Privacy Backtracking and Investment: Oligarchs are significant and future value can be expected
Source: Turbo Capital
(Figure shows the five dimensions of mainstream anonymous currency)
Guide
- Libra responds to G7 full text: Improving opportunities for cross-border payments
- The cryptocurrency developer 108 will (1): the craftsmen who hide behind the code
- The four operations of the correct investment in the encryption market: how to minimize losses to make a profit?
1. Privacy protection represents the ability to protect transactions and participants in a distributed network. However, at present, all kinds of digital pass transactions are only pseudonymous and not anonymous. Therefore, it is necessary to take certain measures to achieve anonymity and protect the privacy of users. Privacy protection not only reduces real-world privacy threats, but also ensures currency substitutability. Currently, it mainly includes privacy currency, smart contract privacy, privacy infrastructure and privacy research.
2. Based on the disclosure of online transactions and digital pass information, privacy coins were born. About 42 kinds of privacy coins have been online. However, among the many privacy currencies, only 12 kinds of privacy coins have a market value of more than 100 million, and only the top 4 market capitalization exceeds 2 billion, which is quite different from other market values. The total market value of 5-10 private currencies is not comparable to the first. The market value of the four people, the oligarchy situation is obvious.
3. Among them, the main functions of the three mainstream privacy coins XMR, DASH and Zcash are concentrated on the currency payment function. We can observe three according to some of its trading indicators, such as market value, active address number, number of transactions and transaction amount. Performance of the person.
4, the investment value of the privacy currency is mainly concentrated in three points: the urgent need for commercial transactions, the initial promotion of bitcoin is because of its anonymity and people's concern for their rights. To choose the right investment, you need to consider the market value, code update speed, team strength, technology and user scale.
table of Contents
The first chapter is the concept and role of blockchain privacy protection
1.1 Concept: Privacy protection represents the ability to protect transactions and participants in a distributed network
1.2 Significance: On the one hand to reduce the privacy threat of the real world, on the other hand to ensure the exchangeability of money
1.3 Classification: Privacy, Smart Contracts, Privacy Infrastructure, Privacy Research
Chapter II Historical Development of Privacy Coins and Agreements
Chapter III Introduction to Mainstream Privacy Coins
3.1 The status quo of the privacy currency market: the top 4 market value exceeds 2 billion, and the oligopoly situation is significant
3.2 Three mainstream privacy currencies: XMR, DASH and Zcash are more focused
Chapter IV Investment Value of Privacy Coins
4.1 The investment value of the privacy currency: the necessity of commercial transactions and the concern for its own rights and interests
4.2 How to invest in private currency: not only must consider the purpose of investment, but also need to consider from multiple investment dimensions
The first chapter, the concept and significance of blockchain privacy protection
1.1 Concept: Privacy protection represents the ability to protect transactions and participants in a distributed network
Privacy protection is an extremely important concept in the blockchain and represents the ability to protect transactions and participants in a distributed network. Although the blockchain has always advocated its anonymity, from the current point of view, in all kinds of digital pass transactions, users do not need to use the real name, but use the public key hash value as the transaction identifier, unable to identify the trader, only It is only a pseudonym, and anonymity refers to a pseudonym with no relevance, but the digital pass transaction that reuses the public key hash as the transaction identifier can obviously establish an association. Therefore, the anonymity is not available at present, so it is necessary to take certain Measures to achieve anonymity and protect the privacy of users.
Privacy protection technology is not suddenly generated. Since ancient times, humans have used encryption to ensure the safety of some important information. The original encryption technology can be traced back to ancient times. The conformal replacement used by most early civilizations was somewhat of a primitive encryption technique. The earliest recorded use of this form replaced the Egyptian nobles' graves, but the purpose was to enhance the appeal of information. The earliest encryption technology used to protect important information occurred in the formulation of pottery glazes used to protect Mesopotamian clay tablets about 3,500 years ago.
For a long time, encryption technology was widely used to protect important political and military information. Ancient Greece wrote encrypted information on parchment. Only parchment wrapped in a cylinder of a certain size can interpret the information; ancient Rome moved the letters involving important information to a certain position in the Latin alphabet, only knowing this system and moving The talents of the letters to a certain position can be successfully interpreted, which is the Caesar password that we know later.
During the Middle Ages, the Caesars code was still the representative of the cryptography standard. In 800 AD, the famous Arab mathematician Al-Kindi developed a frequency analysis technique to make it easier to decrypt. This is the first time in human history to have a relative system of decoding attempts. In 1465, Leone Alberti developed multi-letter decoding, which is considered to be the opposite of the solution of Al-Kindi frequency analysis technology, which requires two different alphabets to encode information. One is the alphabet that writes the original information, and the second is a completely different alphabet, where the information appears after encoding. To interpret the information, you must know the alphabet in which the information was originally written. In addition, there is a popular early binary encoding method invented by the famous blogger Francis Bacon in 1623.
After centuries of development, at the end of the 17th century, Thomas Jefferson described a major breakthrough in cryptography, the encryption wheel we know later, which consists of a 36-letter ring on the moving wheel for complex implementation. The coding is also the early prototype of the Enigma machine. Enigma's devices used by Axis power supplies use rotary encoder wheels to write information and are widely used in World War II.
With the rise of computer technology, 128-digit encryption coding has become the standard setting for many sensitive devices and computer systems. At the beginning of 1990, quantum cryptography, which was fully developed by computer scientists, also raised the level of modern cryptography. Encryption techniques used in blockchains also use a variety of methods, including hash functions, public key encryption, and digital signatures. These techniques are primarily used to ensure the security of data stored on the blockchain and its verification. Trading matters. In the future, as long as there is sensitive information and data that needs to be protected, encryption technology still has a lot of room for development.
1.2 meaning
l reduce the privacy threat of the real world
Large companies like Google have been collecting offline payment data from Visa and MasterCard. Ali has been collecting online payment data from domestic users from Taobao Mall and using the data to create user portraits, claiming to be used for targeted customized advertising. We can reasonably guess that many other companies or individuals are also collecting this information, but it is not known how these companies and individuals will use the user's transaction data. Therefore, an important significance of blockchain privacy protection is to reduce the privacy threats in the real world. We can't completely protect our privacy, but we can use blockchain technology to keep our data in our hands and reduce the leakage channels.
l ensure currency replaceability
In theory, each unit of the same currency should be equivalent. Transparent transactions and traceability are one of the main advantages of digital certificates on the market today, but this feature can damage the digital pass. Sex, such as certain digital pass addresses are listed as unacceptable blacklists, then users will avoid any connection with the addresses on the blacklist, which will not only increase transaction costs, but ultimately reduce the circulation value of digital passes.
1.3 classification
q privacy currency
The privacy currency can realize all or part of the hidden transaction amount, sender and receiver information, restore the replaceability of the digital currency, and protect the privacy of the holder, aiming to provide complete privacy and non-traceability during the transaction. The current privacy currency can be divided into two categories: the condition is realized by a pseudonym; and the condition of non-association is achieved.
q smart contract privacy
The privacy in a smart contract is different from the privacy in a payment because the smart contract exposes the program code. Unfortunately, it turns out that procedural confusion is not possible, so smart contracts currently lack confidentiality to hide payment amounts and lack anonymity to hide the identity of senders and receivers.
q privacy infrastructure
The Web 3 stack also has an infrastructure project that focuses on privacy. For example, try to build a better Tor version of Orchid, build a private payment channel BOLT, build a NuCypher using a proxy re-encrypted decentralized key management system, and implement zk-STARKs in various blockchains including Ethereum. Starkware and so on.
q privacy research
Academic research in cryptography has driven innovation in the privacy arena. Privacy research mainly involves zero-knowledge, multi-party computing, and homomorphic encryption.
Chapter 2, Historical Development of Privacy Coins and Agreements: Generated by Privacy Disclosure and Digital Passage Problems
With the continuous development of the Internet and the increasing demand for technology, many well-known companies have been exposed to the problem of leaking a large number of user privacy, such as a large-scale data breach incident that occurred in early 2018, causing its market value to evaporate in just two days. Tens of millions of dollars. As a result, people turned their attention to digital passports with natural privacy attributes. However, at the time, although the digital certificate used a combination of numbers and letters as an address to hide part of the user's information to a certain extent, the repeated use of the address transaction easily matched the user information with the transaction data, and there was a great hidden danger in privacy. . For example, in August 2018, Atlas, a highly popular cryptocurrency investment platform in Brazil, was hacked, causing the exchange to leak 264,000 user personal information. Therefore, based on the disclosure of online transactions and digital pass information, privacy coins have emerged. At present, according to incomplete statistics, about 42 kinds of privacy coins have been launched.
Figure 1 Overview of the release date of the privacy currency

Source: Non-small
It is extremely difficult to implement anonymity in the blockchain, because all transactions are transparent, the supply of digital certificates needs to be publicly verified, and the anonymity mechanism must also pay attention to maintaining public verifiability while protecting privacy.
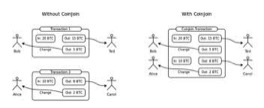
At the earliest, the first way people try to achieve anonymity is to pool money, that is, to mix the money of themselves and others in the pool of funds to confuse the ownership of the certificate to achieve the purpose, but this way can only provide more The basic anonymity, but also need to have absolute trust in the fund pool initiator, so there are certain flaws.
In order to improve the drawbacks of the money pool, the concept of the coin is born. The coin can eliminate the possibility of anonymous initiators stealing the pass, but because the background can record relevant transaction information, it strongly relies on anonymous digital signatures and anonymous login, and will limit the number of people participating in the coin each time, requiring participation. The person who mixes the coin agrees on the amount of the coin. In addition, research shows that even after a multi-round blender, if the user's wallet does not clear the browser cookie when making a payment, the user's wallet can be identified by technical means, because the coin will only cover the transaction link between the addresses. But won't completely destroy them. Even if the coinage device was improved for trusted third parties, such as CoinShuffle++, it could not avoid other defects.
Figure 2 Technology mechanism of the coin mixer
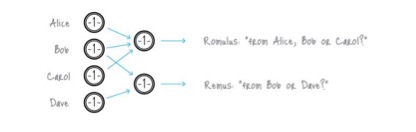
Another anonymous solution is the ring sign, that is, someone signs a transaction and can only track one group and not specifically track the person in the group. The ring sign scheme can automatically achieve anonymity, without the need for other users to specify who you want to mix with, or waiting for others to provide funds, just scan the blockchain to use the output, thus greatly increasing the anonymity of the cooperator program. However, the actual size of the ring sign currently implemented is limited, because the size of the transaction data increases linearly as the size of the ring increases, which means that on the basis of each transaction, the anonymity is limited by the number of ring participants, possibly There is a hidden danger of anonymization, and once there is a bug, the entire blockchain record will be anonymized and traceable, and cannot be corrected afterwards. In addition, the ring sign also sacrifices supply auditability, and there are problems with light wallet payment verification. Despite these shortcomings, the ring sign is currently a better anonymous technology.
Figure 3 Cryptonote and ring signing mechanism
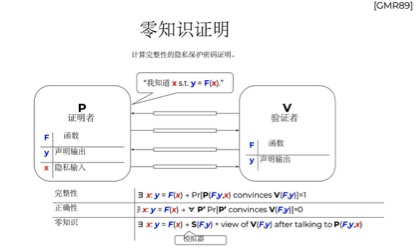
A case of zero-knowledge proof for an anonymous scheme emerged. Zero knowledge proof, that is, you do something or know proof of something, without revealing any other information. The most famous but the zk-SNARKS agreement supports ZCash. zk-SNARKs is a relatively new zero-knowledge encryption algorithm. Based on Zcash, many other anonymous coins have been forked, including Komodo, Zcoin, Horizon, Zclassic, Zencash, etc. It can be said that the zk-SNARKs protocol has created half of the anonymous currency. However, zk-SNARKs have great limitations on large-scale applications, so Professor Eli-Ben Sasson of Israel proposed a faster alternative to zk-SNARKs, zk-STARKs, which is eliminated with simpler symmetric encryption. zk-SNARKs require a lot of computational number theory hypotheses, but there are currently no privacy coins based on zk-STARKs.
Figure 4 Zero-knowledge proof technical mechanism
In addition, five privacy protocols have been created, such as TEE (Trusted Execution Environment), which isolates code execution, remote attestation, security configuration, data secure storage, and trusted path for code execution. APPs running in TEE are secure and almost impossible to access by third parties. They are a popular method of introducing trusted computing into blockchains; the Enigma protocol allows nodes to use smart segments of encrypted contracts for calculations without Need to decrypt; MimbleWimble protocol, designed to improve the scalability, privacy and substitutability of digital currency, combines multiple privacy protection technologies such as confidential transactions, transaction mix and dandelion agreement, hides the transaction amount, eliminates the transaction address, and Intermediate states can be combined to simplify transaction size while protecting transaction privacy; Zether (Quorum) protects participants' identities and existing accesses in the Quorum mechanism based on protecting transactions and node-level privacy. The combination of control features provides a powerful end-to-end security experience; SMPC (Secure Multiparty Computing) allows calculations to be performed on a set of inputs while maintaining the privacy of the input data, which can be used by parties in a secure token exchange to Exchange relevant information while maintaining the privacy of actual information and so on. These are new privacy protocols that have been created to improve the previous drawbacks.
Chapter III, Mainstream Privacy Currency
3.1 The status quo of the privacy currency market: the top 4 market value exceeds 2 billion, and the oligopoly situation is significant
At present, there are as many as 42 kinds of private currency circulating on the market, including the private currency that has not been publicly released and has no statistics. Among the more than 40 kinds of privacy coins, only 12 kinds of privacy coins have a market value of more than 100 million, and only the top 4 kinds of privacy coins have a market value of more than 2 billion, which is different from other market values, and the total market value of 5-10 private currencies is Compared with the market value of the 4th place, the oligarchy situation is obvious.
Table 1 Top Ten Mainstream Privacy Coins
 Source: Non-small
Source: Non-small
Figure 5 Top 10 privacy currency market value ratio
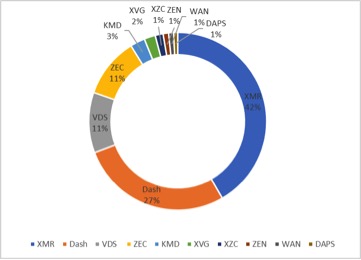
3.2 three mainstream privacy coins
Here, we only introduce the first three types of XMR, DASH and Zcash . The market value of these three categories ranks in the top 30 in all digital certificates, with a high degree of attention, and the main applications are concentrated in the currency function.
l XMR
Monroe, referred to as XMR, was born on April 18, 2014. There is no limit to the block size, so there is no risk of expansion. Monroe provides anonymity through a circular signature. In the blockchain network of Monroe, the network first mixes the signer's public key with another public key, and then signs the message, making it impossible for the outside world to distinguish. Which public key in the collection corresponds to the real signer.
l DASH
Dash is a digital certificate that supports real-time transactions and protects user privacy. It has made technical improvements based on Bitcoin, including second-level confirmation, citing the new X11 algorithm at the time, and reference times. The level network and the implementation of DarkSend, with good anonymity and decentralization features, is the first digital certificate to protect privacy.
l Zcash
It is the first blockchain system that uses a zero-knowledge proof mechanism that provides full payment confidentiality while still maintaining a decentralized network using a public blockchain. ZCash is a branch of bitcoin that retains the original bitcoin pattern and is modified based on bitcoin version 0.11.2 code. The difference is that the Zcash transaction automatically hides the sender, recipient and amount of all transactions on the blockchain. Only those who have the view key can see the contents of the transaction. Users have full control and they have the option to provide others with a view key.
The foothold based on these three kinds of digital certificates is in the function of money, so the performance of the three is mainly observed according to some of its trading indicators. (Blue in the picture: DASH; Deep red: ZEC; Orange: XMR)
(1) Market value
From the perspective of market value change, before January 2018, DASH has maintained a trend of rising volatility since its release in 2014. The trend of XMR is similar to DASH in time, and ZEC suffered a big devaluation in the market value just after its release. After the current trend is also gradually consistent with DASH and XMR. In general, the market trajectories of the three countries have gradually begun to match in 2017, and the growth momentum in 2017 has reached its peak at the end of the year. It also echoes the 17-year bull market, and has remained basically throughout the 18-year period. The trend of declining volatility did not begin to pick up slightly until 19 years.
Figure 6 XMR, DASH and Zcash market value comparison
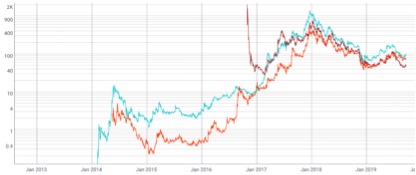
Source: coinmetrics
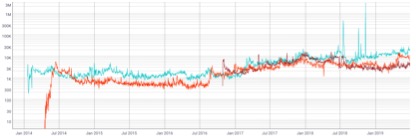
(2) Number of active addresses
According to the definition of coinmetrics, an active address is an address that initiates a transaction within a specific time. It can be seen that although the number of active addresses of DASH has been accompanied by a small decline in the process, the basic trend tends to rise steadily, and it has risen significantly in January 2019, which is inseparable from its market strategy. The number of Zcash active addresses has shown a significant downward trend since June 2018.
Figure 7 DASH and Zcash active address comparison

Source: coinmetrics
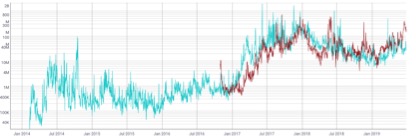
(3) Number of transactions
From the point of view of the number of transactions, on the whole, the number of transactions in DASH is almost higher than the other two types of certificates, especially after September 2018, the number of transactions in DASH has risen significantly, and there are 3 very obvious ups and downs. The trend of XMR and Zcash has been relatively stable since 2018, except that XMR is stable and rising, while Zcash is stable and slightly lower.
Figure 8 Comparison of XMR, DASH and Zcash transactions
Source: coinmetrics
(4) Transaction amount
In terms of transaction volume, the transaction volume of DASH and Zcash has maintained a volatility trend as a whole, especially in the 17-year bull market environment. Although Zcash has been accompanied by large ups and downs in 18 years, it is still impossible to avoid the big bear market environment tending to decline. In 19 years, as the environment began to pick up and supervision began to relax, both types of certificates began to turn into a turbulent upward trend.
Figure 9 DASH and Zcash transaction amount comparison
Source: coinmetrics
Chapter IV, Investment Value of Privacy Coins
4.1 The investment value of the privacy currency
l modern society, especially business transaction needs
Modern society, especially many commercial activities and transactions, sometimes contain very confidential information, including user transactions and other personal and private information, such as customer data breaches in Amazon in 2018. In March of this year, Ctrip also had a credit card information disclosure incident. It was exploded because Ctrip opened the debugging function of the user payment service excuses, resulting in its secure payment log being arbitrarily read, including cardholder name, ID card, bank card category, Private information such as bank card number and CVV code. Therefore, the demand for privacy in commercial transactions is very urgent.
l Advocating bitcoin was originally because of its anonymity
Initially, geeks praised Bitcoin because of the lack of supervision in the early days, the anonymity of Bitcoin was enough to protect the privacy of users, and when Bitcoin was more and more accepted by the mass market, its anonymity could not be guaranteed due to the current Most currencies do not support underground transactions very well, especially in dark-net transactions, so anonymous money has its necessity for development and special investment value.
l Pursuit of privacy has become part of people's concerns about their rights and interests
The era of big data is an era of data, that is, assets and information, and many companies and organizations are keen to collect data through electronic terminals, web browsing records, etc. in order to more accurately reach the audience. This way, the data is deeper. The mining and more comprehensive monitoring makes it easy for companies and organizations to forecast data and analyze the future situation of the audience.
However, personal data does not only contain part of the data that companies and organizations originally want to master. Most of the data is beyond the control and may also be the goods of inter-organizational transactions. These goods contain confidential information, which may include personally identifiable information, and other individuals. Information that is willing to be public, such as physical health, will cause great harm to personal privacy and is an important reason why people are increasingly pursuing privacy.
4.2 How to invest in privacy coins
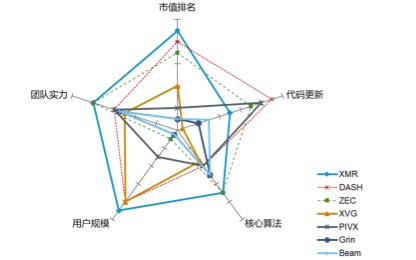
Although the current privacy currency is not as good as other types of digital certificates, but also more than 40 kinds, including the well-known private privacy coins XMR, Zcash and Dash, as well as emerging privacy coins XVG, PIVX, Grin and Beam, etc., many privacy coins are dazzling, So how do we choose the right investment?
From the perspective of investment rather than speculation, we mainly consider investment objects from five dimensions: market value, code update speed, team strength, technology and user size. among them:
l market value ranking
The market value mainly reflects the status of such private currency in the market and the degree of market acceptance. According to the short-term and long-term changes in the market value, it is determined whether the public is optimistic about such a privacy currency. After all, the market is an important criterion for testing the quality of the product. Although sometimes the quality of a project is not necessarily proportional to the market value, but in today's less mature blockchain market, market value can be used as a relatively objective evaluation criteria.
l code update
Blockchain is a transparent technology, especially for code is completely open and transparent, so through the speed of code update and the quality of the code, you can see the comprehensive strength of a team, and the reliability of the project and Whether the project has a long-term development plan.
l team strength
Although the code update can also reflect part of the team's strength, but many people are not technically born, and may not be able to visually see the technical strength of the team from the code. At this time, the entire team can only be seen from the background of the core team of the white paper or the project. Is there enough strength?
l Advanced technology
Since the privacy currency needs to have a sufficiently strong privacy protection mechanism, the technical requirements are high, so advanced technology can support the long-term development of a privacy currency. This condition reflects whether the privacy currency has the potential, or whether it can establish its own technology moat. The wider the moat, the more difficult it is for the latecomers to challenge, the more they can maintain their position, the more core competitiveness. .
l User scale
The user size here does not mean how many addresses participate in the transaction of the privacy currency, because it is not easy to judge whether there are several addresses behind the transaction to increase the transaction activity of the privacy currency. Of course, the number of addresses can also be used as a reference. index. The size of the user here mainly refers to the degree of belief of the user, focusing on that part of the audience. Although we have pointed out several indicators for your reference, the belief of the user determines the activity and market value of the privacy currency, so this is also a Very important indicator.
Take the well-known private privacy coins XMR, Zcash and Dash, as well as the emerging privacy coins XVG, PIVX, Grin and Beam as examples:
Table 2 Comparison of privacy coin investment dimensions
 Source: non-small, 2019.10.10
Source: non-small, 2019.10.10
Figure 10 Comparison of five dimensions of mainstream anonymous currency
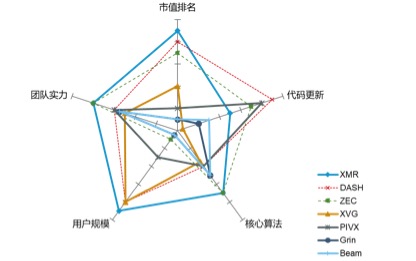
Through the above data, we can easily find that the old-fashioned privacy currency still occupies the unshakable position of the head, the market value is basically kept within the top 30 of all encryption certificates, and the code submissions are kept at a relatively high frequency, and emerging. The market value of the privacy currency is relatively backward, and the overall market value is larger than that of the old-fashioned privacy currency. Except for PIVX, the frequency of update of other emerging privacy currency codes is not high, and of course, the reasons for the late appearance, such as Grin and Beam.
In terms of technical difficulty, for example, XMR uses core technologies including Ring Signatures, Stealth Addresses and Ring CT, mainly through multi-party co-signing, senders using one-time random wallet address and encrypted transaction amount for privacy. Protection, and Zcash is a key technology that uses Zk-SNARKS and Shielded Transactions. It can prove the correctness of a given statement without revealing any information, and includes both open transaction forms and anonymous transaction forms. The purpose of both is to achieve anonymity by creating a homogenous digital pass, the difference is that XMR's privacy attributes are inherent, and Zcash's privacy attributes are optional. The emerging privacy coins, Grin and Beam, use the MimbleWimble protocol to negotiate transactions through wallet direct exchanges, thus avoiding transaction addresses. At the same time, MW's Confidential Transaction can hide the amount of the transaction and protect privacy. Technically speaking, Zcash and XMR have greater privacy and MW-like projects, such as the MW-type agreement, which has to be resolved before the transaction is confirmed, and Zcash has implemented encryption measures since the transaction. In addition, XMR and Zcash have undergone several years of actual verification, and Grin and Beam still need to improve.
From the perspective of user scale, the gap between these types of privacy coins is large. First, the old privacy of XMR and DASH users exceeds 30W, and the emerging privacy of only XVG users can compete, but in fact XVG was released in 2014, and the big bull market that experienced the blockchain in the middle accumulated A large number of users. The remaining few privacy currency users are small, mostly emerging privacy coins, which is also related to the overall market.
In summary, if users who want to invest in privacy currency need to consider their own investment objectives, if it is necessary to ensure basic security benefits, it is recommended to invest in relatively veteran and stable privacy currencies, which are relatively low risk; if it is necessary to consider For growth investment, you can consider the old-fashioned private currency and up-and-coming talents, or a combination of currencies similar to the old-fashioned private currency technology, which will reduce some of the risks while striving for profit; if it is for high profits, it is recommended to invest. Emerging privacy coins, although extremely risky, have the potential for high returns.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- New Balance's latest sneakers are coming soon, plus the blockchain hidden gameplay do you know?
- Deputy Governor of the Bank of France: Encrypted assets have the potential to replace the traditional banking system, stabilizing the currency or will have a systemic impact
- If Solana succeeds, does it mean that all the shards are scams?
- Telegram insists that Gram is not a security, former SEC legal counsel: this is just a struggle
- The first full text! Libra Association calls out the G7: Libra can coexist harmoniously with the central bank's digital currency
- Explore the cemetery of cryptocurrencies: Who killed the altcoin?
- Getting started with blockchain | What is a good digital currency valuation model?






