Research | Blockchain empowers traditional video security surveillance industry
This article was authorized by the author "Murphy's Time" to authorize Babbitt, please do not reprint without permission.
After decades of development, the video security surveillance industry has gradually developed into a traditional industry with high market maturity and large scale. Its core product, the IP-based network video surveillance system, has become the core of maintaining social security and implementing comprehensive social governance. The application system is also an important part of the construction of a city public safety system that implements strong police in science and technology, realizes overall joint defense, joint control, and rapid response.
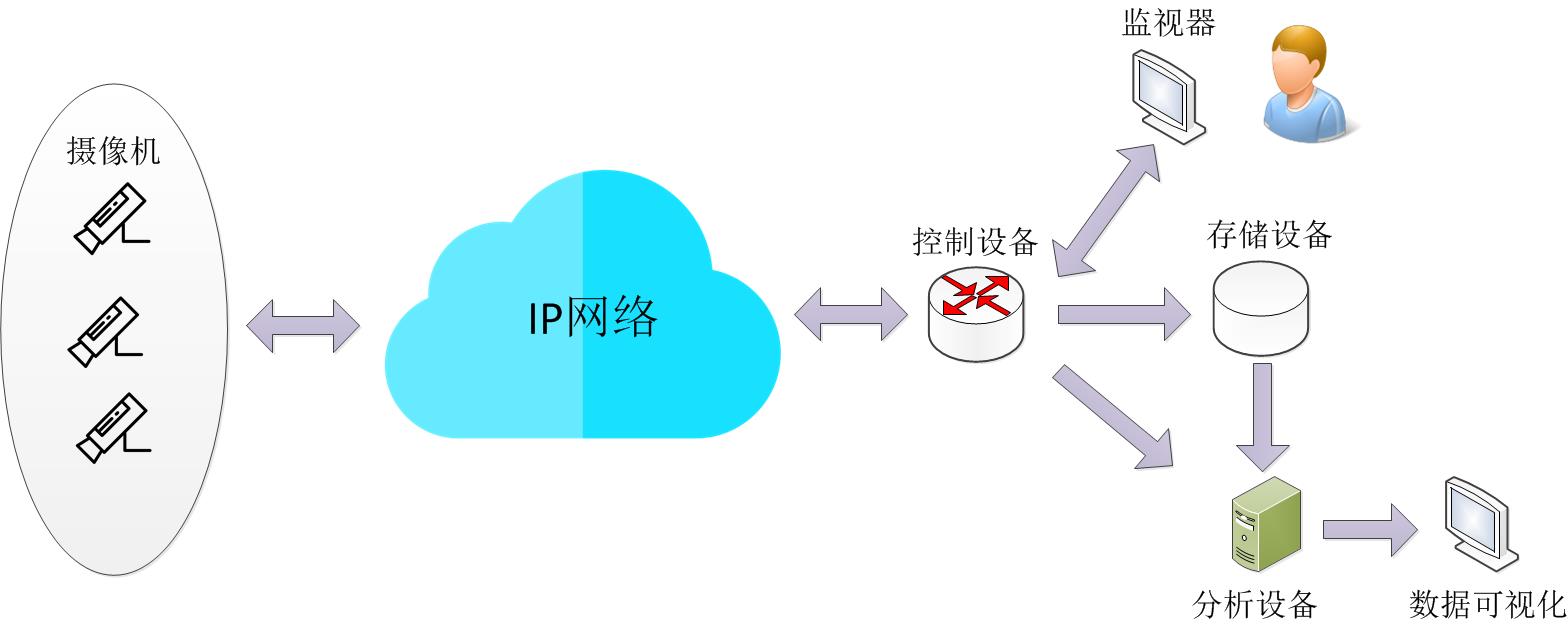
The traditional network video surveillance system is composed of five parts: camera, transmission, control, display and storage. The cameras deployed at each monitoring point transmit the video images collected on site to the control device through the IP network, and the control device distributes the video to the corresponding monitor and storage device. Surveillance personnel can issue commands to the camera through the control device to control the gimbal to adjust the angle of the camera up, down, left, and right, and adjust the zoom of the lens, etc. Switch between stations. The real-time video stream can be divided into three channels. One channel is sent to the monitor. In addition to displaying the real-time images of each monitoring point, the monitor can also receive and process real-time alarms, such as foreign objects breaking into the delimited area, etc .; the second channel is sent to storage The device performs storage backup; the third way is sent to the analysis device, which can analyze the video content using artificial intelligence technology, such as human behavior recognition, face recognition, vehicle recognition, etc .; the video in the storage device can not only play back the video , Editing, and other operations, you can also perform post-analysis on video content, such as personnel / vehicle trajectory analysis.
- Analysis | Bank attitudes are negative, German cryptocurrency policy is "good" than expected
- BCH and BSV are halved, and the hash rate drops significantly
- Automated market maker AMM is on fire, but you need to understand the risks of providing liquidity
Traditional network video surveillance system
The traditional network video surveillance system has a serious drawback, that is, the video data is controlled by the central organization, and it is easy to be tampered with or deleted. For example, in recent years, there have been many accidents in kindergartens in China. We can see from the news that video surveillance materials are generally stored in the garden. When law enforcement agencies and parents request to view video surveillance, the relevant responsible person will always cause surveillance video loss or surveillance video due to camera damage, hard disk damage, etc. The lack of some key pictures to evade, resulting in law enforcement departments can not effectively obtain evidence, and then can not quickly and effectively punish criminals. Although in some cities, real-time videos of kindergartens are required to be transmitted to the regulatory authorities for storage at the same time, it is not easy for parents to view the videos.
In view of the disadvantages of traditional network video surveillance, the author of this article briefly introduced a video surveillance system based on blockchain technology in the book "Zero Basics Blockchain". The system can effectively prevent the loss of video data, and realize the detection and recovery of video data loss, as well as the extraction of video, thereby providing a strong support for investigation and forensics and a strong guarantee for social supervision.
Taking the application of this system in the kindergarten scenario as an example, this article will introduce the system's basic architecture and various functional module components in detail.
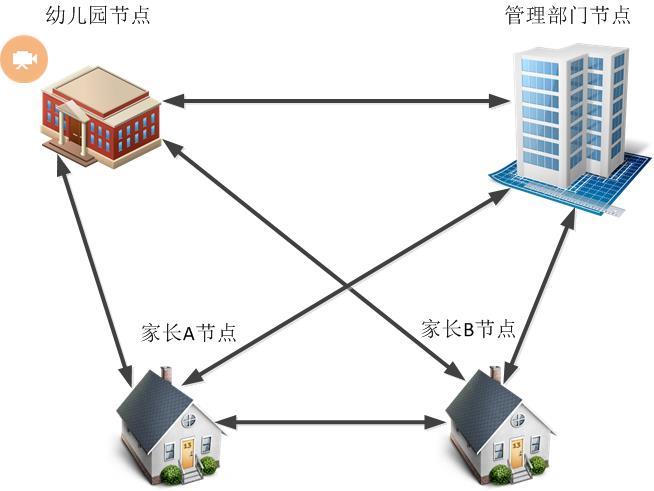
The whole system is based on the alliance chain architecture, in which kindergarten, management department, parent A and parent B (assuming there are two parent nodes) are the nodes in the alliance chain, which together form a P2P video surveillance network. The system establishes multi-level management authority authentication, the management department decides the entry of the kindergarten node, and the kindergarten node determines the entry of the parent node. The video data source is acquired by the camera installed in the classroom of the kindergarten, and the generated video data is sent to the node of the kindergarten, but also to the management node, the parent A node and the parent B node.
Each time these four nodes receive video frame data, they must first check the security of the frame data to prevent the video frame data from being damaged or malicious illegal data from entering the network. Check the passed video data, and the node will put it into the video frame At the same time, several video frames are extracted from the video frame pool according to the sequence of video generation to construct a video block, and waiting to be recorded into the video blockchain. This system abandons the traditional alliance chain's way of selecting bookkeeping nodes, because the traditional alliance chain still belongs to multi-center management. Once the data is managed by multiple centers, the authenticity of the data will be questioned. In addition, there is no hard requirement for real-time processing of the data in this system, so these four nodes use the proof-of-work mechanism used by Bitcoin to compete for accounting rights fairly. The nodes that obtain accounting rights have the right to propose their own video area. The block is written to the video blockchain, and the video block is broadcast to other nodes, and after verification by other nodes, they are synchronized to their respective local video blockchains, thereby achieving synchronization of video data across the entire network.
The above is the general flow of video surveillance based on blockchain technology. The general design scheme is introduced below.
(1) Establishment of video creation block
Before the generation of classroom surveillance video data, first create the genesis block of the video blockchain, whose structure is shown in the following figure:
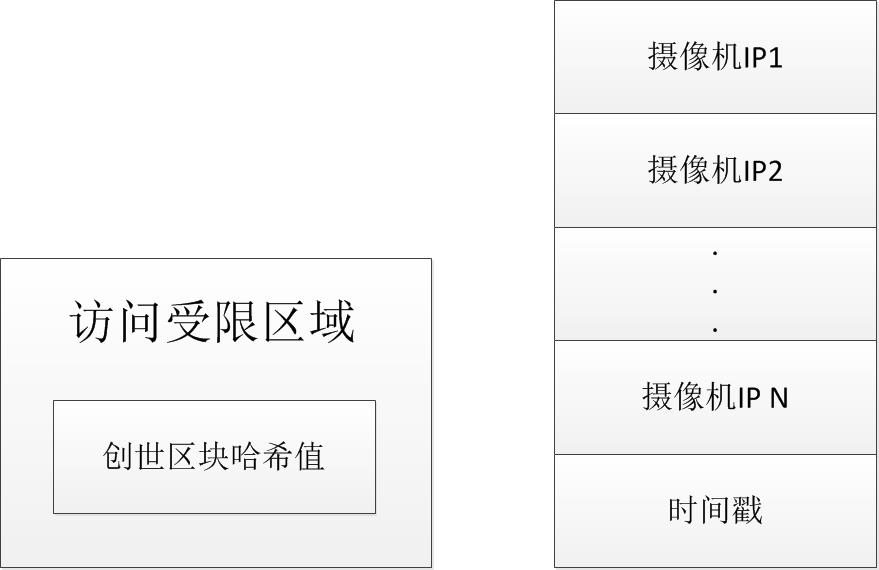
Video Genesis Block
The genesis block is divided into two parts, one is the IP address of each camera , and the other is the time stamp, which is the creation time of the genesis block. Calculate the hash value of all camera IP addresses plus timestamp, which is hash (camera IP1 || camera IP2 ||… || camera IP N || timestamp). Place the hash value in the restricted access area, which can effectively protect the IP and time stamp of each camera from being tampered.
(2 ) Data structure of the camera's head block
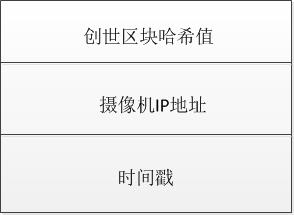
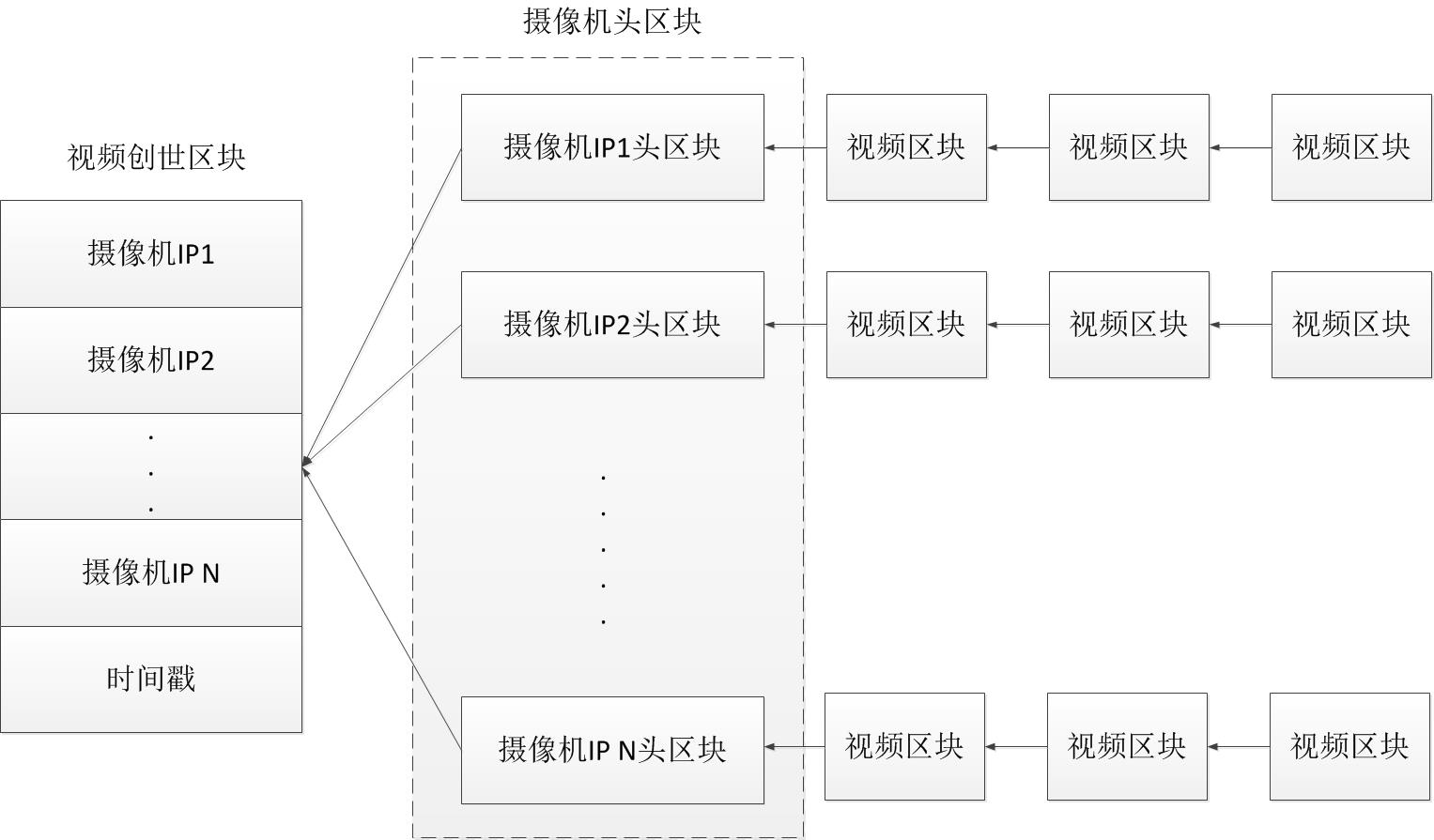
This system allows each camera to create its own video block chain. The video block chains point to the same video creation block. The first block on each chain is called the camera head block. Its data structure is Composed of three parts:
①The hash value of the genesis block: abbreviated as pre_iniBlock. The hash pointer points to the video creation block.
② Camera IP address: abbreviated as camera_ip. Reflects geographic location information and is used to identify cameras that collect video data.
③ Timestamp: Abbreviated as timestamp. Indicates the time when the header block was created.
In this solution, the video blockchain does not only contain a blockchain, but creates corresponding video blockchains based on different camera IP addresses. The subsequent video blocks generated by each camera can be based on the camera IP address. Link to the corresponding video blockchain. Each video blockchain points to the same genesis block, as shown below.
(3) Video data structure
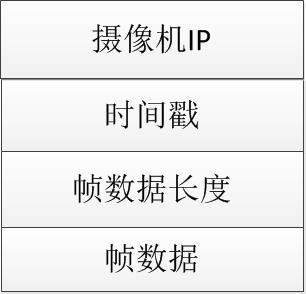
In addition to a frame of complete data, the video data structure also contains the camera IP, time stamp, and frame data length. As shown below. The camera assembles the frame data, camera IP, time stamp, and frame data length into video data, and sends it to the video surveillance network. Each node receives the video data.
(4) The security of node detection video data
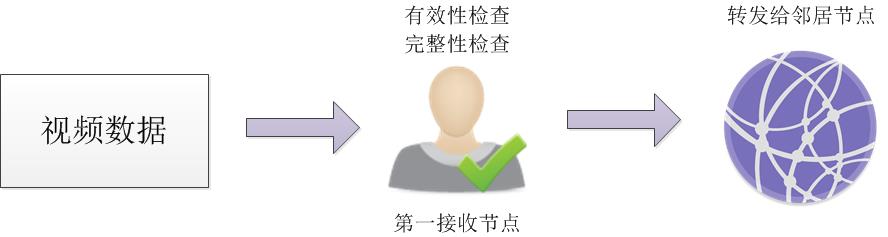
When video data is propagated in the network, it is inevitable that due to network problems, all video data will be lost or key frame data will be lost. If all are lost, then later can be solved by synchronizing video data from other nodes, but if it is the second In this case, an error will occur when the video data is restored in the later period; in addition, it is necessary to prevent illegal data from spreading on the network. Therefore, the node needs to detect the security of the video data, including legality and integrity. Legality indicates whether the video data originates from a legal camera, that is, to check whether the camera IP in the video data belongs to the camera IP set in the video creation block, if it is illegal video data, it is discarded by the node that was received first, This can effectively prevent illegal video data from flooding the network, causing network congestion; integrity, that is, the integrity of a frame of data.
According to the structure of the video data, it can be judged by comparing whether the length of the frame data in the video data is the same as the length of the received frame data. Broadcast to the neighbor node, the neighbor node receives the alarm information, and locates the video data in the local video frame pool according to the camera ip and time stamp. If the data is located in the pool, it means that the neighbor node has verified that the video data has passed Security detection, at this time, the video data is sent to the alarm node, and the alarm node restores the frame data according to the data; if the video data is not located, there may be two reasons, one is that the neighbor node also received a bad frame Second, the video data has not reached the neighbor node.
For the former, neighbor nodes will also record into the alarm pool when they receive a bad frame, so after receiving the alarm information, if the video data is not found in the local video frame pool, go to the alarm pool, if the alarm pool exists, then no longer Forward this alarm information to prevent network flooding; for the latter, the neighbor node will forward the alarm information to its neighbor nodes. After the alarm node receives the correct video data from other nodes, it will check the security again. If the detection passes, the bad frame information will be deleted from the alarm pool. If the response data of multiple nodes are consistent, it is basically confirmed that the recovered data is correct and reliable To prevent malicious nodes from replying with error frames.
After the node checks that the video data passes, it forwards the video data to its neighbor nodes, and the neighbor nodes also need to perform security checks.
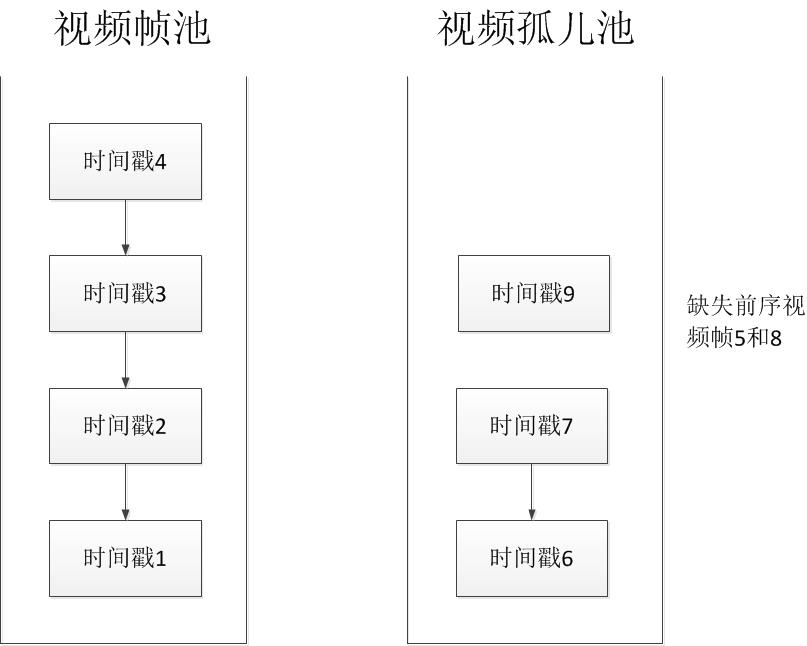
(5) Video frame pool and orphan pool
Once the classroom camera monitoring is started, it will continuously push the video stream to the monitoring network . The video data that passes the security detection is placed in the local video frame pool by the receiving node, arranged in order of timestamp , this is to enable timely Detect whether there is video data loss, prevent the video cannot be recovered later, especially the key frame is lost. Because there may be a delay in the P2P network, the video data of the subsequent time will arrive at the node first. If some video data does not have the previous video data, it will be temporarily placed in the video frame orphan pool. We can assume waiting for a certain period of time. If the missing video data has not been received after this period of time, the missing information will be recorded in the local alarm pool, and the alarm message will be broadcast to the neighbor node. Does the video frame pool contain the video data? If so, will the data be sent in the past and will not forward the alarm message. If the video frame pool does not exist, check the alarm pool. Once the alarm pool also exists, the alarm message will not be forwarded.
(6) Alarm pool
The alarm pool mainly stores the alarm information sent by the node. When the node receives a bad frame or does not receive video data, it will write the alarm information into the alarm pool and broadcast the alarm information throughout the network. This system designs a central process that centrally handles alarms. It will periodically detect the alarm pool of each node. If all the network nodes receive bad frames or no video data for a period of time, it is necessary to consider whether there is a network problem .
After the node re-synchronizes the video data, it will delete the related alarm information from the alarm pool and notify the neighboring nodes to delete the corresponding alarm.
(7) Video block construction
The node extracts video data from the video frame pool according to the timestamp sequence to construct a video block. Assume that the video data within 1 minute is constructed as a block. The data structure of the video block is composed of the video block header data structure and video data. Merkel tree structure composition . The video block header data is shown below:
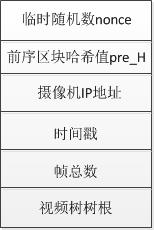
The video block header data is mainly composed of six parts. For the design of other fields, please refer to the Bitcoin block header data structure introduced in "Zero Fundamental Blockchain":
①Temporary random number nonce: Temporary random number used for proof of work algorithm;
② The pre-block hash value pre_H: a hash pointer to the pre-video block; for the first video block, it points to the camera head block to which the video block belongs;
③ Camera IP address: abbreviated as camera_ip. Reflect geographic location information, used to identify the camera that collects video data;
④Timestamp: Abbreviated as timestamp, the time when the video block is generated;
The total number of frames: abbreviated as frameCount, the number of frames generated by the camera in one second, generally 24 frames, then one minute is 1440 frames. The number of frames can be determined according to the actual situation. This data is used to detect whether the number of frames attached under the Merkle tree of video data is complete;
⑥ The root of the video tree: abbreviated as root_hash, calculate the hash value of 1440 video data generated within 1 minute, and constitute the first leaf node of the Merkel tree. Then the leaf nodes of the first layer are grouped and combined in twos, and the hash calculation is performed again, and the calculation results form the leaf nodes of the second layer. The leaf node finally obtains a single hash value, which is the root node of the tree, thus forming a Merkel tree structure, as shown in the following figure:
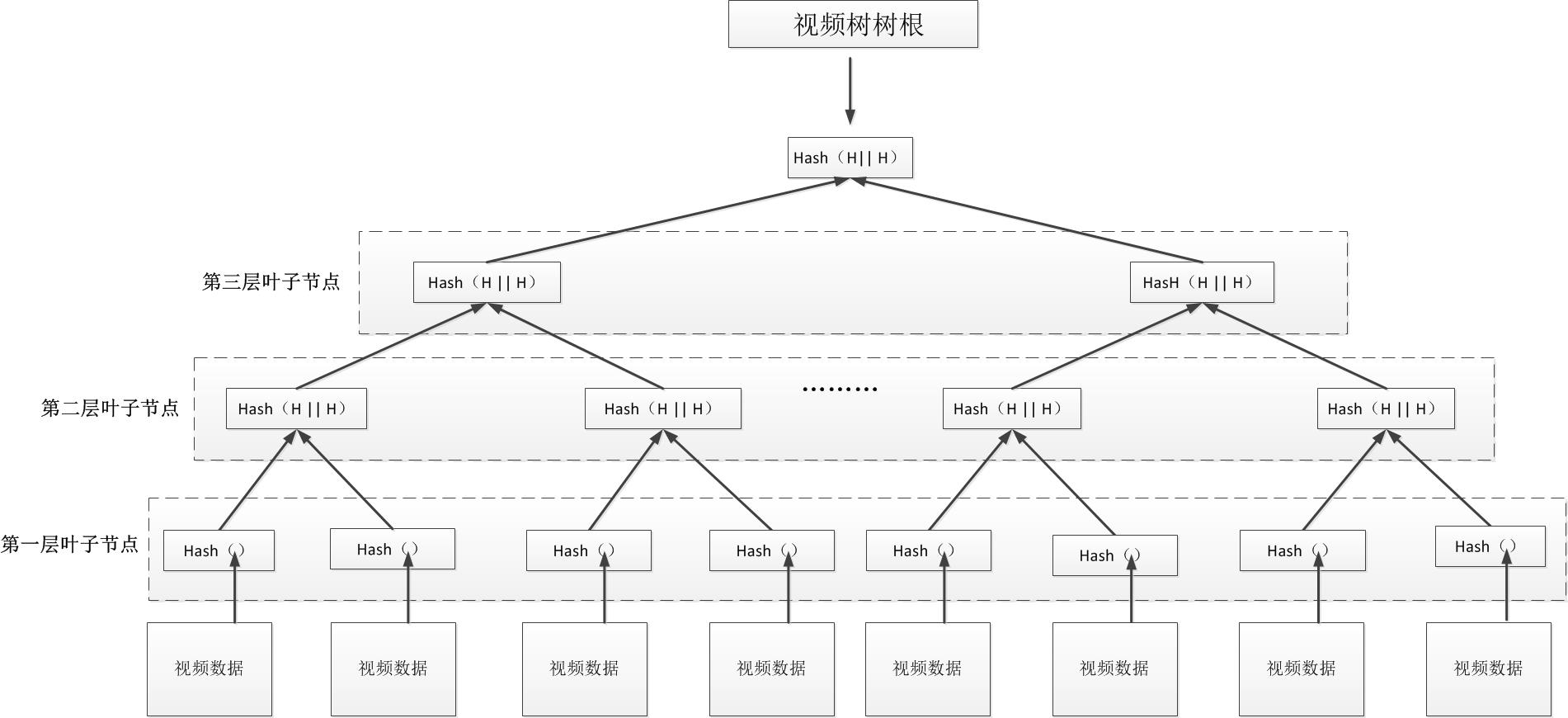
The system requires that all the video data extracted from the video frame pool is time-continuous video data to form a video block. If the video data in the video frame pool does not arrive or is lost, it will cause a discontinuous time, then the video information extracted later will not complete.
(8) Nodes compete for bookkeeping rights in blocks
Each node uses a proof-of-work mechanism to compete for the accounting power of the block. The node that obtains the accounting power hangs the block it claims on the video blockchain of the node, as shown in the following figure. At the same time, it broadcasts the blocks it claims to other nodes through the P2P network, which ensures the data synchronization of each node and the high consistency of the data content.
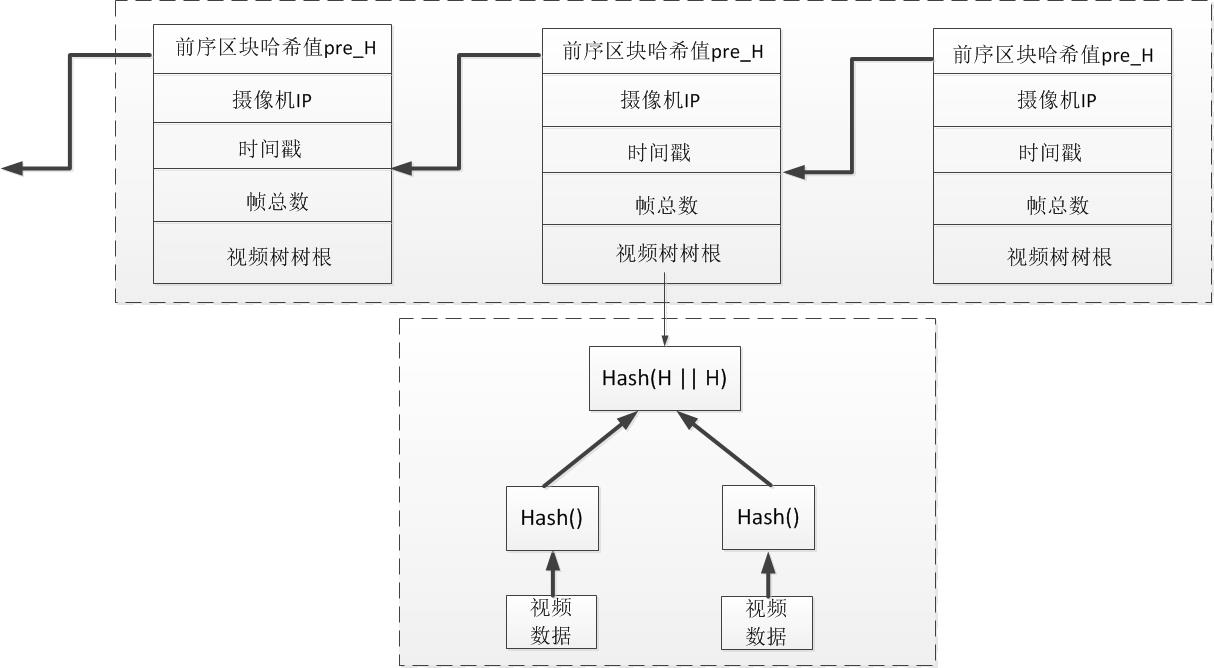
(9) Verification of video blocks by nodes
After the node receives the video block, it stops the ongoing proof-of-work calculation and verifies the received video block, mainly to verify whether the block header meets the proof-of-work requirements, and secondly to verify the video data in the block Whether the camera IP is the same as the camera IP in the block header, whether the total number of frames is correct, whether the time stamps are continuous, whether the frame data is correct and complete, and whether the frame data is the data in the local video frame pool, and then hang the verified block Into the local video blockchain, at the same time update its own video frame pool, delete the video data that has been linked.
In the video blockchain, the steps to pass the verified block to the previous block are as follows:
① The node finds the corresponding blockchain link through the camera IP in the block header data structure. If the corresponding blockchain is not found, it discards and generates an alarm message, and the system prompts that the camera IP may be modified.
②Check whether the timestamp in the newly received block header data structure has time continuity with the timestamp in the preamble block header data structure. If the time is not continuous, put the block into the video block orphan pool Here, wait for the parent block to arrive before hanging up.
Through the above two steps, an association relationship is formed between the previous block and the current block through the hash value.
(10) Extract video from the video blockchain
Enter the camera IP and time range of the video to be extracted, traverse the blocks on the video blockchain, find the corresponding time period by matching the time stamp of each block, and then extract and store it in each block within the time period The video data of the video is restored to the original video in chronological order.
(11) Optimization plan
In the previous scheme, the video frames are stored directly in the local blockchain of the node, but the amount of video data generated by the camera every day is very large, which will cause a lot of pressure on the storage of the local node, you can consider the video data It is placed in the cloud, and only the index value of the video data in the cloud and the hash value of the video data are stored in the video blockchain. The index value is used to locate the cloud video data, and the hash value is used to detect whether the video data extracted from the cloud complete. At the same time, in order to prevent the data stored in the cloud from being tampered with, you can consider using the key of each node to lock the cloud data. The modification of cloud data requires the consent of all nodes, and the data read permission can only provide the key to access the node Yes .
In addition, in order to prevent the video data from being tampered with by the node that has the accounting right, the accounting node can use its own private key to sign the proposed video block, and other nodes extract the corresponding video data from their local video pool. Combined with the public key provided by the accounting node to verify whether the video data has been tampered with.
The above is just a general idea of the design of a video surveillance system based on blockchain technology. If you are interested in blockchain technology and the basic principles of Bitcoin, welcome to refer to the book "Zero Fundamental Blockchain" by Tsinghua University Press .
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Market analysis: BTC rebound is still weak, pay attention to the downside risks in the short term
- On-chain data scan in March: Where did all these USDTs go in a single month with more than 1.3 billion additional issuances?
- Zhu Jiaming: 2020 will be an important year for the integration of blockchain and industry
- Babbitt Cloud Summit | Where is the path to open finance to crack the bottleneck of DeFi development?
- The latest report of the European Parliament: Crypto assets are not the same as CBDC. Global stablecoins will have a far-reaching impact (full text download)
- The anti-epidemic supplies company was fined for returning goods, this pot blockchain does not back!
- Foreign media views | Digital RMB is ushering in a golden stage, the People's Bank of China actively promotes legal digital currency






