Perfecting Blockchain Cognition with Bitcoin's Middle Tier Knowledge
Source: See you there
Production: Blockchain Base Camp
Why do you have so much knowledge about the blockchain?
The first is the entertainment era, where propaganda is often used instead of theory.
- Dry goods | Three technical analysis methods to play the Bitcoin market cycle
- Babbitt Column | Regulatory Sandbox Confirms Difficulties in Implementation, China Should Actively Deploy Industrial Sandbox
- Will the date of CME's launch of Bitcoin options be the end of altcoins?
The second is that everyone is used to the causal routine in cognition. For many things, you first see the effect, then look at the cause, and then you come to the cause and effect. This method is generally useful, but it is not always effective, because it ignores the middle layer, so it may lead to a cause and effect with a large deviation.
For example, Huawei company, the common "effect" of Huawei is high innovation and high profit. Then look at the "effect" of Huawei is high salary, wolf culture, big R & D, etc., and then come to the cause and effect of "wolf sex can be high profit" .
This is certainly a fallacy, because this cause and effect ignores Huawei's important "middle tier"-from 1998 to 2007, Huawei spent 10 years, smashing billions of dollars, and completed it with the support of IBM. Real digital transformation [1] .
Today (2019), many companies are only preparing for the digital transformation in the next five years. Huawei achieved high-quality implementation more than a decade ago. This is the key point of Huawei's outstanding performance.
After "sharpening", talk about the middle layer of the blockchain. Now Baidu, we can see that the blockchain has four elements: distributed data storage, point-to-point transmission, consensus mechanism, and encryption algorithm. Many readers have already brushed this up a few years ago, but why are they still confused? Because the four elements are not the truth of the blockchain , but only the four characteristics of the blockchain, the blockchain has its own "middle layer". So we have to start with Bitcoin.
Satoshi Nakamoto created the first decentralized experimental financial system successfully operating on the Internet-Bitcoin, which is also the origin of today's generalized blockchain. Regarding the basic operating mechanism of Bitcoin, you can read the only handed-down book, the Bitcoin White Paper, by Zhong Jiao.
At that time, Satoshi Nakamoto did not know the broad block chain that has become a trend today. He just focused on how to build an absolutely secure and reliable Internet, remove the center and third-party intermediaries, and fully participate in a fully credible currency issuance and transaction mechanism. This is also the basic tenet of "blockchain teaching". Based on this original intention, Satoshi's bitcoin world is actually composed of three elements: an asymmetric encryption algorithm mechanism, a blockchain ledger, and a node (miner). Let's talk about the asymmetric encryption algorithm mechanism first.
Asymmetric encryption algorithm mechanism in Bitcoin
Satoshi Nakamoto's skilled application of cryptography and encryption algorithms is one of the most admirable geniuses in the Bitcoin system. The asymmetric encryption algorithm mechanism mainly includes three key technical points: private key, public key, and digital signature, and supporting asymmetric encryption algorithms.
Let's talk about information encryption first. In the course of human society's development, the first need for information encryption and cracking is the military. In ancient Roman times, humans were skilled at using "key" mechanisms for encryption. The so-called key is the stuff that can encrypt the original data or decrypt the encrypted data.
For example, the word "baby", we use a backward misalignment encryption algorithm with a key of 1 (b backwards is 1 bit is c, a backwards is 1 bit is b …), then it becomes " cbcz ", you can push back with key 1 when decrypting. In the long history of humans, the evolution of the single-key algorithm has become more complex. By the time of World War II, the British and Germans had been fighting brilliantly and brilliantly in single-key-based telegram encryption and breaking secrets, and directly changed the course of World War II. .
The asymmetric encryption algorithm was invented in 1976. After continuous optimization and evolution, it is currently known as the most secure encryption algorithm for human beings. The main business mechanisms of asymmetric encryption are :
1) Encryption and decryption use keys, which can be used for encryption and decryption;
2) There are now two keys paired, called private key A and public key B, which is asymmetric;
3) The information encrypted with the private key A can be decrypted with the paired public key B;
4) The information encrypted with the public key B can be decrypted with the paired private key A;
5) At present, the computing power of human beings cannot theoretically crack asymmetric encryption.
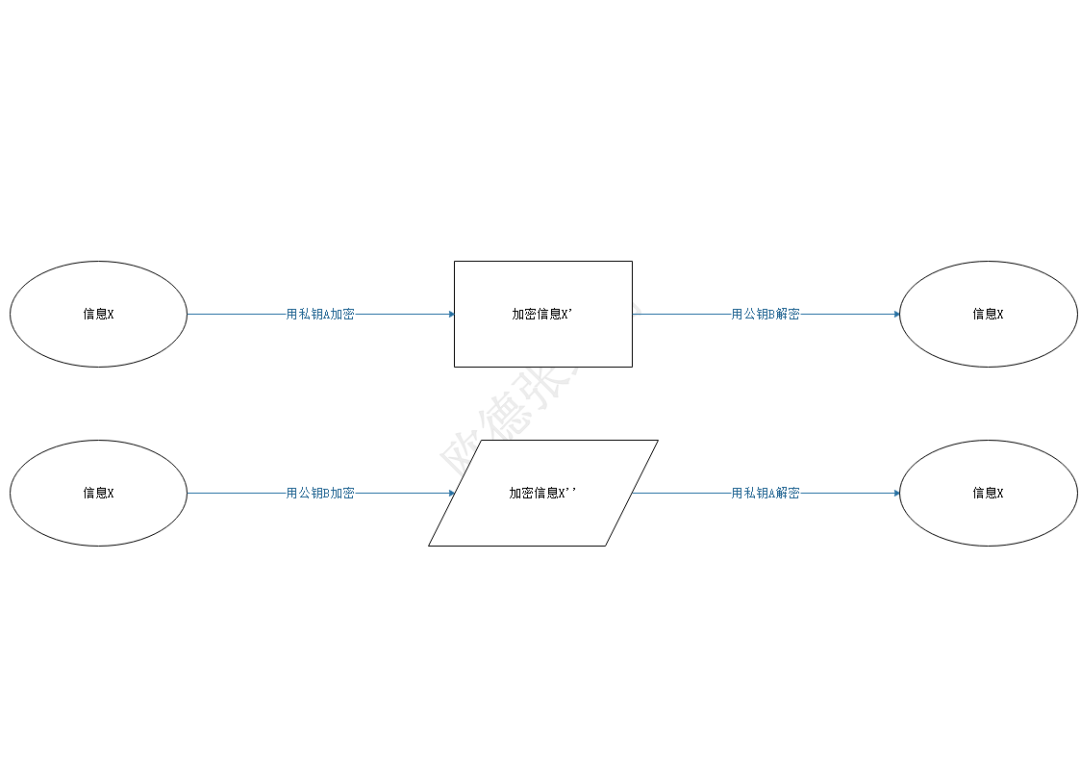
After the emergence of asymmetric encryption algorithms, they have been widely used in security authentication and information transmission encryption. But when he came to Satoshi Nakamoto, the asymmetric encryption algorithm changed suddenly and became one of the most dazzling creations in decentralized design. This is also what Satoshi Nakamoto thought of. He has come up in the "Bitcoin White Paper" You have to create this: "Digital signatures provide part of the solution."
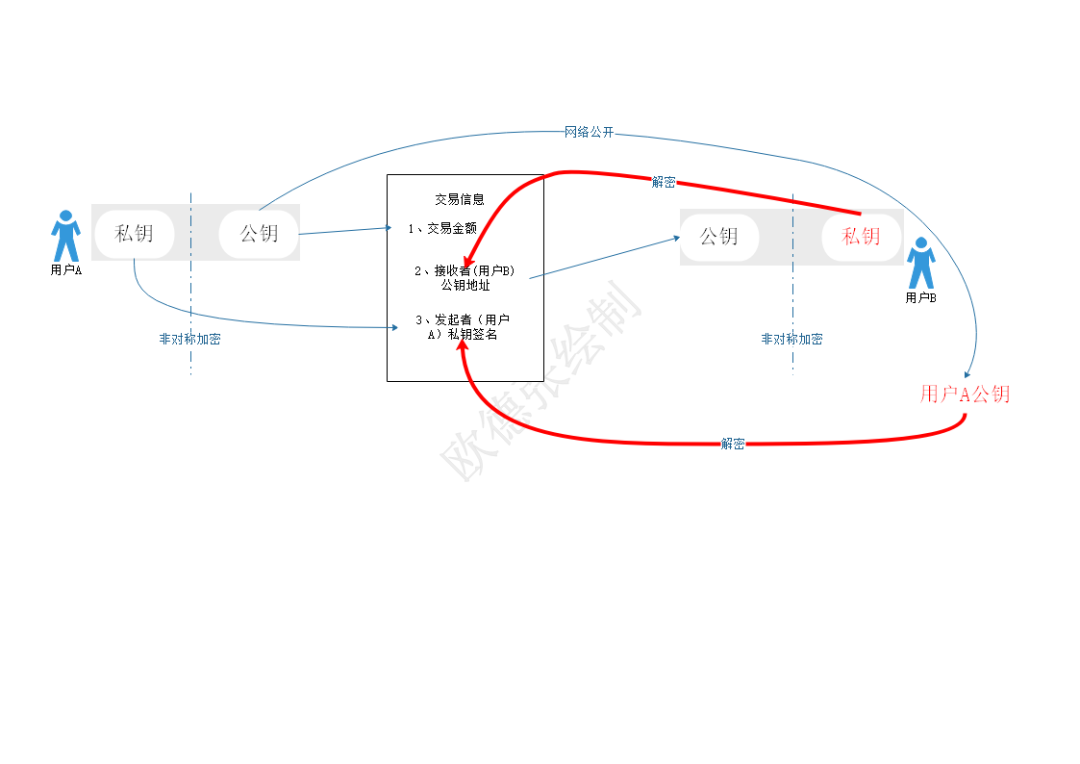
See the above figure, which is a simplified version of the Bitcoin transaction model drawn by the author. The main process is as follows:
(1) Both user A and user B use private keys for transactions, but exposed on the network are public keys that are uniquely matched with their respective private keys calculated by asymmetric encryption algorithms. The public key cannot be used to derive the private key. Key, which protects the privacy of the user;
(2) When user A initiates a transaction, the main information includes: a. The initiator's wallet (public key) address; b. The transaction amount; c. The recipient (user B) public key address; d. The transaction initiator (user A ) Use your own private key to digitally sign the transaction confirmation.
(3) At this time, to decrypt the transaction information (to obtain the "transfer money" of user A), it is necessary to unlock the composite encrypted content of the two keys of user A and user B at the same time: a. The encrypted information of the initiator user A ( Digital signature of the private key of the initiator); b. Receiver user B's own identity encryption (recipient's public key).
(4) The recipient only needs to use his own private key and the public key of the initiator (here, user A) that is publicly available on the network to decrypt the transaction information.
This mechanism realizes the initiator's effective confirmation and immutability of the transaction from the business logic, and enables the receiver to decrypt the transaction with the only valid identity (personal private key).
Theoretically, we have deduced the above logic. The practice of secure operation of the Bitcoin system for so many years also proves its security and effectiveness: User A and User B can freely and securely transfer large amounts of money (considering that a bitcoin is worth thousands of dollars now), That is one of the foundations of Bitcoin's " decentralized peer-to-peer secure and reliable transaction ": "Digital signatures provide part of the solution."
Dear officials, you can tell me that at this time, although the Bitcoin system is peer-to-peer information exchange like QQ, there is no need to have a central database like QQ to store your account number and password. As long as you have your private key, no one can steal your number. You can use your personal private key to break into the country alone. This really opens the magic box. Satoshi Nakamoto used the private key, public key, and digital signature to kill Roush's data center! From now on, your world is yours! Sometimes I think, is this one of the reasons for the hidden world of the middle school master?
Of course, the actual Bitcoin transaction is slightly more complicated, mainly due to the symmetric encryption conversion between "public key" and "wallet address". 【2】
In addition, in the bitcoin world, private keys are very important (many people are on a USB flash drive). Once you lose them, you really ca n’t find them. It is estimated that the number of Bitcoins that cannot be recovered due to the loss of the private key is as high as More than 20%-It is said that going to the trash can in the densely populated living area of Madong when it's okay is to find the lost USB flash drive. It is an activity that is full of exercise and full of dreams of getting rich.
Postscript: The vernacular of the next point of knowledge in the middle layer is being written. If you want to know the future, listen to it next time.
Notes:
[1] Ren Zhengfei's interview with the Wall Street Journal: In our company, I am actually a puppet, and my presence or absence has not affected the company so much. When we learned about management change from IBM, an IBM consultant told me that "management change is ultimately about killing you, leaving you without power, do you have that determination?" I said we did. Hundreds of IBM experts have helped us change here for more than a decade. Huawei has become like this today. IBM has laid a very important organizational structure and management foundation for us.
[2] In Bitcoin, the private key is a 256-bit binary number (32 bytes), and the private key conversion output has two: one is to generate a public key through an asymmetric encryption algorithm, and then convert to generate a public key hash value This process irreversibly finds the private key. The public key in compressed format has 33 bytes, and the uncompressed public key has 65 bytes. In order to facilitate memory, the public key hash can also be converted to generate a wallet address (20 bytes), which uniquely matches the public key. Reverse deduction is mainly to facilitate memory. The second is that digital signatures can be generated through private keys. The owner of bitcoin must pass the double verification of public key and signature to use bitcoin.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Analysis of Singapore's Payment Services Act: What is the difference between the regulatory policies imposed on different types of digital currencies
- EOSIO 2.0 is officially released, solving the biggest bottleneck of blockchain development, making EOS "faster, easier and more secure"
- 2020 Investor's Congress discussion: Market fluctuations, how to predict capital?
- IDC report: Blockchain + AI will be the world of Chinese enterprises?
- 10 indicators show why BTC is successful
- How to start a blockchain fairly or unfairly?
- NFT-the cornerstone of encrypted digital assets





