Introduction to blockchain | Explain the problem of General Byzantine and the principle of mining with the Romance of the Three Kingdoms
Today, ugly, let's talk about the issue of General Byzantine – to ensure that it is easy to understand.
Background introduction
The Byzantine General question was raised in 1982 by a master named Leslie Lamport (who won the Turing Award) on point-to-point information transmission and system fault tolerance. As soon as this Byzantine general question was raised, everyone felt that "well, the technical theory of the story" is very interesting.
Almost every book about Bitcoin will talk about this question, but after the translation of this question to China, it is a bit strange and difficult to understand. Everyone who studies bitcoin will see the problem of General Byzantine. Looks like I understand, but I don't seem to understand. So, do you really understand? The answer is, I don't understand.
- Blockchain Friends | Dozens of hardcore practitioners, chat for 4 hours, what do they say?
- Exclusive Compilation | Can Bitcoin enter the mainstream financial market with exchange-traded funds (ETFs)?
- Nestlé and Carrefour announce that consumers can access product data via blockchain
The Byzantine general itself is considered to be a good introduction, but it is not a good story. The Chinese are not familiar with it. A pair of stinky feet have been held for a long time, and it seems that the time is long. There is no such thing as the level of Leslie. This story is for a person with computer cryptography. It is a good analogy. It may not be for us.
Military division
Today we have deconstructed this issue and explained the so-called Byzantine generals in more detail with the well-known story of the Three Kingdoms.
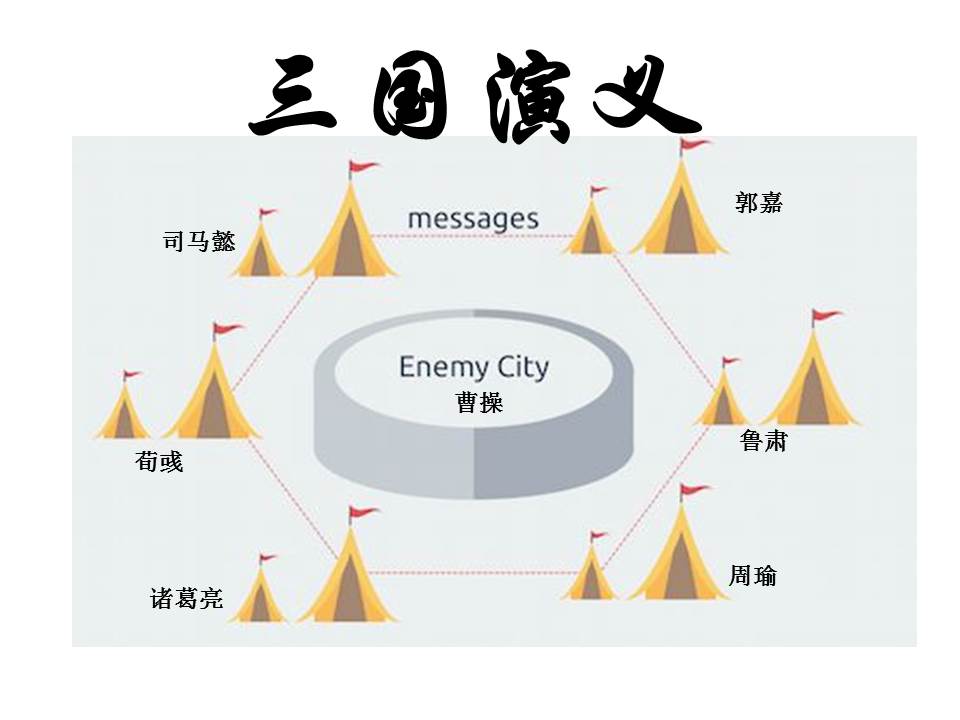
Pulling the timeline back to the Three Kingdoms era, we set a premise. In the era of the times, as long as a letter file is the information you wrote down, your signature and seal should be recognized, and reputation is very important. Then set a background, the boss at that time was Cao Cao, he under house arrest of the emperor Han Xiandi. There are ten generals or military divisions around Cao Cao's capital. There are Zhuge Liang, Yi, Guo Jia, Sun Ce, Xu Wei and other military divisions. These ten people, separated from each other (like distributed nodes), if more than half of the people unite, they can defeat Cao Cao and discuss whether or not to play Cao Cao.
At that time, the information was mainly transmitted by the pigeons flying around, and the flying pigeons between the ten military divisions were analogous to the point-to-point information transmission .
There are two problems here:
First , if there is a spy, in fact, there is no need to spy, Zhuge Liang's pigeons flew to Guo Jia, Guo Jiayi wants to fight the Lord, I will change it to you, then send it out. Ok? How to ensure that each node will not tamper with the information sent by another node (so-called malicious nodes impersonate normal nodes)?
Second , how to ensure that the records of each node (military or general) are consistent?
How to solve the first problem? Use asymmetric encryption technology.
For example, Zhuge Liang said that he would like to play Cao Cao and sign the seal of the letter. The process is encrypted with his own private key. After the completion of the secret, the pigeons fly to Guo Jia, Guo Jiayi, to fight the Lord. I want to change to Cao Cao, but I can’t change it.
The second question, how to ensure that the information recorded by each node (military or general) is the same?
The problem now is not the problem of not playing Cao Cao. The key is that the military order information recorded by everyone is the same.
such as,
Zhuge Liang’s message: Attacking Cao Cao from Lushan at 8:00 am on the 3rd of next month;
Guo Jia: I don't call Cao Cao;
Hey: Cao Yuxiang is not bad, don't fight first;
Lu Su: I took the waterway to play Cao Cao;
Sima Yi: I have been playing for 30 years, and the brothers are on the first…
It can be done without playing, but the information recorded by everyone needs to be consistent.
Every military division is qualified to record military order information. Whoever records it? Set up a math problem, and then whoever calculates the math problem first will record the information. Give it to a person to record and then post it to everyone. Whoever has a high IQ, who is a big man, is more likely to calculate a math problem first. Let him remember this information, then post the hero list, let everyone know who is playing this information (similar to bitcoin transaction information). Then everyone looked at the math problems and figured it out. This time the math problem is counted, and I started to fight for the next hero.
Incentives
Think about it, I am going to send a hero list (bookkeeping, broadcasting). This is a labor. Why do I have to work hard to calculate math problems? At this time, an incentive mechanism is added. Take the principle of Bitcoin as an example, calculate a math problem and dig out a block and reward 50 BTCs (the four-year reward is halved today, simplifying the model). In the Three Kingdoms era, a military division first calculated the math problem, recorded the information and posted the notice to issue the hero list, and sent you 50 gold or 50 beautiful women or 50 cities – this is similar to the bitcoin inventor. Cong design incentive mechanism.
At this time, everyone has enthusiasm, and they have to rush to calculate this math problem. After calculating it, remember the information and post the hero list. This is the PoW workload proof mechanism. The PoW workload proof mechanism ensures that the recorded information is consistent.
The problem of General Byzantine was solved perfectly.
Recruit three thousand visitors to mine
The story is here, it is even less important to play Cao Cao. These ten military divisions, everyone wants to calculate math problems, and then record the information, post this notice to the heroes list (posted to the whole network), you can get rewards, 50 ingots of gold or 50 cities (50 bits) The temptation of the coin is too great.
At this time, some people are thieves, such as Zhuge Liang, a person is not good. My brain has become smarter, and my IQ has increased, from CPU to GPU to ASIC chip level. However, it was discovered that the IQ of Guo Jia and Yu was also raised, from 100 to 200. Ok, I have money, I am the doorman, you recruit 300 guests, I recruit 3000 guests, 3000 people and 3000 people give me this math problem! The IQ base is higher and the calculation power is higher. The probability of calculating it first is greater. I figured out the problem first. Once published, other military divisions (nodes, miners) would not have to count this question again, to calculate the next question.
These 3,000 passengers are equivalent to 3,000 mining machines, which is the mining principle of Bitcoin .
Of course, everyone can continue to open the brain, Zhuge Liang door-to-door accommodation costs like the mining machine's electricity and maintenance costs; 3000 guests together to form a mine; there are mining pools, access to computing platforms and so on. Friends can make up their own brains and will not repeat them here.
Summary: Bitcoin solves the problem of General Byzantine. The first problem to be solved is to ensure that the information sent by me (an honest node) will not be modified by the person (another node), the method is asymmetric encryption technology; the second problem is to ensure that the information sent by everyone is The recorded data is consistent. The method is the PoW workload proof mechanism.
References in this article: Himalayan audio: Encrypted Erguotou ; Babbitt video: ignorant blockchain ; " Three Kingdoms "
Welcome to leave a message! Welcome to recommend to friends.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- French Finance Minister: Do your best to support blockchain technology innovation and let France take the lead
- Blockchain and games | IPFS's God-level application lies in the game?
- BMW and Mercedes-Benz have frequent rights protection, can blockchain technology be solved?
- The battle between bitcoin: big data vs personal privacy
- DCF model and crypto asset valuation
- Executives sentenced, currency prices were low, Korea's fifth largest cryptocurrency exchange COINNEST ceased operations
- You said that you are a Buddha holding money? NO, you are just a turtle






