Blockchain Security Monthly Report | 11 security incidents occurred in February, with a loss of 48.23 million US dollars
DeFi security
There were 4 DeFi security incidents in February, as follows:
1) On February 15th, the DeFi project bZx team issued an announcement on the official telegram group, stating that a hacker had conducted a vulnerability attack on the bZx protocol. PeckShield security personnel proactively followed up the bZx attack incident and found that the incident was an attack on the design of shared composable liquidity between DeFi projects, especially in DeFi projects with leveraged trading and lending capabilities, this problem is easier to be exploited.
2) On February 18, bZx encountered a similar attack again. This time the attack is different from the previous one. The hacker "deceived" the bZx contract by manipulating the Oracle price, and the root cause was due to shared flows between platforms. It is caused by too little sex and flaws in the design of the price mechanism.
3) On February 23, due to human error during a function upgrade, the chain predictor Chainlink incorrectly marked the price of gold (XAU) as the price of silver (XAG), causing a loss of approximately $ 40,000.
- Data Direction 丨 BTC price trend from the fundamentals, market, sentiment and technology
- Analysis: halving is coming, Bitcoin may face greater volatility
- Highlights of the week: The central bank officially released the "technical security specifications for financial distributed ledger"
4) On February 29, Curve, a decentralized stablecoin trading platform, experienced an abnormal transaction. This transaction exchanged USDC worth USD 89,000 for BUSD valued at USD 465,000. The attacker conducted a clamp attack on two bus pools: curd's busd.curve.fi and y.curve.fi.
PeckShield comment: As the functionality of the DeFi project becomes more and more diverse, the hidden security issues are gradually exposed. Given its close relationship with user assets, it can be seen that the security issue of the DeFi project is very serious. Because each project is developed by a different team and has a limited understanding of the design and implementation of their respective products, integrated products are likely to encounter security issues in the process of interacting with third-party platforms, which in turn can lead to enemy suffering. PeckShield hereby recommends that before the DeFi project party goes online, they should seek a team that has conducted in-depth research on the product design of each link of DeFi to do a complete security audit to avoid potential security risks.
Exchange security
There were four exchange security incidents in February, including two hacking:
1) On February 10, the server storing the hot wallet private key on the Altsbit Exchange was hacked, and the theft of the hot wallet private key resulted in the loss of user assets.
2) On February 17, the VBITEX trading platform announced that it was hacked, resulting in malicious alteration of platform data and theft of virtual assets.
3) On February 17, the FCoin exchange claimed that due to funding difficulties, the capital reserve could not be cashed out by users, and the amount of funds that could not be redeemed was between 7,000-13,000 BTC.
4) On February 28, exchanges such as OKEx and Bitfinex suffered frequent DDoS attacks and related services were affected.
Among them, in response to the financial difficulties of the FCoin exchange, CoinHolmes, a visual digital asset tracking system under the PeckShield security team, launched targeted tracking and analysis of the relevant addresses involved. The CoinHolmes on-chain tracking system includes dozens of exchanges, over 60 million address tags, and involves a variety of mainstream digital assets such as BTC, ETH, USDT.
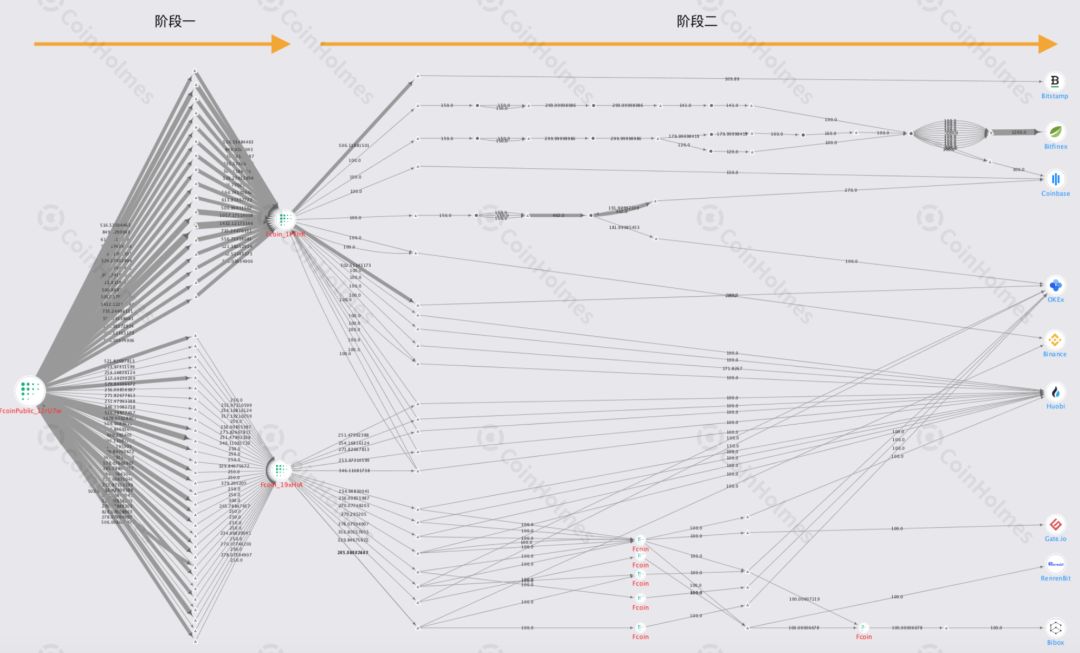
PeckShield comment: Through this incident of FCoin, everyone began to realize the potential crisis of centralized exchanges due to the lack of transparency of assets. This is a disaster, but at the same time I hope it will also be an inflection point. I hope more centralized exchanges will recognize the importance of transparency of funds and the mechanism of reserve payments. For the theft of private exchange keys and server intrusion, PeckShield recommends that exchanges use a more secure defense system, keep their private keys well, and patch operating system or third-party software vulnerabilities in a timely manner.
DApp ecology
PeckShield comments: Most DApp ecological security incidents are caused by contract players. Before receiving a player's token or rebate, DApp should check whether the target account is a smart contract. At the same time, developers should conduct security testing before the contract goes online to prevent known attack methods. If necessary, they can seek the assistance of third-party security companies to help them complete the attack testing and basic security defense deployment before the contract goes online.
SIM card attack
According to the address provided by the victim, CoinHolmes, a visual digital asset tracking system owned by the PeckShield security team, quickly locked the relevant address of the hacker, launched targeted tracking and analysis, and finally drew a panoramic view of the visual path transition:
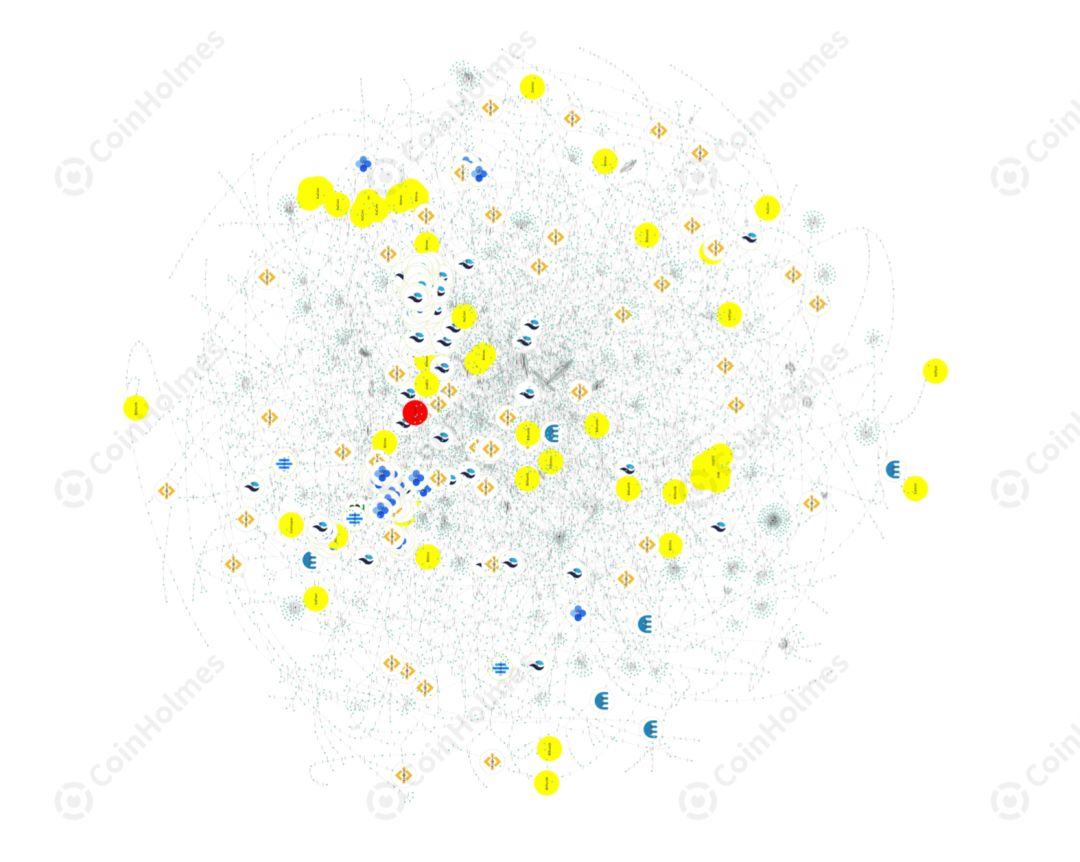
As shown in the figure, the method of the hacker's transfer of funds on the chain is very professional and complex, so that after the use of visual tools, it has no clear layering and context. By following up and analyzing the stolen BTC assets of the killer whale account, PeckShield security personnel found that after stealing 1,547 BTC, the hackers quickly cut and dispersed the funds and split them into small amounts, and further tried to make the assets through a more complicated obfuscation system. Tracking becomes extremely difficult.
Since the incident on February 22, in just a few days, hackers have used hundreds of addresses to transfer funds. The deepest level has reached 20 levels. In the process of fund splitting and transfer, 11.19 BTC have passed. Multiple transactions flowed into the Bittrex exchange address. As of now, most of the stolen funds are still in the hacker's address, and PeckShield is also locking in monitoring the further movement of target funds.
PeckShield comment: There is reason to believe that the hacker in this attack was a professional and technical gang. The gang made a lot of efforts from the selected target to the long-term tracking and breakthrough on-chain + off-chain. This seems to remind some early-earning and profitable bigwigs that they need to be vigilant against SIM card attacks, phishing and other common means of stealing coins, and carefully protect their crypto assets.
other
In addition to the above, there are some security incidents in February that are also worth watching:
1) The hacker used the loophole in IOTA's official wallet application Trinity to steal funds, and the official announced that the entire network would be closed.
2) Beware of malware called "Raccoon" that uses phishing and toolkits to steal user data and cryptocurrency through the browser.
PeckShield Comments: Various types of security hazards caused by lack of user security awareness and standardized operations have emerged endlessly, and various events such as phishing attacks and fraud are typical. It is reminded that users should carefully keep all kinds of private information, any small oversight may cause irreparable loss.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Can DeFi become a solution to the difficult financing of SMEs?
- MakerDAO Risk Leader: ProgPoW may do no good to the DeFi industry
- Crypto industry talent demand grows 26%, let's see what new positions are available?
- Before the halving, do you still have the opportunity to join the "Bitcoin 1% Elite Club"?
- Market enters the stage of grinding tofu, persistence is victory
- Air currency warning: the market may be entering the sixth cottage season, beware of air players
- Depth | Solve core pain points, blockchain opens up new space for supply chain finance






