Bitcoin as ransom, WannaRen ransomware hits twice
Author: Ma Chao
Source: Procedural Life
Editor's Note: This article has been deleted without changing the author's original intention.
Recently, a new bitcoin ransomware virus named WannaRen has appeared on the Internet. Similar to the previous "WannaCry" virus, the "WannaRen" virus will encrypt almost all files in the system after it invades the computer. Pay a ransom of 0.05 bitcoins.
- "Digging" 500 years to recover the cost of equipment? V God calls HTC mobile mining a fool's game
- Learn about Utreexo, an improved MIT Bitcoin solution in 5 minutes
- Babbitt Column | Essential Knowledge of Encrypted Digital Currency Wallet: Divide Wallet Types and Their Advantages and Disadvantages by Terminal

There are currently two variants of the WannaRen virus, one through text and the other through ransomware messages. Unlike the way that the previous generation of ransomware WannaCry combined with eternal blue vulnerabilities to quickly spread on the intranet, WannaRen ransomware did not use RDP, SMB and other high-risk vulnerabilities to actively spread. Therefore, the destructive power of WannaRen is relatively limited, but it does not rule out that subsequent variants of the virus will use the "eternal black" series of vulnerabilities to conduct intranet penetration attacks. According to the latest report, the download link of the open source editor Notepad ++ provided by a well-known domestic download site was found to be bundled with the code associated with WannaRen, making the ransomware likely to undergo a second outbreak through the domestic download station.
The author checks the wallet used by the WannaRen virus 1NXTgfGprVktuokv3ZLhGCPCjcKjXbswAM to check the wallet used by the attacker, and has not yet received the ransom. Fortunately, the author of WannaRen has proactively released the decryption key and released a non-toxic decryption tool, but the effectiveness of the decryption tool has not been confirmed.
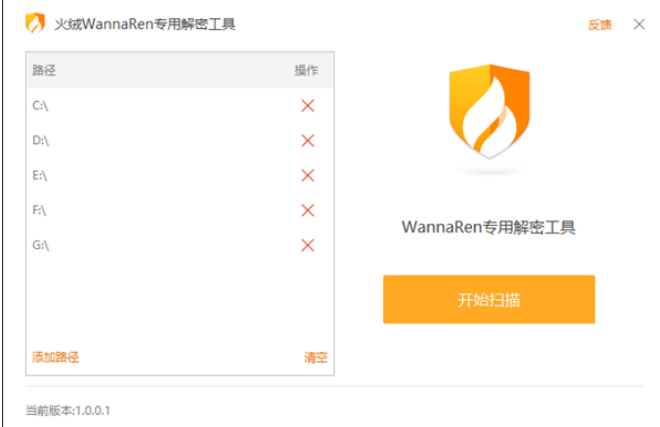
The WannaRen virus is currently only available in Chinese, so the author estimates that this is properly a domestic virus. The large-scale spread of WannaRen mainly relies on forging other tools to deceive downloads.
Why does ransomware always prefer Bitcoin?
Bitcoin's surge in 2017 is directly related to the WannaCry ransomware global outbreak. WannaCry has attracted 300,000 users in at least 150 countries, causing a global loss of $ 8 billion and affecting finance. , Energy, medical and other industries, causing a serious information security crisis. In China, WannaCry takes advantage of the horizontal propagation characteristics of the intranet to make the campus network bear the brunt, and suffers serious damage. A large amount of laboratory data and graduation designs are locked and encrypted. Many scientific and technological institutions have to buy bitcoin to pay ransom in order to retrieve relevant data files. However, due to the limited blockchain transaction capacity of Bitcoin, the transaction limit per second does not exceed 10, and the sudden transaction volume brought by WannaCry is also considered to be one of the incentives that led to the fork of the Bitcoin blockchain network. .
However, it is awkward that even if a ransom is paid, users cannot recover damaged files, and WannaCry is notorious for this. And this is not the first time Bitcoin has been used by hackers. CryptoLocker, which appeared in 2013, is the initiator of Bitcoin ransomware. CryptoLocker will masquerade as a legitimate email attachment or .exe format file. If activated, the malware will use RSA public key encryption and AES key form , Encrypt specific types of files on local and internal networks; and the private key is held on a server controlled by the CryptoLocker producer. If you pay bitcoin within the prescribed time limit, you can decrypt these files, otherwise the private key will be destroyed and the damaged files can no longer be recovered. So at this point CryptoLocker is more stolen than WannaCry, at least collecting money can help users recover files.
I saw a large number of articles on the Internet that said that ransomware such as WannaCry and CryptoLocker chose Bitcoin because bitcoin transactions cannot be tracked, but this statement is more biased. Bitcoin is essentially a distributed account. In this book, everyone can find their transaction information through the extorted bitcoin address like the author, so bitcoin is traceable.
The anonymity of the Bitcoin account is the reason why it is heavily used by hackers. The emergence of bitcoin, especially its anonymity, also poses new challenges to the anti-money laundering goals of regulation. The supervision method for the existing real-name financial account system is certainly not applicable to bitcoin. The lack of regulatory anti-money laundering is also the main reason why hackers currently prefer Bitcoin as a ransom.
Ransomware development trends
Viruses are also open source: In the second half of 2015, Turkish security expert Utku Sen released an open source virus named Hidden Tear on GitHub (https://github.com/utkusen/hidden-tear)
The emergence of Hidden Tear is of great significance. It is only 12KB. Although it is small, the sparrow is small and full of organs. This software has excellent design in the aspects of propagation module and destruction module. Although the author Utku Sen has repeatedly emphasized that this software is to let people know more about how ransomware works, its open source as ransomware has caused a lot of controversy. This project is currently hidden on Github, but you can still get the source code after sending an application to the author. After reading the source code of Hidden Tear's ransomware, the author also suddenly realized that the original programming ideas and methods are really unique. Destructive thinking and constructive thinking are indeed completely different styles. It can be said that the emergence of Hidden Tear objectively also allowed ransomware to develop greatly.
Viruses are also industrialized: In 2015, a ransomware development kit called Tox was officially released. Through the registration service, anyone can create ransomware. The Tox management panel will display the number of infections, the number of ransoms paid, and the overall income. The founder of Tox charges 20% of the ransom. However, the popularity of virus exploit kits, especially after "The Shadow Brokers" (Shadow Brokers) announced the tools of the formula hacking organization, the vulnerability attack tools were widely used by hackers, and the ransomware was also widely spread. The combination of destructive viruses and worm propagation not only extorted a lot of money, but also created large-scale sabotage operations that affected the world. At this stage, the ransomware has shown a trend of continued industrialization. Throughout the chain, each link has a clear division of labor, and a complete ransomware attack process may involve ransom virus authors, ransomware implementers, communication channel distributors, and agents, and ultimately profit.
Antivirus tips
1. Close high-risk port 445: We see that security vulnerabilities such as the eternal blue used by WannaCry are all vulnerabilities that use the SMB protocol, and spread wildly in the local area network, that is, as long as the virus has captured a machine under the same WIFI, then other computers Will also be successful. The closing of port 445 is the most effective countermeasure.
2. Update patches in a timely manner: Running Windows Update to repair patches is also an effective protection method.
According to the author's observation, the situation where the defensive party is dominant in information security is slowly changing as the situation changes, so the industry needs to pay great attention to new trends in security. , In case the tragedy of the new crown virus occurs in the IT world.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Observation | How have Chinese insurance technology giants used blockchain to transform?
- New Path of International Cooperation for Chinese Enterprises Against Globalization: Blockchain Industry Alliance
- This is the real blockchain! Tens of billions of dollars are put here, 4 industry experts bring you first-line experience
- FBI warning: under the new crown epidemic, beware of four encryption scams
- QKL123 market analysis | New days of global diagnosis? American Oolong! Data those things (0414)
- WBF founder Bella Fang: no evil + long-termism, the correct position of the encrypted derivatives track 丨 chain node AMA
- Introduction to Blockchain | How Does DeFi Liquidator Work?





