BTC block reward is about to be halved, will its security rate be halved?

- People think that halving the issuance of BTC is a bullish event, but ignore its hidden dangers of network security;
- No matter how the U.S. dollar appreciates, the BTC safety rate (divided by the miner's income divided by the value of the network) will be halved, which may lead to potential speculative attacks;
- To keep the BTC safety rate at the level before halving, the fee income must increase by about 4300%.
BTC's "halving" will take place in May, sparking active discussions around the application of efficient market hypotheses. BTC halving is usually considered a bullish event, and the focus of the debate is mainly on the pricing range for block reward halving.
Although some analysts have found advantages in these discussions, these predictions are ultimately speculations and difficult to prove or refute. Without a basic valuation framework, it is impossible to determine whether the trading price of BTC is higher or lower than the fair market value, and the appreciation or depreciation after halving is likely to be a function of completely orthogonal factors.
Therefore, we think that the discussion related to halving is best focused on the deterministic fact: In addition to the total destruction of the network, at a block height of 630,000, the BTC reward will drop from 12.5BTC to 6.25BTC. Excluding the miraculous rebound of the BTC fee market, the BTC security rate (SR) will be halved. Contrary to the general halving narrative, this represents a fundamentally bearish development of the BTC network and its existing stakeholders.
Before delving into the safety rate itself, it's worth briefly discussing the importance of safety itself. In theory, the value proposition of the blockchain network stems from BTC's credible neutral attributes, which are mainly manifested in immutable transaction history and censorship-resistant transaction processing. This is different from a ledger recorded by a single organization or enterprise, in which the transaction history and service access rights are unilaterally controlled by a limited party at its discretion. In order for the blockchain network to realize its value proposition, the cost of obtaining majority control must be increased. 

Safety rate
- Industry Blockchain Weekly 丨 Blockchain writes 7 provincial government work reports, Baidu and Tencent enter A shares
- Babbitt weekly election 丨 Do you panic when 2020 starts like this?
- Decentralization cannot be done in one step, A16z talks about three factors for the success of cryptocurrency projects
There are several different ways to quantify security. The first (and most basic) technique is computing the security budget of the network. Assuming that the existing miner is honest, the cost of the miner is gradually equal to the income of the miner, and we can declare that the cost of obtaining most hashing power is equal to the income of the existing miner. The security budget gives us a nominal security value: for BTC, this is equivalent to approximately $ 13 million per day, or $ 5.2 billion per year.
Another method is to calculate network security through the relationship between miner income and "miner extractable value" (MEV). MEV refers to all the value that miners can extract from on-chain and off-chain attacks. Preemptive MakerDAO CDP clearing or Uniswap transactions are two examples. If the benefits from MEV opportunities exceed the revenues miners receive from block rewards and fees, rational miners should be motivated to continuously develop blocks in order to seize these opportunities themselves. The end result is instability in the consensus layer and disruption of the ledger history and transaction processing. At present, MEV's opportunities in the BTC field are basically limited, but Professor Narayanan believes that with fee income accounting for the vast majority of miner income, MEV may become more and more common.
Finally, we calculate the safety rate by finding the ratio between miner income and network value. In other words, the safety ratio describes the value of wealth guaranteed by the value of safety. As we will discuss, the reduction in this ratio results in more and more value being protected by less and less security value, thus providing the possibility for deliberate attacks.

Form of attack
Blockchain networks must respond to three different forms of attack.
The first and most worrying form of attack is the double-spend attack. The word "double spend" can be misleading as it implies that funds can only be used twice. In fact, the requested funds can be reused any number of times. Double spend requires the attacker to control most of the hashing power. Once this hashing power is combined, attackers can "spend" their tokens in exchange for some tangible items, whether legal or non-monetary assets, such as a car. Once this exchange has occurred and the items have been received, the attackers begin to fork the network and build a longer chain to exclude their previous transactions. By excluding their initial transactions, the ledger shows that the attackers retain custody of the digital currency used to purchase items: at the same time, they also retain custody of the exchanged items. Assuming there are enough counterparties, this process can be repeated indefinitely. Benefits are a function of the "double spend" scale and imply rewards during this period, while costs are derived from the value spent on obtaining most of the hashing power. However, due to the proliferation of blockchain analysis companies and the threat of frozen accounts of exchanges supporting fiat currencies, the possibility of double-spend attacks seems to be getting smaller and smaller.
Unlike double spending, a deliberate attack is not necessarily driven by obvious profits. The forms of destruction include arbitrary review of accounts, the release of empty blocks, and disruption of activity through successive forks. Like double spend, sabotage attacks require a lot of hashing power to perform. However, deliberate attacks are easier to perform than double spends because they do not require the presence of a willing opponent to succeed. The ultimate goal is just to disrupt the utility of the blockchain network. Countries that are worried that digital currencies could undermine legal hegemony or support blockchain activities (money laundering, unregulated financial services) are the most likely participants. Here, returns cannot be calculated with explicit dollar returns. Instead, revenue is a function that limits the expected harm from an active network.
Speculative attacks include shorting digital currencies through spot or derivatives and disrupting the network as described above. In theory, market participants should react negatively to deliberate attacks because it reveals that the network cannot serve as a reliable platform for neutral economic activity. Although not very similar, there are many precedents of deliberate attacks in history, including the "Black Wednesday" attack launched by George Soros in 1992 and the recent manipulation of hedge fund credit default swaps. Here, the gain is a function of the profit from short positions minus the cost of combining most hashing power. Activist hedge funds may be participants.
As with any investment, the key decision factor is return on risk. In other words, what is the relationship between the probability of success and potential expenditure? If there is a 10% chance of success, the return must be at least 10 times the investment capital in order to have a chance to obtain a positive expectation. Another way to structure risk-reward is to look for any investment opportunity with a positively skewed expected value. This is where the security ratio comes into play: When the ratio between the cost of an attack and the value of the network decreases, the attack becomes correspondingly more profitable. Conversely, as the security rate of the network increases, the appeal of speculative attacks decreases accordingly.

Cross-network security rate
From the perspective of BTC safety rate, as time goes by, halving events will occur every four years and prices will rise significantly. Although miners' income or safety budgets are generally on the rise, safety rates have halved. There is a common misunderstanding in the industry that the increase in the price of BTC denominated in US dollars is sufficient to make up for the regular halving of block rewards. However, the BTC safety rate is not tied to the dollar value of BTC: miners' income doubles every four years, raising the safety budget to half of what it was before. But as the ratio of miner income to network value remains the same, this will still lead to halving the safety rate.

Data source: The Block, Coinmetrics
Ethereum's security rate has taken on different forms due to the uncertainty of its release time. However, just like BTC, over time, due to the decrease in block rewards, we have seen that the overall trend of the safety rate will deteriorate over time. From the beginning of 2020, due to the Miur network upgrade, the average block recovery time is 12-13 seconds. However, compared with BTC, the security rate is much less relevant for Ethereum, because the former is about to transition to an equity consensus proof algorithm, which requires a transformation of the network's security model.
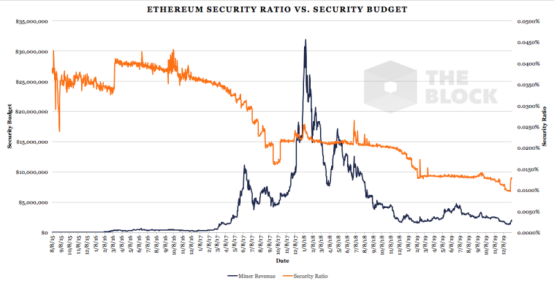
Data source: The Block, Coinmetrics
The following figure illustrates the comparative safety ratio:
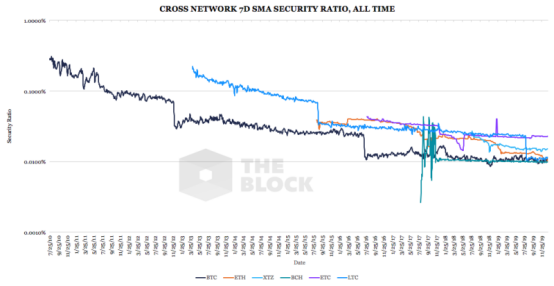
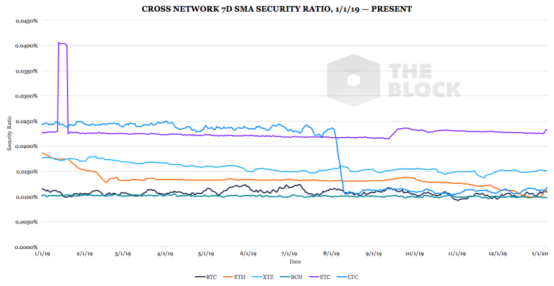
Data source: The Block, Coinmetrics
Assuming BTC's existing security rate is high enough to prevent speculative attacks, we can compare alternative networks to BTC to understand which platforms have too high or too low security costs.
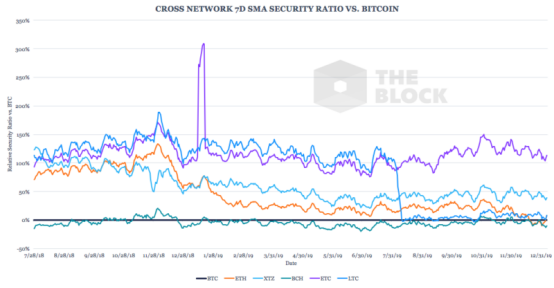
Data source: The Block, Coinmetrics
As of January 6, based on the 7-day moving average, we see that Ethereum (7.83%) and Litecoin (7.89%) are slightly higher than BTC. At the same time, the prices of Ethereum Classic (113.85%) and Tezos (38.90%) have been too high, while the price of Bitcoin Cash is lower (-9.98%). Tezos' overpayments may be explained by issuing bonds as a form of development funding.

What are the actual impacts?
Is BTC's imminent safety rate halving worthy of attention? The answer is probably no. Although the safety rate will be reduced by almost 630,000 blocks, potential speculators are still limited. First, there is not enough liquidity in the borrowing, futures and options markets to profit from the attack. Bitmex's BTC permanent swap currently has $ 729 million open positions, while Derbit's open positions are only $ 390 million. Although there are some of the most liquid digital currency markets on the market, these markets are still not large enough to achieve benefits from deliberate attacks.
Speculators are also limited in organizing the necessary hashing capabilities, geographically limited in low-cost energy prices, and the secondary market for mining hardware is largely illiquid. Here are three opposing views: Joseph Bonneau raised the possibility of making a lease or purchase through a bribery attack. Selfish-mining shows that controlling 51% of hashing power is not necessary to perform malicious actions, and bringing a large amount of potential hashing power online will drive low-profit operations, which means that the cost of an attack may be higher than existing miners Income should be low. However, considering that we haven't seen Selfish-mining and bribery attacks, we have reason to conclude that they are currently largely impractical and unattractive.
Finally, potential speculative attackers must note that the digital currency market often ignores fundamental-driven events: Ethereum Classic's trading volume has fallen by only 2% after a double spend in January last year. Since the cost of attack is linearly proportional to time, the uncertainty surrounding the delay in considering this information will directly affect revenue.
However, the decline in BTC safety rates in the next decade has caused concern. As Bryan Ford writes, "Only when systems become large enough to be swallowed up by their own success will they become temporarily safer." "If BTC 'success'-the definition of success is broad, But it may be measured by the continuous increase in the value of the network, or at least the continuous increase in the degree of continuous activity-we should naturally expect the growth of the liquidity of derivatives to flourish, opening up the possibility for such attacks. The increasing "go "Centralized exchanges" liquidity may spawn such attacks, as their pseudonym assets allow unlimited contract caps, which limits their possibility of launching similar attacks in traditional capital markets.
Miner concentration is itself a double-edged sword. In the short term, the concentration of hashing power may help prevent speculative attacks, as miners may collude to implement the anti-bribery strategy described by Bonneau. However, this concentration also makes it possible for miners to collude and become attackers. Of course, as owners of capital assets, their income structure must take into account the write-down of mining hardware.
The only natural solution to the deteriorating security rate of BTC is the rapid rise of a healthy toll market. If we assume that the existing safety rate is balanced-any higher price is overpaid and any lower price is unsafe-after the halving event, the fee income of each block must rise to 6.25 BTC. At the current level of fee income, this would require a 4300% increase in fees per block.
MATTEO LEIBOWITZ Author
Edited by Roy Wang
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Viewpoint | Talking about Bitcoin from the Theory of Monetary Information: Bitcoin is the ultimate safe-haven asset
- Weekly data report on the BTC chain: The data on the chain rebounded quickly after the rebound, and the sluggish situation is still difficult to get out of
- ChainLink, the oracle connecting the two worlds
- Beijing will promote blockchain technology applications in more than 20 areas including real estate transactions
- Featured | Top 10 content producers in the currency of Twitter; Is Bitcoin 2020 really like the early Internet?
- Can distributed search engines challenge Google's dominance?
- If Buffett wanted to buy Bitcoin, what would he buy?





