Talking about the governance of encryption protocol: making good use of the power of evolution to achieve network effect
Our retail investors in the Chinese currency circle are accustomed to self-deprecating, leeks, bricks, hardships, etc., but in fact they do not have to. Because almost all blockchain projects have to be more or less invested by retail investors. In this sense, the retail is the God of the currency.
Just being a god, breaking money is always inevitable. Compared with hardcore technology and big coffee stations, the topic of blockchain governance lacks heat, and individual investors are not very concerned about it. But in my opinion, this is much the place where God looks away.
Why pay attention to governance? What is governance?
The reason is actually very simple: in the blockchain industry, all technologies are open source. Breakthrough technology can bring a certain first-mover advantage in addition to the immature risk. As for the big coffee, no one has signed a deed of the project, and it is not voluntary. Maybe you don't think it's all right. Anyway, it's a short-term one. It's true or false to let him go. So if you are a short-term investor, the topic of blockchain governance can be said to have nothing to do with you. Because governance should replace the rule of man with the rule of law, ensure the long-term stability of the blockchain project. If you focus on the future of a coin 2 or 3 years later, governance is more important than technology.
This article discusses governance. The first question that needs to be answered is: What is governance?
- Wanchain released the PoS Galaxy Consensus Beta in the first quarter of the year, doubling the speed of the block, the official light wallet debut
- Bitcoin is 15 minutes deep and $1,700. Coinbase and other platforms once 瘫痪
- Analysis of the market: BTC high shocks, mainstream currency will usurish up?
Simply put, governance is how an organization makes decisions. This raises the zeroth question: Why do organizations make decisions? The reason is that anything (not an object) must have the purpose and ability to survive. Darwin said: The most viable species are not necessarily the strongest, or the smartest, but the fastest to adapt to environmental changes. The same is true for the exchange of species for organization. Therefore, organizations make decisions in order to constantly change themselves, adapt to the environment, and achieve the purpose of survival and development.
Encryption protocols are a set of transaction rules implemented using cryptographic techniques (primarily blockchain techniques) . This set of trading rules defines a market for digital products or services that have the advantage of transaction costs, can aggregate trading activities, and establish network effects.
In order to separate from the non-specific free market , I refer to the market defined by the encryption protocol as the "encryption economy", and the encryption protocol can be regarded as the law of the encryption economy. Encryption protocol economies can have a large number of participants with different roles, and the purpose of participating in the encryption protocol is to obtain economic incentives. Participants are usually anonymous and have no center. The advantage of going to the center is freedom and fairness. Who can't control others is not controlled by others. Mature organizations, such as countries, enterprises, and associations, have constitutions or regulations. The main content of the constitution or the charter is to explain how the organization makes decisions, who has the final say or how to vote. The decentralized organization is a new type of organization produced by human society in the last 10 years, and its historical experience is almost zero. So how can decentralized organizations make effective and fair decisions that are conducive to survival and development? This is the topic to be discussed in this article. To understand this topic, you need to understand the network effect first.
Read network effects
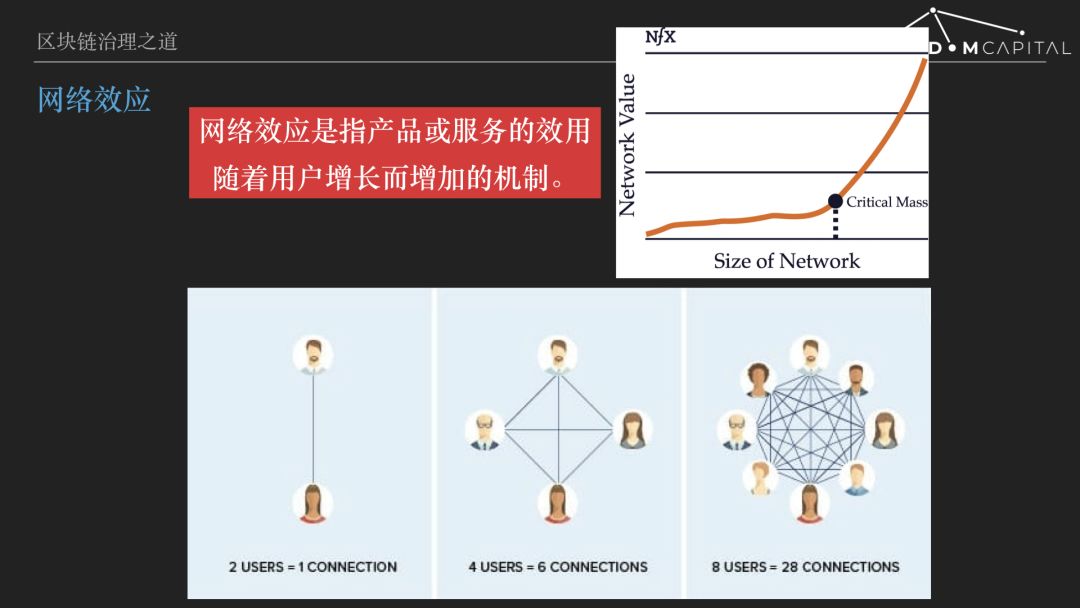
Network effect refers to the mechanism by which the utility of a product or service increases as the user grows. Both the Internet platform and the encryption protocol economy must have significant network effects. Or conversely, economic activities without network effects, or only weak network effects, cannot be implemented on a large Internet platform, and there is no need to use an encryption protocol.
We now understand the network effect very easily, because many products and services used every day have network effects, such as mobile phone, WeChat, Taobao, Alipay, Bitcoin have network effects, the more users, the more products and services become. A useful or better mechanism.
But think a little deeper, is the network effect of WeChat and Taobao the same? Obviously it is different. People who have contact with me start to use WeChat, so WeChat is more and more useful to me. Taobao is more buyers to gather more businesses, more competitive business, improve the cost performance and service experience, but also attract more buyers. So although they are all network effects, the mechanism is different.
So how many types of network effects? There are 3 kinds of researchers, or 5 kinds of researchers, and there are 13 kinds of people. We don't talk about it here. Different network effects, the function of network value varies with users.
The most famous quantitative formula for network effects is Metcalfe's law , that is, the network value is proportional to the square of the number of users. Use n for the number of users, the communication network value is proportional to n*(n-1), and when n is large enough, n*(n-1) is approximately equal to the square of n.
Metcalfe's law is a visual inference. In fact, if you think about it in depth, you know that it is not accurate. Because the communication network can grow larger and even cover everyone, the number of relationships that each person can maintain is a small number. For example, WeChat has 1 billion active users, but no matter how convenient, you will not contact all WeChat users, but only a small part of them, because each of us is limited by time and energy. Therefore, the network value cannot always grow according to the trend of n square, and when it reaches a certain level, the growth trend will slow down. Studies have shown that the network effect of some Internet services is n*log(n), and there are S curves. The S curve is the exponential growth of the network value as the user grows, which is slower and faster. After reaching saturation, the growth rate slows down.
Regardless of the quantitative relationship of network effects, there are similar important features. That is, the growth of the network effect is very slow at first, and when it reaches a certain scale, it starts to grow rapidly, and the growth rate is far more than linear growth. This slow-to-fast turning point is generally referred to as a critical size or tipping point. The key to the growth of network effects is to try to break through the critical dimensions.
What is the goal of governance?
Knowing the network effect, we can answer the primary question of encryption protocol governance: What is the goal of governance? Or another angle: how to judge successful governance and failed governance?
My answer to this question is: The goal of encryption protocol governance is to maximize the long-term network effect of the encryption economy, and the degree of achievement of this goal can be measured by the total market capitalization of the built-in pass.
The reason is very simple, because we have defined before, the purpose of the participants of the encryption protocol is to obtain economic incentives, and the design of the encryption protocol mechanism makes the incentives of all parties involved directly from the certificate, so the goal of governance is to improve the certificate for a long time. value. More specifically, the governance that can push up the total market value of the certificate for a long time is successful. The goal is very clear, but there is a place to pay attention to, that is, long-term, can not hurt the network effect of the economy for the short-term push up the price of the pass. Therefore, the goal of governance cannot be equated with "the pull is the biggest consensus." Because any pull, it must be accompanied by profit. Such price manipulation behavior will only cause some interference in the operation of the economy, and there is no role in promoting the network effect.
Some of my peers may disagree with the governance goals I proposed, and believe that encryption protocols are not just economic phenomena, but have some moral and even political goals. I can only say that it is different starting point, and to achieve moral or political goals, it is beyond the scope of mechanism design research, not something I can understand.
Who will participate in governance?
After establishing the governance objectives, an in-depth discussion of the governance process. Let us introduce the structure and main players of the encryption protocol economy. You can refer to the figure below to show the typical structure of the encryption economy.
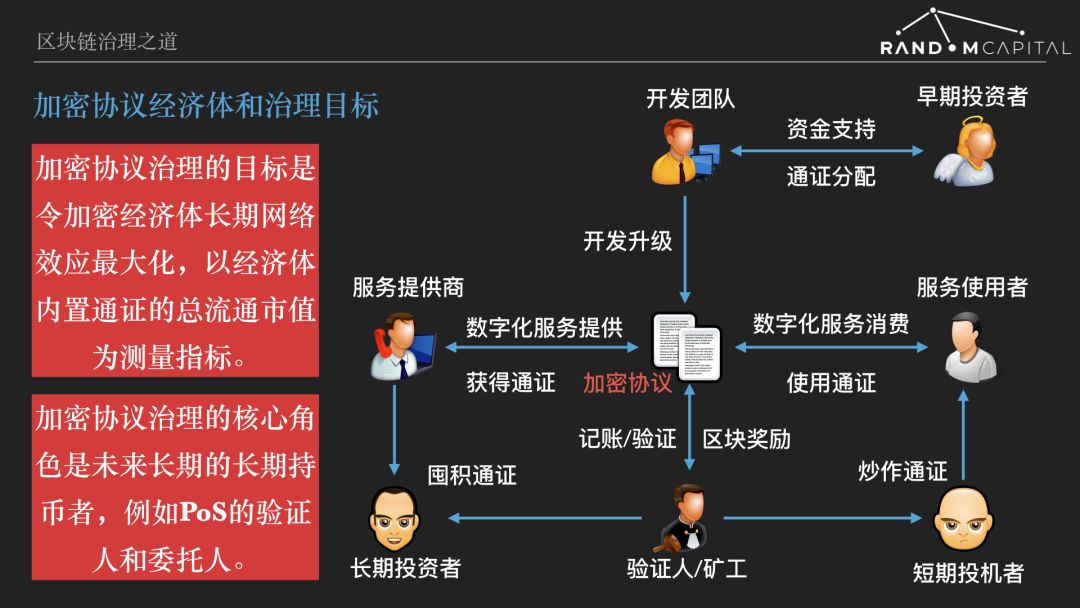
The first is that developers develop, improve encryption protocols, and issue certificates. In the early days, venture capital will provide financial support for developers to obtain a part of the certificate. The encryption protocol defines the market trading rules for digital products or services. The most common bilateral markets are the party providing the service and the party using the service, and the certifier (miner) to secure the encryption protocol. After the certificate has value and price, it circulates in the secondary market. The investor buys the certificate and expects to appreciate. The investor can be divided into long-term investors and short-term investors. Users need to purchase a pass from the market in order to use the service. Service providers and verifiers can sell passes in the market to pay for service costs and cash in on profits.
Note that the structure of the encryption protocol economy is not monotonous, and it is more complex and simpler than the typical structure described above. For example, a simple cryptocurrency such as Bitcoin, the service provider and the miner are in the same role. For the multilateral market structure, in addition to service providers and users, there may be intermediaries, guarantors and other roles involved in the transaction process.
After the goal is clear, the question of who is involved in governance is easier to answer, that is, long-term stakeholders should participate in governance. Because their interests are consistent with the long-term growth of the price of the certificate, this will only be given to the citizens with the right to governance, and will not be given to tourists. And long-term stakeholders should focus on the future, not the past. For example, a service provider, even if he has a long history of service in the economy, when he decides to leave for some reason, he is also likely to make behaviors that harm the overall interests, and such a situation is difficult to predict. Therefore, we hope that the future will be the same as the overall interests to determine the future of the encryption protocol.
But how do you distinguish between long-term stakeholders in the future? It is clear that developers, developers have invested time and energy in developing encryption protocols, have invested in entrepreneurial enthusiasm, and usually have a large part of the certificate, with a long-term lock commitment. Therefore, developers play an important role in governance, especially as a "benevolent dictator" in the early stages of the project, and generally can be widely recognized.
There is also an investor who can prove that he is a long-term stakeholder in the future through Staking. Service providers and service users, if they value the long-term development of the encryption economy, should hold a considerable amount of certificates and participate in Staking or commissioning, and should not be directly given the right to governance. Early investors will eventually become long-term investors and /or short-term investors, while short-term investors are not related to the long-term network effects of the encryption protocol (governance goals) , so they are not considered.
In summary, in the long run, the core role of encryption protocol governance is long-term holders . For the PoS chain, it is the verifier and the principal . In the early days of the development of encryption protocols, developers can temporarily act as core governance roles.
Encryption protocol governance process and status
Below we introduce the general process and development status of encryption protocol management.
Taking Bitcoin as an example, the first basis for governance is the extensive participation of discussions, in the bitcointalk, reddit network community, large and small meetings, numerous media, opinions, discussions and even debates. Researchers will conduct research on specific topics such as privacy, performance or more general signature schemes, P2P communication protocols, etc., and publish research results.
Suggestions for improvements to the Bitcoin protocol are presented in the form of BIP (Bitcoin Improvement Proposal) . Important BIPs raise the attention of the Bitcoin community and lead to broader discussions. The developer (not necessarily Core, not necessarily the sponsor of the proposal) can implement a BIP. Currently Bitcoin does not have a formal process for funding developers. In cryptocurrency communities such as Dash/Monero, there are standard processes to determine whether and how to fund developers.
After the implementation of the protocol improvements, it comes to the most critical step in decentralized governance: who and how to decide to deploy the BIP to become part of the Bitcoin protocol. Bitcoin governance is very ambiguous at this critical point, and can be described as a core developer's decision on whether to go online BIP based on the broad community consensus that has been reached. What is the broad consensus? Has a broad consensus been reached? There are no clear standards, which is particularly evident in the controversy surrounding the “big block vs. isolation testimony” that lasted for nearly three years.
The governance process of Ethereum is very similar to Bitcoin. Perhaps the only important difference is that V God's great influence in the Ethereum community makes it easier to reach consensus on the protocol improvements supported by V God. Since the final result of this type of governance process is the implementation of forks, it may be called fork management.
Fork management has obvious drawbacks. The biggest problem is that the governance process is ambiguous, so it is inefficient, difficult to improve, and easily controversial. For example, the lengthy soap opera around Ethereum around ProgPoW is the inevitable result of chaotic and disorderly governance. Without a clear governance process, similar soap operas will be repeated.
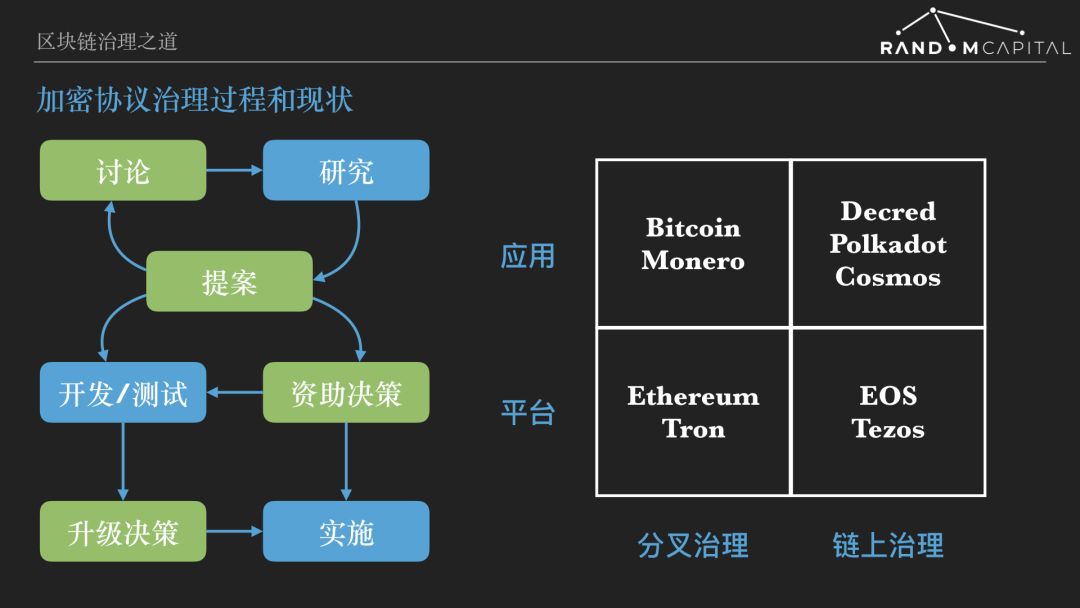
The overall governance process is shown on the left side of the figure. The four green processes, namely discussion , proposal , funding decision and upgrade decision, are cryptographic protocol governance.
In response to the flaws in fork management, Decred pioneered chain governance. That is, the holder of the Decred Pass will vote on the proposal through the chain transaction, and the proposal passed by the vote can be deployed online. EOS and Tezos have also done a lot of useful explorations on chain governance. The quadrant on the right side of the above picture for the decentralized governance status. Bitcoin, Monroe, Ethereum and Wavefield use fork management. EOS and Tezos two smart contract platforms use chain governance. Decred is a cryptocurrency application that implements partial chain governance. Both Polkadot and Cosmos have achieved chain governance to varying degrees, and through the Substrate and Cosmos SDK development tools, the chain management capabilities are given to the parallel chain and the partition chain, which is the decentralized application in the form of independent blockchain.
Bitcoin governance
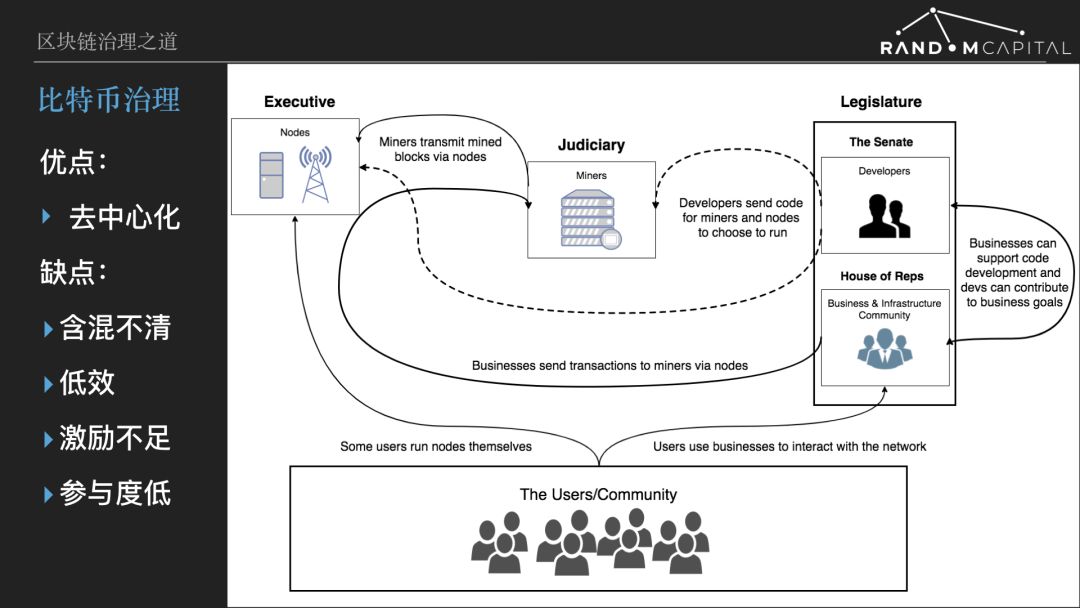
For the decision on how to determine the upgrade of the Bitcoin protocol, Nakamoto's initial idea is to count the power, the so-called "one CPU one vote." The reason is that computing power is unforgeable, and miners are the main stakeholder group of Bitcoin. However, it is very likely that Nakamoto did not foresee the emergence of a dedicated ASIC mining machine, completely extruding the personal computer from the mining competition, and formed the status quo of several large pools of monopoly computing power.
There are four main stakeholder groups in Bitcoin: miners, developers, users, and businesses (exchanges, wallet vendors, blockchain browsers, communities, media, etc.) . They have consistent interests and conflicting interests. For example, almost all participants benefit from the long-term price increase of Bitcoin. But users want the lower the transaction fee, the better, and the miners hope that the higher the transaction fee, the better. Due to conflicts of interest, the parties will have different opinions on the evolution of the Bitcoin protocol, and all four parties have the ability and means to influence the research of the agreement. Based on the history of the bitcoin fork game, it seems that the biggest impact on the evolution of the protocol is the bitcoin core (developer) , not the miner.
First of all, it must be acknowledged that Bitcoin is the first decentralized encryption protocol, and for the first time it has realized the decentralization of the encryption protocol, which is a revolutionary innovation. But it should also be noted that as the ancestor of the encryption protocol, Bitcoin is limited by the era in which it is located. After 10 years, there are many shortcomings. Among them, in terms of governance, as mentioned above, the biggest drawback is inefficiency and ambiguity. The problem is that Bitcoin has evolved very slowly.
Some people say that the slow upgrade of Bitcoin is intentional, in order to avoid too much risk in such an important value storage agreement. I don't agree with this because efficiency and prudence do not conflict. For development suggestions that help Bitcoin's long-term network effect growth, such as Schnorr signature, should the development team be funded? What tests and code reviews are being conducted? If there is an efficient decision-making mechanism, it is a job that can be promoted quickly and with high quality. The ambiguous and inefficient process has been extended to years, and it is not possible to obtain higher quality software and a more confident upgrade.
Bitcoin is not motivated to govern participants and even has no funding for core developers. Now that most of the Bitcoin core developers are hired by the same commercial company, how can they expect them to be biased towards the future of Bitcoin? In addition, most of the Bitcoin holders did not participate in the governance process, becoming a veritable "silent majority." Bitcoin sits on the biggest network effect, but its own development is stagnant. Historical experience has proven that even the great empire across the three continents cannot be inexhaustible. If Bitcoin continues to stand still, it’s only a matter of time before it is taken over.
Decred governance
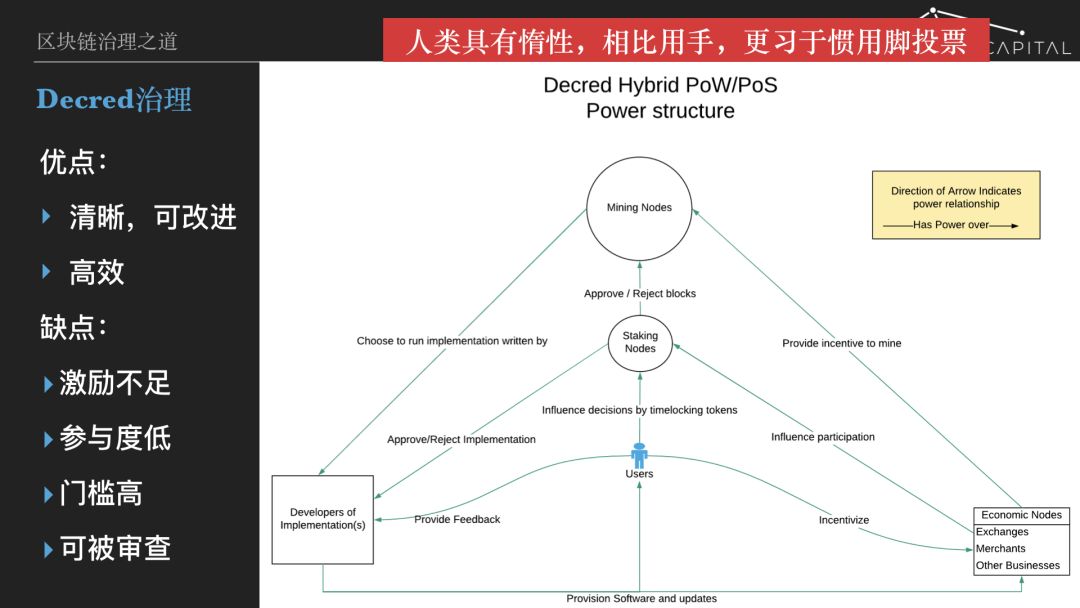
It was out of disappointment with the governance process that a group of Bitcoin developers left to create Decred. Decred is also a point-to-point e-cash, and its main feature is to have a fairer and more efficient governance system. Yoco -Piatt , founder of Decred, said: "The governance of Bitcoin is chained and very informal. Miners have all the rights. We believe that as a stakeholder, cryptocurrency users should have a say. If you hold encryption Money, and miners can pass a proposal against you, this system is very unhealthy. We hope to find a balance of rights between the holders and the mine."
Decred governance is divided into two parts: chain governance and chain governance:
- The process of chain governance is to lock the positions of DCR holders to obtain the tickets. Tickets have two functions. The first effect is that tickets will be randomly selected to vote on the blocks produced by PoW. If there are more votes, then all the transactions in the block are rolled back and PoW miners are not rewarded by the block. If there are more votes in favor, then the block is recognized, PoW miners receive 60% of the block rewards, voters (equivalent to PoS certifiers) receive 30% reward, and the remaining 10% are awarded to the public vault. The second role of tickets is to vote on the upgrade of the consensus agreement, which also occurs on the chain.
- Decred's chain governance is carried out through a Web site called Politeia, which is used to determine the use of funds in public vaults, such as funding development or community activities, etc.; second, to make decisions on the big policies of the economy, such as modifying Decred. Constitution, etc.
Compared with Bitcoin governance, Decred has made important explorations in the direction of encryption protocol management, and has achieved remarkable results. The biggest achievement is to turn the ambiguous governance of Bitcoin into a clear governance process, which can be said to be the Hama Rabbi Code, which writes the world of encryption protocols. And Decred has developed governance tools (primarily the Politeia website) that automate governance processes and lower the barriers to participation, making governance more efficient.
But strictly speaking, voting on blocks is verification and is not part of the governance process. Decred's true chain governance is only the part of tickets that vote on consensus escalation. Verification voting and upgrade voting are inseparable because getting tickets has a lock-in cost, and if there is no verification bonus, voting cannot be done. Decred certifiers can only get 30% of block rewards. In the later pure PoS system, the certifier was also responsible for the block and received a higher percentage of rewards (usually 100%) . Moreover, Decre's voting process was not rewarded. Although the holders obtained the tickets, the motivation for voting was still insufficient, resulting in low participation in Decred governance. There is a more ambiguous place here, which is the calculation of participation. For example, the participation of the proposal can usually reach 30%, which means that 30% of the tickets participate in the voting. However, if you use the ticketing address to count, the actual participation is often less than 1%.
In addition, in order to obtain tickets, a considerable amount of DCR needs to be mortgaged. This requirement is dynamically adjusted to keep the total number of votes in the 40,000. The current fare is 120 DCRs, which is about $3,000, and the threshold is relatively high.
Doing direct democratic encryption protocol management will encounter the dilemma of setting the threshold for participation. There are too few participants in the threshold, but if the threshold is too low, the participants are more motivated and not enough, or the individual participants get too little incentive to participate. Low participation has always been a chronic illness in the management of encryption protocols. In fact, not only the encryption protocol governance, in the real world, even the top priority of governance such as the election of state leaders, in many countries, the turnout rate is less than 50%. Humans are inert, and we are more accustomed to voting with our feet than with our hands. Compared to assets such as land, housing, and private equity, cryptocurrencies usually have better liquidity. If I am not optimistic about the development of an economy, the easiest response is to sell coins out of the market. It is much more difficult and more costly to actively participate in governance and reverse the rules that they think are unreasonable. Therefore, it is necessary to provide sufficient incentives to the encryption protocol governance participants. It is hoped that the governance that relies on people's loyalty and dedication will be unsustainable.
In addition, most of Decre's governance process takes place on the Politeia website, which allows the governance process to be reviewed by the site's operators. Anti-examination means that anyone can participate on an equal basis and will not be discriminated against or denied service because of his personal identity or data. For example, if Bitcoin Core develops and maintains a governance website, it will vote on the Bitcoin protocol upgrade. So, can the core block the vote of the big block for the isolation testimony? If it can be stopped, it means that this governance process has not been reviewed. Although Politeia regularly deposits the website data in a chain, trying to achieve so-called review transparency, that is, once it is reviewed, it can be easily found. But the deposit process itself is difficult to verify, and the Politeia website is virtually impossible to review.
EOS governance
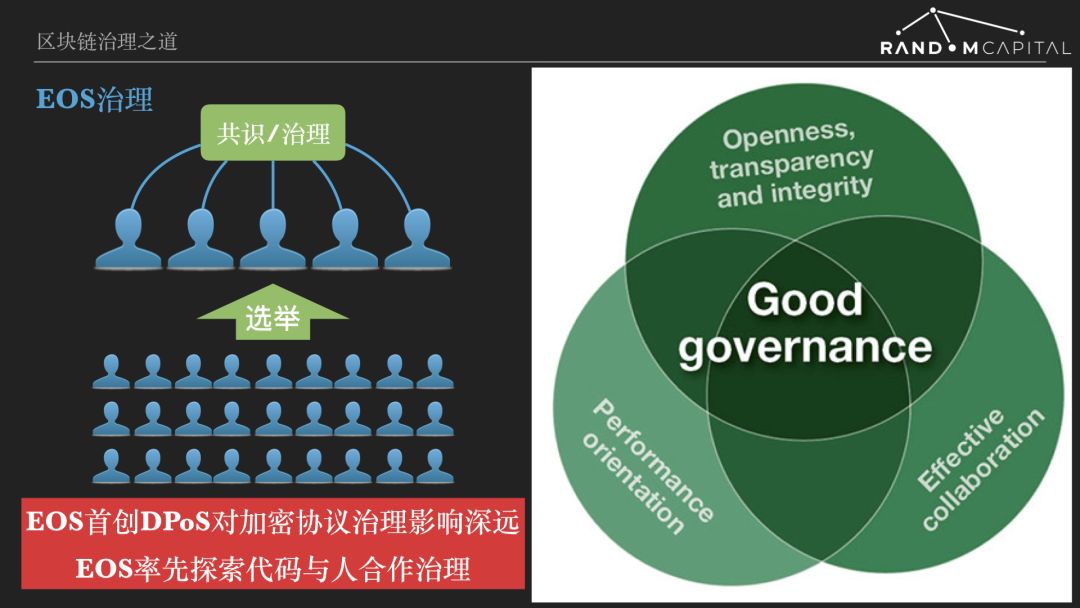
EOS is a public chain that pays special attention to governance. The EOS community believes that good governance includes three aspects: effective cooperation, efficiency, and openness, transparency, and integrity. I think EOS's greatest contribution to the management of cryptographic protocols is to combine PoS with representative systems and creatively propose DPoS .
Representative democracy stems from the ancient political wisdom of mankind because the direct democracy of the whole people is too costly and inefficient. The Brexit decision was made through a referendum, but obviously not all issues are subject to a referendum. The representative system is that the people choose the agent, and then the agent will negotiate the law or major resolution. There are two reasons for the representative system to improve decision-making efficiency. The first is that the number of people participating in the consensus is greatly reduced. The second is that agents are usually professional politicians who have more resources and knowledge to negotiate national events.
Under the DPoS mechanism, the holders do not directly participate in the governance process, but vote for the verifier (EOS is called the blocker , also known as the super node) , and the blockers participate in the consensus and exercise the right to governance. The EOS has a blocker of 21 and the other nodes are alternate. The inflation rate of EOS is 5% per year, of which only 20%, that is, 1% of the annual increase, is given to blockers and alternates. Equivalently, the EOS Ecology collects 1% of the tax each year in the form of coinage, paying the block and the spare block, in exchange for the block (maintenance system security) and governance services they provide.
In the current public chain, the security and governance costs of EOS are very low. The reason for this is that the number of agents in EOS is small, and although the total amount of incentives is low, the incentives given to each agent are still sufficient. But overall, I think EOS's incentives for consensus/governance are too low. The holders did not share the incentives, so they were indifferent to the voting. A large number of votes were cast by the exchange, plus one vote for 30 votes. The EOS block has been monopolized by the alliance of big players. Although it seems that EOS's DPoS has problems such as low decentralization, alliance and bribery, it is a major breakthrough in the field of encryption protocol governance. Later, BPoS, NPoS, etc. were all improved on the basis of DPoS.
EOS governance practices are broadly explored and far beyond other encryption economies. The reason is that EOS hopes to achieve a very ambitious goal: not only to protect the user's assets with decentralization, but also to allow users to enjoy asset protection similar to the real society, that is, to avoid property damage due to loss of private keys, hacking and other reasons. If this goal is achieved, the barriers for Internet users to use encryption protocols will be greatly reduced. Obviously the code can't tell if the transfer is shopping or being cheated. To obtain protection similar to that of a traditional society, it is only possible to introduce a rule of man. To this end, EOS has established the ECAF, the EOS Core Arbitration Forum. Users or smart contract developers who have been attacked or scamed can appeal to ECAF. The ECAF can make a ruling such as freezing a hacker account and hand it over to the blocker.
Such a seemingly good design has a lot of problems in its actual operation. First of all, the members of the ECAF are volunteers. Their ability and time commitment are not guaranteed. Therefore, there is a problem of backlog of complaints and lack of credibility in arbitration. Moreover, the collaboration between the ECAF and the exporter was not smooth. In the early days, there were cases in which the blocker first frozen the account and then submitted the appeal to the ECAF. There have also been ECAF issued a verdict to freeze the hacker account, but the individual blockers did not execute in time. The hacker took advantage of the unsuccessful block-out period and successfully took the money.
Overall, EOS's exploration of human governance has encountered two major problems:
- The first is the issue of the creation, renewal and self-motivation of arbitration organizations. The ECAF and the exporter are checks and balances, so they cannot be elected or appointed by the blocker. The holders do not have the incentive to elect the ECAF. The lack of transparency in the selection process of members has made the authority of the ECAF questionable from the outset. As mentioned earlier, members of the ECAF are volunteers, and their ability and time to arbitrate are not guaranteed.
- The second big problem is the connection between computers and people. For example, for an appeal, the arbitrator can obtain relevant evidence data comprehensively. The arbitrator's judgment, how to safely convey the block person, and then map to the calculation operation of the block person. The hardest part is to judge breach of contract or fraud based on what. A contract that a machine can execute (smart contract) , such as The DAO 's 1CO contract, which the project party believes is a bug in the code and is exploited by hackers. But hackers can think that since the contract is written like this, code is law, the code is law, then there is no stealing. EOS introduced the Ricardo contract to try to solve this problem. The Ricardo contract is a contractual text clause that humans can read and understand in a contract that the machine can execute. Once the participant has disputed the execution of the contract, the arbitrator can determine who is right or wrong by interpreting the Ricardo contract.
The ECAF was cancelled by the EOS User Agreement (EUA) adopted in April 2019 due to the failure of ECAF to perform its duties effectively. EOS's exploration of human governance has so far been said to be unsuccessful. But I have to applaud EOS. If the blockchain project can't explore even an unknown area, there is no need to exist.
But I also want to vomit EOS. The distribution mechanism designed by the project Block.One company is too favorable for itself, and it has seriously squeezed the interests of other participants. On the one hand, Block.One raised $4 billion through ICO, and the promised $1 billion eco-investment fund did not move. The company repurchased shares at high prices, giving equity investors a return of dozens of times. 80% of the annual EOS is added to the eosio.saving account. After accumulating 34 million EOS sums, it was destroyed because it was not used properly. On the other hand, the blockers bear the responsibility of maintaining network security and governance. They are barely maintained by 1% of the increase, and some backups are unable to make ends meet. How can it increase investment in governance? The failure of ECAF and insufficient resources are one of the reasons.
The mechanism of Block.One design is to be afraid of others to take more, but you must not make less. The positioning on the surface is very modest, only to provide technology for the ecosystem, but the resources have been taken away by you, can you expect others to do the ecology?
Tezos governance
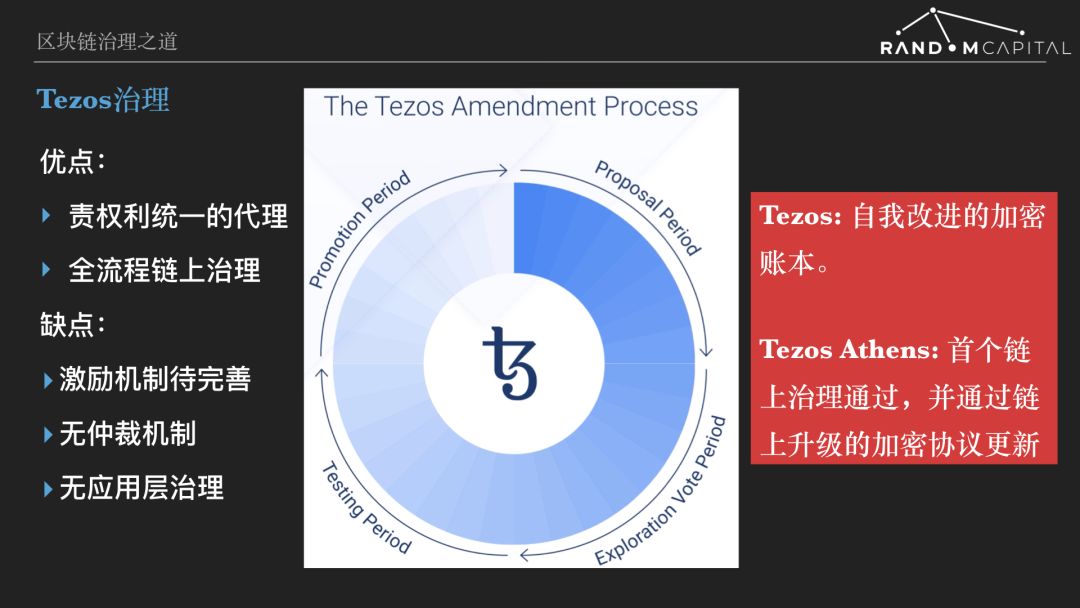
Similar to Decred, Tezos can be said to be a public chain of governance, positioned as a self-improving encrypted ledger. The Tezos Agreement provides stakeholders with a disciplined process that can effectively manage agreements and implement future innovations. The so-called normative process, as shown in the above figure, is a reciprocating cycle consisting of four stages of proposal, inquiry, testing and promotion, all of which occur on the chain.
I think that Tezos has made two major contributions to the management of cryptographic protocols so far. One is to set up the role of the agent, Baker. Baker is the certifier of the Tezos PoS Consensus and is responsible for maintaining cybersecurity and getting a block bonus. Ordinary holders also participate in Bken by entrusting the coins and share the block rewards with Baker. Baker is also a central role in governance, and they have the right to make proposals and vote. The holder and Baker are principal-agent relationships. The currency holder chooses Baker to have two layers of consideration. The first layer is the revenue, that is, whether Baker can get the full block reward, which mainly depends on the IT capability of the running node and the honest participation in the consensus process (avoiding slash) . The other is the proportion of Baker's share of the principal. These two aspects determine how much Staking revenue the client can get. The second layer is governance, which is which Baker is more representative of its own interests. Baker also attaches great importance to the client because the more commissions he accepts, the more rewards he receives for the block, and the greater the voting power of governance. Tezos' second major contribution to governance is to achieve chain-wide governance of the entire process. The four stages of the process of proposal, inquiry, testing and promotion are all carried out on the blockchain, ensuring that the process is open, efficient, and Licensing and anti-censorship.
In other words, the holder of the money pays more attention to the benefits than to the governance. Therefore, I believe that under the premise of the full efforts of the agents, the mechanism design should make the proceeds of the principals converge. That is, the agent runs the node stably and honestly, and the system sets a unified principal/agent reward distribution ratio, and directly awards the reward (without the agent) to the client. Only in this way, the principal will choose the agent from the governance level, and the agent will have the motivation to continuously invest resources in the governance, and use this as a means to win the client.
Tezos does not currently have a uniform proxy/agent reward distribution ratio. But this is not a very serious problem, because as long as the consensus can be reached in the community, Tezos can adjust and optimize the encryption protocol or the governance process itself at any time. This is the advantage of efficient governance, that is, Kevin Kelly 's higher "evolution" in the book "What is Technology?" (Related reading: " Understanding Kevin Kelly, understanding what technology wants, re-understanding the district." Blockchain ") .
The other shortcomings of Tezos governance are actually rather stubborn. It is not so much a shortcoming, but rather a design choice. Is the arbitration mechanism necessary? There is no conclusive question. But I think Tezos should give Baker the right and obligation to arbitrate, so that the clear and clear automatic process, combined with human comprehensive judgment and resilience, pushes the level of governance of the encryption protocol to a new level. In addition, the smart contract platform public chain does not have governance support for the application layer. The underlying reason is that smart contracts are verifiable application development techniques, and there are conflicts between verifiable and scalable. For an in-depth discussion of this topic, see Creating a Cross-Chain Release of DApp Innovation Potential .
Polkadot governance
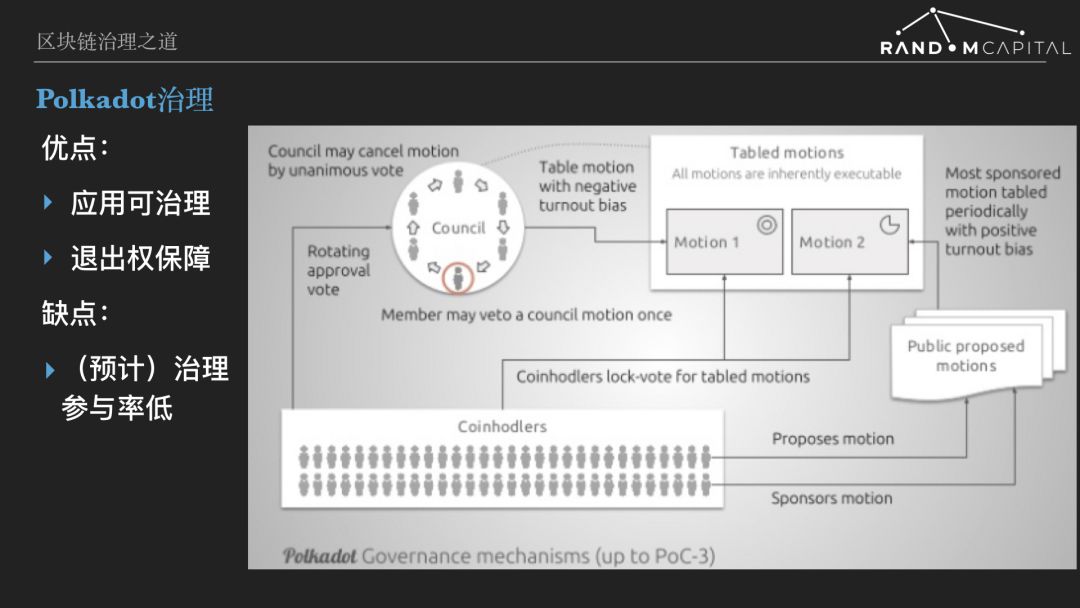
Polkadot's governance is also a comprehensive chain of governance, the proposal being voted not only for the description of the protocol modification, but also the new protocol itself, that is, the executable program compiled into wasm blob. After the vote is passed on the chain, the new version of the program is distributed to the authenticator node through the blockchain and is automatically enabled. There will be no forks during the upgrade process.
Polkadot's governance technology has been applied to the application (parallel chain) through Substrate, enabling decentralized applications to evolve their own governance processes. And the governance process is implemented through open source code, which can be easily borrowed from each other. Based on breathtaking technology, Polkadot is riding on the chain and is doing a lot of innovation and exploration.
The governance process of Polkadot's main network (Polkadot Relay) revolves around proposals and voting. Proposals can be made by ordinary money holders or by the board of directors. The board of directors is elected by the holder of the currency, and the holder of the currency can vote for any number of director candidates. The person with the most votes in each election cycle enters the board of directors and replaces the director who has served the longest time. The number of votes for the second most votes is retained, and the votes of other candidates are cleared. Each director has the veto power of other directors' proposals, but cannot be used continuously. The proposal adopted by the Council entered a referendum and will be rejected only if it is opposed by the majority. The general holder's proposal enters the proposal queue and waits for the support of other holders. Every once in a while, the most supportive proposal entered the referendum. Ordinary holders’ proposals must be supported by majority support. In a full-blown vote, the holder can choose the lock factor, ranging from 1-6, and the actual number of votes cast is the number of DOTs he holds multiplied by the lock factor. If the voting result is consistent with the voter's choice (pass/reject) , then the voter's DOT will be locked, lock time = constant * lock factor. If the voting result is contrary to the voter's choice, there is no need to lock the position. This way of counting votes is to give the long-term holders (future rather than the past) greater weight.
Polkadot governance has built-in protection of minority rights. There is a buffer period between the confirmation of the voting result and the submission of the proposal. During the buffer period, the losing party (minority group) can choose to sell the coin to leave the market, while the winning party (majority group) is locked.
This reminds me of the fact that in ancient Greece, people who did not recognize the governance of city-states could organize to leave the city-state and establish colonies elsewhere. I call this right the right to withdraw. However, in modern times, there is no land of no ownership suitable for human habitation, and the right to withdraw from the external colonial form no longer exists. The protection of minority rights has become a difficult problem for democracy. But in the digital world, space is infinite and can accommodate all dissident groups. Polkadot is a great innovation to protect minority rights through a buffer period.
However, it should be noted that the buffer period mechanism can only provide protection to minority groups of investor types. However, service providers and service users in the economy cannot retreat in a simple way such as selling a pass. For them, the fork is a better exit right. Regarding the fork, we will discuss it in depth later.
As can be seen from the process, Polkadot attempts to achieve a model of representative and direct democratic mixing. Both the board and the holders have the right to make proposals, and the board proposal is easier to pass, but the final decision (voting) right belongs to the holder. Due to lack of incentives, I expect Polkadot governance participation (voting rate) to be very low. Board members have great rights, but there is no corresponding incentive mechanism and it is feasible to verify. Thanks to the Polkadot Relay shared security pool design, there are thousands or even tens of thousands of certifiers after a period of time. If the certifier is given the responsibility of governance, this number is really too much. From the experience of social governance, the number of people in the parliament is ideal. The encryption protocol is a specific purpose market, and the complexity and difference of participants are far lower than the real society. I think the number of governance agents for encryption protocols is tens to hundreds. Therefore, it is difficult for Polkadot to use the certifier as an agent for governance in the future.
Bifurcation is a double-edged sword
In this section, we explore how bifurcation affects the network effect of encryption protocols and what it means for governance.
First of all, the community's controversy over the upgrade of encryption protocols has been long overdue, which is a very bad situation. Since there are irreconcilable contradictions, there is no need to eat in a pot. Through the fork, the two parties who are arguing can move forward lightly and pursue their own goals. Bifurcation is a fast evolutionary approach unique to encryption protocols. Biological evolution is a variation in DNA replication errors, and sexual reproduction adds more variation through genetic recombination. The encryption protocol also mutates during the fork process. Unlike random trial and error with DNA mutations, the variation of the encryption protocol is a well-thought-out result, and each time a fork forms a new "encryption protocol species." The fork can inherit the data and participants of the original chain. The network effect does not have to be rebuilt from scratch, and the cost of trial and error is much lower than that of the push.
The second point is that divisibility is the patron saint of decentralization. Decentralization is not about the project team limiting its contribution and influence. The project team should ensure that the encryption protocol is divisible and understand the constraints of divisibility on its own actions, so that it can participate fairly in the construction of the economy, share risks with other participants, and share success. Other parties to the encryption protocol, including service providers, service consumers, and certifiers, have real money investments in the growth of the encryption protocol network. They should pay close attention to the cleavability of the encryption protocol, which may be reduced or Defeat the divisible upgrade with caution. If the development team, whales or cartels try to control the encryption protocol and unfairly squeeze the rights of other parties, other parties can use the fork to form a new encryption protocol economy, eliminate the monopolist and protect their own interests. However, the cleavability of the encryption protocol is not easy to detect and difficult to verify. Encryption protocol researchers should delve into the divisibility and introduce simple and practical bifurcated verification methods and even measurement tools to facilitate the observability of the observing economy participants to observe and compare protocols.
The first two points are the value and meaning of divisibility, but the fork is a double-edged sword.
First, the network is divided into two. Service providers, service users, and verifiers (miners) are divided into two groups. Since network effects are usually superlinear, the sum of the values of the two new networks will be lower than the old ones. And the forks are often accompanied by a struggle for orthodoxy (such as which is the real bitcoin) or even mutual attacks (such as power wars) , causing interference to the operation of the economy. There are even irresponsible forks, refusing to join the replay protection, placing the user's assets in a dangerous situation. Two cryptocurrencies are generated after the PoW chain forks, which is obtained by the user 1:1. Since the separation of the coins provided by the wallet and the exchange will be lagging behind, and many users are not eager to trade, the actual transaction depth of the forked coins is very shallow, and it is easy to be used by the speculators to make the price control of the pull-dish. There are even some forked coins that do not have independent value propositions and evolutionary directions, purely for market speculation.
Governance principles and best practices
By summarizing the experience and lessons learned from encryption protocol governance over the past decade, I hope to summarize some of the principles and best practices. But at present, it seems that there is still a long way to go to achieve this goal. Here we can only talk about some less systematic ideas.
We Chinese people are quite dissatisfied with the mutual attacks in the Western parliamentary debates and elections. I don’t know that a group of harmony is the great harm of governance. The power of encryption protocols is to change economic activities from corporate management coordination to free market competition, and governance is no exception.
Good governance should be a freely competitive market. A competitor is a governance agent who is a trinity of competence, prestige, and income. Governance agents strive to participate in governance and provide advice and escort for the long-term network effect growth of the encryption economy. The holder of the currency chooses the agent who best represents his own interests and is the most responsible agent to act as his agent and share the benefits of governance with him. Agents with the ability and prestige receive higher returns, and thus have the will and the potential to invest more resources in governance activities. There should be a fundamental conflict of interest between the agents of governance, which is lost by others, that is, my income . This makes it difficult for governance agents to make ends meet, because not being responsible will be exposed by other agents, resulting in impaired reputation and earnings.
Although we can try to use economic incentives to guide the behavior of the governance agent. But if you completely abandon the values and hand over the governance of the economy to a group of people who are profitable and ready to take advantage of the situation, I am afraid it is more dangerous than the blind man riding a horse. The agent and the holder are typical agent-trust relationships, and the agent has fiduciary responsibility.
Since the birth of the encryption protocol economy, it is necessary to have values, and the values should include elements such as integrity and fairness. The founding team of encryption protocols plays a decisive role in the formation of economic values.
Most of the encryption protocol governance is around voting, but is voting omnipotent? Obviously not. For example, most economies have serious polarizations between rich and poor. If someone proposes a "all rich and poor" proposal and resorts to a one-person, one-vote referendum, it is likely to pass. But everyone knows that private property is not protected and the greatest internal driving force for economic development has disappeared. Both the poor and the poor benefit some people in the short term, but they will seriously harm the long-term overall interests. Such wrong decisions are not uncommon, as in South Africa, for example.
How does the decentralized crypto economy prevent short-sighted cases from being passed? There are two possible solutions, but they are not perfect. The first option is to have “super rights” on top of the governance process, in the hands of individuals who are widely trusted by the community. Super-rights should not be used for daily governance, but the veto can be exercised under special circumstances. The drawbacks of this program are obvious, and the super rights can hardly be controlled. It is believed that Vitalik Buterin has super rights in the Ethereum community, which is to a certain extent the luck of the Ethereum community, but not all of the encryption protocol communities have a Vitalik Buterin. A more practical solution is to grade and classify the agreement. The more the modification of the underlying protocol requires a higher turnout rate and a higher pass rate. The proposal that the certifier and the client have a conflict of interest shall be referred to all holders of the currency. But even so, the stratification and classification of proposals, voting rules, etc. can be modified through governance, so there is no guarantee that the proposals passed will meet the long-term overall interests of the crypto economy.
If the encryption protocol violates the principle of decentralization, the implementation of access to members, or the implementation of some kind of censorship or even discrimination, should it be condemned? We should pay attention to the difference between the encryption economy and the real society. For example, in some countries and regions of the world, women are discriminated against and some basic rights (such as education, freedom of marriage, etc.) are denied. So for women in these areas, it is almost impossible for them to leave without a price to live in a country that does not discriminate against women. But for crypto economies, joining and leaving are voluntary and often not costly. The purpose of governance in crypto-economics is to expand the network effect, to pursue censorship and discrimination, and to inevitably suffer from some people's resentment, which is not conducive to the expansion of network effects. Therefore, I believe that in general, the penetration of cryptographic protocols into economic activities will promote the development of society in a more open, fairer and more free direction. In the process, it is inevitable that some alternative economies will emerge, representing the consensus of certain special groups. There are also some economies that choose to comply with the legal requirements of a certain country and accept supervision. These are the community's own choices. Whether it is right or wrong, the so-called survival of the fittest, the market will give an answer.
Encryption economies have become accustomed to paying for security (out of the box) and will be accustomed to paying for governance. By controlling the number of governance agents and improving the efficiency of governance, the cost of governance in crypto-economics can be very low, such as an annual increase of 1%-2% for security and governance incentives, which is far lower than the defense spending of the real society, the parliament Expenditure and government administrative expenses. In the future, it is hoped that researchers will quantitatively analyze and compare the security and governance costs of major encryption economies, and gradually establish a consensus on appropriate governance costs in the encryption community.
Web3 is a new generation of Internet that is more free, open, safer and fairer. From a computing architecture perspective, Web3 is a serverless, decentralized Internet. In the Web3 network, participants or nodes are equal, there is no distinction between server and client, and all nodes participate in the formation and recording of network consensus more or less.
Web3 is an ecosystem of interconnected and interdependent encryption protocols. Internet users use a self-generated identity ID (asymmetric key pair/address) to use an encryption protocol to directly control their digital assets through encryption protocols. A trading activity and participate in the encryption protocol governance process either deeply or shallowly. Web3 enables Internet users to master their digital identity, assets and data.
Written by: Liu Yi, Partner, Random Capital
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- China Blockchain Game Development Team Pure White Matrix Launches World's First Cloud IDE to Access Libra Move Language
- After halving, LTC is sluggish, maybe it’s just BTC’s fault.
- Years of regulatory uncertainty have caused ICO projects to flee the US
- Ethereum 2.0: The future of Ethereum
- The Digital Currency in the Eyes of Economists – The Exchange: The Glory of the King
- Nakamoto's mistakes have made Bitcoin more central. Do you understand these questions?
- Market analysis: the sharp drop is just a dishwashing, the positive is not honored