Science | How the blockchain works (annotated version)
Blockchain technology is probably the greatest invention after the Internet. It allows people to exchange value without trust and decentralization. Suppose we have a bet between us and bet on San Francisco tomorrow's weather, the bet is $50. I bet that it will be sunny tomorrow, and you think it will be rainy. Today we have three ways to achieve this bet:
- We can trust each other. Whether it is raining or clearing, the loser pays the winner $50. If we are friends, this is of course a good way to achieve a bet. However, whether we are friends or strangers, there are 10,000 ways for losers to refuse to pay.
- We can convert the bet into a contract . Once a contract is signed, both parties are obliged to perform the bet and pay the bet. However, if the loser decides to refuse to perform, the winner has to pay extra and spend a lot of time to seek legal rights through legal means. Especially for small bets, this does not seem to be an optimal implementation.
- We can also invite neutral third parties . Players participating in the bet pay $50 each to a third party, and the third party will pay the $100 to the winner. However, this so-called third party is also likely to make a move to abscond. Therefore, this method is not fundamentally different from the first two methods: either mutual trust or contract .
The best solution is neither trust nor contract: we can't trust strangers, and it takes a lot of money and time to sign a contract. Blockchain technology is eye-catching in this respect because it gives us a third choice, which is safe, fast, and inexpensive.
The blockchain allows us to write a few lines of code and run a program on the chain, sending $50 to the program. This program will ensure this $100 security and automatically check tomorrow's weather conditions based on multiple data sources. Whether it is sunny or rainy, it will automatically transfer the money to the winner. Either party has the right to check the contract logic and cannot be changed or aborted once the program starts running on the chain. Perhaps this is a big deal for a $50 bet, but it's a common choice for home buying and selling and intercompany trading.
Editor's Note: As far as the current (July 3, 2019), the above description of the function of the blockchain is a bit exaggerated, it can't be done. But this does not affect the value of the subsequent part of this article, and I believe that after reading the article in detail, the reader can understand why the above paragraph is not feasible, but the blockchain still has its value.
- This year's Bitcoiner is not average. Analysts believe that investors are now more willing to hold Bitcoin than to convert to French currency.
- Sell Mt.Gox, leave Ripple to create stars, legendary life of coin technology genius Jed
- Li Xiaolai sends a new coin, build a new group, are you willing to help him pull the head?
This article does not delve into the technical details and only releases the knowledge that must be in order to understand the underlying logic and mechanisms of the technology.
Bitcoin basics

– Image courtesy of the author – The most well-known and widely discussed application of the blockchain is Bitcoin , a digital currency that can be used for product and service transactions, just like the US dollar, the euro, the renminbi, and other national currencies. Let us learn how it works by the first application of blockchain technology.
"Bitcoin gives us an experience we've never had before – enabling Internet users to transfer a unique digital asset to another user and make sure that the transfer is safe and secure, and everyone knows that the transfer occurred. But no one can challenge the legitimacy of the transfer. I can hardly praise this groundbreaking result in words."
——Marc Andreessen
Bitcoin is the basic unit of bitcoin (BTC), a digital currency. Like the US dollar, Bitcoin itself has no use value; it has value because people agree to use it to pay for goods and services in exchange for more of that currency, and believe that others will do the same.
To record the amount of bitcoin that each of us has, the blockchain uses a ledger , a digital file that records all bitcoin transactions.
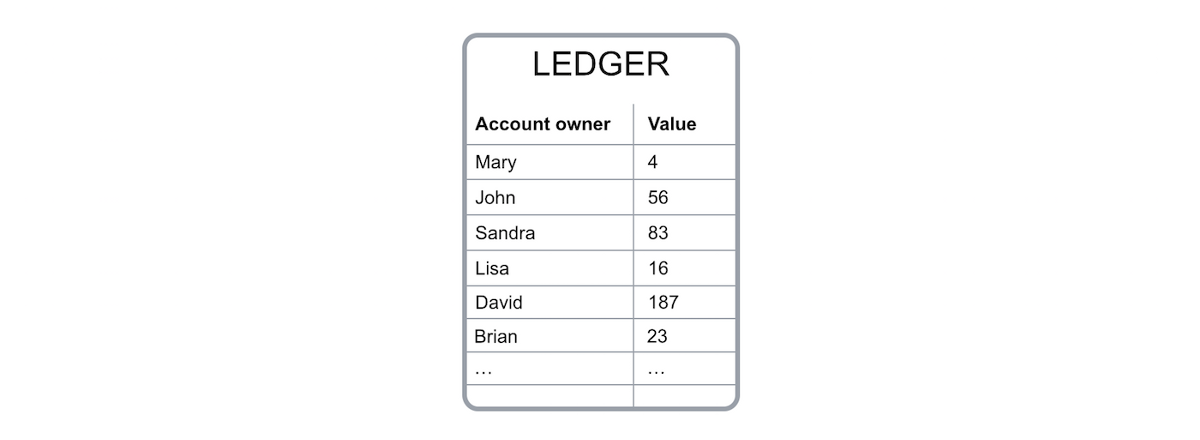
– Figure 1. Simplified Bitcoin ledger digital file – The ledger file is not stored in a central processor, such as a bank or a data center. It is stored all over the world via a private computer network, through which data is stored and calculated. Each computer represents a " node " of the blockchain network and has a copy of the ledger file .
If David wants to pay Bitcoin to Sandra, he broadcasts on the network, claiming that Bitcoin in David's own account will be reduced by 5 bitcoins, while Bitcoin in Sandra's account will increase by the same amount. Each node in the network receives this message and overwrites the transaction request with a copy of its account and updates the balance of both accounts.
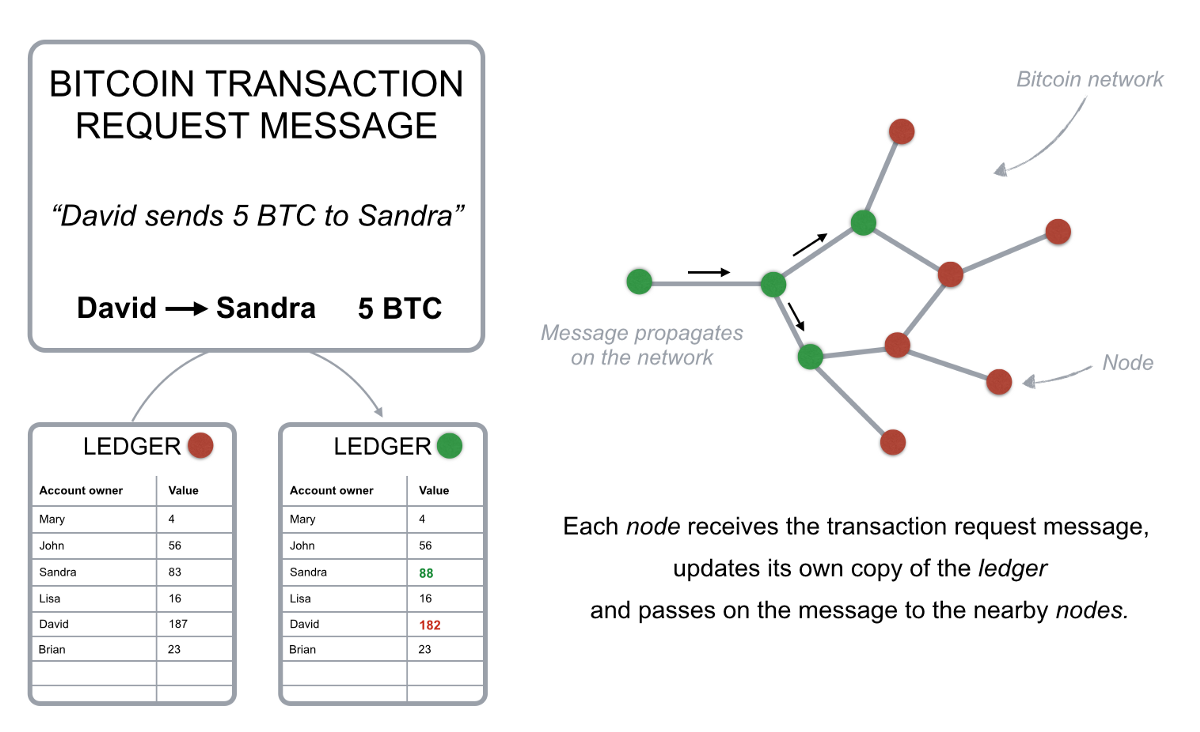
– Figure 2. Simplified Transaction Request Message – Since the ledger is maintained by a group of interconnected computers rather than a centralized entity such as a bank, the blockchain has the following characteristics:
- In our banking system, everyone only knows the transactions and account balances that happen to them; in the blockchain everyone knows the transactions of everyone else.
- Although you can usually trust your bank, the Bitcoin network is distributed. If there is a problem, you can't consult the service desk and no one can ask you to sue .
- The blockchain itself is designed in such a way that people do not need to trust each other, but through specific mathematical functions and code to ensure their security and reliability.
We can define blockchains in such a way that a group of interconnected computers can maintain a secure ledger and the system can be constantly updated . In order to complete a transaction on the blockchain, you need a wallet – a program that lets you store and trade Bitcoin. Since each person's bitcoin should only be spent by themselves, each wallet is protected by a special cryptographic technique that uses a pair of different but interrelated keys: private and public keys. .
Editor's Note: The use of two different but interrelated private keys comes from asymmetric cryptography, a cryptographic technique that uses two different keys in the encryption and decryption process. In this mode, the private key is the Private Key, which refers to the key that is kept by the actor, can derive the public key (but cannot reverse the private key) and (for actual needs) should not be disclosed to anyone. The public key, Public Key, is a key derived from the private key that can be disclosed to anyone.
Public key cryptography generally has two uses. One is encrypted communication, the sender encrypts using the recipient's public key, the receiver uses its own private key to decrypt, which guarantees confidentiality; the other is digital signature, the signer signs with his own private key The verifier uses the signer's public key to verify, so that the identity identity of the signature can be guaranteed (cannot be fraudulent or denied).
…. When David wants to pay for Bitcoin, he needs to broadcast a message that has been encrypted via the private key in his wallet. Since David is the only person who knows the private key corresponding to the unlocked wallet, he is the only one who can spend the bitcoin he holds. Any node in the network can decrypt the information by using the public key corresponding to the David wallet to check whether the transaction request is indeed from David himself.
When you use a private key in your wallet to encrypt a transaction request message, you also generate a digital signature, and the computer in the blockchain checks the signature to determine the source and authenticity of the transaction request. This digital signature is a string of text generated by your transaction request and private key; therefore it cannot be used for other transactions. If you change any of the characters in the transaction request message, the digital signature will become different, so any attacker (if any) cannot change the transaction request or transaction amount.

– Figure 3. Simplified digital signature – Since transaction request information needs to be encrypted with a private key, that is, before paying bitcoin, you always need to prove that you are the owner of your wallet private key. Since the information is always broadcast after being encrypted, you will never reveal your private key.
Editor's Note: Advanced Reading:
"Basic Cryptography on Wallets"
How does cryptography redefine private property rights? 》
Track your wallet balance
A copy of the ledger is saved for each node in the blockchain. So how does a node know your account balance? The blockchain system itself does not track balances; it only records each confirmed and verified transaction. In fact, the ledger does not track the balance, but only tracks every transaction broadcast within the Bitcoin network (Figure 4). To determine your wallet balance, you need to analyze and verify every transaction in the entire network that is associated with your wallet.
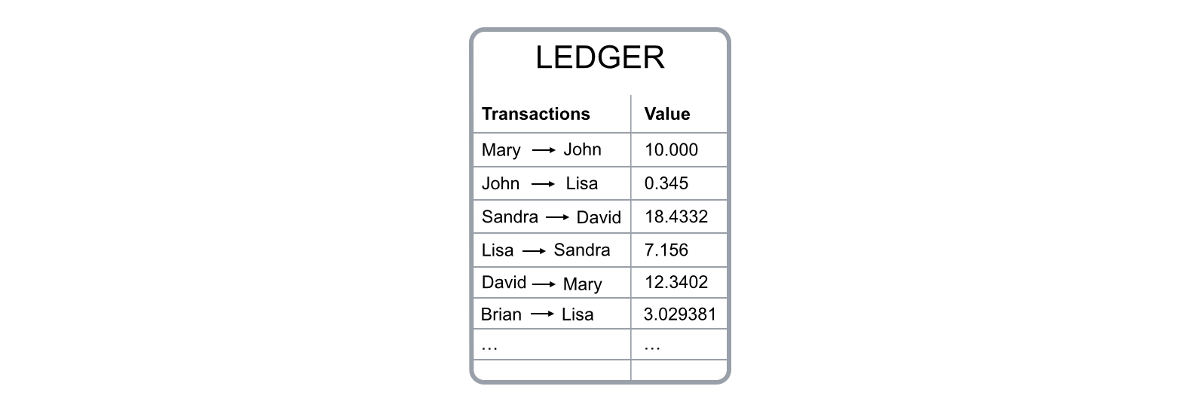
– Figure 4. Blockchain ledger – The verification of "balance" is based on previously traded. To pay John 10 bitcoins, Mary needs to generate a transaction request that includes a transaction link that Mary has previously received at least 10 bitcoins total. These links are called "inputs." Nodes in the network will confirm the transaction amount and ensure that these "inputs" are not spent. In fact, whenever you include certain “inputs” in a transaction, they become invalid in the transaction after the transaction. The above content is automatically done in Mary's wallet and is confirmed twice by the node of the Bitcoin network; she only paid 10 bitcoins to his wallet via John's public key.
Editor's Note: The above is just a description of the characteristics of blockchains such as Bitcoin that use UTXO to represent funds. Not all blockchains are like this, as is the case with Ethereum.

– Figure 5. Blockchain Transaction Request Structure – So how does the system confirm that the inputs to these transactions are valid? It checks all the transactions associated with the wallet you are using to pay by querying "Enter". To make this check faster, the network node keeps a record of unspent currency. Thanks to this security check, we can ensure that Bitcoin cannot be double-spended (ie, a sum of money is paid to different people at the same time).
Having bitcoin means that some of the transactions in the Bitcoin books point to your wallet address, and they have not yet been used as "inputs". All code used to execute transactions on the Bitcoin network is open source; that is, any holder of a networked laptop can make a transaction. However, once there is any problem with the code used to broadcast the transaction request information, the bitcoin associated with the transaction will disappear forever.
Editor's Note: In fact, the last sentence of the above paragraph is wrong. Because as long as the code does not destroy the account book, there are countless copies of the whole network; the money recorded on the ledger, as long as it is not spent, will naturally not be less. But will there be some software vulnerabilities that will make Bitcoin completely lose value? Take a look at the discussion in this article:
Bitcoin and Social Contract
Keep in mind that because the network is distributed, customer service calls don't exist, and no one can help you find lost transactions or forgotten passwords. Therefore, if you are interested in Bitcoin network transactions, it is best to use the official open source version of Bitcoin Wallet (such as Bitcoin Core ) and keep your wallet password and private key in a Vault.
Is the money in the Bitcoin wallet really safe? The source of the name of the "blockchain" is ~
Everyone can connect to the Bitcoin network anonymously (for example, they can connect to the Bitcoin network via TOR network or VPN network ), and the process of sending and receiving transactions only needs to disclose the public key (without revealing other information). If someone always uses the same public key, people can query all his transactions by simply using his public key. But people can create a lot of wallets, each with a different private key, so users can receive transfers with different wallets. Unless you transfer all of your Bitcoin to a wallet, no one else knows which wallet address is yours anyway.
The total number of Bitcoin addresses is 2 160 , or 1461501637330902918203684832716283019655932542976.
The large number of Bitcoin wallet addresses allows each user to have their own wallet without fear of being attacked by an attacker.
Despite this setup, there is still a security hole that has not been resolved – withdrawing Bitcoin that has already been spent. Because transactions are randomly passed between nodes, the order in which the two transactions are transmitted between nodes may vary. The attacker can send a trading order first, and then wait until the counterparty delivers the goods, and immediately send the opposite trading order to his own account. In this case, some nodes may have received the second transaction instruction before receiving the first transaction instruction, so the first payment transaction instruction is considered invalid. At this point, the transaction entry has been shown as "Complete." So, the question is coming – how do people check which trading order is first? Sorting individual transactions with timestamps is extremely insecure because timestamps are easily forged. Therefore, (in such an open network) there is no (simple technical) way to identify the order of transactions; this is the possibility of fraud.
If someone is maliciously withdrawing the transaction, the order of the transactions received by the nodes in the network will be inconsistent. Therefore, the blockchain system is deliberately designed to require nodes to agree (consensus) to prevent the above-mentioned fraud incident.
The Bitcoin network sorts the individual transactions into different blocks , each block containing a determined number of transactions and a link between the block and the previous block. As a result, the blocks are arranged one after the other in time. The block has thus become a chain of chronological order, hence the name: blockchain .

– Figure 6. Simplified blockchain sorting structure – transactions within the same block are considered to occur simultaneously, while transactions not yet included in the block are unconfirmed transactions. Each node can package the transaction into a data block and broadcast it to the network, suggesting that other nodes accept the data block as the latest block . However, according to this meaning, any node can propose a new block. Faced with numerous answers, how should the nodes in the system reach a consensus on the next block?
Each block must unravel the complex mathematical problem set by the (computed) irreversible cryptographic hash function to become a member (block) in the blockchain. The only way to solve this complex mathematical problem is to combine the contents of the previous block and constantly guess the random number until you find a result that matches the definition. It takes about a year for a regular computer to guess the number. This number sounds great, but don't forget that there are thousands of computers on the network that are guessing numbers, and an average of every 10 minutes. The node that solves the math problem will get the right to broadcast the block and ask everyone to treat the block as the latest block.
Editor's Note: This may be a bit more succinct. In design, (except for the first block) each block must specify the previous block it wants to undertake; combined with the content of the previous block, we can design a kind of cryptographic hash function Computational puzzle: It is required to change the input to make the result of the hash function conform to certain formal requirements (such as less than a certain value). Because the result of the hash function is random and computationally unidirectional (it is not possible to push x back through y), the only way to find a solution that meets the requirements is violent computing. After finding such a solution, the node that finds the solution can broadcast the corresponding block and ask other nodes to accept it.
The above "10 minutes" is the "block interval" (or "out of block time") of Bitcoin. Different blockchains often have different block times.
For the cryptographic hash function, you can see: "Emoji emoticons bring you a second to understand the hash function"
At this time, there may be students who are good at asking questions and raise their hands. Q: If you encounter two nodes and solve the problem at the same time, and send their blocks to the network, what can you do?
In this case, both blocks are broadcast to the network, and other nodes start to add blocks on the block they first received. However, the Bitcoin protocol requires each node to add blocks to its longest visible chain. Therefore, if it is not clear which one is the latest block (two blocks are simultaneously dug), once the area behind a block The block can be dug up and the problem can be solved according to the longest chain rule.

– Figure 7. Fuzzy solution logic at the top of the chain –
Since the possibility of excavating blocks at the same time is very low, it is almost impossible to have multiple blocks simultaneously excavated at each height. Therefore, the entire blockchain will quickly stabilize on a chain agreed by each node.
But the disagreement of "which block is the top of the blockchain" gives the scammers a chance. If the transaction happens to be in the non-longest chain (block B in Figure 7), once the (longest chain) has dug up the next block, the single and other transactions in that block will be re-stated as "not Determined transaction (status).
The mathematics competition protects transactions in the Bitcoin blockchain system. In short, each attacker is undoubtedly singled out the entire network.
Let's take a look at this example, how Mary used the ambiguity at the top of the chain for a "double flower attack." Mary turned some money to John, and John knew it and shipped it to Mary. Because the node always uses the longest chain rule to confirm the transaction, if Mary can dig a longer chain and withdraw the transaction at the same time, then John will have both money and goods.
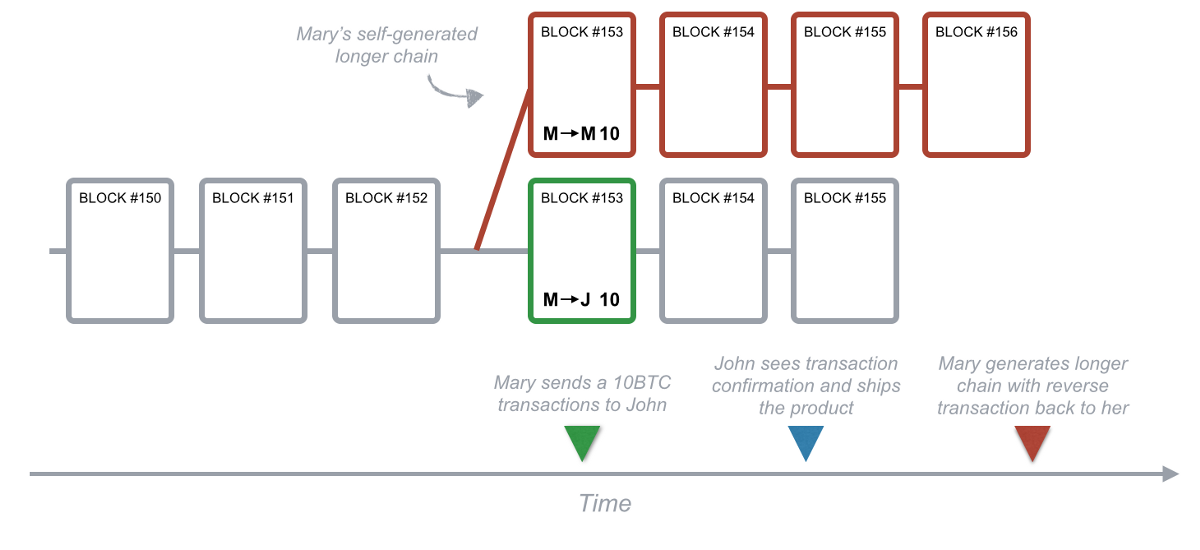
– Figure 8. Mary's "double flower attack" –
How does the system prevent this kind of fraud? Each block will reference the block ID of the previous block (see 6:6 for details). The ID of the previous block is also an element of the cryptographic puzzle, and the node ("miner") has to solve this problem in order to wind the subsequent block. Because solving a problem and putting new blocks on the chain requires a lot of random guesses, it is extremely difficult to pre-compute a series of blocks. In this mathematics competition, a host of Mary temporarily preemptively placed the next block, but it was still early from her wishful thinking – she is almost impossible to solve the second, third, and third consecutively Four… After all, her opponent is the whole network!
What if Mary uses a super fast computer and an entire network bar? The answer is still the same. Because there are thousands of opponents on the Internet, no matter how fast the computer is used by Mary, Mary needs to solve the math problems one after another in the double flower attack. This is really impossible. (Do not blame me for attacking people. Oh).
Mary needs to control 50% of the computing power of the entire network, only 50% of the possibility to unlock a block before other nodes. Even in this case, she only has a 25% chance of two blocks in a row. Simply put, the more blocks she needs to go out, the less likely she is to succeed. Knock on the small blackboard again – the transactions in the Bitcoin blockchain system are "protected" by this mathematical competition, and the attacker is undoubtedly a stone.
Therefore, transactions will be safer over time. For example, transactions that were confirmed and saved in the block an hour ago were more secure than those confirmed ten minutes ago. Since the block will increase by one every ten minutes on average, the trades saved in the block one hour ago have long been confirmed and become irreversible.
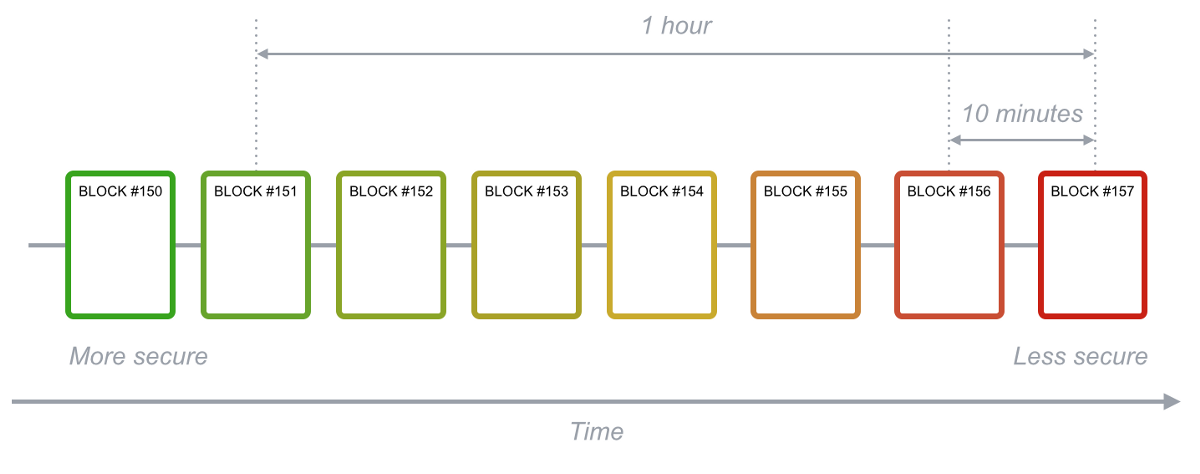
– Figure 9. Blockchain transaction security –
Bitcoin mining
To send Bitcoin, you need to quote a recipient's money for your wallet. This applies to every transaction in the network.
Editor's Note: This is called "UTXO". In the Bitcoin system, money is not in the form of numbers like our bank accounts, but in the form of a note. When you want to transfer money, you are equal to breaking (or replenishing) the ticket into a certain amount of the ticket, and then locking the funds in a way that only provides the recipient's private key to unlock. The same is true when the recipient spends the money in the future: unlock it with his private key.
Ethereum, on the other hand, uses an account model, much like our bank account. Details can be seen:
"Thinking about UTXO"
So, we will ask at this time – where did Bitcoin originally come from?
As a way to balance Bitcoin deflation characteristics (this feature is caused by software errors and wallet password loss), whenever people solve a block math problem, they will be rewarded accordingly. This kind of behavior of running Bitcoin software in order to get Bitcoin rewards, we call it "mining", which is actually quite like gold mining.
The main motivation for motivating individuals to operate nodes is rewards, which also provide the necessary computing power to ensure the normal operation of the transaction and the stability of the blockchain network. As we mentioned before, it takes nearly a year for a normal computer to solve a block. Therefore, nodes generally team up to reduce the number of nodes that need to be guessed. Groups can speed up the guessing of numbers and get rewards, and then share the benefits in the group. We call these groups a "mining pool."
Some mines are very large, concentrating more than 20% of the computing power of the entire network. Such a large computing power seems to challenge the security of the network, we can see from the above example of the double-flower attack. But even if some mines may have concentrated 50% of the computing power of the entire network, the higher the depth of the block in the chain, the higher the transaction security.
It is worth mentioning that some mines with powerful computing power have decided to limit the number of their members to secure the entire network.
As science and technology innovations and the number of nodes increase, the computing power of the entire network is likely to become stronger and stronger, and the Bitcoin protocol will recalibrate the difficulty of solving problems to ensure that an average block is added every ten minutes . This guarantees the stability and overall security of the network.
In addition, block rewards are halved every four years, so for people, mining (running the network) will not always be so attractive. In order to encourage the node to keep running, a small fee can be attached to each transaction. These rewards will enter the miners' pockets where the blocks are successfully dug. With this mechanism, transactions with high fees are usually packaged faster than those with less fees. So, do you want the transaction to be confirmed (more expensive) as soon as possible? Still want to save a little transaction fee (slower)? Ren Jun chooses. At present, the transaction cost in the Bitcoin network is much lower than the transaction cost of the bank. In addition, the transaction fee of Bitcoin is not related to the transaction amount.
The advantages of Bitcoin and the challenges it faces
Read the article here and you have an overall understanding of the operation of the blockchain. Let's quickly review why the blockchain is so interesting~
The significant advantages of blockchain technology are:
- You can firmly control the value of your assets, no other third party can control your assets or limit your access to your assets.
- The cost of global transfer value has become very low, making micropayments viable.
- Value can be delivered in a matter of minutes, and in just a few hours, we can determine the certainty of the transfer, rather than the traditional rhythm on a daily or weekly basis.
- Everyone can verify every single transaction that takes place on the blockchain at all times, which ensures transparency of the transaction.
- We can also use blockchain technology to build decentralized applications that manage information and deliver value quickly and securely.
However, there are still some challenges that need to be solved in the blockchain:
- You can send and receive transactions anonymously. This protects the privacy of the user, but it also allows illegal activities on the network.
- Although more and more trading platforms have emerged and electronic money has become more popular, it is not easy to use bitcoin for goods and services.
- Like other cryptocurrencies, bitcoin prices fluctuate significantly. In the market, there is not a lot of circulating bitcoin, and people's demand for bitcoin is unpredictable. Bitcoin prices are also largely affected by big events in the industry.
In general, blockchain has the potential to innovate many industries, from advertising to energy distribution. Decentralized attributes and the elimination of people's need for trust are its most magical powers.
New use cases are increasing all the time, such as: a completely decentralized platform that can run smart contracts – Ethereum. But what we need to remember is that this technology is still in its early stages. Day after day, with the continuous development of new tools that help improve the security of blockchains, blockchain technology can cover a wider range of functions, tools and services.
Original link: https://medium.com/s/story/how-does-the-blockchain-work-98c8cd01d2ae Author: Michele D'Aliessi translation & proofreading: Jin Zhou, ViolaH & Elisa
This article was authored by the original author to translate and republish EthFans.
(This article is from the EthFans of Ethereum fans, and it is strictly forbidden to reprint without the permission of the author.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- The company that declared bankruptcy was consistent with the FB goal. Can Libra complete its mission for it?
- Facebook Libra turned out, People’s Daily and CCTV screamed, and the policy should be better?
- Regarding the fire currency public chain and Nervos, these 6 questions may be your concern.
- Interview with Babbitt | Connect blockchain technology to 12 provincial courts, how does Zhongjing Tianping use technology to drive the future of law?
- The US Congress asks Facebook to stop Libra, but the social giants are moving frequently.
- Newer than the original segment: blockchain – from the triangle hypothesis to the extended model
- Read the history, current status and future opportunities of decentralized identity recognition