Interview with Sui’s Vice Chief Information Security Officer at Mysten Labs Considerations, Design, and Practice of Sui Blockchain Security
Interview with Sui's Vice CISO at Mysten Labs Sui Blockchain SecurityRecently, we had a face-to-face conversation with Christian Thompson, the Deputy Chief Information Security Officer of Mysten Labs, to understand his insights on the interdependence of security practices and his observations and evaluations of Sui developer security practices.
Below is the content of the interview:
Q1. What are the responsibilities of a CISO for a technology company?
The Chief Information Security Officer (CISO) has a very broad range of responsibilities and plays a crucial role in protecting our digital environment. One key task is collecting threat intelligence, which involves a deep understanding of the mindset of potential attackers: who they are, why they might target us, when they might launch an attack, what motivates their actions, and their level of proficiency in attack methods.
By having a clear understanding of potential adversaries and their capabilities, we can take proactive action to protect our systems. You can think of it as a jigsaw puzzle – if we know who the puzzle players are and how they operate, we can more effectively piece together those fragments. For example, we can combine their known tactics with the areas in our system that are most vulnerable to attacks. It’s like building a defense system that immediately alerts us when someone tries to breach our digital boundaries.
- Sei’s ultimate marketing rule Make headlines through news, and use sunshine airdrops to sweep the cryptocurrency community.
- 10 Ways NFTs are Boosting the African Tourism Industry
- Insights and Reflections Why is it difficult to hear the voices of female entrepreneurs in Web3?
Just like an alarm system alerts us when someone tries to break into our house, this defense setup can provide real-time alerts for any suspicious activities. This means we can quickly respond to potential threats and take appropriate measures to mitigate risks.
These key focuses cover a wide range of areas, including network security, data management, risks in various domains, architecture, compliance, governance, resilience, and reporting.
Some of the CISO’s roles also extend to protecting internal team members. We invest a lot of effort in understanding the level of risk for team members. These risk levels can change significantly, especially when team members travel to areas with violent tendencies or other insecure locations.
Q2. How does security differ when considering L1 blockchains like Sui?
In order to create a cohesive defense strategy like the Sui blockchain, multiple functionalities and services must be combined. This strategy should focus not only on what is considered weak areas but also on the responsibility of the Sui community to protect the interests of the entire ecosystem, including the network and developers building applications on the Sui platform. Achieving excellence in security is an expensive and challenging task, especially for startups.
To address this issue, the Sui Foundation is developing a product that extends security measures to a larger ecosystem. In fact, the Sui Foundation will provide security tools and services that are typically only available to larger organizations to smaller companies. This allows them to build in a more secure environment and enhances the confidence of end users and regulatory bodies. Our goal is to ensure that people can build on Sui efficiently and securely.
Q3. What tools and services are used in maintaining blockchain security?
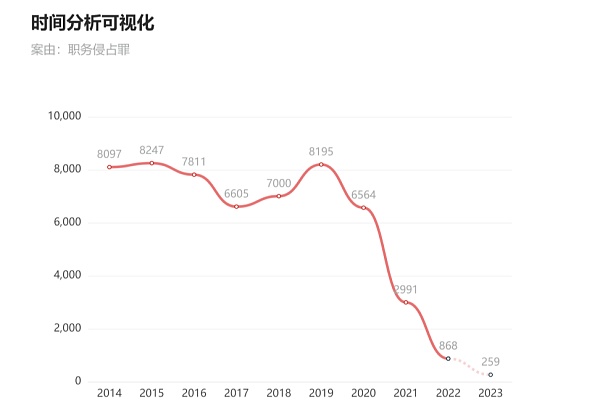
The following chart shows the types of services and tools that I believe proficient security teams currently use. These elements represent the diverse services that are essential for building a strong security framework. It is important to recognize that the true effectiveness lies not only in the individual existence of each service, but also in the intricate interactions between them. This includes understanding their relationships, the sequence of implementation, and the synergistic effects they create.

For these described services (listed on the chart), Sui Network utilizes specific tools or relies on service providers to deploy them. The Sui Foundation plans to package these components and offer them to any enterprise seeking to adopt them, in order to fully leverage their practicality. Therefore, the separate areas in the diagram symbolize a well-structured repository that is yet to be explored, available for entities pursuing strengthened security.
Q4. There are many elements in this chart. Are they equal and closely connected, or is there a priority mechanism?
Correct, there is a priority. The concept behind this chart is well thought out. Just like identifying matters that require immediate attention from scratch, you can view it as constructing a foundation for secure blocks, or you can view it as a basic security toolkit. This toolkit may include what we call “brand defense,” which means maintaining vigilance against any damage that may affect the company’s reputation. It involves intelligence gathering to monitor and mitigate any negative brand effects. In addition, “integrity” is also crucial, meaning the toolkit must have the ability to detect and address potential harm to the brand image.
Now, the toolkit is not a one-size-fits-all solution. Different organizations may need customized toolkits to adapt to their unique purposes. For example, a company closely related to coding may prioritize the development of “vulnerability detection capabilities.” This involves closely examining whether there are potential vulnerabilities in the system and performing tasks such as “fuzz testing” to stress test its code. On the other hand, consider a decentralized finance company and a gaming company. A decentralized finance company may lean towards focusing on a toolkit for regulatory risk, governance, and compliance. In contrast, a gaming company may focus more on operations, intelligence, and specific levels of security engineering.
Essentially, this chart summarizes the idea of adapting security strategies to different types of companies with different cultures and priorities.
Companies usually consider, “These are all my risks, how can I mitigate them?” Is this the perspective they start with, or are there other perspectives?
That’s right.
Q5. The toolkit seems to be the key way to keep the entire blockchain ecosystem secure. Considering that the key point of a public chain is that it is decentralized and permissionless, how do you maintain network security when anyone can access and participate in it?
Yes, the concept of toolkits plays a key role in maintaining the security of the entire ecosystem. The beauty of public chains lies in their decentralization and permissionless nature, which allows many people to review all aspects of it. Therefore, the ability to build necessary tools and promote education is crucial.
Imagine this: people within the ecosystem not only need to understand what is happening, but also need to know what tools are available and how to effectively use them. It is worth noting that many factors that affect the ecosystem go beyond the blockchain itself. Discussions on social media, fear, uncertainty, and doubt (FUD), as well as potential fraudulent activities, can all have an impact on the ecosystem. This emphasizes the importance of comprehensive awareness.
The third key factor is information exchange within the community. When individuals can communicate and collaborate, they enhance the collective knowledge base. Therefore, this is a three-pronged approach: education promotes knowledge learning, information promotes industry insights, and tools promote action. This combination provides the community with the ability to not only understand but also actively influence various behaviors.
Q6. How do ecosystems within the Sui communicate with each other?
There are various ways in which the Sui ecosystem communicates. The recent validator node summit provided individuals with a valuable platform to connect and exchange insights. There are also Builder Houses activities that provide such opportunities. In addition, I understand that the Sui Foundation plans to release a series of articles focusing on Sui security in the near future.
Daily communication channels include platforms such as Discord and Telegram, facilitating interaction between validator nodes, node operators, and other relevant parties. These forums not only increase people’s awareness of collaboration but also continue to expand over time, creating a continuously evolving platform for knowledge discussion and sharing.
Q7. The design of Sui Move is fundamentally more secure than other blockchain programming languages. How does this affect Sui’s approach to security?
It is undeniable that Move is safer compared to some other programming languages. What I want to add is that many people in the original team involved in Sui development focused on security. Therefore, it is not just a language issue, but also how various components of Sui are built, making it more resilient and difficult to exploit. Of course, this is not to say that there are no equally intelligent people in the security field. Given enough incentives, they will also work hard to find vulnerabilities. Therefore, experts need to understand who, when, where, why, and how such situations could occur. This is where our focus lies.
Q8. How do security incidents occurring elsewhere in Web3 affect the work being done by Sui?
Unfortunately, when security incidents occur in the Web3 space, they always attract widespread attention. However, these incidents are also valuable learning experiences. They prompt security professionals to delve into the mechanisms of vulnerabilities – how, what, when, who, and why. These insights provide additional insights for a wider field.
The Sui Foundation team has invested a lot of security resources to understand the identities and capabilities of these threat actors, focusing on deciphering their preferred targets and motives.
These vulnerabilities have brought us two different insights. First, for those affected, their plight deserves sympathy because these incidents have an impact on real people. Second, this is an opportunity to strengthen the Sui strategy. These lessons enable Sui to optimize and enhance its position to mitigate similar risks.
Q9. What is your view on security in the future Web3?
We are standing at the threshold of a new era, which marks the emergence of Web3 and the extraordinary technologies it brings – artificial intelligence, machine learning, augmented reality, virtual reality, and so on. What excites me is the incredible potential it holds. We are experiencing interfaces that are highly immersive and gaining access to information at an unprecedented speed and in unprecedented ways.
This transformation also extends to the field of security. Imagine having an artificial intelligence partner that can identify potential threats we are about to face, and even scenarios where artificial intelligence confronts artificial intelligence. There is no doubt that this is the direction we are striving for, and I look forward to Sui being at the forefront of these advanced technologies.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Exploring the Concept and Function of Layer 3 in Modular Blockchain
- Inventory of Seven Bills that Could Determine the Future of Cryptocurrency in the United States
- Bybit Compensation Manager’s Self-Embezzlement Analysis Vulnerabilities and Improvements in Blockchain Enterprise Financial Management
- The integration of blockchain and AI is a natural demand analysis of relevant use cases.
- Interview with Linea product manager ConsenSys entering the crowded Layer2 race, what is unique about Linea?
- Legal Perspectives on Blockchain Issues and Pathways
- Exploration of Full-Chain Games Freedom, Liberation, Authenticity, and the On-chain Deployment of Game Core