A picture to understand the blockchain App security system
Blockchain technology has become the most popular technology this year. Say goodbye to the boom of pure crypto asset speculation. This technology is gradually landing or seeking the direction of landing in various scenarios. As the so-called "moisture is silent", in the various industries' attempts on the blockchain, we believe that it will gradually penetrate into a large number of application scenarios, or as the underlying technology, or as a middleware for improving efficiency, or as the front end The components of technology even make full use of the characteristics of credit transfer and value remodeling embodied in the technology, and change the operation of some business models.
With the gradual implementation of this technology, directly or indirectly, blockchain technology will ultimately achieve user value through terminal products. In the era of the mobile Internet, one of the important forms is mobile applications, which are often called mobile apps. .
From a purely technical perspective, mobile phone apps in the blockchain technology application scenario have their universal technical characteristics, but also have special features in combination with the blockchain scenario, which is closely related to the specific application scenario. For example, in the field of digital assets, related mobile applications involve scenarios such as keys, mnemonics, and encrypted asset transfers, which require special security protection. In the future application of blockchain technology such as finance, credit reporting, and government affairs, it may involve mobile applications and related nodes, and even directly participate in the process of the blockchain network itself. The protection of sensitive information involved during this period is even more important. problem.
Compared with the blockchain industry, the development of the mobile Internet is obviously more mature. "Predecessors planted trees and future generations took advantage of the cold." In the early days of the mobile Internet, many "thunders" have been trampled on. At an early age, the entire industry needs further communication and improvement. In Beijing Chain Security's security monitoring of the overall mobile application of the industry, we also found that many mobile applications in the blockchain scenario have not taken sufficient security measures, especially in digital asset-related mobile applications with financial attributes. It can be said that There are many problems.
- "Farewell Hayek": Conjecture on the Development Space of STO in China
- How to seize the breakthrough of the blockchain overpass? Experts and experienced practitioners give answers
- Hainan sets up digital asset trading test area, STO falling from the altar may usher in the biggest turning point
In the "Blockchain Mobile Terminal Security Survey Report" released by Beijing Chainan in May this year, the main security issues reflected by mobile applications in the industry were disclosed.
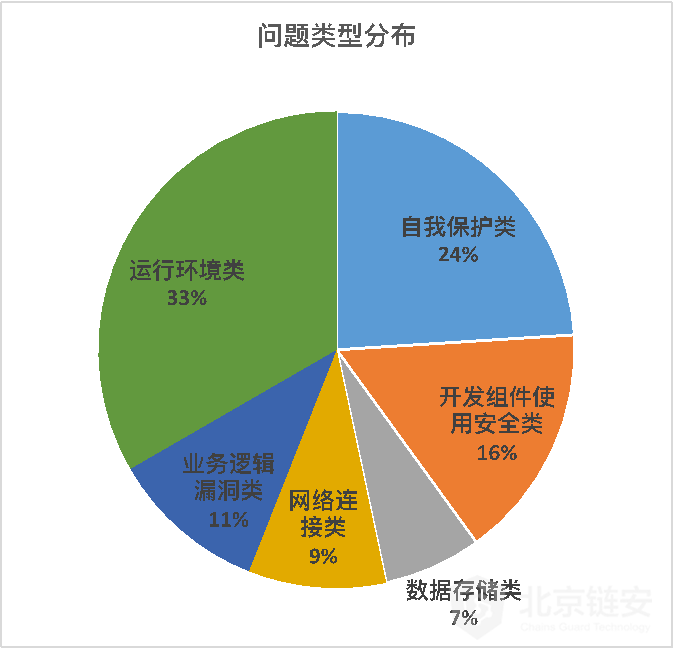
Even in basic security protections such as security testing of the operating environment, self-protection against cracking and tampering, there is much room for improvement in mobile applications in the industry.
And because of the openness of the system, the Android system can be described as a prone place for mobile security issues. So, what is a complete Android mobile application security system? Let us first look at a brain map, which reflects the security concept of mobile applications in the blockchain industry in the eyes of Beijing Lian'an.
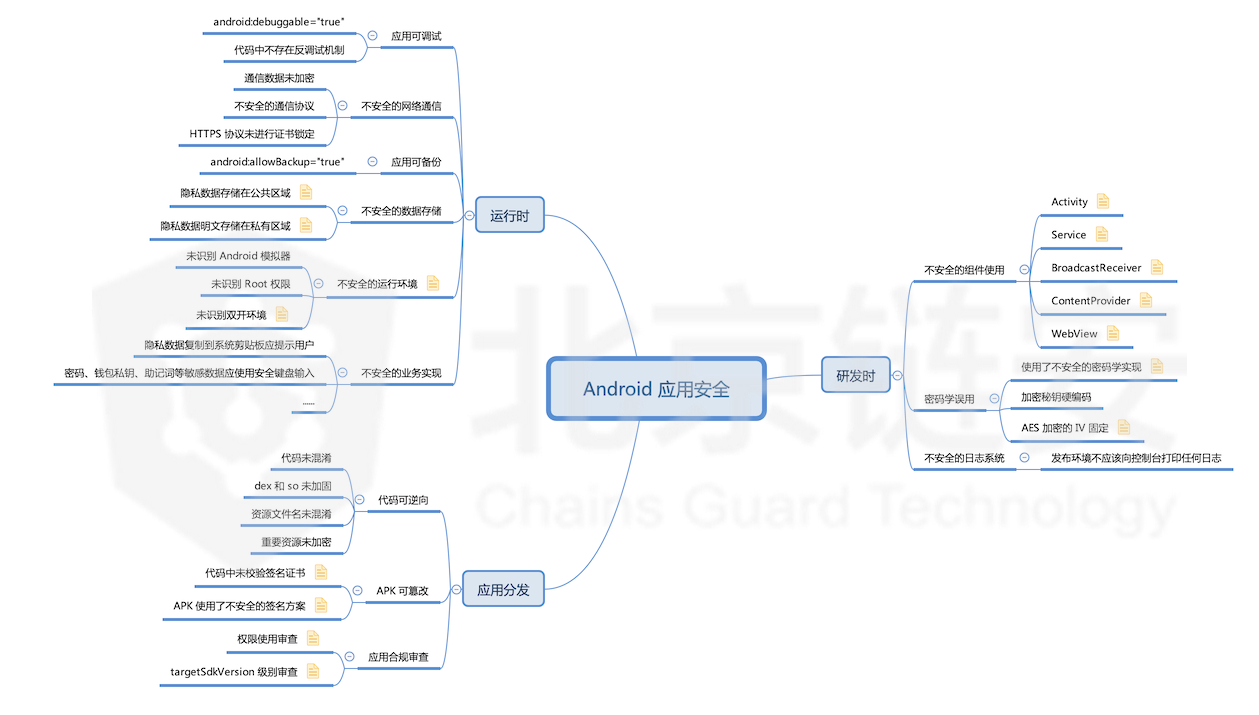
Tips: Friends can download this picture to a computer or tablet for a clearer view.
From this brain map, we can first have a general understanding of Beijing Chain Security's C-side security system, and then let us understand some of the details.
We divide mobile application security from a B-side developer perspective into three phases, namely the R & D phase, the operation phase, and the application distribution phase.
As far as the R & D phase is concerned, we need to focus on security issues in some logic implementation and component use, such as the following links:
1. Use of unsafe components: During the development process, we will use some system or third-party components, which can greatly improve our development efficiency, but improper use of them is also a frequent cause of security issues, such as:
The export of Activity, Service, BroadcastReceiver, and ContentProvider without controlling access permissions may lead to DDOS attack risks.
In the use of WebView, improper configuration policies lead to code execution vulnerabilities, password plaintext storage vulnerabilities, cross-domain access vulnerabilities, and XSS attacks on related code, which may introduce serious security issues such as code injection attacks. Since many apps currently load H5 pages through WebView to implement some functions, the threat of such security issues is very prominent.
2. Cryptographic misuse: For current developers, most of them already have an awareness of data encryption, but we find that in many cases, in practice, developers often customize some weak encryption algorithms, or use some existing encryption algorithms. Algorithms that prove to be insecure, or use algorithms that have insufficient encryption levels in terms of their use cases, can cause the leakage of sensitive user data. Because in blockchain applications, there are often data operations such as keys and mnemonics that are related to user property, the losses caused by this security issue can be very direct.
3. Insecure log design: This is actually a matter of good development habits, that is, in a formal release environment, you should not print any log information to the console. However, we regret to find that the online versions of many apps have not turned off the printing of log information, and even directly printed sensitive information such as passwords.
As far as the operation phase is concerned, after the user downloads and installs the app, the security problems that may occur in the operating environment are often in the operation phase, but the root cause is that the developer has not implemented security precautions, such as the following steps.
1. Application debuggable: App does not take anti-debugging measures, which leads to the possibility that an attacker can figure out the business implementation process behind the app by decompiling and debugging its App, thereby setting the attack point.
2. Application can be backed up: The app can be backed up to another phone as a whole, including its data such as user authentication, so that an attacker can directly perform related operations as the user.
3. Unsafe operating environment: Apps take for granted that they are running in a normal and safe environment. In fact, there are three types of operating environments that may cause your App to be attacked:
- Rooted Phone
- Android emulator
- Virtual App, MultiDroid, DroidPlugin and other dual-open environments
If you do not detect the current environment of the App and let it run directly, and perform services such as registration, login, and transfer, it may expose users to attacks.
Of course, we cannot ignore the security vulnerability issues of the operating system itself, such as the recent StrandHogg vulnerability. Attackers who use this vulnerability can disguise legitimate applications to request permission permission and do whatever they want in your system. For this type of security problem, the corresponding security situation awareness service is even more needed to obtain the latest information in a timely manner, remind users, and perform necessary security upgrades on their own apps.
4. Insecure data storage: App's private data for users, especially data related to user privacy and property security, if stored in the data public area, is obviously a high-risk data processing. At the same time, we also see that some apps store this kind of data in private areas, but they also take it for granted that this is a safe place that attackers cannot reach. For plaintext data storage, these practices will threaten user data security.
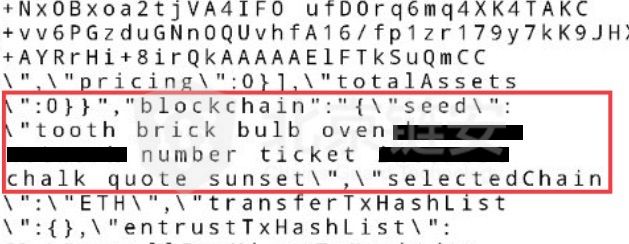
The above picture is a mnemonic stored in the wallet in plain text. I believe that when you first use a digital wallet, you will see the app "sizzling" to remind you not to take pictures, do not exist locally, find a piece of paper to copy, but some wallets It leaves these mnemonics unarmed.
5. Insecure network communication: The key business of blockchain apps mostly involves communication with the server. This process must involve the transmission of some sensitive data, such as the use of insecure communication protocols, which are not encrypted during data transmission. Although some developers consciously use a secure communication method such as HTTPS, they do further security measures such as certificate locking.
6. Insecure business implementation: For blockchain applications in different business scenarios, there are their own business implementation methods, and there are also potential security risks that need attention during the period. In some common scenarios, we find that there are some general problems with apps in the industry, such as the use of a secure keyboard for passwords, private keys, and mnemonics, and the use of a system clipboard with potential security risks. In this case, The user's operation can be easily monitored by an attacker to obtain sensitive data.
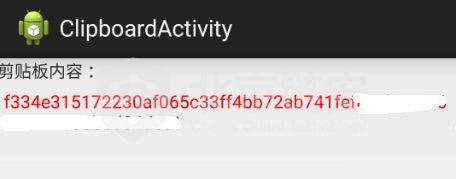
In the example above, the user's private key information is obtained by listening to the clipboard event
Finally, we need to pay special attention to the application distribution stage, because after the development of blockchain applications, they will always be spread through the application store, official website, community, IM and other channels. The security issues in this process are often ignored. Here we remind the development Authors are concerned about the following issues.
1. The installation package can be tampered: If the developer adopts an insecure signature scheme, or the corresponding verification is not performed in the code, then the application installation package you released will be unpacked by the attacker, insert the attack code, and repackage it to The risk that the original App was released in the name will not only attack users such as phishing and Trojan horse implants, but also damage the reputation of developers.
2. Code reversibility: Code reversal technology is a technology that can parse your App code to run logic based on executable files. This type of technology allows you to make your original black box logic implementation public, including some secrets. It's about safe operation. After the attacker understands these logics, it is naturally possible that through further technical means or bypassing some code logic or implanting malicious code, recompilation and packaging will turn your App into a harmful application.
3. Application compliance check: Whether it is published in the store or in some industry application areas, there is a series of compliance reviews on the App itself, such as the use of operating system permissions and the specification of business processes, which need to be done during the App development process. deploy.
If we do a good job of mobile application security from the above points, the probability of your app being attacked and tampered will be greatly reduced.
As a developer, you may also be confused. The above security system involves too many security points. What specific measures should be taken to implement these security measures in your own products?
As a user, you may also be wondering what harm will happen to so many security issues mentioned above in the App you use? What is the probability that such a security problem will occur on an app in the blockchain field?
Next, in this "Mobile Application Security Talk" series, we will introduce related security issues one by one, including how they are used, the harm they cause, and measures to prevent these risks, and work together to create blockchain applications. Scenarios, secure mobile applications.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Chinese Blockchain Enterprises Capture US Exchanges?
- The truth about blockchain employment: higher thresholds, fewer job applicants, high salaries or history?
- Beginner's Guide: Five dimensions to take you through the chaos of the blockchain
- Singapore government-backed accelerator Tribe announces $ 15.7 million funding to support blockchain startups
- Blockchain redemption guide: stay away from speculation and cultivate value awareness
- Gong Ming: Crypto War, Blockchain Technology Road
- Is South Africa's central bank introducing new cryptocurrency regulations?