Can't you have both privacy and utility? Privacy protection opens up new horizons for business
Author: Yan strong
Source: Weizhong Bank Blockchain
Speaking of the world's data, points must be divided for a long time.
- Million-sold hardware wallet, can Ledger NanoX shake the throne of the previous "machine emperor"
- South Korea officially passes amendments to the special financial law! Cryptocurrency Institutionalization Goes Next
- LingTing · Blockchain General Knowledge Lecture 70: Make the blockchain "understand"
With the rapid development of computer software and hardware technology, the overall informatization of society has increased, and the value of data has gradually become more prominent, thus creating an information age of data collection, data extraction, and data realization. With the deepening of the commercialization of information technology, the hidden privacy risks of data collection are also increasing.
Marked by a series of laws and regulations and technical specifications such as the "People's Republic of China Cyber Security Law", "Information Security Technology Personal Information Security Specifications", "Personal Financial Information Protection Technical Specifications", "Financial Distributed Ledger Technical Security Specifications" and other marks, privacy The refinement of protection legislation and the awakening of the awareness of data owners' rights and interests have further promoted the return of the unified data control right of the big platform to the scattered data owners.
Changing times, privacy demands and business utility seem to have evolved into a pair of contradictions that are difficult to reconcile, and business models that rely on data are challenging to maintain sustainable growth.
How to solve this dilemma? Here, we will share some thoughts on the relationship between privacy protection and modern commercial reciprocity from the perspective of exploring business opportunities: how to resolve the conflict of claims between the protection of owner's rights and the transformation of commercial interests with the help of technical means, and realize the two Symbiosis.

Clarify the objects and scope of privacy protection
First, we need to clarify the objects and categories of privacy protection.
When it comes to private data, the first impression is mostly related to individual users, such as identity, whereabouts, purchase behavior, etc., but the scope of private data is not limited to this. Any data that is not willing to be publicly disclosed is essentially, such as internal business data The owner of the corresponding data ownership, correspondingly the data owner, should be protected.
Private data is called private data because it has special value to the owner of the data and usually reflects the owner ’s unique identity or other sensitive information. Compared with public data, private data has higher information entropy and can provide better individual discrimination in the commercialization of information.
This is especially true for commercial activities that take swap as the essence, because it not only increases the possibility of finding potential exchange counterparties, but also provides scarce information to determine a more reasonable exchange price.
At present, information service platforms whose main profit model is to match the needs of buyers and sellers, such as e-commerce, search, online advertising, etc., one of the most core competitiveness comes from such data.

Risk analysis of commercial privacy data
The greater the amount of privacy data that the platform brings together, the greater the commercial value that it generates, but it will also make privacy risks "mine".
Privacy protection legislation is gradually improving, and data commercial needs to be legal and compliant
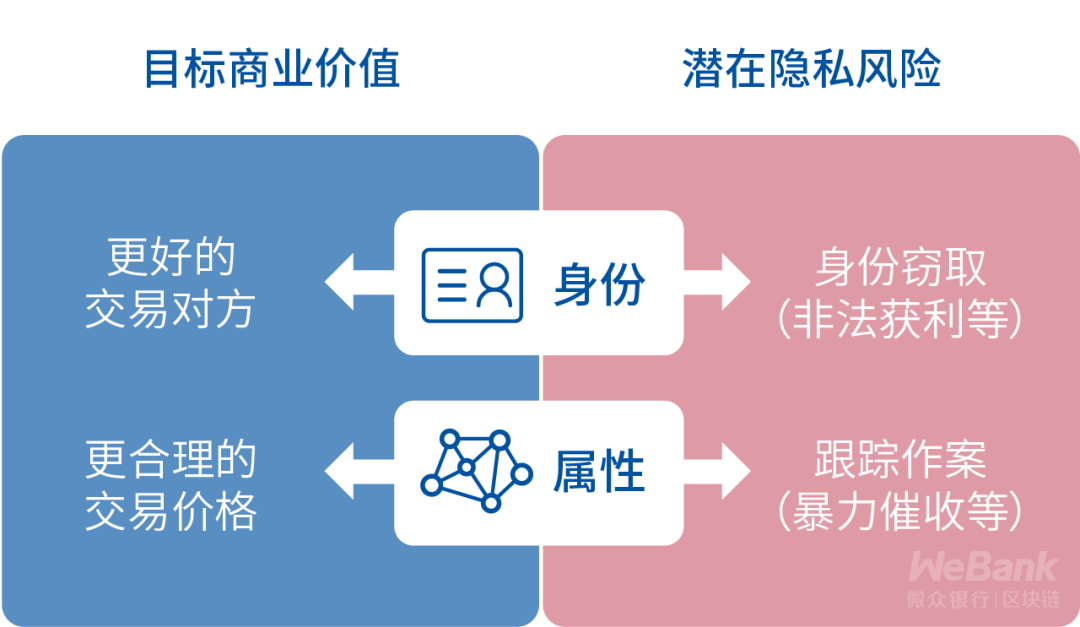


In addition to the privacy protection laws and regulations, in addition to regulating the applicable scope and use restrictions of private data, the original intention is to return control and profit rights of private data to the data owner.
Awareness of data owner protection rises
In the current society, the commercialization of information technology is no longer a new thing. After years of user education, data owners have gradually realized the value of their own private data and the risks of sharing private data. Compared to earlier days, more and more data owners actively explore the value of this type of exchange process, begin to conduct risk assessments on it, and selectively participate in the value exchange process of private data.
If the use of a product faces more than expected privacy risks, a reasonable data owner is likely to make the following choices:
1) Continue to use the product but give false data.
2) Discard the product or switch to a replaceable product of the same type.
The rise of the protection consciousness of data owners, coupled with the improvement of privacy protection legislation and the evolution of privacy data control from concentration to differentiation, will present a series of major challenges to existing business models that use data as the main driving force. . The key to solving the challenge lies not in the zero-sum game between the owner of the data and the user of the data, but in how to align the interests of the two in order to achieve the optimal benefits together.

Expected effect of four layers of privacy protection technology
In resolving the conflict between the privacy protection of data owners and the transformation of commercial interests, we need to introduce privacy protection technologies.
Due to space limitations, this article only outlines the four expected effects of privacy protection technology to resolve conflicts. The scientific theory, technical solutions and case analysis of privacy protection will be shared in subsequent tweets.
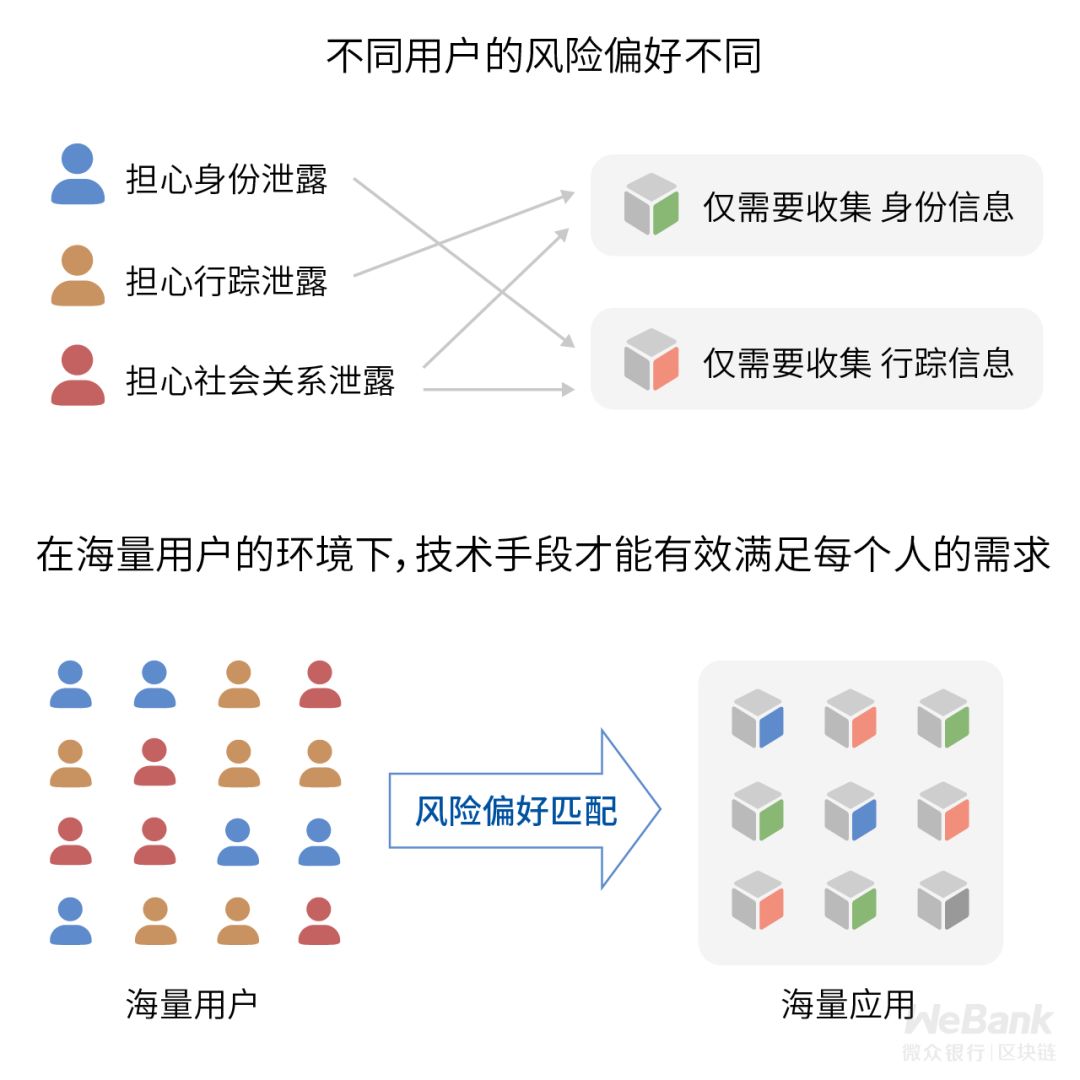
The first layer of privacy protection technology: enhanced data transparency
Technical means can reduce the user's cognitive cost and make it easier to understand key data such as what data will be collected and how it will be used to better assess their own risks.
The intelligent recommendation model is appropriately introduced, and a reasonable judgment is automatically made according to the risk preference preset by the user, so as to reduce the potential loss caused by the reduced user participation due to the risk uncertainty.
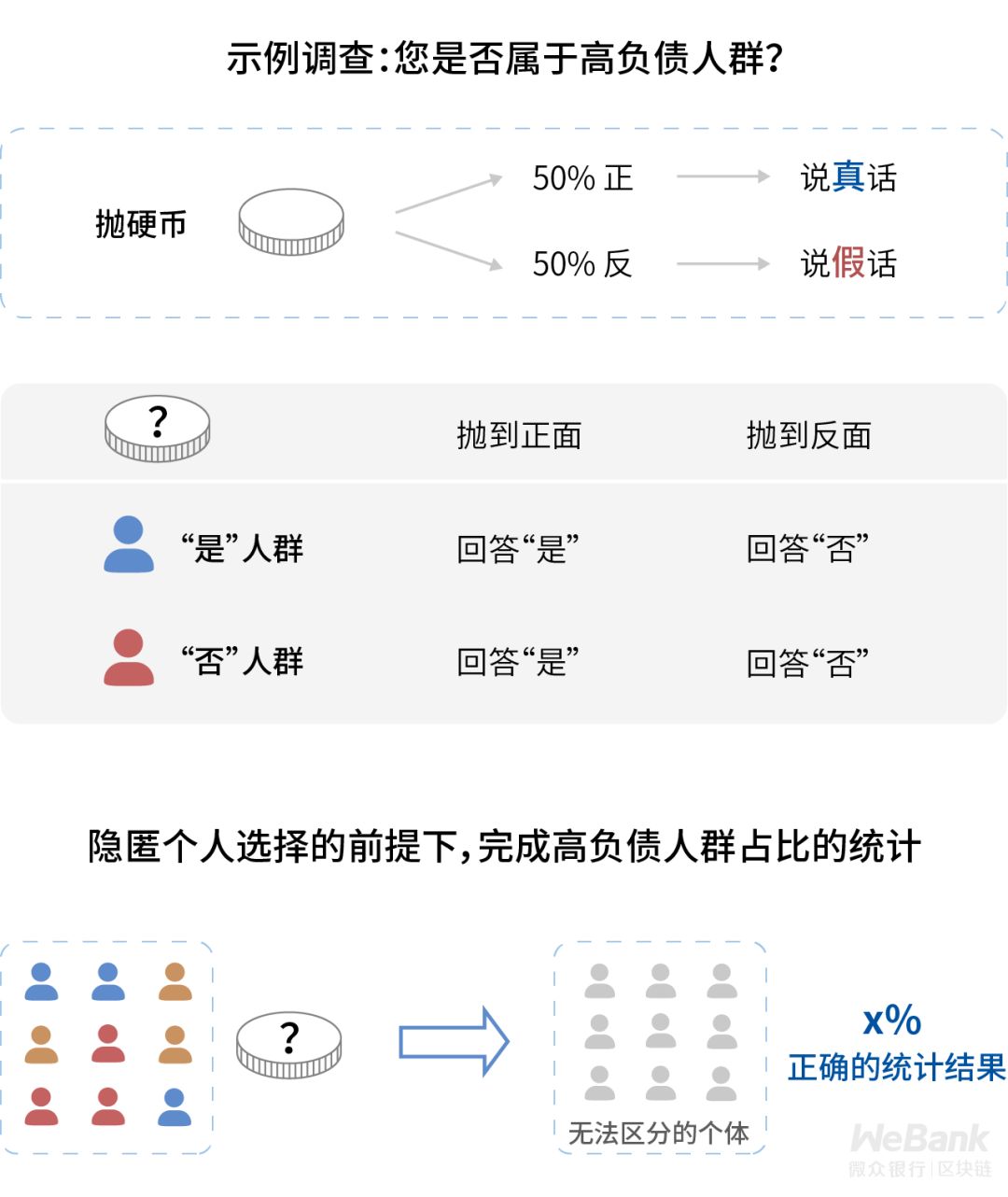
The second effect of privacy protection technology: enhance data privacy
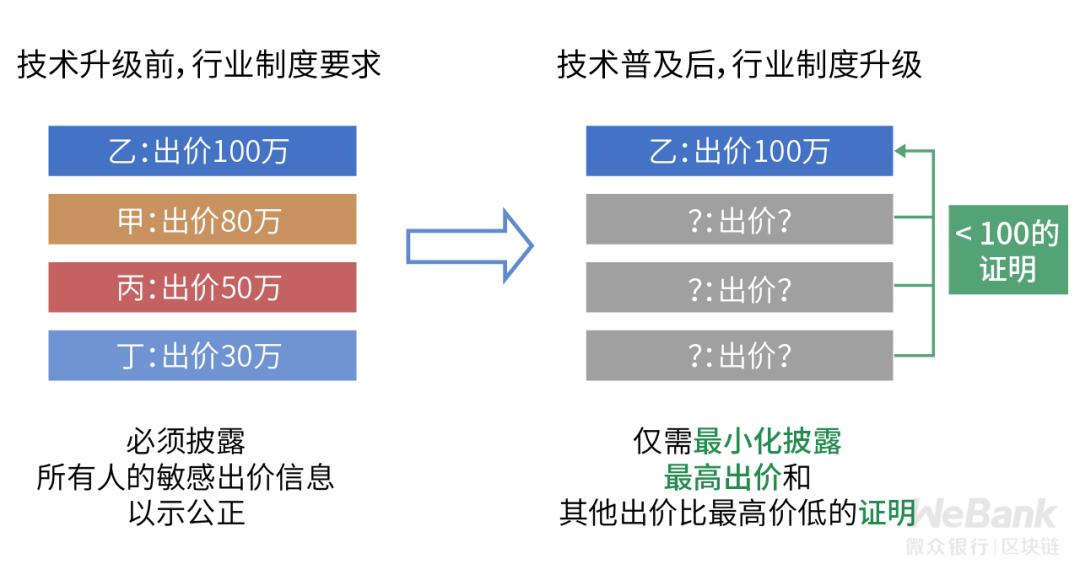
Technical means can ensure that users cannot be attributed to individuals even if they share sensitive information, so as to increase users' willingness to share real data and reduce potential losses caused by users giving false data due to too sensitive information.
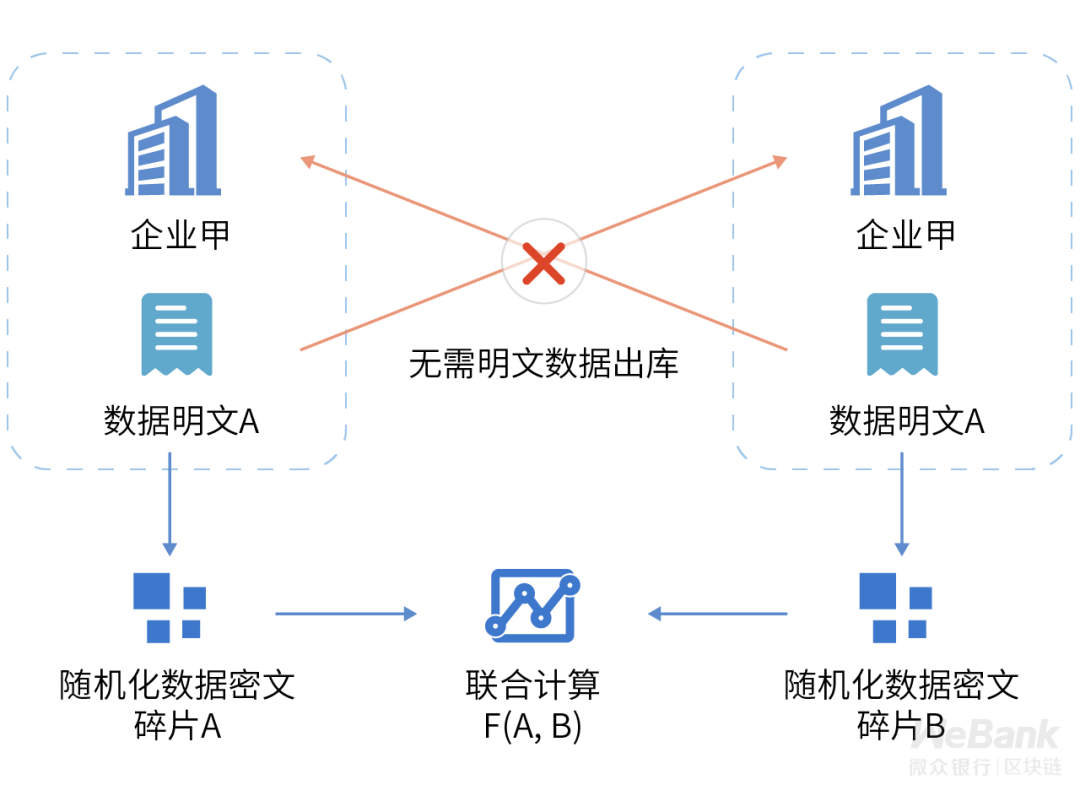
The third layer of privacy protection technology: enhanced data control
Technical means can ensure that private data can only be used in an "authorized" manner. In other cases, data cannot be used at all, further increasing users' willingness to participate in value exchange.
In particular, as the owner of the data, under the premise of protecting the confidentiality of the company's own business data, it can securely develop joint data businesses and promote new business cooperation models.
The fourth layer of privacy protection technology: enhance data collaboration
The privacy protection technology has certain technical theoretical thresholds, and the practice-proven privacy protection technology solutions are relatively limited, which is conducive to the standardization of data interfaces in the industry, reduces the collaboration cost of joint business data between enterprises, and promotes more privacy-friendly business cooperation. The establishment of a regulatory system will ultimately promote the technological upgrading of the entire industry.
It is: Talking about the privacy of information attracting attention, creating opportunities for business and creating new horizons!
The value of privacy protection technology is gradually being demonstrated, and the privacy protection legislation of countries around the world is gradually improving. How can companies ride the waves and effectively achieve legal compliance in the process of business exploration and innovation? Stay tuned for the next breakdown.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- QKL123 market analysis | What is Bitcoin? Risk assets or hedge assets (0305)
- Intensive Reading | BIS: From the Flower of Money to the CBDDC Pyramid
- US Congress Holds Blockchain Hearing, Participating Companies Outspoken: Crypto Tax Is A "Nightmare"
- Perspectives | Bitcoin is not dead, the cycle is immortal
- Wall Street capital forces palace, Silicon Valley elite trust crisis and crypto sweetness
- Perspective | Digital assets will establish a new order for the private equity market, which will become the standard investment market
- ProgPoW algorithm is leaked, Ethereum ASIC mining is unstoppable?




