Research Report | The biggest hidden danger of blockchain security in 2020 is it
According to data from the blockchain security company PeckShield, there were a total of 177 blockchain security incidents in 2019, including 63 major security incidents, with a total loss of US $ 7.679 billion, a 60% increase from 2018. .
Text | Odaily Planet Daily & PeckShield
Edit | Mandy
Production | Odaily Planet Daily (ID: o-daily)
- Business Insider predicts that Libra will not be officially released in 2020, and China will release digital currency
- Instead of gaining weight, build a knowledge map of the blockchain in 7 days and 14 hours | Babbitt Industry Welcome Orientation
- Revisiting 2020, Bitcoin wants to say
According to data from the blockchain security company PeckShield, there were a total of 177 blockchain security incidents in 2019, including 63 major security incidents, with a total loss of US $ 7.679 billion, a 60% increase from 2018. .
From the perspective of the segmented track, in 2019, blockchain security incidents involve exchanges, smart contracts & DApps, DeFi, wealth management wallets and other fields, which are the closest places to transactions.
Although the overall security awareness and measures of developers have been improved in the past year, and basic attacks such as DApps, smart contracts, and other existing overflows, replays, and random numbers have been reduced overall, this has also forced the upgrade of hacking methods. Their methods of attack have diversified. Taking the DApp attack on EOS as an example, hackers have switched from traditional overflow attacks, fake transfer attacks, random number cracking to transaction blocking and transaction memo attacks, etc., and do not follow the "common sense" card.
At the same time, the reasons behind the security crisis have become increasingly "magic": fancy "holes" such as the loss of private keys, backdoors for code reservation, attacks on cold wallets, and the strange death of the founder let us know: technical bugs are easy to remove, and human BUG is difficult to level.
In addition, we found that DeFi, the most watched dark horse in 2019, began to be targeted by hackers. DeFi products are mostly based on smart contracts and interactive protocols. The code is generally open source, and the assets are completely on the chain. At present, prevention is still insufficient, and the industry has large potential for growth. In the future, it may become the target of hackers' key attacks.
So, what new types of attacks should alert practitioners? What security issues are becoming common in the industry? Which vulnerabilities and security incidents deserve widespread attention? 2020 How can we continue to hold this lifeline?
In this report, Odaily Planet Daily and PeckShield sent a shield to review the most comprehensive security data in 2019, focusing on five major areas, and counting the serious challenges the industry is facing. It is recommended to collect.
Exchange security crisis never stops
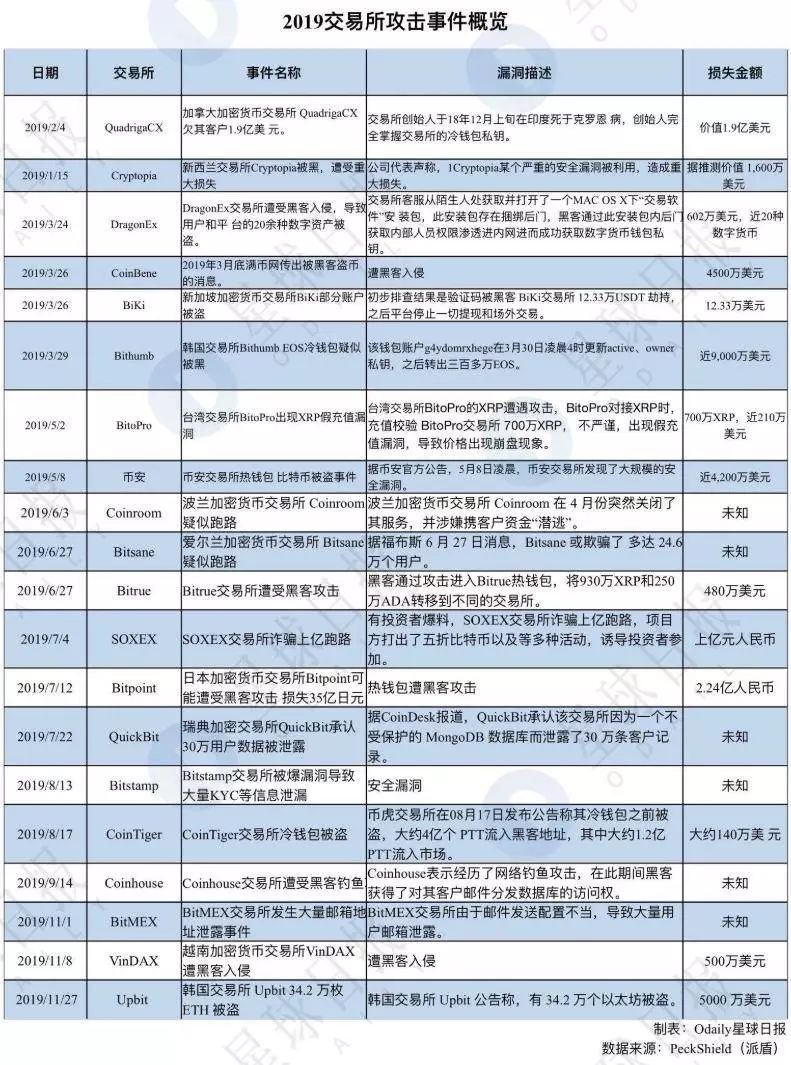
1.Overview of exchange attacks in 2019
Due to the large amount of funds gathered by exchanges, the difficulty of recovering stolen assets, and the insufficient attention paid to the security of some exchanges, trading platforms have been the focus of hackers' attacks.
The exchange theft in 2019 is not uncommon: On January 14, Cryptopia lost $ 16 million in tokens after being attacked, and subsequently declared bankruptcy; On March 24, DragonEx was compromised and lost more than $ 6 million in cryptocurrency; in March On the 29th, Bithumb stole 3 million EOS and 20 million XRP. After that, South Korean Upbit suffered a hacker attack and lost 340,000 ETH.
According to data from the blockchain security company PeckShield, in 2019, there will be more than 20 exchange security incidents, of which more than 7 will be the digital asset theft incidents of the exchanges, and the rest will include exchange runways and exchange information. Leaks and other asset loss incidents cost more than $ 800 million.
2. Binance stolen 7074 BTC incident
Among the published incidents, the biggest impact was the theft of 7074 BTC by Binance. At 01:15 in the morning of May 08, 2019, Binance, the world's largest exchange, announced that it suffered hacking and lost 7,074 BTC (about 41 million U.S. dollars).
According to Binance's official announcement, this is a large-scale systemic attack. Hackers mainly use composite attack technologies, including phishing, virus and other attack methods, to obtain a large number of user API keys, Google verification 2FA codes, and other related Information for withdrawal operations.
After the news was fermented, it immediately triggered market turmoil. Binance platform coin BNB fell more than 10% for a short time, which also caused mainstream digital currencies such as BTC to fall by more than 2%.
However, Binance soon promised to use the "SAFU Fund" to fully bear all the losses of this attack. The fund was established in July 2018, and 10% of all transaction fees received will be allocated to it to provide coverage for potential vulnerabilities. In addition, Binance also began a week-long security review, suspending users' deposits and withdrawals.
Centralized exchanges, as guardians of user assets, are already on the list of hackers' key concerns. They should increase security investment and strengthen their protection capabilities. If the theft of a centralized exchange happens again and again, end users will choose to vote with their feet.
It is worth noting that, six months after Binance was attacked, Binance CEO Zhao Changpeng told Odaily Planet Daily that its security performance has been improved by several grades.
"Now Binance can already achieve a zero-trust foundation, and no one's computer can break through our security system. Any operation requires the cooperation of several people in order to obtain full permissions. This design concept is similar to "Multi-signature." In this way, if any one person fails, no loss will occur, and multiple people will make mistakes at the same time. "Zhao Changpeng said.
Odaily Planet Daily attached a full path restoration of assets on the stolen chain by PeckShield security personnel. Through the following three digital asset full-path transfer diagrams, we can clearly see that within 24 hours after Binance was stolen, Buddhist hackers calmly "stolen" the entire process.
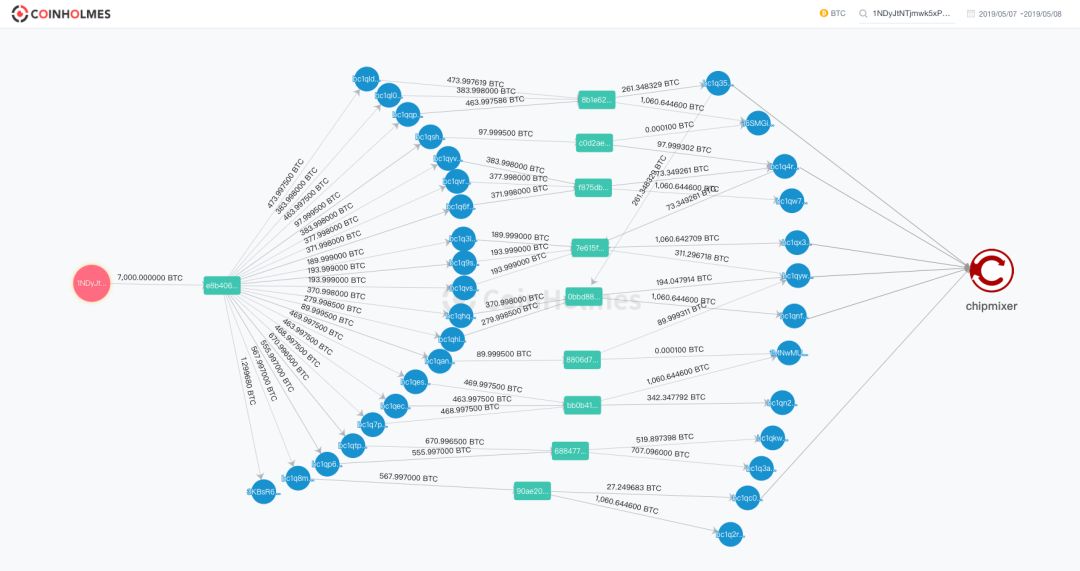
Step 1: 20 major decentralized storage addresses
After the hacking was successful, the funds were first transferred and stored in a decentralized manner. A total of 7,074 BTCs were distributed at 20 main (more than 1 BTC) new addresses with an amount ranging from 100 to 600 per address.
Step 2: Start to aggregate addresses and implement asset transfers
After storing the stolen 7,074 BTC, 7 hours later, the hacker began to organize the funds again, first clearing 2 of the 20 addresses, and storing 2 of them with 566 and 671, respectively. BTC is aggregated into 1,226 BTCs and transferred to two new addresses starting with bc1qkwu and bc1q3a5. Finally, 519.9 BTCs in the funds were transferred to another address, and the remaining 707.1 BTCs stayed at the original address.
Finally, the funds are transferred to the 7 addresses starting with bc1q2rd, 16SMGih, 1MNwMUR, bc1qw7g, bc1qnf2, bc1qx36, and bc1q3a5.
Step 3: Implement money laundering through ChipMixer.
In a period of time thereafter, hackers began to perform money laundering operations in batches, split the funds into small amounts, and then confuse them with tools like ChipMixer, and then sold them off-site OTC channels.
Recommended reading: "7000 Bitcoin Stolen by Binance"
3.How Exchanges Keep Their Lifeline
The theft of Binance reveals that the challenges facing exchange security are particularly daunting. In addition to consolidating the security of its own servers, Binance also needs to be aware of whether the intermediary asset custody service has been compromised by Trojan horses, especially if the user client is hijacked.
At the same time, the exchange also needs to strengthen the review mechanism from the business layer, such as the classification of automated withdrawal limits and the manual review of withdrawals.
Generally speaking, the security issues of exchanges are mainly divided into two aspects: technology and business. Security issues in technology are mainly three aspects: blockchain wallet security, software system security, and server network security; business security issues are mainly It is business process security and internal governance security.
At present, the general way for centralized exchanges to ensure security is to improve the business risk control system, to achieve the security guarantee of encrypted assets through technologies such as hot and cold separation and three-party multi-signature.
Generally, centralized exchanges are found to be attacked, and most of them will stop withdrawing coins to check the losses, and formulate a response method based on the scale of the losses. If the asset loss that has occurred is too large and the exchange cannot continue to operate, it will generally go through bankruptcy liquidation procedures .
There is also a big problem in the security of exchanges. When security risks and assets occur, the exchange cannot prove itself innocently, and cannot prove whether these assets are truly stolen or supervised. This poses a very serious problem for the management and operators of the exchange Big challenge.
At present, it seems that fully decentralized exchanges can effectively alleviate the problems of the security technology and business of the exchanges. However, issues such as ease of use, cost, and technical strength still limit the acquisition of customers by decentralized exchanges. And development.
Finally, in the face of the stolen incident, the exchange itself, in addition to actively responding and calmly seeking a feasible way to make up for the loss, is more important to make a clear statement of the consequences of the matter, and to the extent possible, tolerate Users are implicated or harmed, learn from their lessons and sum up their experiences, perform the most stringent security self-tests, and avoid repeating mistakes. Cherishing the trust given by investors and users is the bottom line that exchanges should have.
Smart contracts & DApp ecological loopholes are gradually decreasing
1. Overview of 2019 DApp Vulnerabilities
According to PeckShield statistics, as of early December 2019, there were 101 smart contract & DApp security incidents. Most of the hacked incidents occurred in EOS DApp, followed by TRON DApp, and the ETH ecosystem has increased maturity and stability. Three hacked incidents occurred. As of December 2019, the total hacked DApps of the three major platforms exceeded US $ 10 million.
Although the amount of losses is still huge, PeckShield found that in 2019, some simple and threatening vulnerabilities in the smart contract & DApp ecosystem are gradually decreasing. Although hackers continue to carry out net-attack attacks, but The project developer's basic security attack and defense awareness has been initially formed, and some lower-level security vulnerabilities have been significantly reduced.
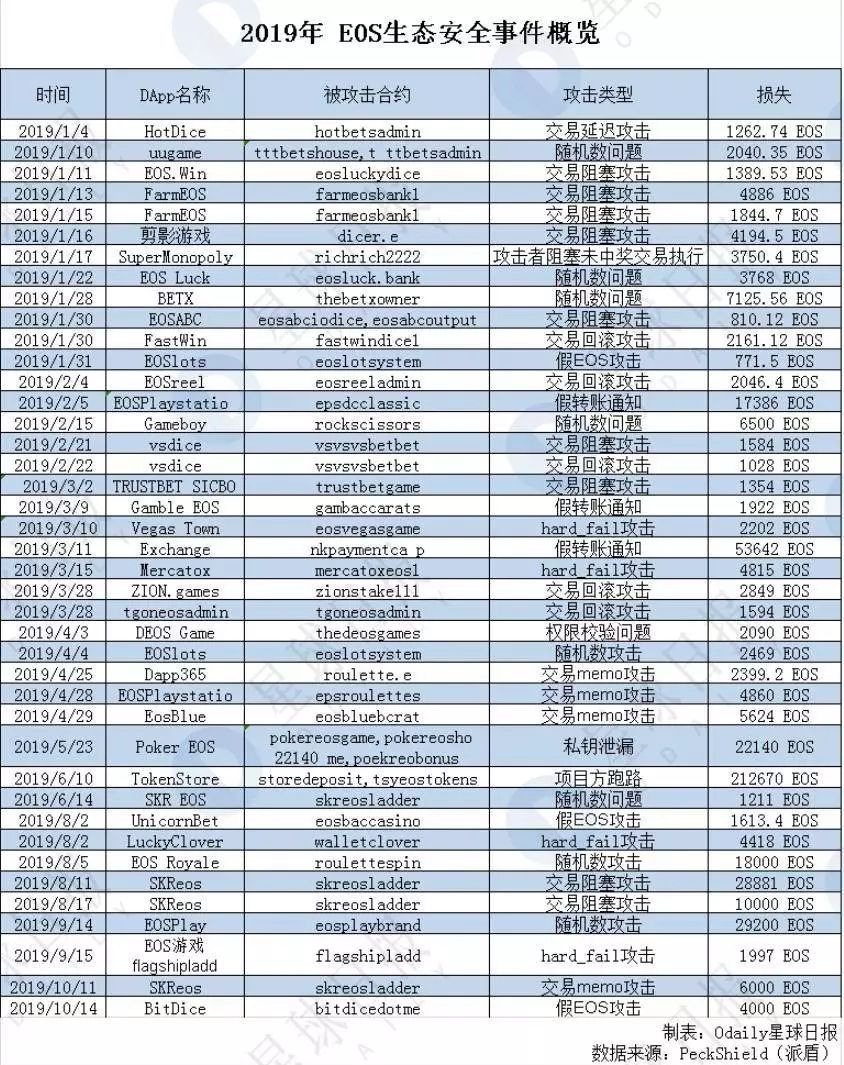
A total of 78 typical attack events occurred on the EOS public chain this year. The Odaily Planet Daily counted the cases of losses over 1000 EOS (see the table below) and found that the concentrated outbreak period from January to April accounted for the entire year ’s attack events. 70%. The attack methods mainly include transaction blocking, rollback transaction attack, fake transfer notification, random number cracking, etc. Among them, 9 are transaction blocking attacks, 8 are attacks caused by random number problems, and 5 are transaction rollback attacks.
Different from previous contract layer attacks such as random numbers or transaction rollback attacks, transaction blocking attacks are attacks that take advantage of the underlying public chain defects. Zhongzhao applications include EOS.Win, FarmEOS, silhouette games, Popular DAPPs such as EOSABC and SKReos, among which SKReos have been reported many times before that they suffered from transaction blocking and random number attacks.
After in-depth analysis, it was found that the transaction blocking attack is a fatal denial of service vulnerability that exists in the main network layer. The attacker can initiate a large number of junk delayed transactions, causing the EOS-wide super node (BP) to be unable to package other normal transactions, that is, by blocking the packaging of normal users. Transactions paralyzed the EOS network.
Because the vulnerability is essentially a low-level mainnet problem, any DApp game that has to rely on relevant on-chain factors such as account balance or time to generate random numbers is likely to be attacked. This is why a large number of EOS DApps were attacked in January.
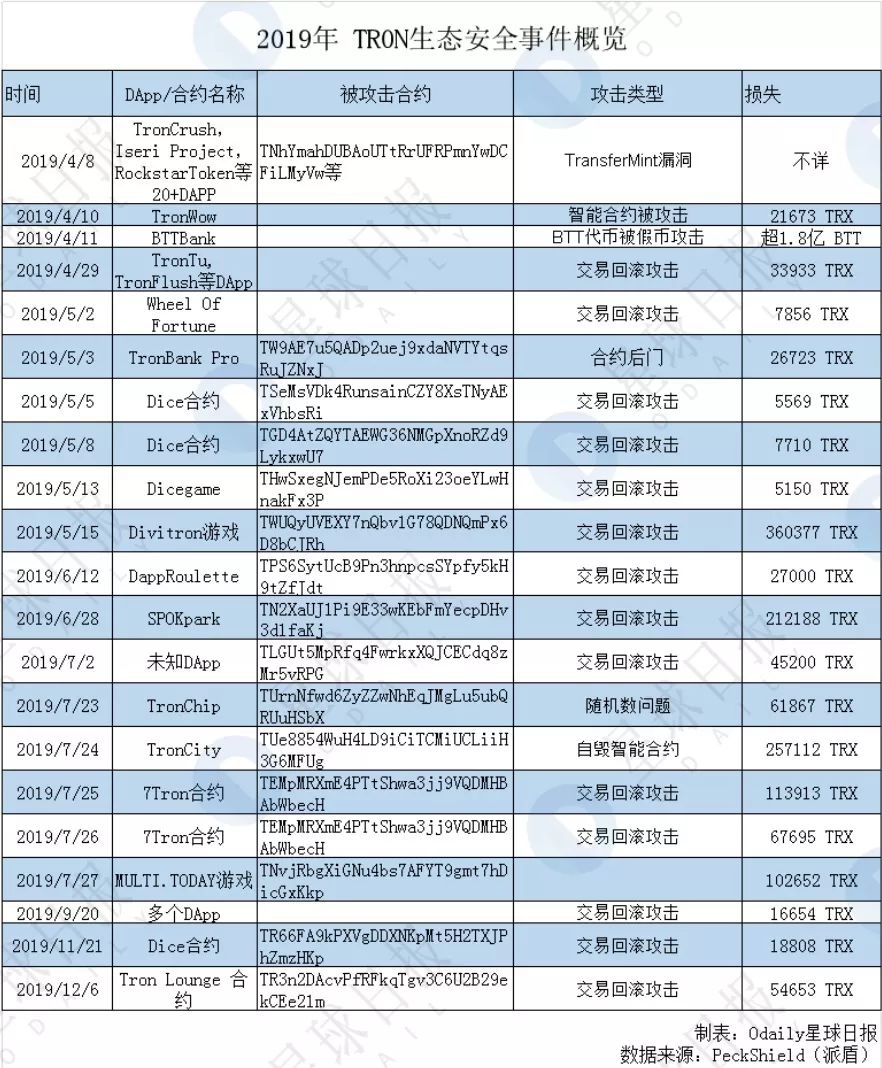
In 2019, there were nearly 20 typical attack events on the TRON public chain, which were mainly concentrated in April, May, and July. They were mainly small-scale attacks, and the attack methods were mainly transaction rollback attacks.
The time when the hacker starts is related to the price of TRX. According to BitUniverse data, March to May 2019 are the months in which the TRON token has the largest increase throughout the year, and reached its peak of the year on April 29 ( 0.09 USDT). On this day, multiple DApps including TronTu, TronFlush were attacked by hackers to roll back the network.
By deploying attack contracts, hackers continue to place fixed bets on multiple DApp contract addresses. Each time a bet is placed, if the profit is successful, the bet is continued. Otherwise, a rollback is implemented to ensure a stable win every time. This rollback attack lost a total of 33933 TRX, which is about 21364 yuan based on the price of TRX.
The ETH ecosystem did not have a serious DApp attack in 2019. One is that the number of spinach quiz contracts on the ETH public chain is small and the heat is not enough. The second is because the ETH smart contract project parties have done better in security. .
On October 14, 2019, Cheeze Wizards launched on the Ethereum mainnet. In less than 24 hours, player @samczsun reported to the official that there is a serious loophole in the game contract, and using this loophole can put the player in an invincible position. Cheeze Wizards then decided to use a forked solution to protect users' rights. The official has since fixed this vulnerability and deployed new smart contracts, while making up for the losses suffered by users.
This vulnerability also made Cheeze Wizards the first blockchain game to undergo a hard fork.
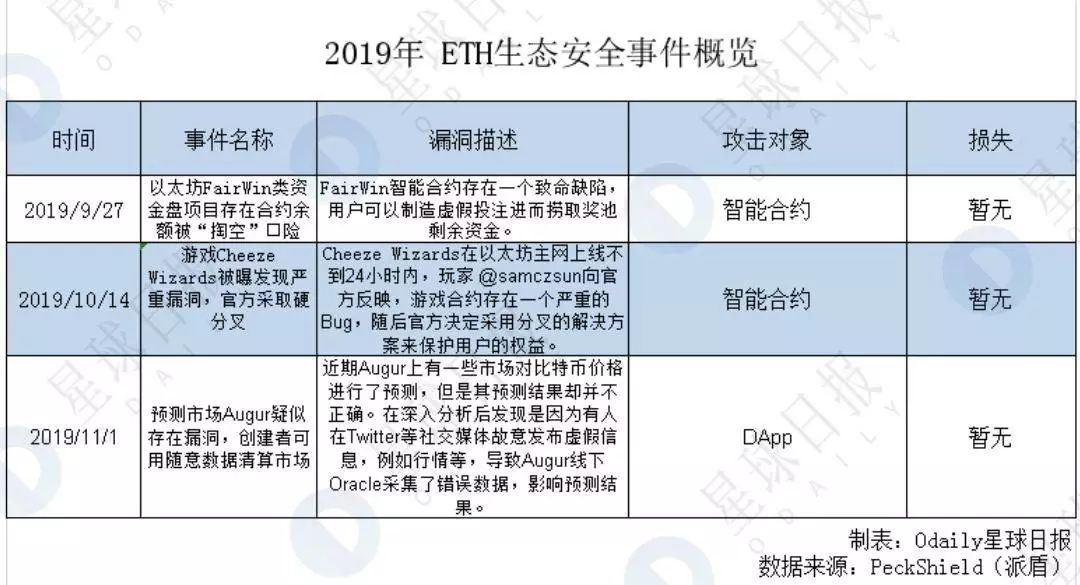
2. DApp attack: The evolution from EOS attack to TRON attack
In summary, Odaily Planet Daily found that in 2019, hacking DApps showed a trend of evolution from EOS attacks to TRON attacks.
In 2018, EOS detonated the DApp market, and many public chains began to compete in this market. Among them, TRON actively expanded the DApp ecosystem through a series of support plans. According to DAppTotal data, as of December 31, there were more than 600 active DApps in TRON, the total number of daily activities was close to 50,000, and the daily transaction volume exceeded 200 million TRX. These data make TRON seem to have the ability to compete with Ethereum and EOS in the DApp market.
At the same time that the TRON public chain DApp market is highly prosperous, it will inevitably attract hacker covets. At present, TRON has not been attacked as highly as EOS.
According to PeckShield statistics, during the entire year of 2018, 49 security incidents occurred on DApps on EOS, and the total loss caused by 12 attack methods reached US $ 3.19 million. Throughout 2019, there were a total of 80 EOS DApp security incidents with a loss of 2.79 million EOS. Overall, the number of DApp attacks on EOS has decreased. In 2018, there were only 1 TRON DApp security incident and 2 million TRX losses. In 2019, TRON DApp security incidents totaled 22, with 30.25 million TRX losses.
In April this year, the DApp TronBank on the wave field was attacked and lost more than 180 million BTT (valued at 850,000 yuan), which directly pushed the security ecology of the wave field to the cusp of public opinion.
Security personnel believe that hackers use the fake currency attack method by calling the invest function of the BTTBank smart contract, and then calling the withdraw function multiple times to retrieve the BTT real currency. As of now, BTTBank has lost a total of 180 million BTT. Preliminary analysis believes that this is a new type of vulnerability with widespread hazards that will threaten the security of multiple DApp-like contracts after the TransferMint vulnerability.
The DApp TronBank was attacked. Immediately afterwards, PeckShield monitoring showed that the hacker launched 1203 attacks on the TronWow game, a TronWow game, and made a total of 2,167,377 TRX.
According to preliminary analysis by security personnel, hackers bet 20 TRX each time, returning 1,940 TRX, a total of 23,004 TRX betting, returning over 94 times. The random number attack method currently exists in the EOS DApp ecosystem. At present, such attacks are gradually spreading to the TRON ecosystem, and developers need to be vigilant.
DeFi lending platform may become a key target for hackers in the future
1.Hackers start attacking DeFi smart contracts
2019 is considered the first year of DeFi by industry insiders. The lending market on the blockchain has become the most popular decentralized financial (DeFi) application scenario. The total borrowing generated through MakerDAO, Compound and dYdX has exceeded 600 million U.S. dollars, and the growth of DeFi market users has increased from thousands to the end of the year Nearly 180,000 people.
According to DAppTotal data, as of December 31, the overall value of the DeFi project hedging was US $ 874 million, of which the value of MakerDAO's hedging was US $ 310 million, accounting for 35.35%, and the value of EOSREX hedging was US $ 195 million, accounting for 22.33% , Edgeware lock-up value is 100 million US dollars, accounting for 11.50%, Compound, Synthetix, dYdX, Nuo and other DeFi applications accounted for a total of 30.82%.
In addition to the well-known lending market, stablecoins and decentralized exchanges are also the two major markets where DeFi is widely used, and the lending market is also known as the DeFi troika.
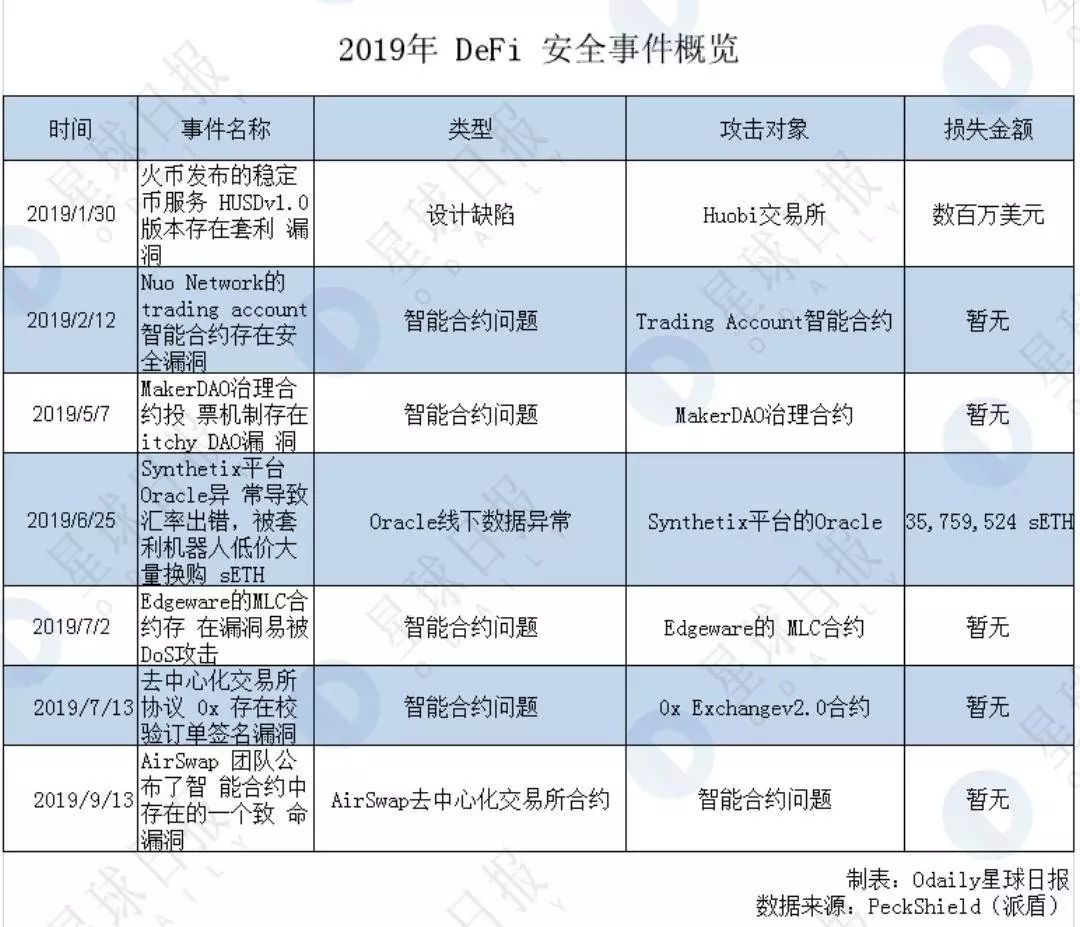
However, most DeFi products are built based on smart contracts and interactive protocols. The code is generally open source and the assets are completely on the chain. Therefore, it is also very easy to become the focus of hacking. According to PeckShield statistics, there are 7 typical cases in 2019. In the DeFi attack incident, hackers mainly attacked DeFi smart contracts.
2.MakerDao, AirSwap fix the vulnerabilities in time with the help of security companies
On May 07, 2019, Beijing time, blockchain security company Zeppelin issued a security alert to the DeFi star project MakerDAO on Ethereum, claiming that its governance contract has security vulnerabilities.
On the same day, an independent study by PeckShield found that the existence of the vulnerability was confirmed (PeckShield named it itchy DAO). Specifically: because of a certain flaw in the voting mechanism (vote (bytes32)) implemented by the governance contract, it is allowed to vote for A slate that does not yet exist (but contains a proposal that is being voted on). After the user has voted, the attacker can maliciously call free () to exit, reduce the number of valid votes for a valid proposal, and lock the voter's MKR tokens at the same time.
To put it simply, hackers can cause the following possible effects through this attack: 1. malicious manipulation of voting results; 2. because hackers deducted some votes in advance, causing real voters may not be able to unlock the lock.
PeckShield tracked the transfer of MKR tokens throughout the process and issued multiple warnings to the community, calling on MKR token holders to immediately transfer MKR tokens from old contracts.
The next day, PeckShield and Maker Company synchronized the details of the vulnerability. In the early morning of May 10, MakerDAO released a new version of the contract. Zeppelin and PeckShield also independently audited their new contracts and determined that the new version fixes the vulnerability. Because of the rapid response, the user did not lose in this vulnerability.
Another smart contract vulnerability occurred on September 13, 2019. The AirSwap team announced a fatal vulnerability in an AirSwap smart contract, which could allow users' assets to be maliciously stolen by their opponents under certain circumstances.
A deep analysis of AirSwap smart contracts by PeckShield security personnel found that this vulnerability only affected the recently launched Wrapper. This vulnerability could allow users' assets to be stolen maliciously by attackers. There were a total of 18 affected accounts, some of which had assets of tens of thousands to hundreds of thousands of dollars.
Subsequently, PeckShield security personnel independently analyzed the details of the vulnerability, communicated the details and the repair plan with the AirSwap team, and named the vulnerability "ItchySwap".
After discovering the problem, the AirSwap team rolled out the contract as soon as possible, and rolled back the AirSwap website to the previous contract. The entire process from the contract's launch to the problem repair lasted only 24 hours, without causing user losses.
In addition, it is worth noting that in addition to traditional centralized exchanges, the DeFi platform is also becoming a new channel for hackers to launder money. CoinHolmes, a subsidiary of PeckShield, monitored in October last year that in January 2019, some assets stolen by hackers from the Cryptopia exchange flowed into the Uniswap decentralized exchange and the "DeFi Bank" Compound. The main purpose is to use DeFi lending platform for obfuscated money laundering.
Regarding the technical issues of the two smart contract vulnerabilities, it is recommended to read:
"Detailed AirSwap Smart Contract Vulnerability"
https://www.odaily.com/post/5141298
"The Security Storm Behind the Upgrade of MakerDAO Governance Contracts"
https://www.odaily.com/post/5137754
Although the industry lost a small amount, it revealed a red flag that hackers are already focusing on the DeFi field. Once the DeFi platform's asset collateral scale and audience are on the order of magnitude again, this area is likely to be the next security incident-prone area after DApps.
Financial wallets, fund disks, phishing scams become industry tumors
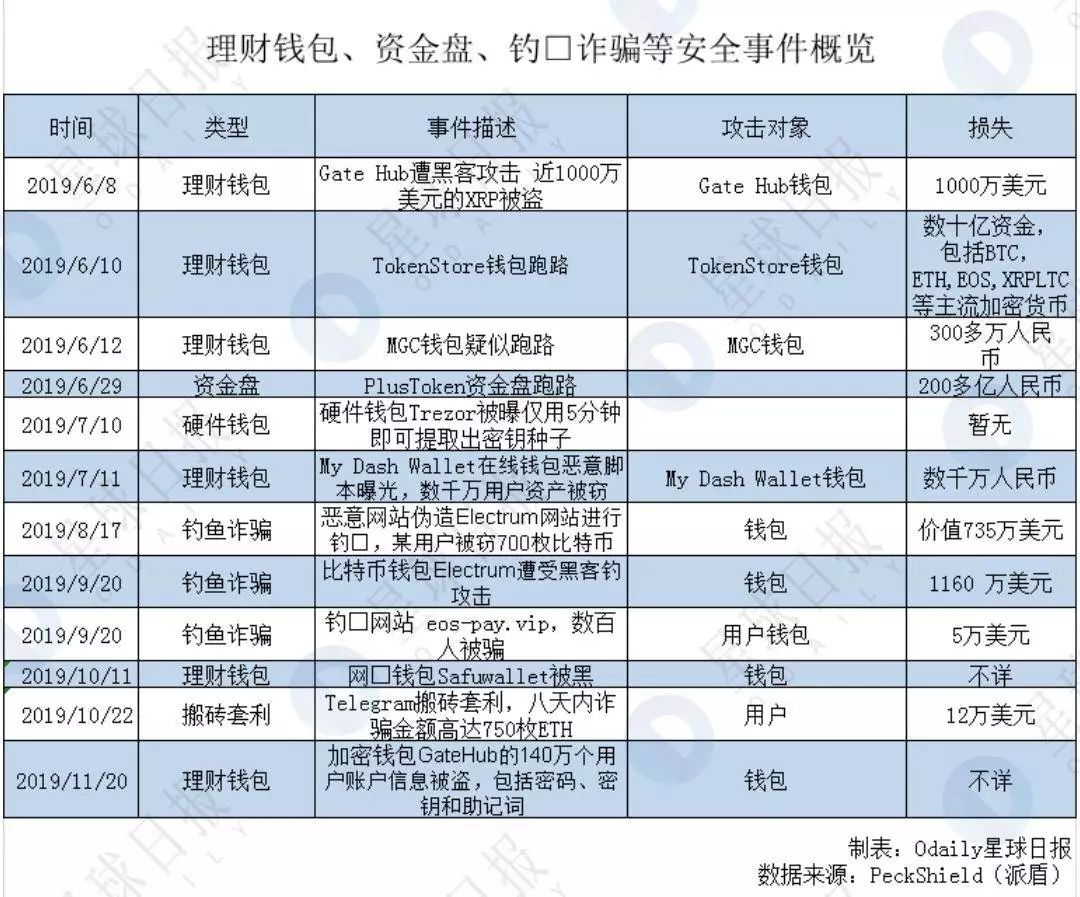
In 2019, wealth management wallets, money disks, and phishing scams have become a cancer in the industry. PlusToken, TokenStore, OneCoin, and other wealth management wallets were exposed, tens of billions of digital assets were taken away, and millions of investors embarked on a long "rights road."
Among them, the most eye-catching event is the PlusToken wallet run event, which is known as the first capital disk of the currency circle. On the day, many users reported that the PlusToken wallet was no longer available for withdrawal. Over 20 billion yuan, more than 3 million users have participated in the PlusToken wallet.
As early as 2018, articles questioned PlusToken as a MLM scam. Because from the perspective of the operating model, PlusToken is almost perfectly in line with all the characteristics of MLM-payment of membership, development of offline, and tier-level income.
By transferring a certain amount of digital currency into the official address of PlusToken, you can turn on the smart dog and get the “moving bricks” income, that is, pay for membership. You can get the qualification to develop offline by opening the smart dog, and by developing more offline Members, upgrade the membership level, get different percentages of rewards; personal income is linked to the number of downline and income, the highest level members enjoy project dividends, that is, the level of income.
In addition, PlusToken claims "10% -30% of monthly income", plus the transaction fee required by the exchange to withdraw, which means that the difference between the exchanges needs to be higher than this to be possible. If such an exchange does exist, it will go bankrupt in minutes.
The hidden danger of the public chain project-double spend attack
According to PeckShield, between January 05 and January 08, there were at least 15 suspected double-spend transactions on the ETC chain, with a total loss of 219,500 ETC and a value of about $ 1.1 million.
The so-called double spend attack means that a token has been spent twice or more. Simply put, the attacker transfers a token to another address, usually to the exchange for cash, and then uses the computing power in his hands to roll back the transfer transaction, and then transfer the token back to himself. address.
The double spend attack is also the most common attack method in the currency circle. Hackers usually choose tokens with low computing power. Prior to the ETC double spend attack, BTG, ZenCash, etc. also had such incidents.
Of course, in order to succeed in a double spend attack, you must first master the vast majority of computing power. The industry generally believes that computing power should exceed 51% in order to perform attack operations. Take the ETC double spend attack, for example, the hashrate of this attack is likely to come from the hashrate website NiceHash. The website's leaseable ETC computing power once accounted for 112% of ETC's entire network computing power, meeting the conditions of a double spend attack. At present, the website has stopped computing power rental.
The losses caused by this "double spend attack" were eventually paid by the exchange. Gate.io has stated in a statement: Although the 51% attack is caused by insufficient computing power of the ETC network and is not the responsibility of the trading platform, Gate.io will still bear all ETC losses.
Looking back on this security incident a year ago also gave us some inspiration. As a participant in the cryptocurrency ecosystem, preventing double-spend attacks may not just be the responsibility of the public chain. Exchanges, wallets, and investors must be vigilant.
For exchanges and wallets, the withdrawal confirmation requirements can be increased to reduce the risk of double spending. For example, some exchanges increased the number of confirmed deposits to 100 and the withdrawal confirmations to 400 after the ETC double spend attack.
For the project party, the mining algorithm can be upgraded. In addition, the project party needs to closely monitor changes in computing power to prevent attackers from attacking with limited computing power.
For users, in order to prevent transactions from being double spent, be sure to trade at regular exchanges. After suffering losses, contact the exchange or the project party as soon as possible to roll back the transaction in a timely manner. In addition, when trading some tokens with a small market value, special attention needs to be paid to prevent their computing power from being manipulated artificially.
The double-spend attack is also a rite of passage for the project. Projects that have stood the test of double spend attacks can go further in the world of blockchain.
Recommended reading:
"The attacker has not let go of ETC after taking millions of dollars away"
https://www.odaily.com/post/5135528
Prospects for the future development of blockchain security
Breaking down various security incidents in 2019, we also found some trends that deserve the attention of the entire blockchain practitioners.
First, exchanges are still the area where security risks are greatest.
The exchange is the closest place to the asset and has always been an important target for hacking. Security is naturally the most important core element.
At present, some exchanges choose to build their own security protection, hire professional security protection personnel with high pay, and build their own firewalls. But even so, front-line exchanges such as Binance still encountered security incidents, which also alarmed practitioners.
Other small exchanges choose to purchase a complete set of trading technologies and security protection from third-party technology providers. Although it seems not a big problem, to a certain extent, this is equivalent to opening up your own backyard to others, and the quality of safety is worrying.
In addition, the security of exchanges is inseparable from end users. In numerous reports, we also found multiple thefts, with only a small number of victims, and the security system of the exchange has not been breached. This is mainly due to the weak awareness of end-user protection, hacking attacks by hackers, leakage of their private information (accounts and passwords), and eventually security incidents.
Therefore, the security of exchanges requires not only the exchanges to improve their own protection capabilities, but also the end users to improve their self-protection awareness.
The second is the transfer of security incidents to the direction closer to assets such as DeFi.
In 2019, many DeFi products are sought after, especially decentralized lending.
However, most DeFi products are built based on smart contracts and interactive protocols. The code is generally open source and the assets are completely on the chain, so it is also very easy to become the focus of hacking.
From MakerDAO governance contract vulnerabilities to 0x protocol verification order signature defects, each vulnerability affects the security of thousands of encrypted assets. Although in the end, there was no danger, no accidents occurred, but there was no chance of luck in dealing with security issues.
For the developers of DeFi products, before the products are finally introduced to the market, they should look for professional security agencies to review their code, check for missing and fill in gaps, and protect user assets.
For users, for some DeFi products that have not undergone security audits, they should also be vigilant to prevent phishing attacks from theft of assets.
In addition, we must always be vigilant against criminals under the banner of the blockchain, bank funds, and fraud.
Only by establishing a set of strict security audit standards and procedures from the source to the terminal to escort users, can the industry flourish.
Security is a protracted battle, and every practitioner has the responsibility and obligation to participate.
References:
“ 2018 Annual Blockchain Security Report ''
DeFi Industry Report 2019
Tool website:
https://www.dapptotal.cn/analytics
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Compared with Bitcoin, will Ethereum be more risky in the past six months?
- Hedge funds short Zcash and XRP to hear what they say
- 22 halving coins detonated 2020: ferocious little coins, taking you to heaven and hell
- The most profitable cryptocurrency field is lending
- Overview of Cryptocurrency Market Regulation: Status, Demands, and Challenges
- Chief Economist of CBEX: Bitcoin lacks correlation with mainstream assets and can be included in investment portfolios
- If you halve, you will appreciate. Half a bitcoin is more valuable?





