Discussion on anti-counterfeiting, anti-intrusion and tampering, and blockchain technology to improve the security of drone operations
Author: Lu Yue Feng Ze ice (Information Security Institute, Chinese Academy of Communications, Beijing 100191, China)
Source: ICT and Policy
Editor's Note: The original title was "Blockchain Enhances Security Analysis of UAV Bee Colony System"
Abstract: UAV bee colony operations have scale advantages and cost advantages in the face of high-intensity confrontation and dynamic battlefield changes. At present, they have been widely used in military fields by countries around the world. At the same time, the drone bee colony system has also become a network attack target, facing security risks such as malicious node intrusion, drone hijacking, wireless interference, and data theft. Blockchain technology has the characteristics of asymmetric encryption, chain data storage, and node collaboration consensus. It has been studied as an effective technical means to resist the threat of distributed network attacks, which can effectively enhance the security of drone bee colonies . The current development situation and security risks of drone bee colony systems, and the feasibility of blockchain technology to enhance the safety of drone bee colony systems are analyzed and studied, and some technical challenges in applying blockchain technology are proposed .
- Super Planet Token GDP Price "Zeroed" Issuing Convertible Bonds With Annual Interest Rates Up To 250%
- Former CFTC Chairman: Satoshi Nakamoto's white paper does not include concepts aimed at breaking away from government or regulatory networks
- Coins Story | Do you still love Bitcoin after the plunge?
Keywords: drone bee colony; blockchain; network security
1 Development situation of drone bee colony system
Unmanned aerial vehicle (UAV) technology has developed rapidly. Given its "easy deployment, low maintenance costs, high maneuverability, and hovering capabilities", it has been used in search and rescue, remote sensing, power inspection, agriculture, and parcel Delivery, traffic monitoring, surveillance and wireless network coverage [1]. It is estimated that by 2025, the market value of drones is expected to be $ 127 billion, which will create about 100,000 new jobs. The versatility of drones makes them more commonplace in daily life, so the robustness and security of drone networks is critical.
In addition to civilian use, drones are also widely used in military applications. Unmanned aerial vehicle swarm cooperative formation operations have become important mission methods for military countries in the world. Unmanned aerial vehicle swarm means that under the command or supervision of the operating personnel (air or ground), it forms a combat swarm to cooperate to perform tasks through self-organizing and cooperative networking. The drones that make up the bee colony can be isomorphic or heterogeneous, and the grouping method can be master-slave or centerless. Networked drone bee swarms can greatly enhance the capabilities of a single drone, giving play to the advantages of a large number, wide range, fast speed, and flexible combat, and improving joint target search, battlefield situational awareness, and combat tasks for drone bee swarms. Ability to coordinate, suppress and destroy in wartime.
At present, countries around the world are accelerating projects to combat drone fleets. U.S. military technology research institutes have launched a large number of drone research projects, such as the "Grey Mountain Quail" micro-drone project of the US Department of Defense's Strategic Capability Office, and the Defense Advanced Research Projects Agency (DARPA) "elf" drone bee colony project 2. The "Low-cost UAV Bee Colony" project of the U.S. Navy Research Agency [2]. The European Defense Agency launched the "European Swarm" project in November 2016 to develop key technologies such as autonomous mission decision-making and coordinated navigation for drone swarms. The British Ministry of Defence launched a drone swarm competition with a bonus of 3 million pounds in September 2016. The participating swarms completed tasks such as information relay, communication interference, tracking and targeting personnel or vehicles, and area mapping.
2 Security risks of drone swarm cooperative operations
Although the drone bee colony has excellent combat capabilities due to its flexible networking and intelligent collaboration, it also attracts hackers trying to invade the drone. For example, hacked drones can be controlled by hackers to obtain some very important information in the battlefield environment. Due to the fact that combat drone swarms often perform tasks in areas that cannot be covered by ground station signals, their transition to the wireless environment and distributed networking features make them face a series of security risks.
(1) Centralized bee colony management brings a single point of risk. At present, many UAV bee colony systems mainly control UAVs in the air or on the ground. For example, large-scale aircraft nodes or ground control stations (GCS) control the fleets [3]. This management method is highly centralized. When the management node is destroyed by the enemy or takes over control, it will cause the entire UAV network control to fail, affecting the flight and combat mission execution of the UAV. Some studies have proposed that when the central node fails, the cluster can use distributed Mesh networking to achieve collaborative communication [4]. Due to the lack of reliable authentication and consensus mechanisms, single point of distrust spreads into multiple points of distrust in the network. It is still difficult to guarantee authentication and data reliability between drone nodes.
(2) Security risks of hijacking and illegal intrusion. Due to software vulnerabilities or insecure settings, drones may be hijacked by the enemy, and the enemy can completely control and use the hijacked drone for various internal attacks. On the one hand, the invaded UAV node acts as a springboard node, sending false information or combat instructions to neighboring nodes, affecting the execution of the combat task of the fleet; on the other hand, the hijacked UAV node will also interfere with other normal nodes. Collaboration and communication.
(3) Physical link interference and monitoring risks. UAV bee swarms generally transmit data through wireless channels. The unreliability of the wireless communication environment will seriously affect the interaction between nodes. For example, excessive wireless interference will affect wireless signal reception. At the same time, the drone terminal has insufficient capabilities, and its capacity and computing capacity are limited by the battery capacity. Traditional encryption technology and data storage are difficult to store on the drone device, which makes the drone particularly vulnerable to data integrity, especially tamper-resistant. Risk of wireless link listening and data theft.
3 Blockchain-enhanced drone bee colony security analysis
Blockchain technology uses computer networks and cryptographic principles, and through the integration of asymmetric encryption, distributed networking, and smart contracts, it realizes distributed node collaboration and secure data storage. Nodes in the blockchain record the verified information into the block, and each block forms a chain structure in time sequence to achieve information traceability; the distributed networking technology of the blockchain achieves decentralization, and the network And computing resources are distributed on each node, and the P2P network architecture is used to resist centralized attacks and achieve high fault tolerance. Even if individual nodes fail, the entire blockchain system is not affected; the blockchain can introduce asymmetric encryption to achieve trust, and public and private Key technology can realize the signature, authentication and data encryption communication between nodes; the blockchain implements multi-node negotiation and collaboration through consensus algorithms, avoiding problems such as location restrictions brought by centralized data management. Because of these characteristics of the blockchain, it has been used to solve multiple problems in the field of drones. For example, the United States Boeing Company uses blockchain technology to record information such as the location, time and resources of drones in flight, enabling real-time accurate tracking of drones during flight; IBM uses blockchain technology to improve airspace controllers and supervision Institutions' ability to supervise aerial drones; Wal-Mart uses blockchain infrastructure to replace cloud platforms to achieve management of drone logistics processes.
UAV swarm formations perform combat tasks and can self-organize into a temporary distributed blockchain system. UAVs act as blockchain nodes to achieve the storage of battlefield detection information, the consensus and execution of combat task execution instructions, etc. ( see picture 1).
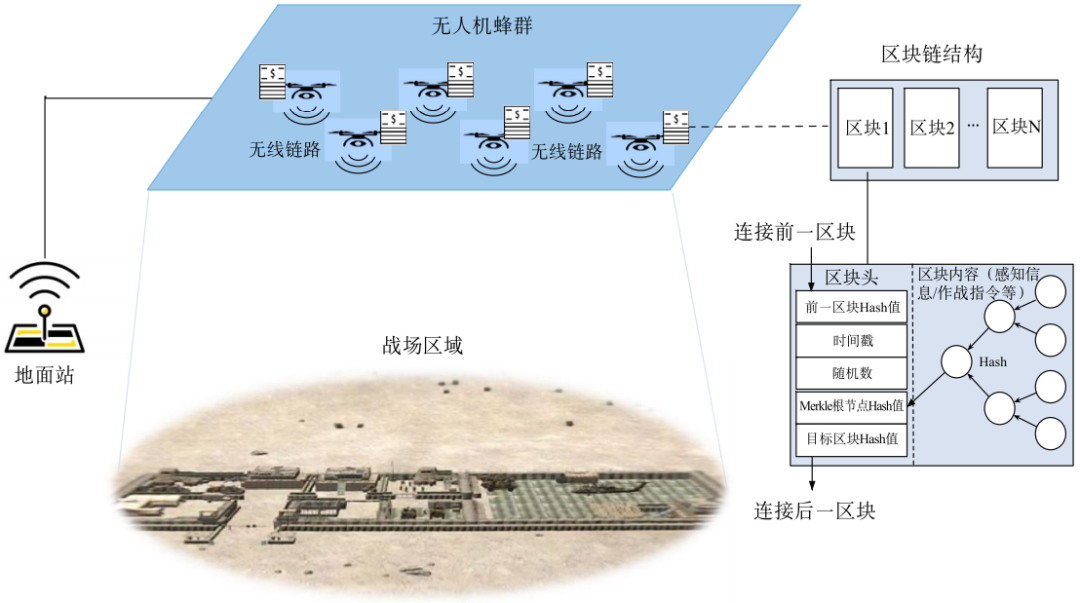
Figure 1 Blockchain-based drone bee colony system
On the one hand, the broadcast characteristics of wireless communications are consistent with the transaction broadcast characteristics of the blockchain. When the drone node generates information that needs to be chained, the drone node can broadcast through the wireless channel, and other drone nodes can receive and verify the received broadcast message, which simplifies the routing management in the wired network. . On the other hand, blockchain technology can enable drone bee swarms to vote based on collected information without a central node, and at the same time write the voting results into the blockchain to reach consensus, thereby completing group decisions and effectively reducing maliciousness. Drone penetration risk.
The use of blockchain technology can enhance the security of drone bee colony systems in the following aspects. (1) Strong anonymity identity management. In a drone bee colony blockchain system, if an external drone node wants to communicate with a bee colony node, it first needs to authenticate its identity. Nodes that do not belong to the blockchain cannot be authenticated by the bee colony, which can effectively prevent the network intrusion of malicious drone nodes. In addition, in order to prevent malicious drone nodes from intercepting and monitoring data, asymmetric encryption technology can be used, and the data exchange between the two parties can be encrypted with each other's public key, so even if the information is broadcast in all nodes, only the master The node with the private key can decrypt the information, and other nodes cannot read the information after receiving it (similar to the principle of BitMessage). (2) Node consensus effectively prevents the spread of fake information. If a drone is hijacked or maliciously hijacked, it may generate interference noise information and affect the results of collaborative detection. For example, when a fleet conducts cooperative detection, a drone that has been hijacked locally broadcasts incorrect detection results or combat instructions to neighboring drones. In the blockchain system, the drone nodes in the bee colony will verify the received detection messages according to their own detection results. If the detection result information fails to pass the verification of most nodes, it is considered an illegal message. No winding record will be performed. This can effectively confirm and optimize the monitoring information and ensure the accuracy of the detection results. (3) Chain storage prevents key information from being tampered with. In the process of the bee colony performing tasks, the blockchain's difficult to tamper characteristics are used to effectively protect mission-critical instruction information. The key instruction set used to perform combat tasks can be stored on the blockchain to prevent some nodes from being hijacked or attacked. Bring operational instructions or detect data tampering. In addition, as each drone records a backup of the blockchain information, as long as one drone can successfully return to the base, all the drone bee colony detection data can be restored.
4 Challenges in applying blockchain
Although the blockchain technology and the drone bee network have a natural fit, the problems of drone bee colony mobility, distributed wireless networking, and resource constraints will still affect the feasibility of applying the blockchain. There are also certain challenges in using blockchain to improve drone security.
(1) The failure of the drone point affects the consensus and accounting process. Because drones are both data storage nodes and computing nodes, when some drones return home due to battery exhaustion or are maliciously damaged, nodes in the blockchain system will fail (see Figure 2), which will affect the drone network. Node consensus process for topologies and blockchain systems. Especially when a certain node that bears the main computing power is attacked, it will have a great impact on the capacity of the blockchain system and the block recording rate. If some nodes are betrayed by viruses, it will prevent the remaining nodes from reaching consensus. It has been proved that in a synchronous and reliable network with n nodes, as long as there are no betrayer (n-1) / 3, practical Byzantine fault tolerance can achieve node consistency [5].
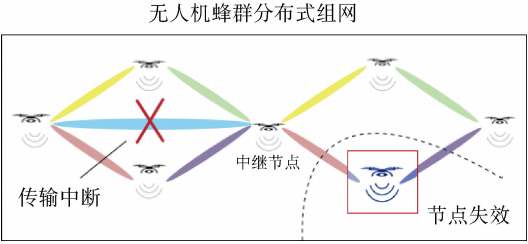
Figure 2 Transmission interruption and node failure
(2) Unreliability of the transmission link affects node consensus. Drone bee swarms transmit via wireless links. Problems such as wireless channel attenuation, signal interference, and limited node power can reduce signal quality. A lower signal-to-noise ratio affects signal reception. The transmission rate between drone nodes and The possibility of a link interruption causes nodes to be non-equal in the entire network [6]. On the one hand, after a node completes the consensus algorithm, it suffers from large channel interference, which causes the signal strength of its communication with neighboring nodes to be lower than a certain threshold and cannot be successfully transmitted, resulting in the node's failure to successfully broadcast its workload certification to other nodes. Nodes, which will affect the record of this block; on the other hand, the mobility of drone nodes will cause dynamic changes in the network topology, and the nodes participating in the consensus each time a node broadcasts a message are also different, which will also affect to a certain extent The stability of the blockchain system. (3) Limited node resources affect the availability of the blockchain. In addition to the necessary flight, communication and execution tasks, the drone bee colony also needs to participate in the information broadcast, consensus, and accounting processes of the blockchain. Due to the limited power resources of drones, if a large amount of computing resources are used for consensus, it is likely to consume resources highly and affect nodes to perform combat tasks. Therefore, how to reasonably allocate the roles and functions of the nodes in the drone bee colony blockchain network (for example, nodes performing reconnaissance tasks can save resources and not participate in consensus), and optimize resource utilization is also a big challenge for the application of blockchain technology. challenge.
5 Conclusion
The distributed networking and wireless broadcast communication features of drone bee colonies are consistent with the decentralized characteristics of blockchain technology. The application of blockchain technology can effectively enhance the node identity management of drone bee colonies, prevent malicious node network intrusion, effectively prevent the spread of forged information through node consensus collaboration, and use blockchain storage to reliably record the battlefield environment information detected by bee colonies. . At present, the application of blockchain to enhance the safety of drone swarms is still in the preliminary research stage. Features such as failure of UAV nodes, unreliable transmission links, and limited resources will bring greater challenges to the application of blockchain technology. In order to improve the availability of blockchain technology, on the one hand, you can optimize the blockchain system, for example, you can use lightweight and consensus mechanisms to reduce node resource overhead; on the other hand, you can also use physical layer security technology and optimization Technologies such as relay transmission improve the quality of wireless transmission and improve the accuracy and reliability of information transmission between nodes.
references
[1] IJ Jensen, DF Selvaraj and P. Ranganathan. Blockchain technology for Networked swarms of Unmanned Aerial Vehicles (UAVs) [C]. 2019 IEEE 20th International symposium on A World of Wireless, Mobile and Multimedia Networks (WoWMoM), Washington, DC, USA, 2019: 1-7.
[2] Jiao Shijun, Wang Bingqie, Liu Jianhao, et al. A review of the research status of drone bee colonies at home and abroad [J]. Aerospace Electronic Countermeasure, 2019, 35 (1): 63-66.
[3] Kai Lei, Qichao Zhang, Junjun Lou, et al. Securing ICN-based UAV Ad Hoc Networks with Blockchain [J]. IEEE Communications Magazine, June 2019.
[4] Zha X, Ni W, Liu RP, et al. Secure data transmission and modelling in vehicular ad hoc networks [C]. IEEE Globecom Workshops, 2015: 1–6.
[5] Lamport L, Shostak R, Pease M. The Byzantine generals problem [J]. ACM Transactions on Programming Languages and Systems (TOPLAS), 1982, 4 (3): 382–401.
[6] IJ Jensen, DF Selvaraj, P. Ranganathan. Blockchain technology for Networked swarms of Unmanned Aerial Vehicles (UAVs) [C]. 2019 IEEE 20th International Symposium on A World of Wireless, Mobile and Multimedia Networks (WoWMoM), Washington, DC, USA, 2019: 1-7.
Analysis on Blockchain technology enhancing the security of UAV swarm system
FENG Zebing, LU Yue
(China Academy of Information and Communications Technology, Beijing 100191, China)
Abstract: Unmanned aerial vehicle (UAV) swarm warfare has advantages of scale and cost when facing high-intensity confrontation and dynamic battlefield changes. It has been widely used in the military field by countries around the world. At the same time, the drone swarm system has also become the target of network attacks, including malicious node intrusion, drone hijacking, wireless interference, data theft and other security risks. Blockchain, as a technology equipped with the characteristics of asymmetric encryption, chained data storage, node collaboration and consensus, has been studied as an effective technical means to resist the threat of distributed network attack, and can be utilized to effectively enhance the security of UAV swarm system. This paper firstly analyzes the current development situation and security risks of UAV swarm system. Then the feasibility of enhancing the UAV swarm system security with Blockchain technology is proposed. Finally, we introduce some techni cal challenges of applying Blockchain technology.
Key words: Unmanned aerial vehicle swarm; Blockchain; security risk
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Foreign media: Binance plans to acquire well-known data service provider CoinMarketCap for $ 400 million
- QKL123 market analysis | Crude oil broke $ 20 in the intraday market, the smoke-free smoke war spread to the capital market (0331)
- Lightning Labs launches digital authentication method based on Lightning Network, users do not need to enter a password to log in
- JD Blockchain traceability data is disclosed for the first time! Traceable product sales increase by nearly 30%
- Vitalik: ETH 2.0 multi-client test network expected to go live in April
- In the era of banknote printing, where are the opportunities for Bitcoin?
- Market analysis: the market rebound can be weak, do not chase up






