Blockchain entry | Blockchain 51% power attack is not so terrible
In the world of bitcoin and cryptocurrencies, it is not uncommon to encounter many concepts and expressions that have never been seen before, and to truly understand their meaning. In this article, I will try to uncover the mystery of one of the concepts, the famous 51% attack.
51% of attacks are inseparable from other concepts, such as mining, consensus mechanisms, lone blocks, and double-flowering issues. It is difficult to understand if readers are unfamiliar with these terms. Here is a discussion that does not limit my 51% attack, I will give a brief explanation.

Introduction
Bitcoin is a point-to-point payment system based on a distributed ledger that is shared by all participants in the network. A distributed ledger is a logbook in which all transactions between network equity holders are recorded. The ledger is linked by blocks, new transactions are recorded on the new block, and new blocks are continuously added to the existing chain, so the term blockchain is used.
- Detailed explanation of the FundWin vulnerability system: Can the project party be suspicious of “doing evil”?
- 8Q | Don't open the scene: Big coffee gathers DVP, big white hat and hacker
- Can the blockchain help “Yang Anze” to “send money” better?
Adding a new block to the existing chain (along with the transactions it contains) requires high-intensity computing, which we call mining, performed by a designated node on the Bitcoin network called the "miner." The miner's computing power is called the hash rate and is measured in hashes per second (H/s) or several times the number of hashes. All the miners are competing with each other. Whoever wins can add new blocks to the chain and receive corresponding rewards. The higher the hash rate, the greater the chance of winning the game.
Since the bitcoin books are distributed, for example, each node on the network has a copy of the blockchain, so it is necessary for different participants to agree on a set of rules to make the payment system of the entire network reliable and consistent. We call this set of rules a consensus agreement.
One of the problems to be solved by the consensus protocol is how to deal with scenarios where different nodes eventually render different blockchain versions. This occurs when two miners extend the blockchain almost simultaneously, resulting in two slightly different and competing accounts. This inconsistency is resolved by waiting for the next miner to add a new block to either of the two chains. The chain that is first extended will win the network consensus, and the other chain will be discarded. To explain in a general way, the longest chain is the king. The blocks (usually only one) contained on the dropped chain are called orphans. Transactions contained on a lone block (unless they are also added to the longest chain) are returned to the memory pool, which is an indeterminate state, and all unacknowledged transactions are waiting to be selected and packaged into a new block.
If a transaction (whether from a lone block) waits too long (a few days) in the memory pool, the transaction will be cancelled and the funds will be returned to the sender's wallet. This can lead to double-flowering problems, and eventually the transaction for purchasing goods or services will be cancelled, and the buyer will withdraw the funds while retaining the goods or services originally purchased.
In order to avoid the double flower problem, the transaction will only be confirmed after adding a certain number of new blocks to the block related to the transaction. In Bitcoin, the number of new blocks is set to 6.
Now that we understand all the concepts and terminology, we can finally discuss 51% of the attacks.
51% attack
The 51% attack is not intended to disrupt or interfere with the consensus protocol. Instead, it follows the protocol rules to help the attacker benefit from changing the contents of the blockchain.
To explain how to implement a 51% attack, we need to consider the following scenario. A group of miners who exceeded the 51% of the entire Bitcoin network decided to separate themselves from the rest and maintain communication in their own parts.
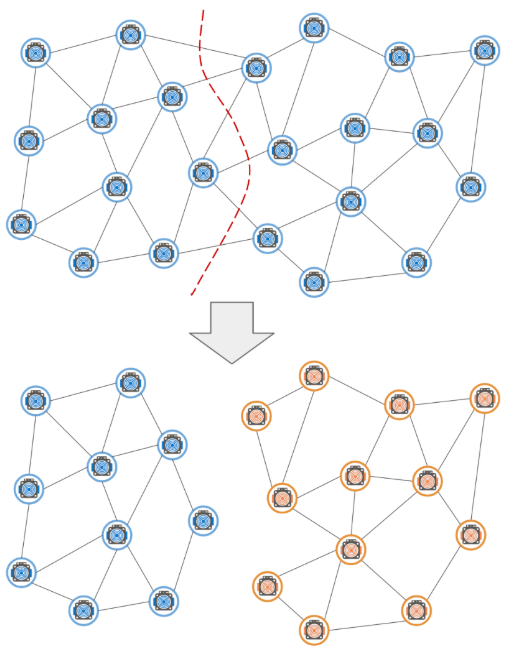
Description 1: A group of miners who exceed 51% of the entire Bitcoin network decided to separate themselves from other chains while maintaining communication in their own chains.
After cutting off the connection with other parts, the group of miners will carry out the mining work as usual, except that they will not share any progress with another group of miners, nor will they receive progress updates from another group of miners. In other words, although the two groups of miners have the same copy of the book at the time of separation, after separation, the two groups will begin to extend their internally shared copies independently of each other.
Now, which blockchain version will be extended faster? Since the separated group (attacker) has more computing power than the rest, it can extend its own chain copy faster than the remaining group. Given a certain amount of time, the difference between the lengths of the two versions of the chain will be statistically proportional to the difference between the two sets of hashing powers.
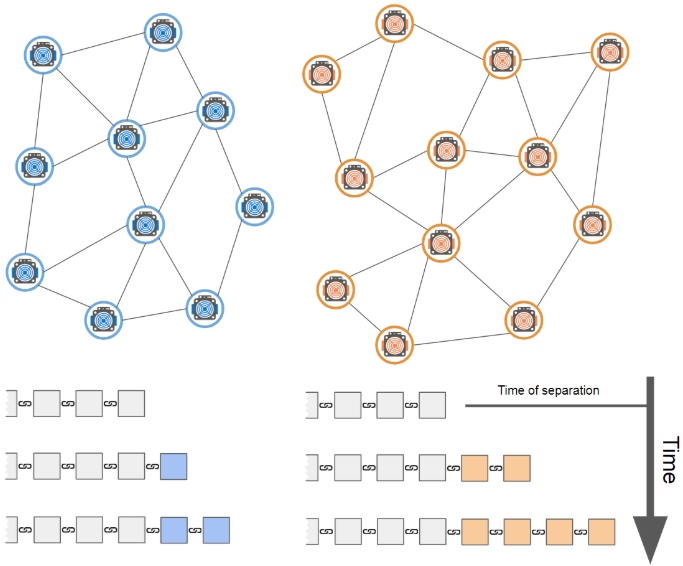
Description 2: Since separate groups (attackers) have more computing power, they can extend their version chain faster than the rest.
If the miners of the detached group are now rejoining the remaining groups, then two competing versions of the chain will be broadcast throughout the network, and according to the consensus protocol rules, the nodes will retain the longer version chain and delete the shorter version. This means that from the time of separation to the time of reunion, the blocks on the shorter chain dug by the remaining groups will be isolated, and the transactions on the block (at least a portion of the transactions) will be returned to the memory pool.
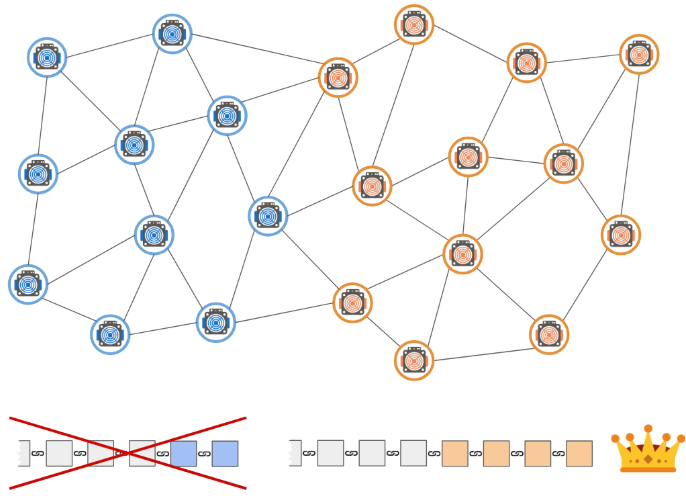
Description 3: If miners separated from the network rejoin the remaining groups and their blockchain version is longer, they will win consensus.
If the transaction returned to the memory pool is used to purchase goods, this situation will open the door to the possibility of double flowers. Most importantly, a group of miners initially separated from the network can block transactions that are selected and packaged into new blocks because they still have 51% more computing power than the entire network. If these transactions stay in the memory pool for longer than a certain time limit (bitcoin is 72 hours), the transaction is cancelled and the funds are returned to the original recipient (buyer wallet). At this point, the buyer will retain the funds and obtain the goods purchased with these funds. If 51% of attacks are premeditated and coordinated, an attacker may take advantage of this unresolved double-flower problem and have items that they ultimately did not pay.
Author | Ettore Murabito Source | Medium Translation | First.VIP Reprinted please keep the information at the end of the article. Original: https://medium.com/swlh/the-51-attack-what-is-it-d295e70b9ac4 Source: https://first.vip/shareNews?id=2255&uid=1
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Babbitt Interview | Author dialogue Bulletproofs: Money is the driving force encryption cryptography practices
- The Block's latest research: Which investment institutions benefit from Coinbase's currency?
- Building a “government wisdom brain” and promoting “blockchain+”, building big data across Hainan Island
- The trade-off of fragmentation technology: NEAR Protocol VS Ethereum 2.0
- LedgerX roars CFTC: Former chairman has delayed the approval of his license due to “personal grudges” and Bakkt received “special care”
- We talked to the author of Bulletproofs about the latest advances in zero-knowledge proof technology.
- Li Lin's latest speech: What is the "dao" of the blockchain?