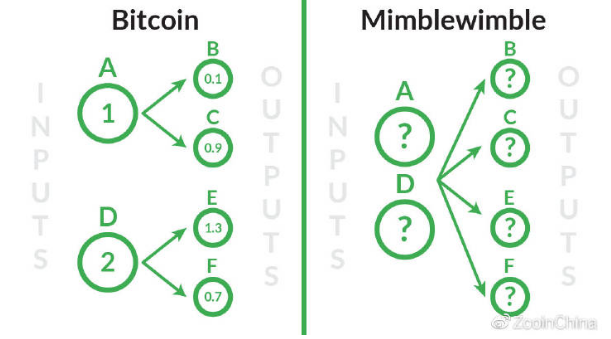
Compare Bitcoin and Mimblewimble trading methods
However, the biggest assumption is that no one is monitoring the network before these transactions are propagated and before they are recorded to the blockchain. With vanilla Mimblewimble, someone can create a malicious node that connects to all the other nodes in the network and record the transaction before they are combined, so that the transaction can be anonymized, which means it uses only one transaction and transaction value except the address. Beyond being hidden, other aspects of anonymity are only equivalent to Bitcoin.
To alleviate this situation, both Grin and Beam use dandelion technology to change the way transactions are traded. Instead of broadcasting each transaction to all peers, the transaction is first sent through a series of randomly selected peers (the backbone phase) before it spreads across the network (diverging phase). Each subsequent node randomly determines whether to continue the trunk phase (90% chance) or switch to the divergence phase (10% chance). Although the transaction is in the main stage, they are also combined with other transactions before extensive broadcast. This makes it more difficult for nodes to fully understand how transactions are connected together. However, it is not a perfect solution, and the way the transactions are still clustered together can still find clues before adding the transaction to the block.
This is combined with the fact that Mimblewimble is also a bait-based system similar to Cryptonote (although it uses different methods to achieve it), it still has the same shortcomings as other "bait"-based privacy systems, where repeated transactions can be further To reduce anonymity, the trading network still exists. In addition, if there are not many transactions in the block, the anonymity will be greatly reduced. As mentioned earlier, proactive monitoring of the network can further threaten anonymity.
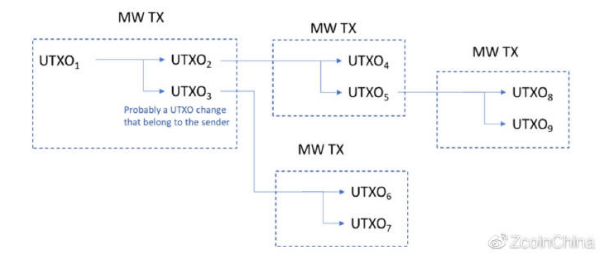
Transaction chart built by tracking MimbleWimble transactions
A major drawback of MimbleWimble is the need for interaction between the recipient and the sender (meaning that the recipient and sender need to communicate directly to convey a blinding factor) and a very different solution that eliminates the address. This means you can't just post addresses on your website, you must always provide new values. This also complicates multi-party transactions, for example, remittances to B, C, D, E in a transaction will require each of these parties to communicate with A prior to transmission. Beam's implementation solves this problem by using a security bulletin board system that allows people to post their messages to Beam's full node so that blindness can be communicated once the user is online, but if this affects privacy, further research is needed. .
In addition, although there is no address, Pedersen's commitment is still unique, so MimbleWimble itself does not hide the transaction map, which means you can still see how the money flows, so it can be considered a "one-off" address. This means that without the dandelion and Coinjoin's additional workarounds, Mimblewimble's privacy is equivalent to Bitcoin, except that the address is used only once and the transaction value is hidden.
Grin doesn't have a scripting language, so implementing smart contracts can be difficult, although "scriptless scripting" development may use similar functionality in specific areas.
With a completely hidden transaction value, Mimblewimble does not provide auditability. It relies on bullet proof/confidential trading to check if any extra coins have been created out of thin air. However, because the cryptography behind it is very mature, its supply auditability is not as big a problem as the Zerocash protocol.
8. Other anonymous programs and why do I like anonymous coins are not analyzed?
All of the blockchain anonymity schemes listed here have been well received by researchers, and various anonymous schemes are easy to understand. However, there are now hundreds of cryptocurrencies, but only a few can truly achieve anonymity. The following are the key factors for the reliability of the new anonymity mechanism:
Ø Can it provide anonymous blockchain?
Some anonymous currencies claim to have anonymous technology, but no anonymous protection is visible on the blockchain. Specifically see below: (the difference between anonymous and hidden IP on the blockchain).
Ø Has the anonymous protection mechanism written by experts been reviewed?
See if their anonymous plans have been reviewed by cryptographers, whether academic papers refer to it, many programs are written by developers or programmers, and they don't have any background in encryption or information security, they implement anonymous technology. The technology is usually not reliable.
Ø Is it just a new name that leverages existing technology?
Some projects rename existing anonymous currency to their own name and issue it as their own name, which is acceptable if they disclose the original anonymous technology.
Ø Is it centralized?
If you rely on you to trust others to protect your anonymous plan, it is usually a bad anonymous plan.
Ø Does the team understand the cryptography behind these anonymous technologies?
Unless you are an expert yourself, it is difficult to determine. Check their team to see if there is a cryptographically relevant research experience on their team or their consultant list.
9. Summary
Each anonymous model has its own interests and trade-offs. We believe that continuous exploration and research on these anonymous solutions will improve the anonymous technology of the entire blockchain.
We strongly believe that the Sigma and Lelantus protocols used in Zcoin provide a very comprehensive anonymity scheme compared to other anonymous solutions. It uses proven encryption technology to provide very strong anonymity while maintaining scalability and scalability. Auditing.
Below you can find a comparison chart of the Zcoin solution with other privacy technologies.
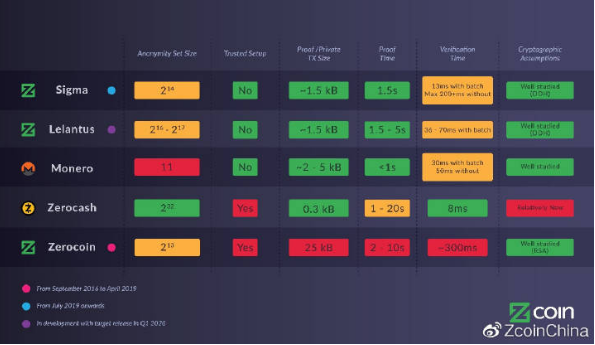
Original: https://card.weibo.com/article/m/show/id/2309404398302274650374 Source: https://first.vip/shareNews?id=2041&uid=1
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Ideal to the left to the right, Grin makes people want to love
- Decentralized Governance: What is the best blockchain governance?
- Bitcoin is a black hole, and the legal currency of these six countries has been swallowed up.
- Babbitt Column | Thinking about the meaning of blockchain from the perspective of reducing transaction costs
- CCF Blockchain Committee S Xueming: In the next three years, the blockchain will be widely distributed in the real economy.
- Should India ban cryptocurrencies? Some officials resigned and the central bank was even charged
- Grassroots victory, Bitcoin became the 11th largest currency in the world





