Articles about Search Results Tron - Section 207

- You may be interested
- Will modularization become the ultimate...
- Bitcoin broke through $5,500 because th...
- Close the back door of the transaction,...
- Amidst the warlord chaos of LSDfi, who ...
- Analysts predict Approval of BTC ETF co...
- Gongxinbao is about to issue a heavywei...
- Iran's Bitcoin price soars? The r...
- Traditional corporate gospel, accountin...
- Onboarding Newbies to Crypto, One Shoe ...
- FBI warning: under the new crown epidem...
- Exploring the Effectiveness of Layer2 A...
- Wang Yongli, former vice president of B...
- Babbitt Column | Regulatory Sandbox Con...
- Hot money has not flowed into the crypt...
- The central bank, the SAFE, and the ban...
Mind Network: Enhancing Data Security and Privacy Protection in the Web3 Era
By combining the zero-trust principle with cutting-edge encryption technology, Mind Network empowers individuals, developers, and enterprises to protect their data, smart contracts, and AI…
US SEC: How to Use Howey Test to Determine Whether a Cryptocurrency is a Security?
This article is a compilation of the main content of the "Framework for "Investment Contract" Analysis of Digital Assets" published by the SEC, which…
Summarizing the three major innovations of Uniswap V4
If you care about DeFi and its future, you should read this article to gain a deeper understanding of Uniswap V4.
Deep analysis of the latest vulnerability “Hamster Wheel” in Sui blockchain
In this article, we share the details of the "hamster wheel" attack technique discovered by the CertiK Skyfall team, explaining how this new type…
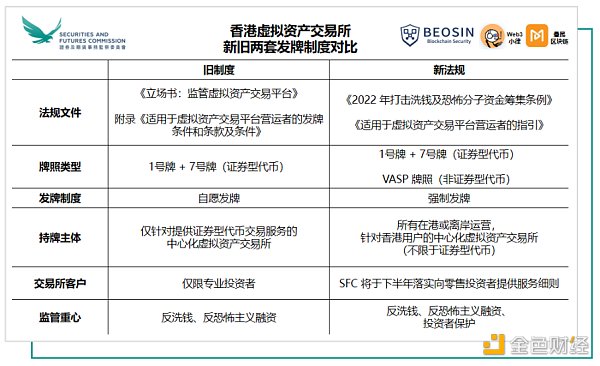
Future Web3 New Chapter: Triple Impact of VSAP on Exchanges, Financial Markets, and TradFi
With the rapid development of the virtual currency market, more and more people are investing in and trading virtual currencies. However, due to the…
Why did Azuki’s Elementals release collide with another release?
Over the past three months, Azuki has gone against market trends and successfully risen to become the strongest blue-chip project. However, the release of…
Future of Web3: Triple Impact of VSAP on Exchanges, Financial Markets, and TradFi
With the rapid development of the virtual currency market, more and more people are investing and trading in virtual currencies. However, due to the…
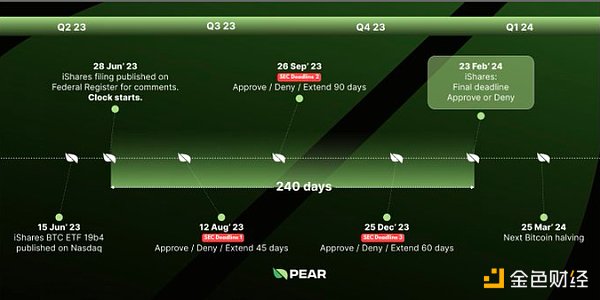
BlackRock’s Bitcoin ETF Key Dates and Timeline for Listing
In this article, we will learn about the key dates and timetable for the BlackRock Bitcoin ETF, and what preparations we need to make…
Chainlink Proof of Reserve (PoR): Putting Transparency at the Forefront
Chainlink Proof of Reserve (PoR) takes a step towards improving the transparency of many core products in the cryptocurrency space. Chainlink PoR can update…
Analysis of the technical details and in-depth of the latest Sui vulnerability “Hamster Wheel”
Damage caused by the attack can still persist after network restarts, and can automatically spread in the Sui network, causing all nodes to endlessly…
Find the right Blockchain Investment for you
Web 3.0 is coming, whether buy Coins, NFTs or just Coding, everyone can participate.