Technical Guide | A Brief Study of Cross-chain Communication
1 Abstract
Cross-chain technology is essentially a technology that securely and reliably transfers data D (or information I, or message M) on the A chain to the B chain and produces the expected effect on the B chain . Because the blockchain system is originally a special distributed ledger database system, the most common data transferred is asset data, such as token balances.
At present, the mainstream blockchain cross-chain technology solutions according to their specific implementation methods include: notary public mechanism, hash lock, side chain & relay chain, distributed private key control.
At present, the most famous cross-chain projects are Cosmos and Polkadot, both of which use a multi-chain and multi-layer architecture based on relay chains. It can be seen that the side chain & relay chain technology will be the main force of future cross-chain technology.
This article first briefly introduces the technical principles of cross-chain. It will briefly introduce the notary mechanism, hash lock, and side chain & relay chain technology in detail. Then this article will introduce several related cross-chain projects, including Plasma based on ETH, Darwin network based on Polkadot, and IRIS based on Cosmos.
- European authorities look at national digital currencies: love and fear
- Barbarians at the Door of the Blockchain: Understanding the Crypto Industry M & A
- Urban rail two-dimensional code interconnection and interoperability realized from "1" to "11" in one year. Blockchain technology increased the "pass" capacity expansion
2 Notary mechanism and hash lock [1]
Cross-chain interaction can be divided into homogeneous chain cross-chain and heterogeneous chain cross-chain according to the different underlying technology platforms of the blockchain. The security mechanism, consensus algorithm, network topology, and block generation verification logic are all consistent between the homogeneous chains, and the cross-chain interaction between them is relatively simple. The cross-chain interaction of heterogeneous chains is relatively complicated. For example, Bitcoin uses the PoW algorithm and Fabric uses the traditional deterministic consensus algorithm. The block composition and deterministic guarantee mechanism are very different. The direct cross-chain interaction mechanism is not easy to design. Cross-chain interactions between heterogeneous chains generally require third-party auxiliary services to assist cross-chain interactions.
To achieve cross-chain security and credibility, there must be some requirements for cross-chain mechanisms and steps. The most important of these is the atomicity of cross-chain transactions. For ordinary intra-chain transactions, transactions need to support atomicity-if the transaction fails, it needs to be rolled back. The same is true for cross-chain transactions. When it fails, it will roll back transactions involving two or more chains of this transaction.
2.1 Notary schemes
Notary public is also called witness mechanism, which is a kind of intermediary. Assuming that blockchains A and B are not directly interoperable, they can introduce a mutually trusted third party as an intermediary, and this mutually trusted intermediary will verify and forward cross-chain messages . Many times, this notary / intermediary is the exchange. Its advantage is that it supports heterogeneous blockchain cross-chain. The disadvantage is that there is a risk of centralization. It can only achieve exchange but not transfer.
Cross-chain transaction example: Suppose Alice wants to trade 1 BTC for 50 ETH with Bob
1. Alice deposits her 1 BTC into the Bitcoin address of the exchange; Bob deposits her 50 ETH into the exchange's Ethereum address; 2. Alice places an order on the exchange: 1 BTC for 50 ETH; 3 .Bob completes the transaction with Alice through the exchange, Alice gets 50 ETH, Bob gets 1 BTC (There will be many forms here. One is that Bob hangs out a list to buy Bitcoin, and then the exchange matches. The other is Bob I saw Alice sell the sell order directly, and then asked for this sell order directly.) 4. Alice withdraws 50 ETH from the transaction to her Ethereum account; Bob withdraws 1 BTC from the transaction to her Bitcoin account. ;
BTC and ETH exchange between Alice and Bob was completed by introducing an intermediary. It can be seen from this example that the exchange method can only support asset exchange at present, and the atomicity and security of asset exchange are completely guaranteed by a centralized exchange, so there is a certain degree of centralization risk.
2.2 Hash-locking
A typical implementation of hash lock is a hashed time lock contract (HTLC). Hash time locks first appeared on Bitcoin's Lightning Network. Hash time lock cleverly uses a hash lock and a time lock to force the receiver of the asset to determine the receipt within the deadline and generate a receipt certificate to the payer, otherwise the asset will be returned to the payer. The receipt certificate can be used by the payer to obtain the equivalent amount of assets on the receiver's blockchain or trigger other events. Hash locks can only be exchanged and cannot transfer assets or information, so its use scenarios are limited.
Cross-chain transaction example (still using the transaction requirements in the previous section as an example):
1. Alice constructs a string s randomly and calculates its hash h ; 2. Alice sends h to Bob; 3. Alice locks her 1 BTC asset through the contract, sets a longer lock time T1 , and then Set the conditions for obtaining the BTC: Bob provides the original value s of h ; 4. Bob locks 50ETH to his contract and sets a relatively short lock time T2 ( T2 <T1 ). Then set the acquisition conditions of 50ETH: Alice provides the original value s of h ; 5. Alice sends the string s to Bob's contract to get 50 ETH;
Bob observes Alice's s value in step 5 and sends it to Alice's contract to successfully obtain 1 BTC; thus completing the exchange of assets.
If it times out, the locked asset is returned to the original owner.
From the above process, it can be seen that there are some constraints on the hash time locked contract:
• Both parties must be able to parse the contract's internal data, such as s , such as proof of locked assets;
• The timeout of the hash lock needs to be set to ensure that there is a time difference so that the other party can withdraw its assets in a timely manner when one side cheats.
3 side chain / relay chain
3.1 The meaning and significance of side chains
First, what is a side chain ?
According to [3] , at the beginning, the main chain specifically refers to the Bitcoin mainnet blockchain . Therefore, the so-called side chain is any block chain that can comply with the side chain protocol and communicate with bitcoin except the bitcoin blockchain. The sidechain makes Bitcoin more liquid; it is difficult to develop applications on the Bitcoin mainnet. Now you can solve this problem by developing applications on the sidechain and then connecting to the main chain using interworking methods-indirect use of Bitcoin , Which further consolidated the central position of Bitcoin.
However, it is naturally impossible to say that the main chain refers to Bitcoin. According to Wikipedia: " Sidechain is used to refer to the blockchain that is parallel to the main blockchain. Entries from the main blockchain can be connected to the sidechain or can be connected by the sidechain; this way , The sidechain can operate independently of the main blockchain (for example, by using an alternate record-keeping method). A sidechain model is the drive chain. "
This statement contains three main points :
1. The side chains are relative. We cannot simply say that a certain chain B is a side chain, but we must say that this chain B can be a side chain of chain A.
2. The side chain is independent from the main chain. Chain B can have its own functions and does not need the support of Chain A when it runs itself. If the B chain fails or is centrally controlled, it will not directly affect the operation of the A chain itself (but it can indirectly affect, for example, the A chain still interacts with it after the B chain is controlled).
3. The side chain and the main chain can be connected and interoperable, that is, cross-chain. When the cross-chain function is to be realized, the B-chain and A-chain need to communicate with each other. Because the side chain interworking mechanism is its most important function, the interworking between the side chain and the main chain is often called the side chain technology. As for whether the side chain itself is included in the side chain technology, different projects have different views.
Secondly, what is the significance of the side chain?
From the perspective of the single chain of the main chain, the side chain can virtually and horizontally improve the performance of the main chain. The so-called horizontal is to interconnect multiple side chains with the main chain, put most of the transactions on the side chain, and then realize through interworking with the main chain, which can virtually enhance the TPS of the main chain. The so-called vertical means that the side chain can have functions that the main chain does not have. With the side chain, the main chain also seems to support these functions. The so-called virtualization is that although there are horizontal and vertical improvements, the main chain itself has not changed at all . It just uses a lot of sidechain brothers to help it act like a proxy, making it appear to improve performance.
From a global perspective, sidechains, as a type of cross-chain technology, naturally make an important contribution to the interconnection of Wanchain. There are two architectures to realize the interconnection of Wanchain: 1. Any chain has both the function of the main chain and the function of the side chain (some materials will have the function of side chain is called follow the side chain protocol), just like any computer network A computer is both a host and a router. 2. Only a few specific chains are used as the main chain. All other chains only support the side chain function. Similar to the current computer network, there are core parts of the network-pure routers and edge parts of the network-pure hosts. .
3.2 Sidechain Technology
The side chain is implemented through a two-way anchoring technique. The temporary digital currency is locked in the main chain, and the equivalent digital assets are released in the side chain. The biggest difficulty in implementing two-way anchoring is that the protocol transformation needs to be compatible with the existing main chain, that is, it cannot affect the work of the existing main chain. According to [2] , the specific implementation methods are: single hosting mode, alliance mode, SPV mode, drive chain mode, and mixed mode.
The single escrow mode is the completion of locks and deposits by intermediaries similar to transactions. The alliance model is the notary model, which uses multiple signatures of multiple notaries to sign transactions that transfer assets, avoiding centralization.
The SPV mode is to send a transaction to a special address of the chain, which will automatically create an SPV certificate to the side chain and initiate a transaction to unlock the corresponding asset on the side chain. The drive chain model is to use miners as fund custodians to release the supervision of assets to digital asset miners. Miners vote to decide when to unlock assets and to whom. The mixed mode is an effective combination of these side chain mechanisms. For chains with different structures, the mode that is most suitable for its structure is used. For example, the main chain uses SPV and the side chain uses drive chains.
Here the SPV mode is the most used and the most promising. SPV is Simple Payment Verification, which can verify the existence of a transaction.
BTC-Relay is known as the first sidechain in history.It builds a Bitcoin sidechain through Ethereum, and uses Ethereum's smart contracts to allow users to verify Bitcoin transactions.
SPV transaction example (still using the previous transaction demand as an example): 1. Bob sends 50ETH to BTCSwap to freeze the contract (if the contract confirms that Bob receives 1BTC from Alice, it will automatically transfer 50ETH to Alice); 2. Alice After confirming Bob's freezing information, transfer 1BTC to Bob's Bitcoin account; 3. BTC-Relay pushes the Bitcoin block header to the BTCSwap contract; Alice sends herself a transaction that transfers BTC to Bob's tx to the contract BTCSwap contract, requesting 50ETH; The .BTCSwap contract combines tx and the Bitcoin blockchain for SPV verification. If the verification is successful, 50ETH will be transferred to Alice's Ethereum address. The side chain mechanism can provide more cross-chain interaction scenarios than hash locking. The idea of side chain and SPV-like verification is suitable for all cross-chain scenarios.
3.3 Relay chain
The relay chain is a fusion and extension of the notary mechanism and the side chain mechanism. At present, the two most active cross-chain projects in the community, Cosmos and Polkadot, use a multi-chain and multi-layer architecture based on the relay chain. Cosmos currently supports It is cross-chain asset interaction; Polkadot claims to provide any type of cross-chain interaction, but the specific implementation remains to be seen.
3.3.1 Cosmos relay chain mechanism [1]
In order to support cross-chain operations between parallel chains, Cosmos proposed an IBC (Inter-Blockchain Communication Protocol).
Take chain A to chain B transfer 10 tokens as an example to illustrate the cross-chain interaction using IBC:
Track each other. If A is to conduct cross-chain transactions with B, then A and B chains need to run light nodes equivalent to each other's blockchain, so that they can receive each other's block header information in real time (to facilitate subsequent SPV-like verification); Chain B initializes the IBC protocol.
Chain A freezes 10 tokens, and generates a corresponding certificate to send to chain B.
Chain B receives the corresponding IBC message, and determines from the block header information of chain A that chain A does indeed freeze the corresponding assets, and then chain B will generate assets equivalent to 10 tokens.
The above is the basic process of using two parallel chains of the IBC protocol to directly cross-chain. If there are many blockchains, the complexity of this two-to-two cross-chain will increase at the combination level. Therefore, the Cosmos network also introduces a Hub relay chain . All the parallel chains are connected to the Hub through IBC , allowing the Hub to assist in the verification and asset transfer of cross-chain transactions. (So, a certain chain can interact with the chain in the Cosmos system. Interaction = A chain can connect to the Hub). Cosmos currently implements an official Hub called the Cosmos Hub (see Figure 3.1).
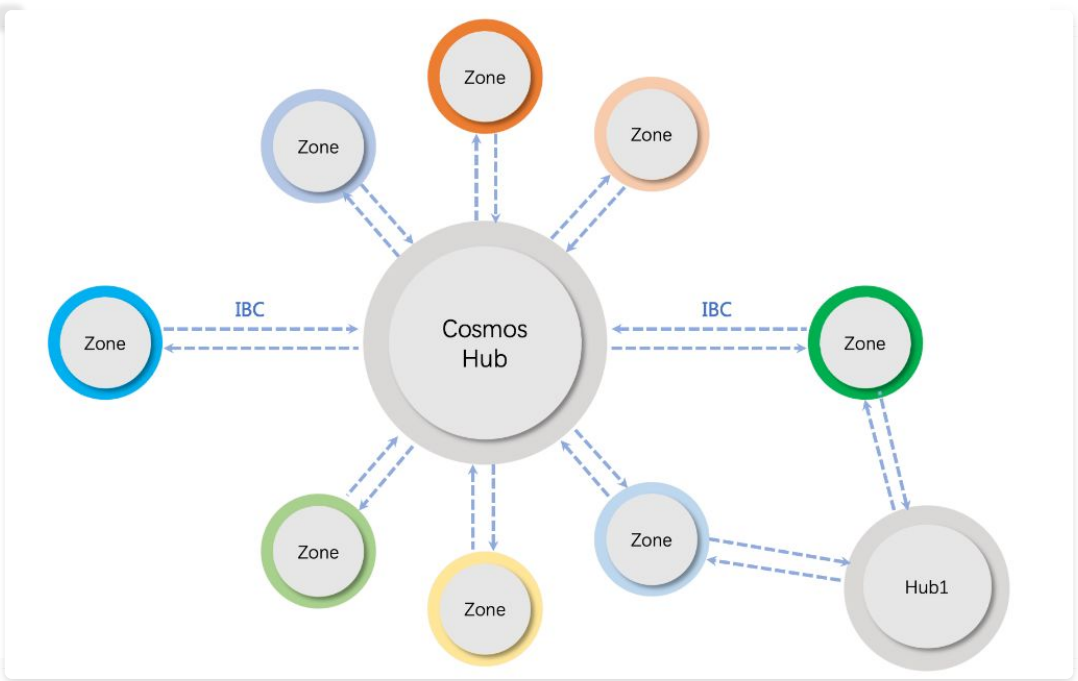
Figure 3.2 is a detailed architecture diagram of the Cosmos network. A chain is divided into a network layer, a formula layer, and an application layer in terms of a hierarchical structure . To facilitate parachain development, Cosmos provides tendermint core (tendermint for short) and Cosmos SDK (Go language) . Among them, tendermint refers to the encapsulation of the network layer and the consensus layer, and the Cosmos SDK is a commonly used module in the application layer: account, governance, staking, IBC, etc. [4] . Therefore, if you develop a new chain yourself, you can use Cosmos SDK + tendermint, and the developed chain can be directly connected to Cosmos Hub (Cosmos Hub itself is also developed with Cosmos SDK + tendermint).
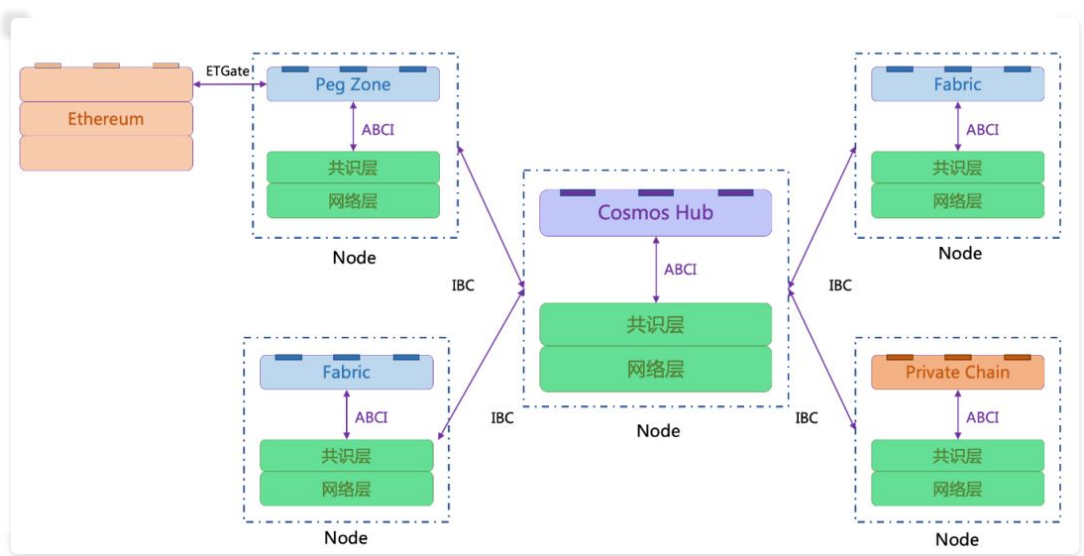
For non-Cosmos SDK-developed blockchains (such as those that already exist), if you want to interact with the chains in the Cosmos system (that is, you can connect with the Hub), you need to use Peg Zone to bridge, so-called Peg Zone It is a chain developed using the Cosmos SDK, which can both access the Hub and interact with the original chain . As shown in the Ethereum in the figure, if you want to access the Cosmos Hub, you need to use the Cosmos SDK to develop a new chain that functions as a Peg Zone.
The so-called Cosmos mainnet refers to the first official version of the Hub developed by the Cosmos team itself , which is the first central hub when different chains perform cross-chain operations. Ethereum will be the first public chain developed by Cosmos and not developed by Cosmos SDK. There are currently two projects to achieve this connection: the Ethermint project led by the Cosmos development team, and PlasmaChain led by the Loom Network. These two projects are actually developing a chain that connects Ethereum and Cosmos Hub and functions as a Peg Zone.
The agreement should be reached by all parties. The "side chain agreement" mentioned in sections 3.1 and 3.2 is not really a real agreement. Because the side chain technology currently does not have some consensus agreements like computer networks, it can only be Said to be a side chain mechanism. The biggest contribution that Cosmos brings to cross-chain lies in the design of the IBC protocol, which provides a universal cross-chain protocol standard . The design of IBC enables cross-chain transactions to be safely routed and forwarded between multiple Hubs, similar to the current TCP / IP protocol of the Internet. But unfortunately, the current Cosmos design can only support the cross-chain of assets, and the inconsistency of the consensus rate due to the different business of different blockchains will also affect the proof of the validity of cross-chain transactions.
Only the sidechain technology of Cosmos is described here. For more information about Cosmos, please see other references.
3.3.2 Polkadot's Relay Chain Mechanism
Polkadot's planar architecture is shown in Figure 3.3. It has three chain roles and four participants.
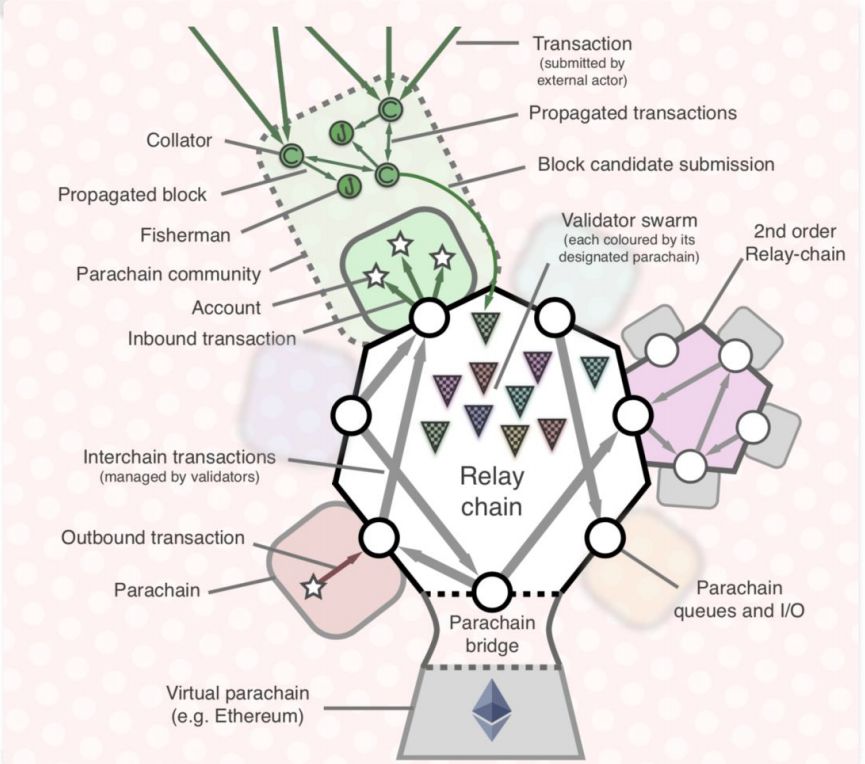
Three chain roles :
• Relay chain: The relay chain is at the core of Polkadot's system, and it mainly provides unified consensus and security guarantee for the entire system;
• Parachain: In Polkadot, parachains are responsible for specific business scenarios. Parachains themselves do not have consensus on blocks. They transfer the responsibility of consensus to the relay chain. All the parallel chains share the relay chain from the relay chain. For security, the relay chain is a part of Polkadot (the relay chain may not be a chain [5] . Polkadot defines it as the data structure of an App, so it can be a DApp or even a general App; but in most cases it is also Will be a chain);
• Bridges: Bridges in Polkadot actually have three meanings [6] , the most important of which is: providing different Bridges and Polkadot for blockchains outside the Polkadot system (such as Bitcoin, Ethereum) Connected together for cross-chain interaction.
The three chain roles are similar to those in the Cosmos system.
Four parties :
• Validator: The Validator is responsible for Polkadot's network block generation. It will run a client of the relay chain, and in each round of block generation, it will verify the blocks it nominates in the parallel chain. When the blocks of the parachain are determined by their verifier set, the verifiers will assemble all parachain block headers into the blocks of the relay chain and reach consensus.
• Collector (also called collator): Helps the verifier to collect, verify, and submit alternative parallel chain blocks, and maintains a full node of the parallel chain.
• Fisherman: Fisherman mainly relies on reporting illegal transactions or blocks to gain income;
• Nominator: The party that owns the stake, maintains and is responsible for the security of the verifier.
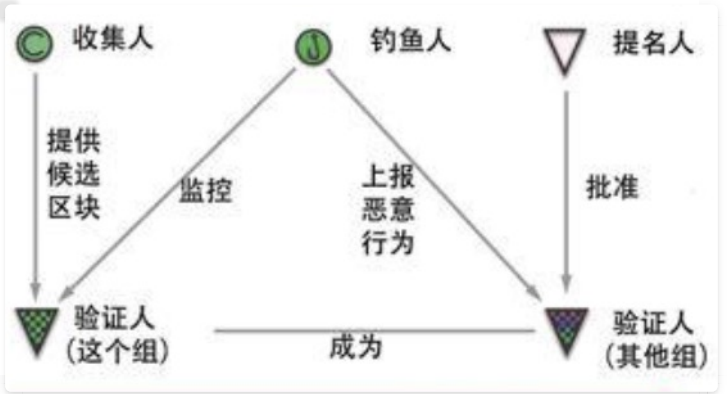
Figure 3.4
Figure 3.4 illustrates these participants. The entire process is performed automatically and decentralized.
The user initiates a transaction on the parallel chain. The transaction is collected by the collector, packaged into blocks, and handed over to a group of validators to verify. This group of validators does not come from the parachain, but comes from the pool of validators managed by the relay chain in a unified manner and is assigned to the parachain.
Each parachain has a message output queue and a message input queue. If the user initiates a cross-chain transaction, the transaction will be placed in the output queue. It is then put into its input queue by the collector of the target parachain. The collector of the target parachain executes the transaction, generates a block, and is finalized by the validator group.
The nominee is the holder of the Polkadot Basic Token DOT, and he hopes to pledge the DOT to gain income. But either because of the small number of DOTs or the lack of expertise in running and maintaining validator nodes. Therefore, the system provides another way to participate, that is, the holder selects the validator he trusts, pledges his DOT through the validator, and shares the benefits of the validator.
Fisherman is a software process that monitors illegal activities on the network and submits reported transactions to the blockchain once it is discovered. Reporting transactions also need to go through a consensus process. They are verified by more than 2/3 of the validators, packaged into blocks, and penalties and rewards are also blockchain transactions [7] .
In Polkadot, if Parachain A needs to send a transaction to Parachain B, the process is as follows:
• Chain A puts cross-chain transactions in its own message output queue, engress.
• Collator of Chain A collects ordinary transactions of Chain A and cross-chain transactions and submits to the set of validators of Chain A.
• The validator set verification of chain A is successful, and the block header information of chain A and the information of the engress of chain A are submitted to the relay chain.
• The relay chain runs a consensus algorithm for block confirmation and cross-chain transaction routing. The validator on the relay chain will move the corresponding transaction of chain A from the queue queue of chain A to the message queue of chain B into the ingress queue.
• Chain B executes the block, executes the corresponding transactions in the inress queue, and modifies its own ledger.
The above are the main steps of Polkadot cross-chain transactions. Polkadot's tool for the application chain is Substrate, which currently supports Rust language development.
4 Cross-chain related projects
4.1 ETH.Plasma
Ethereum's Plasma is a solution for Layer 2 expansion. The principle of Plasma is to move transactions to an off-chain and process them in a Secondary Chain. The idea comes from the side chain, but it is exactly the same. However, Plasma is not as mature as State Channel. At present, it has only applications in payment, and the number is very small. It is conducting research on use in fields other than payment.
4.2 Polkadot. Darwinia
4.2.1 Darwin Network Overview
The Darwin Network is a cross-chain gaming network constructed using Polkadot's Substrate technology. The technology of Darwin Network can actually be seen as a secondary development on Polkadot's Substrate, which is improved into a cross-chain interaction dedicated to game assets and game operations . At present, it is mainly used to support the evolutionary planet and related business systems ( evolutionary planet is a virtual world of games built on the blockchain and also a DAO, similar to "Minecraft" on the blockchain). The mainnet token is RING.
Darwin's network operation modes are Solo mode and Polkadot mode (It is worth noting that the specific incentive scheme will be different under different operation modes [8] .).
1) Solo mode . In fact, the Darwin network itself is a network with its own relay chain . In this network, various games become a sub-world (sub-continent) of Darwin. This sub-world can be a parallel chain developed using Polkadot's Substrate, or it can be a smart contract on ETH or EOS. These sub-worlds access the relay chain of the Darwin network in the same way as Polkadot Parachain accesses the Polkadot Relay-chain.
2) Polkadot mode . The Darwin network as a whole can also be regarded as a Parachain of Polkadot, and connected to the Relay-chain of Polkadot. In this sense, the Darwin network can be regarded as a second order relay-chain (2nd order Relay-chain) of Polkadot.
The Darwin network structure is shown in Figure 4.1. In the picture we see a thing called the Darwin application chain. The Darwin application chain to the Darwin network is equal to the Parachain to the Polkadot network. Darwin Application Chain is a set of application blockchain frameworks designed and developed based on Substrate and Darwinia Kernel.
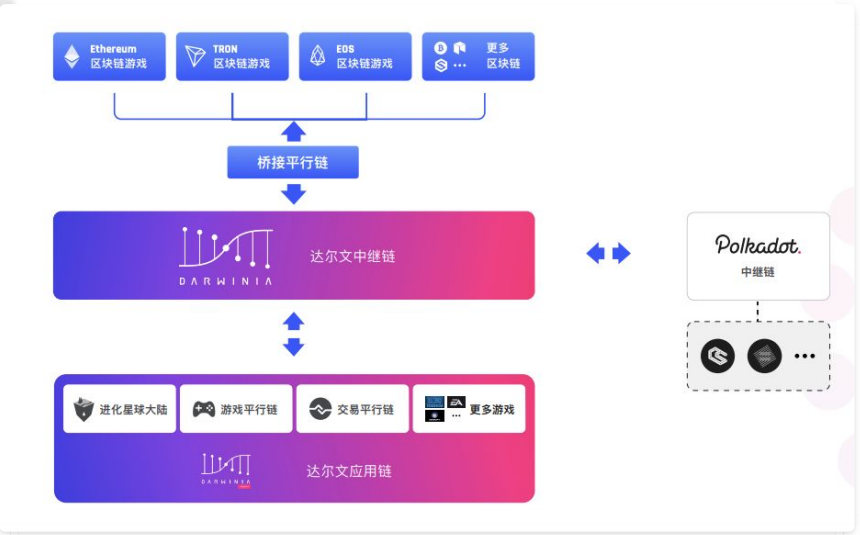
Figure 4.1
4.2.2 Interstellar Asset Standards
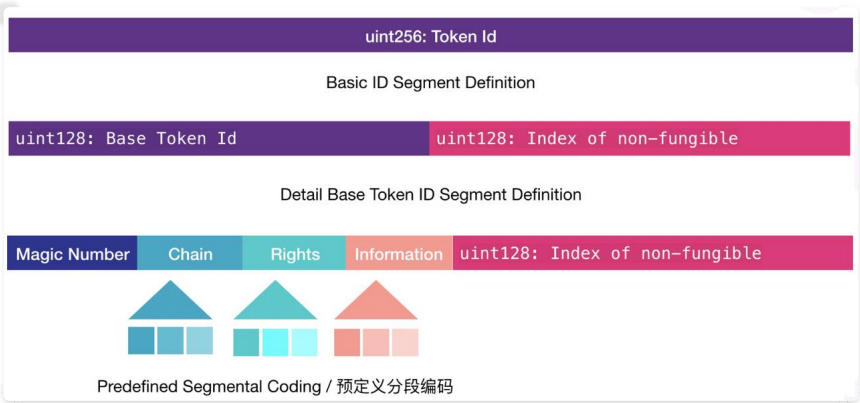
For game asset cross-chain, the most important nature is the definition of asset data structure and operation. The "NFT Identifiability" section of the Darwin Networks official website [9] outlines its interstellar asset coding standards . It believes that in a single network, the token ID in the domain can identify unique items in the domain, but not in the interconnected environment. Therefore, it designed an interstellar asset coding standard, so that assets of different public chains and different games can be uniquely identified on the Dallas Network, allowing game assets to be transferred across chains. The meanings of the fields of the interstellar asset coding standard are as follows:
4.3 Cosmos.IRIS
The previous Darwin network is a project in the Polkadot ecosystem (the main network token is IRIS), and IRIS is a project in the Cosmos ecosystem [10] . There are two main challenges it aims to address:
Integration and collaboration of off-chain computing and resources on distributed ledgers
– Explanation: IRIS believes that many things should not be put on the chain or solved by smart contracts, such as some computing problems
– Explanation: IRIS believes that cross-chain should not be just assets, but various resources (why did you choose Cosmos? Cosmos only supports asset cross-chain = _ =)
Interoperability of services across heterogeneous chains
The previous Darwin network was mainly for games, while IRIS was for business applications (its team has a Ph.D. platform that has been a researcher at the Institute of Computing Technology of the Chinese Academy of Sciences). IRIS preset companies and IRIS cooperate in the way of Consumer / Provider: IRIS provides enterprises and project parties with easier-to-use SDKs to help them take advantage of the benefits of distributed ledgers .
Having said IRIS's vision, let's take a look at its network topology.
In topology, IRIS is similar to Darwin network. IRIS was developed with Cosmos SDK + Tendermint. It is a network in itself, with Hub, and can also access the Cosmos ecosystem as its zone. Of course, IRIS is under the Cosmos ecosystem, and Darwin's network is under the Polkadot ecosystem.
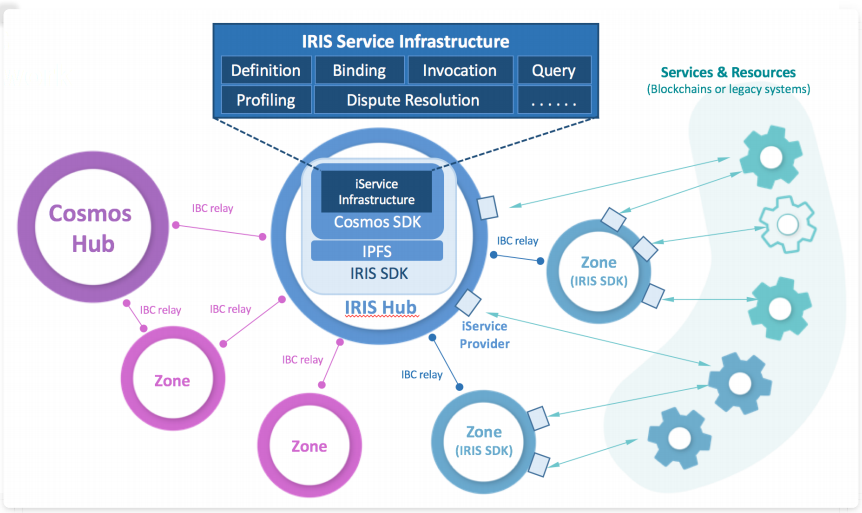
Figure 4.3
What is obvious in Figure 4.3 is not explained. The iService is actually the abbreviation of IRIS Services, which is used to bridge the gap between the blockchain world and the non-chain application world. The way to bridge is to coordinate the complete life cycle of the Off-Chain service (from its definition, binding (provider registration), invocation to its governance (analysis and dispute resolution), which are just a few things in the blue form). By enhancing the IBC processing logic to support service semantics, the IRIS SDK aims to allow distributed business services to be available across the entire blockchain Internet [11] .
In addition, its network contains three roles :
• Consumers: Use Off-Chain services by sending requests to the network and receiving responses from the network.
• Providers: can provide one or more iService-defined implementations. And usually acts as an adapter for basic services and resources located in other public chains and enterprise legacy systems. The provider monitors and processes incoming requests and sends responses back to the network. By sending a request to another provider, the provider can act as a consumer at the same time .
• Profiler: is a special user representing IRIS Foundation Limited ("the Foundation"), a limited liability company established in Hong Kong. The foundation will lead the construction of the IRIS network. Profiler is the only user authorized to call iService in profile mode. This service is designed to help create and maintain target provider profiles for consumers to choose the right provider.
4.4 Other items
ChainX and Edgeware are two very important projects in the Polkadot ecosystem. It can be said that they are the first and second brothers in the Polkadot ecosystem. Projects based on the Polkadot ecology are listed in Teams building on Polkadot . This is only briefly introduced here for the time being.
ChainX is an asset cross-chain project based on Polkadot's Substrate. ChainX transforms inter-chain assets into a system through de-centralization. Any chain can communicate with all chain assets as long as it establishes a connection with ChainX. Polkadot aims to do the underlying infrastructure and achieve arbitrary message cross-chain, while ChainX focuses on asset cross-chain. ChainX's mainnet token is PCX.
Edgeware is a smart contract platform. Once Polkadot is online, users can use Edgeware to quickly deploy smart contracts on Polkadot. Supporting WebAssembly, users can use Rust to write Edgeware smart contracts, and executing contracts in WASM is faster and more efficient than most virtual machines.
Personal thinking
Wanchain Interconnection is exciting, and this will definitely reduce the cost of chain development. Therefore, more blockchains will appear in the future. I guess most of these chains may not be decentralized at that time, and the nodes are controlled by a certain company. In this case, the results of multiple centralized chains interconnected.
Reference
[1] WeChat. Analysis and reflection on cross-chain technology
[2] Li Wancai. Deep understanding of EOS , p: 232-247.
[3] Chang Yan. Blockchain: From Digital Currency to Credit Society , p: 84-94.
[4] Beep News. Cosmos's Wanchain Interconnection Plan! 30 seconds to clarify what Cosmos is!
[5] Polkadot. Documentation / Parachains
[6] Polkadot. Documentation / Bridges
[7] chain news ChainNews. 20,000 words full solution Polkadot architecture and next-generation DApp development technology
[8] Darwin Network WeChat. Darwin Network-the first game chain in the Polkadot ecosystem
[9] Darwin Network Website. Genepaper
[10] StakingScan Wechat. Iris Network (IRIS)
[11] Irisnet Github. WHITEPAPER
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Free and Easy Weekly Review 丨 Can't Blockchain Privacy Protection and Regulation Have Both? Actually!
- Security Monthly Report | 16 security incidents occurred in November, with losses of nearly US $ 56 million
- Babbitt Column | Neglected Blockchain Node Operations: The Hidden Value of Mining
- Save 31 billion US dollars in compliance costs in 5 years, large-scale adoption of blockchain in food and beverage industry
- China Blockchain Talent Recruitment Report
- Perspectives | Bitcoin from a Money Carrier Perspective
- Site | Blockchain national team landed in Hangzhou, 5 applications accelerate the "urban brain" evolution